华为防火墙NAT策略
前言:NAT技术是用来解决当今IP地址资源枯竭的一种技术,同时也是IPv4到IPv6的过渡技术,绝大多数网络环境中在使用NAT技术
文章目录
- 一、理论
- 1.NAT分类
- 1)NAT NO-PAT
- 2)NAPT
- 3)Easy-IP
- 4)NAT Server
- 5)Smart NAT
- 6)三元组NAT
- 2.黑洞路由
- 1)如何解决源地址转换环境下的环路和无效ARP问题
- 3.Sever-map表
- 1)区别
- 2 )配置
- 4.NAT对报文的处理流程
- 5.FTP传输方式
- 1)主动模式
- 2.被动模式
- 二、实验
- 1.实验环境
- 2.拓扑图
- 3.需求
- 4.详细配置
- 1)IP地址
- 2)server服务器和client客户端配置
- sever-ftp服务器配置
- server-http服务器配置
- client客户端配置
- 3)配置防火墙NAT
- 技术部的防火墙NAT
- 行政部的防火墙NAT
- 财务部的防火墙NAT
- 配置DMZ区域中的两台服务器
一、理论
1.NAT分类
1)NAT NO-PAT
- NAT no-PAT 类似于思科的动态转化,多对多,不转化端口,它不能解约公网IP地址
- 实际应用场景使用较少,主要适用于需要上网的用户比较少,而公网IP地址又足够多的场景
2)NAPT
- NAPT(Network Address and Port Translation,网络地址和端口转换)
- 类似于Cisco的PAT转换,NAPT即转换报文的源地址,又转换源端口。转换后的地址不能是外网接口IP地址,
属于多对多或多对一转换,可以节约公网IP地址,使用场景较多。
- 类似于Cisco的PAT转换,NAPT即转换报文的源地址,又转换源端口。转换后的地址不能是外网接口IP地址,
3)Easy-IP
- 出接口地址(Easy-IP):因其转换方式非常简单,所以也被称为Easy-IP
- 和NAPT一样,即转换源IP地址,又转换源端口。区别是出接口地址方式转换后的地址只能是NAT设备外网接口所配置的IP地址,属于多对一转换,可以节约IP地址
4)NAT Server
- 静态一对一发布,主要用于内部服务器需要对Internet提供服务时使用
5)Smart NAT
- Smart NAT(智能转换)通过预留一个公网地址进行NAPT转换,而其他的公网地址用来进行NAT No-PAT转换,该方式不太常用
6)三元组NAT
- 三元组NAT 与源IP地址、源端口和协议类型有关的一种转换,将源IP地址和源端口转换为固定公网IP地址和端口,能解决一些特殊应用在普遍NAT中无法实现的问题
- 主要应用于外部用户访问局域网的一些P2P应用
2.黑洞路由
- 在特定的NAT转换时,可能会产生环路及无效ARP,关于其如何产生,大概就是,在有些NAT的转换方式中,是为了解决内网连接Internet,而映射出了一个公有IP
- 那么,若此时有人通过internet来访问这个映射出来的公有IP,就会产生这两种情况
- 若要详细说起来,又是很麻烦,但是解决这两个问题很简单,就是配置黑洞路由(将internet主动访问映射出来的地址的流量指定到空接口null0)
1)如何解决源地址转换环境下的环路和无效ARP问题
-
NAT Server(粗泛)
- 是NAT Server转换类型中的一种,表示源地址和转换后的地址只有简单的映射关系,没有涉及端口等映射,如源地址为192.168.10.5,转换后的地址为202.96.10.2,如果做的是NAT Server(粗泛)这种类型的NAT,那么所有访问202.96.10.2的数据包都将转发给192.168.10.5这个地址
-
NAT Server(精细)
3.Sever-map表
- 状态化防火墙中会有一张表叫做会话表,用来记录的是内网访问外网时的一个连接信息,
当外网返回的数据匹配到会话表的记录时,直接放行相关返回流量
1)区别
- 会话表记录的是连接信息,包括连接状态
- erver-map表记录的不是当前的连接信息,而是通过分析当前连接的报文后得到的信息,
该信息用来解决接下来的数据流通过防火墙的问题。可以将server-map表的作用理解为通过未雨绸缪解决将来的问题,
如像FTP这种的多端口协议,在从一开始的三次握手,到最后完成数据的传输,其过程中,可能端口会发生改变等问题,
server-map正好可以解决这种问题 - 然而在NAT中也需要这个server-map表,就是在有数据流量通过NAT的方式穿越防火墙时,
server-map表会记录其源地址和转换后地址的对应关系,从而使后续流量可以不用查看NAT策略,
直接匹配到server-map表,从而实现高效的NAT转换。若用户通过互联网访问转换后的地址时,
也可以匹配到server-map表,从而高效的将数据转发到内网真实主机(必须保证安全策略允许通过)
2 )配置
- server-map表不用手动配置,是自动生成的
- 在NAT中,不是所有的表都可以生成server-map表的,我简单总结了一下,如下
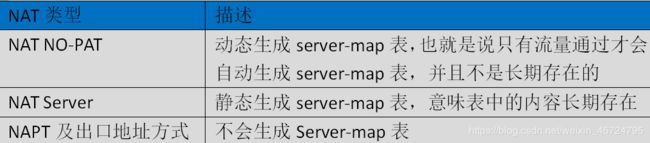
- 当防火墙上配置某些内类的NAT后,在防火墙上会生成Server-map,默认生成两个server-map条目,
分别是正向条目和反向条目(Reverse),如下
[USG6000V1]display firewall server-map
Current Total Server-map : 2
正向 Type: Nat Server, ANY -> 202.96.1.10:445[192.168.1.4:445], Zone:---, protocol:tcp
Vpn: public -> public
反向 Type: Nat Server Reverse, 192.168.1.4[202.96.1.10] -> ANY, Zone:---, protocol:tcp
Vpn: public -> public, counter: 1
- 此时Server-map表的作用是
- 正向条目 :携带端口信息,用来使Internet用户访问内网中的服务器时直接通过server-map表来进行目标地址转换。
- 反向条目(Reverse):不携带端口信息,且目标地址是任意的,用来使服务器可以访问Internet。
4.NAT对报文的处理流程
-
防火墙接口从收到一个报文到最终发送出去需要经历一系列处理流程,而NAT只是其中的一项任务。NAT的配置受到路由及安全策略的影响,所以了解NAT对报文的处理流程对配置AT有非常大的帮助。NAT对报文的处理流程如下图所示

-
从上图中可以看出来,因为防火墙处理报文的顺序是目标地址转换→安全策略→源地址转换,所以在NAT环境中,安全策略的源地址应该是源地址转换之前的地址,目标地址应该是目标地址转换之后的地址
-
一个报文,一般在同一个网络设备上,只会存在一种转换条目,即要么转换源地址(除NAT-Server类型的NAT转换之外),要么转换目的地址(NAT-Server类型的NAT转换)。源地址和目的地址的转换不会同时存在同一个网络设备上
-
NAT处理报文的流程如下
- 1.防火墙收到报文后,首先检查报文是否匹配Server-map中的条目,如果是,则根据表项转换报文的目标地址,然后进行步骤(3)处理;否则进行步骤(2)处理。
- 2.查找是否存在目标NAT的相关配置,如果是,并且符合NAT条件,则转换目标地址后进行步骤(3)处理;否则直接进行步骤(3)处理。
- 3.根据报文的目标地址查找路由表,如果存在目标路由,则进行步骤(4)处理;否则丢弃报文。
- 4.依次匹配安全策略中的规则,如果策略允许报文通过,则进行步骤(5)处理;否则丢弃报文。
- 5.查找是否存在源NAT的相关配置及是否符合NAT条件,如果是,则转换源地址后进行步骤(6)处理;否则直接进行步骤(6)处理。
- 6.在发送报文之前创建会话,后续和返回的报文可以直接匹配会话表转发。
- 7.防火墙发送报文。
-
因为防火墙处理报文的顺序是目标地址转换→安全策略→源地址转换,所以在NAT环境中,安全策略的源地址应该是源地址转换之前的地址,目标地址应该是目标地址转换后的地址
5.FTP传输方式
1)主动模式
- 服务器主动发起数据连接。首先客户端向服务器的21端口建立FTP管理连接
控制连接源端口是1万以上的端口目标端口:21
客户端以PORT命令告诉服务器“我打开了某个端口”你来连我。
这个时候服务器以源端口20目标端口“我打开了某个端口”向客户机请求并建立连接
2.被动模式
- 假设客户端有防火墙
- 客户机主动发起数据连接。首先客户端想服务器的21端口建立FTP管理连接
- 客户端有防火墙,这个时候服务器连接客户机是连不起来的,因为客户端有防火墙,需要被动模式
服务端以PASV命令告诉客户端,于是客户端向服务端进行建立数据连接
二、实验
1.实验环境
- 实验软件:eNSP软件
- 实验设备:
- 一台USG6000V防火墙
- 一台路由器、一台三层交换机
- 三台PC机
- 一台FTP服务器,一台WEB服务器
- 一台client客户端
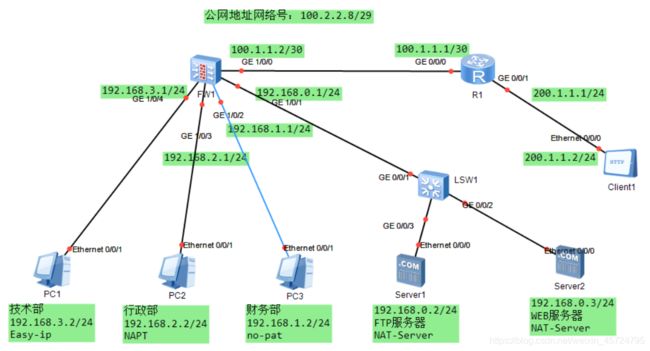
2.拓扑图
3.需求
- 1、ISP为公司分配的公网地址为100.2.2.8/29。
- 2、技术部属于trust区域,通过Easy-ip访问Internet。
- 3、行政部属于trust区域,通过NAPT访问internet(使用100.2.2.12/29)。
- 4、财务部属于trust区域,通过no-pat访问internet(使用100.2.2.10/29-100.2.2.11/29)
- 5、DMZ区域中的两台服务器配置NAT-Server发布,分别提供FTP服务及web服务(使用100.2.2.9/29)
- 6、防护墙的GE1/0/0属于UNtrust区域。
4.详细配置
1)IP地址
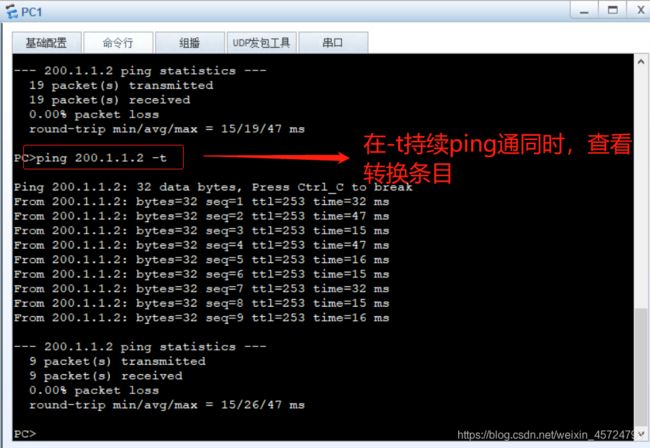
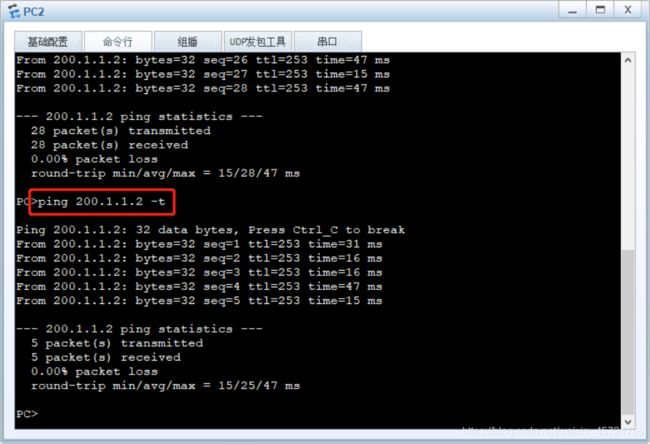
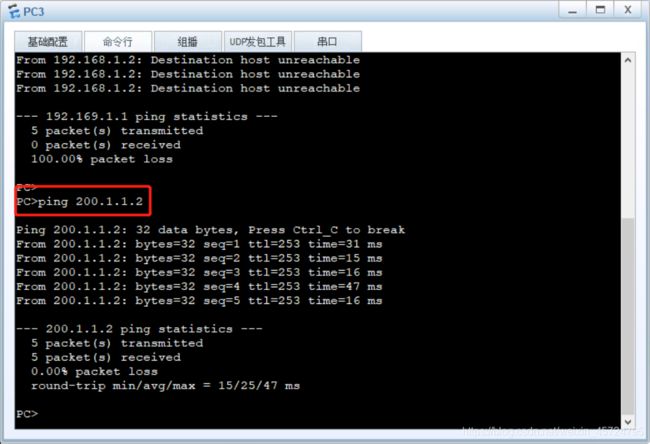
- 将所有PC机和server服务器以及client客户端配上ip地址,点击应用保存即可

- 其他配置都相同,接着进入R1以及防火墙FW1配置IP
- 防火墙配置IP,登录方式可查看上一篇博客华为防火墙理论与管理
[USG6000V1]dis cu
2020-02-13 05:17:57.580
!Software Version V500R005C10SPC300
#
sysname USG6000V1
#
。。。。省略部分内容
interface GigabitEthernet1/0/0
undo shutdown
ip address 100.1.1.2 255.255.255.252
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.0.1 255.255.255.0
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 192.168.2.1 255.255.255.0
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 192.168.3.1 255.255.255.0
#
ip route-static 0.0.0.0 0.0.0.0 100.1.1.1
#
return
- R1配置
[R1]dis cu
#
sysname R1
#
interface GigabitEthernet0/0/0
ip address 100.1.1.1 255.255.255.252
#
interface GigabitEthernet0/0/1
ip address 200.1.1.1 255.255.255.0
#
ip route-static 100.2.2.8 255.255.255.248 100.1.1.2
//该地址为汇总后的地址
#
return
2)server服务器和client客户端配置
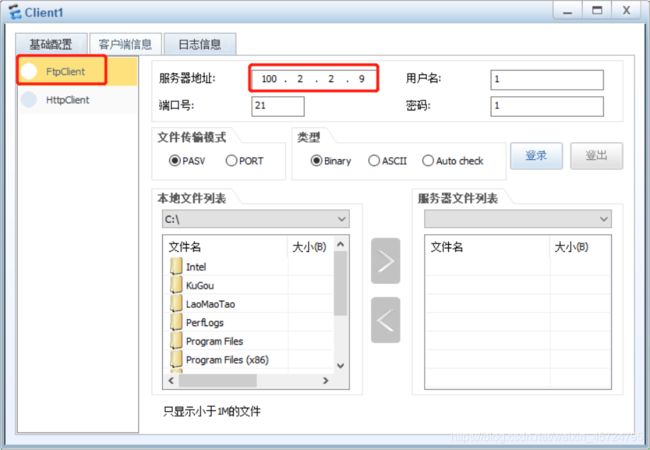
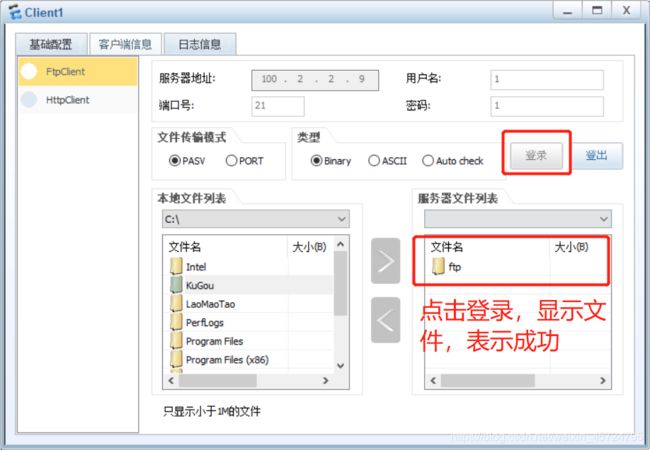
sever-ftp服务器配置
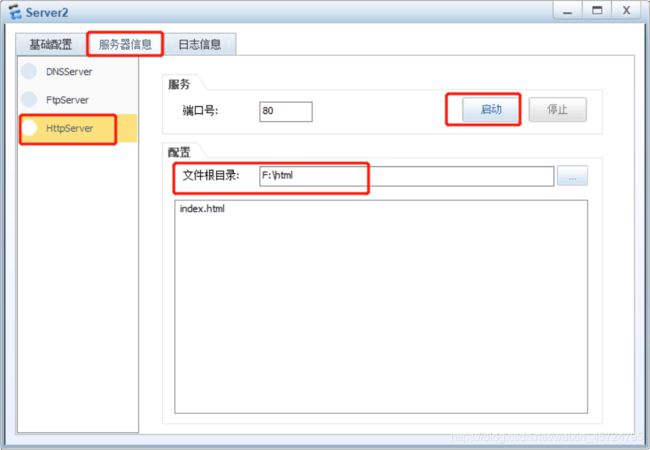
server-http服务器配置
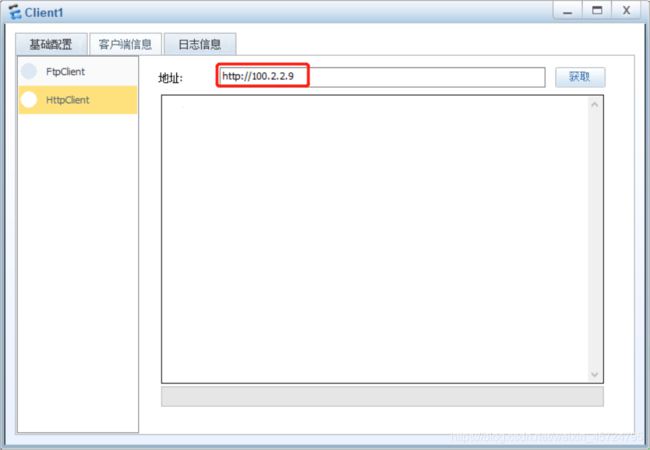
client客户端配置
3)配置防火墙NAT
技术部的防火墙NAT
- 技术部属于trust区域,通过Easy-ip访问Internet
- 先将接口添加到对应区域
[USG6000V1]firewall zone trust //trust区域
[USG6000V1-zone-trust]add in g1/0/4
[USG6000V1-zone-trust]add in g1/0/3
[USG6000V1-zone-trust]add in g1/0/2
[USG6000V1-zone-trust]quit
[USG6000V1]firewall zone dmz //dmz区域
[USG6000V1-zone-dmz]add in g1/0/1
[USG6000V1-zone-dmz]quit
[USG6000V1]firewall zone untrust //untrust区域
[USG6000V1-zone-untrust]add in g1/0/0
- 配置安全策略
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name aqcl //定义安全策略名字
[USG6000V1-policy-security-rule-aqcl]source-zone trust //源区域为trust
[USG6000V1-policy-security-rule-aqcl]destination-zone untrust //目标区域为untrust
[USG6000V1-policy-security-rule-aqcl]action permit //动作为允许
- 配置NAT策略
[USG6000V1]nat-policy
[USG6000V1-policy-nat]rule name natcl 定义NAT策略名字
[USG6000V1-policy-nat-rule-natcl]source-address 192.168.3.0 24 //定义源地址
[USG6000V1-policy-nat-rule-natcl]source-zone trust //定义源区域
[USG6000V1-policy-nat-rule-natcl]destination-zone untrust //定义目标区域
[USG6000V1-policy-nat-rule-natcl]action nat easy-ip //配置出接口方式
[USG6000V1]dis firewall session table //使用dis firewall session table命令查看
2020-02-13 05:48:14.820
Current Total Sessions : 4
icmp VPN: public --> public 192.168.3.2:62177[100.1.1.2:2051] --> 200.1.1.2:2
048
icmp VPN: public --> public 192.168.3.2:61921[100.1.1.2:2050] --> 200.1.1.2:2
048
icmp VPN: public --> public 192.168.3.2:62689[100.1.1.2:2053] --> 200.1.1.2:2
048
icmp VPN: public --> public 192.168.3.2:62433[100.1.1.2:2052] --> 200.1.1.2:2
048
[USG6000V1]
- 注:Easy-ip类型的NAT不会产生server-map
行政部的防火墙NAT
-
配置行政部属于trust区域,通过NAPT访问internet(使用100.2.2.12/29)
-
由于在上面配置Easy-ip的NAT类型时,配置了安全策略,
所以接下来trust区域访问untrust区域的流量就不用配置安全策略了 -
配置NAT地址组,地址组中的地址对应的是公网地址100.2.2.12/29
[USG6000V1]nat address-group napt //定义nat地址组名
[USG6000V1-address-group-napt]section 0 100.2.2.12 //定义组中的地址
[USG6000V1-address-group-napt]mode pat //配置为NAPT方式
[USG6000V1-address-group-napt]quit
- 配置NAT策略
[USG6000V1]nat-policy
[USG6000V1-policy-nat]rule name napt //自定义nat策略的组名
[USG6000V1-policy-nat-rule-napt]source-address 192.168.2.0 24 ####定义需要转换的源地址
[USG6000V1-policy-nat-rule-napt]source-zone trust //定义源区域
[USG6000V1-policy-nat-rule-napt]destination-zone untrust //定义目标区域
[USG6000V1-policy-nat-rule-napt]action source-nat address-group napt //关联地址组
- NAPT的NAT类型要配置黑洞路由,所以要针对转换后的全局地址100.2.2.12/32配置黑洞路由
[USG6000V1] ip route-static 100.2.2.12 32 NULL 0
- NAPT配置至此就完成了,可以自行验证,并查看会话表,查看是否转换为指定的地址
[USG6000V1]dis firewall session table
2020-02-13 07:58:11.940
Current Total Sessions : 5
icmp VPN: public --> public 192.168.2.2:26877[100.2.2.12:2067] --> 200.1.1.2:
2048
icmp VPN: public --> public 192.168.2.2:28413[100.2.2.12:2072] --> 200.1.1.2:
2048
icmp VPN: public --> public 192.168.2.2:27133[100.2.2.12:2068] --> 200.1.1.2:
2048
icmp VPN: public --> public 192.168.2.2:28669[100.2.2.12:2073] --> 200.1.1.2:
2048
icmp VPN: public --> public 192.168.2.2:30973[100.2.2.12:2079] --> 200.1.1.2:
2048
财务部的防火墙NAT
-
配置财务部属于trust区域,通过no-pat访问internet(使用100.2.2.10/29-100.2.2.11/29)
-
配置NAT地址组,地址组中的地址对应的是公网地址100.2.2.10–100.2.2.11
[USG6000V1]nat address-group natnopat //定义nat地址组名
[USG6000V1-address-group-natnopat]section 0 100.2.2.10 100.2.2.11 //定义组中的地址
[USG6000V1-address-group-natnopat]mode no-pat local //配置为NAT No-PAT方式
[USG6000V1-address-group-natnopat]quit
- 配置NAT策略
[USG6000V1]nat-policy
[USG6000V1-policy-nat]rule name nopat //自定义nat策略的组名
[USG6000V1-policy-nat-rule-nopat]source-address 192.168.1.0 24 //定义需要转换的源地址
[USG6000V1-policy-nat-rule-nopat]source-zone trust //定义源区域
[USG6000V1-policy-nat-rule-nopat]destination-zone untrust //定义目标区域
[USG6000V1-policy-nat-rule-nopat]action source-nat address-group natnopat //关联地址组
[USG6000V1-policy-nat-rule-nopat]quit
- 针对转换后的全局地址(NAT地址组中的地址)配置黑洞路由
[USG6000V1]ip route-static 100.2.2.10 32 NULL 0
[USG6000V1]ip route-static 100.2.2.11 32 NULL 0
[USG6000V1]dis firewall session table //查看会话表
2020-02-13 08:16:46.280
Current Total Sessions : 5
icmp VPN: public --> public 192.168.1.2:22017[100.2.2.10:22017] --> 200.1.1.2
:2048
icmp VPN: public --> public 192.168.1.2:22785[100.2.2.10:22785] --> 200.1.1.2
:2048
icmp VPN: public --> public 192.168.1.2:22529[100.2.2.10:22529] --> 200.1.1.2
:2048
icmp VPN: public --> public 192.168.1.2:23041[100.2.2.10:23041] --> 200.1.1.2
:2048
icmp VPN: public --> public 192.168.1.2:22273[100.2.2.10:22273] --> 200.1.1.2
:2048
[USG6000V1]dis firewall server-map //查看server-map表
2020-02-13 08:17:47.660
Current Total Server-map : 2
Type: No-Pat Reverse, ANY -> 100.2.2.10[192.168.1.2], Zone: untrust
Protocol: ANY, TTL:---, Left-Time:---, Pool: 1, Section: 0
Vpn: public
Type: No-Pat, 192.168.1.2[100.2.2.10] -> ANY, Zone: untrust
Protocol: ANY, TTL:360, Left-Time:311, Pool: 1, Section: 0
Vpn: public
配置DMZ区域中的两台服务器
- 配置DMZ区域中的两台服务器配置NAT-Server发布,分别提供FTP服务及web服务(使用100.2.2.9/29)
- 配置安全策略
- 由于之前配置的是trust访问untrust区域的安全策略,所以对DMZ区域没关系,这里是要将DMZ区域的服务器发布出去,使Internet用户可以访问到这些服务器,所以应该放行UNtrust到DMZ区域相关服务的流量
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name todmz
[USG6000V1-policy-security-rule-todmz]source-zone untrust
[USG6000V1-policy-security-rule-todmz]destination-zone dmz
[USG6000V1-policy-security-rule-todmz]destination-address 192.168.0.0 24
[USG6000V1-policy-security-rule-todmz]service ftp
[USG6000V1-policy-security-rule-todmz]service http
[USG6000V1-policy-security-rule-todmz]action permit
- 配置NAT server
[USG6000V1]nat server ftp protocol tcp global 100.2.2.9 21 inside 192.168.0.2 21
[USG6000V1]nat server http protocol tcp global 100.2.2.9 80 inside 192.168.0.3 80
[USG6000V1]dis firewall session table
2020-02-13 08:46:51.680
Current Total Sessions : 3
ftp VPN: public --> public 200.1.1.2:2055 +-> 100.2.2.9:21[192.168.0.2:21]
http VPN: public --> public 200.1.1.2:2057 --> 100.2.2.9:80[192.168.0.3:80]
ftp VPN: public --> public 200.1.1.2:2053 +-> 100.2.2.9:21[192.168.0.2:21]
[USG6000V1]dis firewall server-map
2020-02-13 08:48:09.740
Current Total Server-map : 4
Type: Nat Server, ANY -> 100.2.2.9:80[192.168.0.3:80], Zone:---, protocol:tc
p
Vpn: public -> public
Type: Nat Server, ANY -> 100.2.2.9:21[192.168.0.2:21], Zone:---, protocol:tc
p
Vpn: public -> public
Type: Nat Server Reverse, 192.168.0.2[100.2.2.9] -> ANY, Zone:---, protocol:
tcp
Vpn: public -> public, counter: 1
Type: Nat Server Reverse, 192.168.0.3[100.2.2.9] -> ANY, Zone:---, protocol:
tcp
Vpn: public -> public, counter: 1