ciscn 2020 reverse z3
z3
start
shift+F12找到
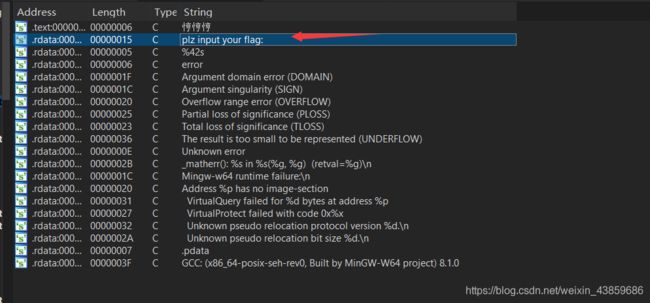
查看引用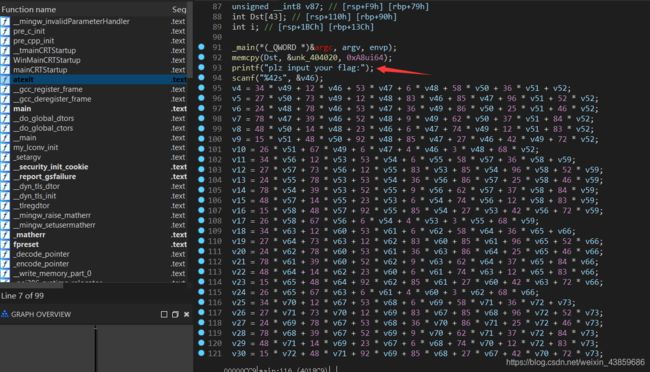
往下拉看到关键比较:

发现Dst来自:
memcpy(Dst, &unk_404020, 0xA8ui64);
找到加密后的字符串,这里注意是int类型的,并且是小端存储的,所以17 4F 0 0 应该读成0x00004F17
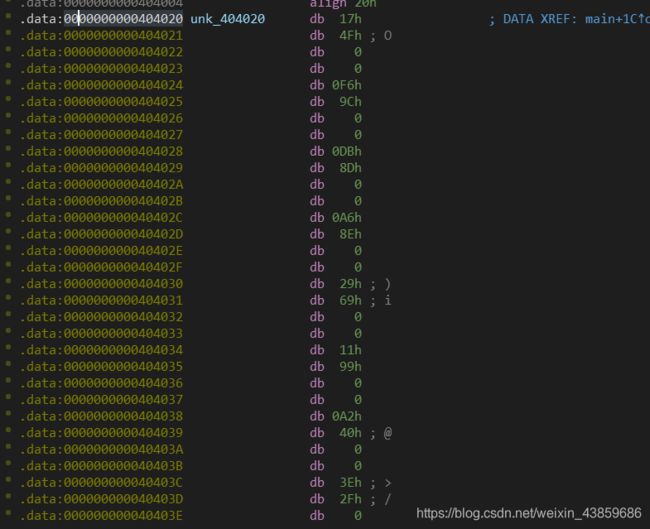
整理后就可以得到完整的加密后的字符串
随后看到那一大堆乱七八糟的加密

发现规律,6个七元一次方程,解出42个字符即为flag
exp.py
import numpy as np
from scipy.linalg import solve
def decrypt(a1, b1):
x = solve(a1, b1)
#print(type(x))
flag = ''
for i in range(7):
tmp1 = x[i].astype(int)
if x[i] - tmp1 >= 0.5 :
flag += chr(tmp1+1)
else:
flag += chr(tmp1)
return flag
# 第一个方程组
a1 = np.array(
[[12,53,6,34,58,36,1],
[83,85,12,73,27,96,52],
[78,53,24,36,86,25,46],
[39,78,52,9,62,37,84],
[23,6,14,74,48,12,83],
[27,85,92,42,48,15,72],
[4,6,3,67,0,26,68]])
b1 = np.array([20247, 40182, 36312, 36518, 26921, 39185, 16546])
# 第二个方程组
a2 = np.array(
[[12, 53, 6, 34, 58, 36, 1],
[83, 85, 12, 73, 27, 96, 52],
[78, 53, 24, 36, 86, 25, 46],
[39, 78, 52, 9, 62, 37, 84],
[23, 6, 14, 74, 48, 12, 83],
[27, 85, 92, 42, 48, 15, 72],
[4, 6, 3, 67, 0, 26, 68]])
b2 = np.array([12094, 25270, 19330, 18540, 16386, 21207, 11759])
# 第三个方程组
a3 = np.array([
[12,53,6,34,58,36,1],
[83,85,12,73,27,96,52],
[78,53,24,36,86,25,46],
[39,78,52,9,62,37,84],
[23,6,14,74,48,12,83],
[27,85,92,42,48,15,72],
[4,6,3,67,0,26,68]
])
b3 = np.array([10460, 25613, 21135, 24891, 18305, 27415, 12855])
# 第四个方程组
a4 = np.array([
[12,53,6,34,58,36,1],
[83,85,12,73,27,96,52],
[78,53,24,36,86,25,46],
[39,78,52,9,62,37,84],
[23,6,14,74,48,12,83],
[27,85,92,42,48,15,72],
[4,6,3,67,0,26,68]
])
b4 = np.array([10899, 24927, 20670, 22926, 18006, 23345, 12602])
# 第五个方程组
a5 = np.array([
[12,53,6,34,58,36,1],
[83,85,12,73,27,96,52],
[78,53,24,36,86,25,46],
[39,78,52,9,62,37,84],
[23,6,14,74,48,12,83],
[27,85,92,42,48,15,72],
[4,6,3,67,0,26,68]
])
b5 = np.array([12304, 26622, 19807, 22747, 14233, 24736, 10064])
# 第六个方程组
a6 = np.array([
[12,53,6,34,58,36,1],
[83,85,12,73,27,96,52],
[78,53,24,36,86,25,46],
[39,78,52,9,62,37,84],
[23,6,14,74,48,12,83],
[27,85,92,42,48,15,72],
[4,6,3,67,0,26,68]
])
b6 = np.array([14169, 35155, 28962, 33273, 21796, 35185, 14877])
flag1 = decrypt(a1, b1)
flag2 = decrypt(a2, b2)
flag3 = decrypt(a3, b3)
flag4 = decrypt(a4, b4)
flag5 = decrypt(a5, b5)
flag6 = decrypt(a6, b6)
print(flag1 + flag2 + flag3 + flag4 + flag5 + flag6)
# flag{7e171d43-63b9-4e18-990e-6e14c2afe648}
ps: 这道题不到十分钟就被师傅们解出来了,我这土方法用了快一个小时了。QAQ