VulnHub打靶のLazySysAdmin
靶机地址: https://drive.google.com/uc?id=0B_A-fCfoBmkLOXN5Y1ZmZnpDQTQ&export=download
nmap -sP 或netdiscover -r 扫描目标机:这里192.168.1.159为目标机。
nmap开路扫描全端口:
root@Kali-X86:~# nmap -sV -p- 192.168.1.159
Starting Nmap 7.70 ( https://nmap.org ) at 2018-10-09 13:10 CST
Nmap scan report for 192.168.1.159
Host is up (0.00049s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
3306/tcp open mysql MySQL (unauthorized)
6667/tcp open irc InspIRCd
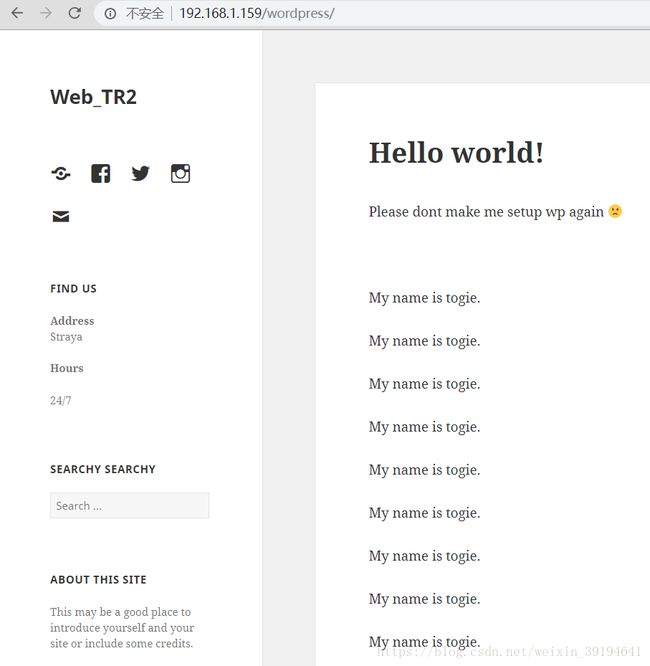
目标机开启着ssh,http,smb服务,访问http找一下flag:
首页与页面源代码无任何线索,用dirb爆破目录:找到phpmyadmin,wordpress目录,访问wordpress:
用wpscan扫描:
root@Kali-X86:~# wpscan -u 192.168.1.159/wordpress
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 2.9.4
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[i] It seems like you have not updated the database for some time
[i] Last database update: 2018-08-18
[?] Do you want to update now? [Y]es [N]o [A]bort update, default: [N] >
[+] URL: http://192.168.1.159/wordpress/
[+] Started: Tue Oct 9 13:19:52 2018
[+] Interesting header: LINK:
[+] Interesting header: SERVER: Apache/2.4.7 (Ubuntu)
[+] Interesting header: X-POWERED-BY: PHP/5.5.9-1ubuntu4.22
[+] XML-RPC Interface available under: http://192.168.1.159/wordpress/xmlrpc.php [HTTP 405]
[+] Found an RSS Feed: http://192.168.1.159/wordpress/?feed=rss2 [HTTP 200]
[!] Detected 1 user from RSS feed:
+-------+
| Name |
+-------+
| Admin |
+-------+
[!] Upload directory has directory listing enabled: http://192.168.1.159/wordpress/wp-content/uploads/
[!] Includes directory has directory listing enabled: http://192.168.1.159/wordpress/wp-includes/
[+] Enumerating WordPress version ...
[+] WordPress version 4.8.1 (Released on 2017-08-02) identified from advanced fingerprinting, meta generator, links opml, stylesheets numbers
[!] 18 vulnerabilities identified from the version number
[!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection
Reference: https://wpvulndb.com/vulnerabilities/8905
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48
Reference: https://github.com/WordPress/WordPress/commit/fc930d3daed1c3acef010d04acc2c5de93cd18ec
[i] Fixed in: 4.8.2
[!] Title: WordPress 2.9.2-4.8.1 - Open Redirect
Reference: https://wpvulndb.com/vulnerabilities/8910
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/changeset/41398
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14725
[i] Fixed in: 4.8.2
[!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping
Reference: https://wpvulndb.com/vulnerabilities/8911
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/changeset/41457
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14719
[i] Fixed in: 4.8.2
[!] Title: WordPress 4.4-4.8.1 - Path Traversal in Customizer
Reference: https://wpvulndb.com/vulnerabilities/8912
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/changeset/41397
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14722
[i] Fixed in: 4.8.2
[!] Title: WordPress 4.4-4.8.1 - Cross-Site Scripting (XSS) in oEmbed
Reference: https://wpvulndb.com/vulnerabilities/8913
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/changeset/41448
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14724
[i] Fixed in: 4.8.2
[!] Title: WordPress 4.2.3-4.8.1 - Authenticated Cross-Site Scripting (XSS) in Visual Editor
Reference: https://wpvulndb.com/vulnerabilities/8914
Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/changeset/41395
Reference: https://blog.sucuri.net/2017/09/stored-cross-site-scripting-vulnerability-in-wordpress-4-8-1.html
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14726
[i] Fixed in: 4.8.2
[!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset
Reference: https://wpvulndb.com/vulnerabilities/8807
Reference: https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html
Reference: http://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html
Reference: https://core.trac.wordpress.org/ticket/25239
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295
[!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness
Reference: https://wpvulndb.com/vulnerabilities/8941
Reference: https://wordpress.org/news/2017/10/wordpress-4-8-3-security-release/
Reference: https://github.com/WordPress/WordPress/commit/a2693fd8602e3263b5925b9d799ddd577202167d
Reference: https://twitter.com/ircmaxell/status/923662170092638208
Reference: https://blog.ircmaxell.com/2017/10/disclosure-wordpress-wpdb-sql-injection-technical.html
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16510
[i] Fixed in: 4.8.3
[!] Title: WordPress 2.8.6-4.9 - Authenticated JavaScript File Upload
Reference: https://wpvulndb.com/vulnerabilities/8966
Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/67d03a98c2cae5f41843c897f206adde299b0509
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17092
[i] Fixed in: 4.8.4
[!] Title: WordPress 1.5.0-4.9 - RSS and Atom Feed Escaping
Reference: https://wpvulndb.com/vulnerabilities/8967
Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/f1de7e42df29395c3314bf85bff3d1f4f90541de
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17094
[i] Fixed in: 4.8.4
[!] Title: WordPress 4.3.0-4.9 - HTML Language Attribute Escaping
Reference: https://wpvulndb.com/vulnerabilities/8968
Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/3713ac5ebc90fb2011e98dfd691420f43da6c09a
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17093
[i] Fixed in: 4.8.4
[!] Title: WordPress 3.7-4.9 - 'newbloguser' Key Weak Hashing
Reference: https://wpvulndb.com/vulnerabilities/8969
Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/eaf1cfdc1fe0bdffabd8d879c591b864d833326c
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17091
[i] Fixed in: 4.8.4
[!] Title: WordPress 3.7-4.9.1 - MediaElement Cross-Site Scripting (XSS)
Reference: https://wpvulndb.com/vulnerabilities/9006
Reference: https://github.com/WordPress/WordPress/commit/3fe9cb61ee71fcfadb5e002399296fcc1198d850
Reference: https://wordpress.org/news/2018/01/wordpress-4-9-2-security-and-maintenance-release/
Reference: https://core.trac.wordpress.org/ticket/42720
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-5776
[i] Fixed in: 4.8.5
[!] Title: WordPress <= 4.9.4 - Application Denial of Service (DoS) (unpatched)
Reference: https://wpvulndb.com/vulnerabilities/9021
Reference: https://baraktawily.blogspot.fr/2018/02/how-to-dos-29-of-world-wide-websites.html
Reference: https://github.com/quitten/doser.py
Reference: https://thehackernews.com/2018/02/wordpress-dos-exploit.html
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-6389
[!] Title: WordPress 3.7-4.9.4 - Remove localhost Default
Reference: https://wpvulndb.com/vulnerabilities/9053
Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/804363859602d4050d9a38a21f5a65d9aec18216
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10101
[i] Fixed in: 4.8.6
[!] Title: WordPress 3.7-4.9.4 - Use Safe Redirect for Login
Reference: https://wpvulndb.com/vulnerabilities/9054
Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/14bc2c0a6fde0da04b47130707e01df850eedc7e
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10100
[i] Fixed in: 4.8.6
[!] Title: WordPress 3.7-4.9.4 - Escape Version in Generator Tag
Reference: https://wpvulndb.com/vulnerabilities/9055
Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/
Reference: https://github.com/WordPress/WordPress/commit/31a4369366d6b8ce30045d4c838de2412c77850d
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10102
[i] Fixed in: 4.8.6
[!] Title: WordPress <= 4.9.6 - Authenticated Arbitrary File Deletion
Reference: https://wpvulndb.com/vulnerabilities/9100
Reference: https://blog.ripstech.com/2018/wordpress-file-delete-to-code-execution/
Reference: http://blog.vulnspy.com/2018/06/27/Wordpress-4-9-6-Arbitrary-File-Delection-Vulnerbility-Exploit/
Reference: https://github.com/WordPress/WordPress/commit/c9dce0606b0d7e6f494d4abe7b193ac046a322cd
Reference: https://wordpress.org/news/2018/07/wordpress-4-9-7-security-and-maintenance-release/
Reference: https://www.wordfence.com/blog/2018/07/details-of-an-additional-file-deletion-vulnerability-patched-in-wordpress-4-9-7/
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12895
[i] Fixed in: 4.8.7
[+] WordPress theme in use: twentyfifteen - v1.8
[+] Name: twentyfifteen - v1.8
| Last updated: 2018-05-17T00:00:00.000Z
| Location: http://192.168.1.159/wordpress/wp-content/themes/twentyfifteen/
| Readme: http://192.168.1.159/wordpress/wp-content/themes/twentyfifteen/readme.txt
[!] The version is out of date, the latest version is 2.0
| Style URL: http://192.168.1.159/wordpress/wp-content/themes/twentyfifteen/style.css
| Theme Name: Twenty Fifteen
| Theme URI: https://wordpress.org/themes/twentyfifteen/
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple,...
| Author: the WordPress team
| Author URI: https://wordpress.org/
[+] Enumerating plugins from passive detection ...
[+] No plugins found passively
enum4linux进行枚举:
root@Kali-X86:~# enum4linux 192.168.1.159
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Tue Oct 9 13:23:32 2018
==========================
| Target Information |
==========================
Target ........... 192.168.1.159
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
=====================================================
| Enumerating Workgroup/Domain on 192.168.1.159 |
=====================================================
[+] Got domain/workgroup name: WORKGROUP
=============================================
| Nbtstat Information for 192.168.1.159 |
=============================================
Looking up status of 192.168.1.159
LAZYSYSADMIN <00> - B
LAZYSYSADMIN <03> - B
LAZYSYSADMIN <20> - B
WORKGROUP <00> -
WORKGROUP <1e> -
MAC Address = 00-00-00-00-00-00
======================================
| Session Check on 192.168.1.159 |
======================================
[+] Server 192.168.1.159 allows sessions using username '', password ''
============================================
| Getting domain SID for 192.168.1.159 |
============================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
=======================================
| OS information on 192.168.1.159 |
=======================================
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for 192.168.1.159 from smbclient:
[+] Got OS info for 192.168.1.159 from srvinfo:
LAZYSYSADMIN Wk Sv PrQ Unx NT SNT Web server
platform_id : 500
os version : 6.1
server type : 0x809a03
==============================
| Users on 192.168.1.159 |
==============================
Use of uninitialized value $users in print at ./enum4linux.pl line 874.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 877.
Use of uninitialized value $users in print at ./enum4linux.pl line 888.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 890.
==========================================
| Share Enumeration on 192.168.1.159 |
==========================================
WARNING: The "syslog" option is deprecated
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
share$ Disk Sumshare
IPC$ IPC IPC Service (Web server)
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP LAZYSYSADMIN
[+] Attempting to map shares on 192.168.1.159
//192.168.1.159/print$ Mapping: DENIED, Listing: N/A
//192.168.1.159/share$ Mapping: OK, Listing: OK
//192.168.1.159/IPC$ [E] Can't understand response:
WARNING: The "syslog" option is deprecated
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
=====================================================
| Password Policy Information for 192.168.1.159 |
=====================================================
[+] Attaching to 192.168.1.159 using a NULL share
[+] Trying protocol 445/SMB...
[+] Found domain(s):
[+] LAZYSYSADMIN
[+] Builtin
[+] Password Info for Domain: LAZYSYSADMIN
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
===============================
| Groups on 192.168.1.159 |
===============================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
可见用username=‘’&password=''可访问$share:
smbclient //192.168.1.159/share$
root@Kali-X86:~# smbclient //192.168.1.159/share$
WARNING: The "syslog" option is deprecated
Enter WORKGROUP\root's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Aug 15 19:05:52 2017
.. D 0 Mon Aug 14 20:34:47 2017
wordpress D 0 Tue Aug 15 19:21:08 2017
Backnode_files D 0 Mon Aug 14 20:08:26 2017
wp D 0 Tue Aug 15 18:51:23 2017
deets.txt N 139 Mon Aug 14 20:20:05 2017
robots.txt N 92 Mon Aug 14 20:36:14 2017
todolist.txt N 79 Mon Aug 14 20:39:56 2017
apache D 0 Mon Aug 14 20:35:19 2017
index.html N 36072 Sun Aug 6 13:02:15 2017
info.php N 20 Tue Aug 15 18:55:19 2017
test D 0 Mon Aug 14 20:35:10 2017
old D 0 Mon Aug 14 20:35:13 2017
3029776 blocks of size 1024. 1459464 blocks available
smb: \>
查看deets.txt与todolist.txt提示密码是12345
进入wordpress看看配置文件的信息:
发现wp-config.php,查看发现数据库账号密码为Admin,TogieMYSQL12345^^。
root@Kali-X86:~# cat wp-config.php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the
* installation. You don't have to use the web site, you can
* copy this file to "wp-config.php" and fill in the values.
*
* This file contains the following configurations:
*
* * MySQL settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://codex.wordpress.org/Editing_wp-config.php
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'Admin');
/** MySQL database password */
define('DB_PASSWORD', 'TogieMYSQL12345^^');
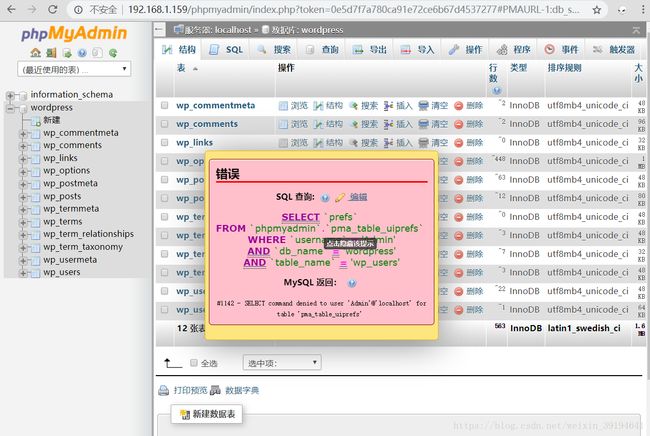
登陆phpmyadmin:
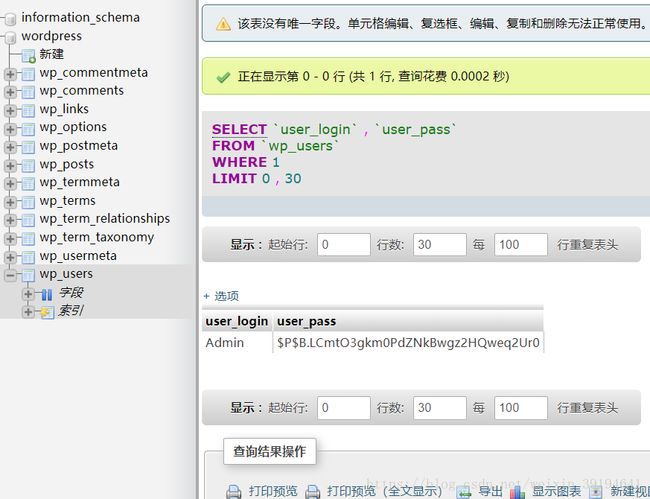
好吧,尝试手动写sql命令:
尝试用用Admin与TogieMYSQL12345^^登陆wordpress成功,在404编辑页面加入php反弹shell获得webshell,用CVE-2017-1000112提权。
参考链接:VulnHub Walk-through – LazySysAdmin: 1