sum-check protocol in zkproof
1. 引言
sum-check protocol首次由Lund等人在1992年论文《Algebraic Methods for Interactive Proof Systems》中提出。
sum-check protocol的价值在当前的ZKProofs community是被低估了的,被低估的原因主要有:
- sum-check protocol 的proof size至少为logarithmic length,对于区块链等对存储敏感的应用,关注的是能提供super short proofs的算法(如 Gennaro等人2012年论文《Quadratic Span Programs and Succinct NIZKs without PCPs》基于pairing的zkSNARKs算法可提供constant proof length)。
- sum-check protocol本身并既不具有zero-knowledge属性,也不具有“succinct for NP statements”。即对于NP statements,通过sum-check protocol实现的proof length is not sublinear in the size of the NP witness。
当前有强证据表明,对于NP statements,不存在succinct interactive proof。这不同于argument system,对于argument system,仅具有computationally sound。
要点:
- 借助sum-check protocol可实现super-efficient IP for matrix-powering。如已知任意的 n × n n\times n n×n矩阵 A A A over field F \mathbf{F} F,该IP可计算any desired entry of the powered matrix A k A^k Ak。整个IP的round和communication cost为 O ( log ( k ) ⋅ log n ) O(\log(k)\cdot \log n) O(log(k)⋅logn),而verifier的runtime为 O ( n 2 + log ( k ) ⋅ log n ) O(n^2+\log(k)\cdot \log n) O(n2+log(k)⋅logn)。
- Goldwasser, Kalai和Rothblum (GKR) 2008年论文《Delegating Computation: Interactive Proofs for Muggles》中正是利用了matrix-powering protocol 实现了arithmetic circuit证明。
近几年的研究中指出,将sum-check protocol与cryptographic commitments结合,可实现arguments——同时具有zero-knowledge属性和succinct for NP statements。实现的相关zk-SNARKs具有state of the art performance,如Hyrax, zk-VSQL, Libra, Virgo, Spartan。
若对zk-SNARKs感兴趣且对具有logarithmic length的proof size满意,可对sum-check protocol进行深入学习。
本文主要关注的是interactive proofs (IPs),关注的场景为:
Verifier V V V 将 expensive computation 外包给 an untrusted prover P P P,从而节约verifier的工作量。
要求:
- verifier V V V的验证工作量为run in time linear in the input size。
- proof size 为short的(logarithmic size)。
- prover P P P 为efficient的。
1.1 多项式及其low-degree extension
- polynomial G \mathcal{G} G over F \mathbb{F} F 表示的是:
monomials(单项式)之和
其中每个单项式是 the product of a constant (from F \mathbb{F} F) and powers of one or more variables (which take values from F \mathbb{F} F)。所有的计算都performed over F \mathbb{F} F。 - 单项式的degree为:the sum of the exponents of variables in the monomial。
- 多项式的degree为:the maximum degree of any monomial in G \mathcal{G} G。
- 多项式的degree in a particular variable x i x_i xi为:the maximum exponent that x i x_i xi takes in any of the monomials in G \mathcal{G} G。
- 多变量多项式是指:具有不只一个变量的多项式。只有一个变量的多项式称为univariate polynomial单变量多项式。
- multilinear polynomial是指:多变量多项式的任一变量的degree均不大于1.
- low-degree polynomial是指:多变量多项式 G \mathcal{G} G over a finite field F \mathbb{F} F 的degree in each variable is exponentially smaller than ∣ F ∣ |\mathbb{F}| ∣F∣。
- Low-degree extensions (LDEs)是指:假设 g : { 0 , 1 } m → F g:\{0,1\}^m\rightarrow \mathbb{F} g:{ 0,1}m→F为a function that maps m m m-bit elements into an element of F \mathbb{F} F。 A polynomial extension of g g g is a low-degree m m m-variate polynomial g ~ ( ⋅ ) \tilde{g}(\cdot) g~(⋅) 使得 g ~ ( x ) = g ( x ) \tilde{g}(x)=g(x) g~(x)=g(x) for all x ∈ { 0 , 1 } m x\in\{0,1\}^m x∈{ 0,1}m。
【若 g ~ ( x ) \tilde{g}(x) g~(x)为multilinear polynomial (degree at most 1 in each variable),则low-degree extension也可成为multilinear polynomial extension。】 - multilinear polynomial extension (简称为MLE) 是指:Given a function Z : { 0 , 1 } m → F Z:\{0,1\}^m\rightarrow \mathbb{F} Z:{ 0,1}m→F,the multilinear extension of Z ( ⋅ ) Z(\cdot) Z(⋅) is the unique multilinear polynomial Z ~ : F m → F \tilde{Z}: \mathbb{F}^m\rightarrow \mathbb{F} Z~:Fm→F。计算方式为:
Z ~ ( x 1 , ⋯ , x m ) = ∑ e ∈ { 0 , 1 } m Z ( e ) ⋅ ∏ i = 1 m ( x i ⋅ e i + ( 1 − x i ) ⋅ ( 1 − e i ) ) = ∑ e ∈ { 0 , 1 } m Z ( e ) ⋅ e q ~ ( x , e ) = < ( Z ( 0 ) , ⋯ , Z ( 2 m − 1 ) ) , ( e q ~ ( x , 0 ) , ⋯ , e q ~ ( x , 2 m − 1 ) ) > \tilde{Z}(x_1,\cdots,x_m)=\sum_{e\in\{0,1\}^m}Z(e)\cdot \prod_{i=1}^{m}(x_i\cdot e_i+(1-x_i)\cdot (1-e_i))=\sum_{e\in\{0,1\}^m}Z(e)\cdot \tilde{eq}(x,e)=<(Z(0),\cdots,Z(2^m-1)), (\tilde{eq}(x,0),\cdots, \tilde{eq}(x,2^m-1))> Z~(x1,⋯,xm)=∑e∈{ 0,1}mZ(e)⋅∏i=1m(xi⋅ei+(1−xi)⋅(1−ei))=∑e∈{ 0,1}mZ(e)⋅eq~(x,e)=<(Z(0),⋯,Z(2m−1)),(eq~(x,0),⋯,eq~(x,2m−1))>
其中 e q ~ ( x , e ) = ∏ i = 1 m ( e i ⋅ x i + ( 1 − e i ) ⋅ ( 1 − x i ) ) \tilde{eq}(x,e)=\prod_{i=1}^{m}(e_i\cdot x_i+(1-e_i)\cdot (1-x_i)) eq~(x,e)=∏i=1m(ei⋅xi+(1−ei)⋅(1−xi)), e q ~ ( x , e ) \tilde{eq}(x,e) eq~(x,e) is the MLE of the following function:
e q ( x , e ) = { 1 if x=e 0 otherwise eq(x,e)= \left\{\begin{matrix} 1 & \text{if x=e} \\ 0 &\text{otherwise} \end{matrix}\right. eq(x,e)={ 10if x=eotherwise
对于任一的 r ∈ F m r\in\mathbb{F}^m r∈Fm,可在 O ( 2 m ) O(2^m) O(2m)次operations in F \mathbb{F} F 之内计算出 Z ~ ( r ) \tilde{Z}(r) Z~(r)的值。
由于a function的MLE是唯一的,因此MLE可用于represent 任意的multilinear polynomial。对于a multilinear polynomial G ( ⋅ ) : F m → F \mathcal{G}(\cdot):\mathbb{F}^m\rightarrow \mathbb{F} G(⋅):Fm→F,可唯一表示为 the list of evaluations of G ( ⋅ ) \mathcal{G}(\cdot) G(⋅) over the Boolean hypercube { 0 , 1 } m \{0,1\}^m { 0,1}m (如a function that maps { 0 , 1 } m → F \{0,1\}^m\rightarrow \mathbb{F} { 0,1}m→F)。
其中关键的技术点——multilinear extension lemma(follow from Lagrange interpolation):【引入multilinear extension可ensure fast computation for the prover。】
设 f : { 0 , 1 } n → F f:\{0,1\}^n\rightarrow \mathbf{F} f:{ 0,1}n→F,则存在唯一的multilinear polynomial f ~ \tilde{f} f~ over F \mathbf{F} F 使得 f ~ ( x ) = f ( x ) \tilde{f}(x)=f(x) f~(x)=f(x) for all x ∈ { 0 , 1 } n x\in\{0,1\}^n x∈{ 0,1}n。
f ~ \tilde{f} f~称为the multilinear extension (MLE) of f f f。
若已知a list of all 2 n 2^n 2n evaluations of f f f 和 an arbitrary point r ⃗ ∈ F n \vec{r}\in\mathbf{F}^n r∈Fn,则存在an algorithm that can evaluate f ~ ( r ⃗ ) \tilde{f}(\vec{r}) f~(r) in O ( 2 n ) O(2^n) O(2n) time。
2. the sum-check protocol
有:
v v v-variate polynomial g g g defined over a finite field F \mathbf{F} F。
此处约定 g g g具有degree at most 2 in each variable。【而对于multilinear polynomial,则要求degree at most 1 1 1 in each variable。】
sum-check protocol的主要目标是求和:
H : = ∑ b 1 ∈ { 0 , 1 } ∑ b 2 ∈ { 0 , 1 } ⋯ ∑ b v ∈ { 0 , 1 } g ( b 1 , ⋯ , b v ) H:=\sum_{b_1\in\{0,1\}}\sum_{b_2\in\{0,1\}}\cdots\sum_{b_v\in\{0,1\}}g(b_1,\cdots,b_v) H:=∑b1∈{ 0,1}∑b2∈{ 0,1}⋯∑bv∈{ 0,1}g(b1,⋯,bv) ……(1)
以上(1)方程式本质是 sum up the evaluations of a polynomial over all Boolean inputs,初看该求和似乎并不实用,但是后续介绍中会指出many natural problems可转化为an inatance of Equation (1)。
【借助sum-check protocol,Verifier不需要evaluate the entire boolean hypercube to verify the claim。相反的,Verifier仅需选择random points ( r 1 , r 2 , r v ) (r_1,r_2,r_v) (r1,r2,rv)。】
![]()
为了便于理解,可假设Verifier具有oracle access to g g g,即 V V V可evaluate g ( r 1 , ⋯ , r v ) g(r_1,\cdots,r_v) g(r1,⋯,rv) for a randomly chosen vector ( r 1 , ⋯ , r v ) ∈ F v (r_1,\cdots,r_v)\in\mathbf{F}^v (r1,⋯,rv)∈Fv with a single query to an oracle,尽管在实际应用中该假设不成立。实际应用中, V V V可自己efficiently evaluate g ( r 1 , ⋯ , r v ) g(r_1,\cdots,r_v) g(r1,⋯,rv),或者要求Prover告诉它 g ( r 1 , ⋯ , r v ) g(r_1,\cdots,r_v) g(r1,⋯,rv)的结果值的同时, P P P提供该结果值正确的证明(借助the sum-checkprotocol)。
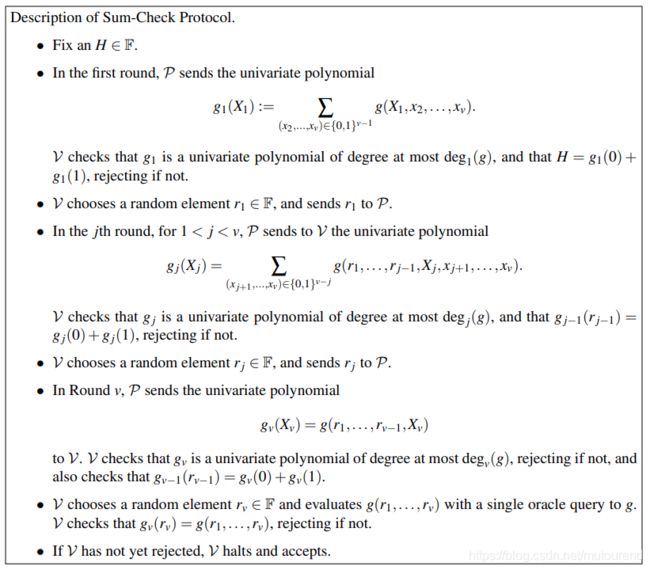
整个sum-check protocol包含 v v v轮,每一轮对应 g g g中的一个变量。
第1轮:
- Prover:发送polynomial g 1 ( X 1 ) g_1(X_1) g1(X1),同时声明 g 1 ( X 1 ) = ∑ x 2 , ⋯ , x v ∈ { 0 , 1 } v − 1 g ( X 1 , x 2 , ⋯ , x v ) g_1(X_1)=\sum_{x_2,\cdots,x_v}\in\{0,1\}^{v-1}g(X_1,x_2,\cdots,x_v) g1(X1)=∑x2,⋯,xv∈{ 0,1}v−1g(X1,x2,⋯,xv)。
若 g 1 g_1 g1是正确的,则有 H = g 1 ( 0 ) + g 1 ( 1 ) H=g_1(0)+g_1(1) H=g1(0)+g1(1)。
【本文约定了该单变量多项式degree为不高于 2 2 2, g j ( X j ) = c 0 , j + c 1 , j X i + c 2 , j X i 2 g_j(X_j)=c_{0,j}+c_{1,j}X_i+c_{2,j}X_i^2 gj(Xj)=c0,j+c1,jXi+c2,jXi2,可以系数 ( c 0 , j , c 1 , j , c 2 , j ) (c_{0,j},c_{1,j},c_{2,j}) (c0,j,c1,j,c2,j)来表示多项式 g j g_j gj,或者以 [ ( b 1 , g j ( b 1 ) ) , ( b 2 , g j ( b 2 ) ) , ( b 3 , g j ( b 3 ) ) ] [(b_1,g_j(b_1)),(b_2,g_j(b_2)),(b_3,g_j(b_3))] [(b1,gj(b1)),(b2,gj(b2)),(b3,gj(b3))] 这样的3组eavaluations值 来表示。】【即每轮Prover将发送3个field elements。】 - Verifier:
验证 H = g 1 ( 0 ) + g 1 ( 1 ) H=g_1(0)+g_1(1) H=g1(0)+g1(1)是否成立,若成立,则发送random challenege r 1 ← F r_1\leftarrow \mathbf{F} r1←F。
第2轮:
- Prover:发送polynomial g 2 ( X 2 ) g_2(X_2) g2(X2),同时声明 g 2 ( X 2 ) = ∑ ( x 3 , ⋯ , x v ) v − 2 g ( r 1 , X 2 , x 3 , ⋯ , x v ) g_2(X_2)=\sum_{(x_3,\cdots,x_v)^{v-2}}g(r_1,X_2,x_3,\cdots,x_v) g2(X2)=∑(x3,⋯,xv)v−2g(r1,X2,x3,⋯,xv)。
若 g 2 g_2 g2是正确的,则有 g 2 ( 0 ) + g 2 ( 1 ) = g 1 ( r 1 ) g_2(0)+g_2(1)=g_1(r_1) g2(0)+g2(1)=g1(r1)。 - Verifier:
验证 g 2 ( 0 ) + g 2 ( 1 ) = g 1 ( r 1 ) g_2(0)+g_2(1)=g_1(r_1) g2(0)+g2(1)=g1(r1)是否成立,若成立,则发送random challenege r 2 ← F r_2\leftarrow \mathbf{F} r2←F。
⋮ \vdots ⋮
第 j > 1 j>1 j>1轮:
- Prover:发送polynomial g j ( X j ) g_j(X_j) gj(Xj),同时声明 g j ( X j ) = ∑ ( x j + 1 , ⋯ , x v ) v − j g ( r 1 , ⋯ , r j − 1 , X j , x j + 1 , ⋯ , x v ) g_j(X_j)=\sum_{(x_{j+1},\cdots,x_v)^{v-j}}g(r_1,\cdots,r_{j-1},X_j,x_{j+1},\cdots,x_v) gj(Xj)=∑(xj+1,⋯,xv)v−jg(r1,⋯,rj−1,Xj,xj+1,⋯,xv)。
若 g j g_j gj是正确的,则有 g j ( 0 ) + g j ( 1 ) = g j − 1 ( r j − 1 ) g_j(0)+g_j(1)=g_{j-1}(r_{j-1}) gj(0)+gj(1)=gj−1(rj−1)。 - Verifier:验证 g j ( 0 ) + g j ( 1 ) = g j − 1 ( r j − 1 ) g_j(0)+g_j(1)=g_{j-1}(r_{j-1}) gj(0)+gj(1)=gj−1(rj−1)是否成立,若成立,则发送random challenege r j ← F r_j\leftarrow \mathbf{F} rj←F。
⋮ \vdots ⋮
最后一轮:
- Prover:发送polynomial g v ( X v ) g_v(X_v) gv(Xv),同时声明 g ( r 1 , ⋯ , r v − 1 , X v ) g(r_1,\cdots,r_{v-1},X_v) g(r1,⋯,rv−1,Xv)。
若 g v g_v gv是正确的,则有 g v ( 0 ) + g v ( 1 ) = g v − 1 ( r v − 1 ) g_v(0)+g_v(1)=g_{v-1}(r_{v-1}) gv(0)+gv(1)=gv−1(rv−1)。 - Verifier:验证 g v ( 0 ) + g v ( 1 ) = g v − 1 ( r v − 1 ) g_v(0)+g_v(1)=g_{v-1}(r_{v-1}) gv(0)+gv(1)=gv−1(rv−1)是否成立,若成立,则Verifier选择random challenge r v ← F r_v\leftarrow \mathbf{F} rv←F并evaluates g ( r 1 , ⋯ , r v ) g(r_1,\cdots,r_v) g(r1,⋯,rv) with a single oracle query to g g g,Verifier验证 g v ( r v ) = g ( r 1 , ⋯ , r v ) g_v(r_v)=g(r_1,\cdots,r_v) gv(rv)=g(r1,⋯,rv)是否成立,若成立,则Verifier可信任 H = g 1 ( 0 ) + g 1 ( 1 ) H=g_1(0)+g_1(1) H=g1(0)+g1(1)。
以上整个sum-check protocol的描述可表示为:
整个sum-check protocol的开销为:

微软研究中心2020年论文《Spartan: Efficient and general-purpose zkSNARKs without trusted setup》中,则从Verifier的角度描述了整个sum-check protocol:
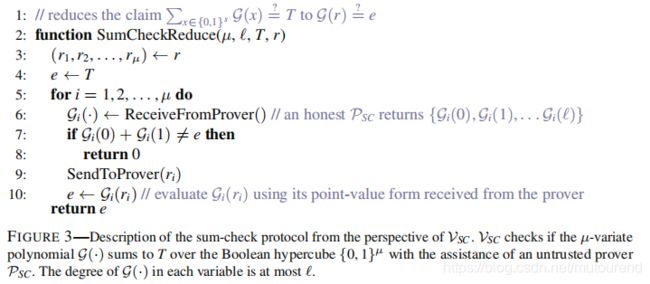
The verifier可process each message sent by the prover in O ( 1 ) O(1) O(1) time,at the very end of the sum-check protocol,verifier仍然需要evaluate g g g at signle point。
在此约定,在 F \mathbf{F} F域内的任意的加法或乘法运算均take O ( 1 ) O(1) O(1) time。
3. verifier的角度看sum-check protocol
Verifier若自己直接计算方程式(1)中的 H H H值,则需要evaluate g g g at 2 v 2^v 2v inputs(即,all inputs in { 0 , 1 } v \{0,1\}^v { 0,1}v)。当 2 v 2^v 2v为unacceptably large runtime for the verifier时,则需要借助sum-check protocol。
借助sum-check protocol,verifier的runtime为:
O ( v + [ the cost to evaluate g at a single input in F v ] ) O(v+[\text{the cost to evaluate }g\text{ at a single input in }\mathbf{F}^v]) O(v+[the cost to evaluate g at a single input in Fv])
该runtime远远优于 直接计算 2 v 2^v 2v evaluations of g g g。
sum-check protocol中的prover可计算all of its prescribed messages by evaluating g g g at O ( 2 v ) O(2^v) O(2v) inputs in F v \mathbf{F}^v Fv。This is only a constant factor more than what is required simply to compute H H H without proving correctness。
sum-check protocol 的soundness error为 O ( v / ∣ F ∣ ) O(v/|\mathbf{F}|) O(v/∣F∣)。只要 g g g is defined over a field of size significantly greater than v v v,则该soundness error可忽略。
4. sum-check protocol 的应用
应用场景之一为:
Verifier有input x x x,需要Prover计算 F ( x ) F(x) F(x)。
为了使用sum-check protocol,需将 F ( x ) F(x) F(x) 表示为类似方程式(1)的形式,即需要 identify some v v v-variate polynomial g g g of degree 2 in each variable,使得 F ( x ) F(x) F(x) can be inferred from the some of g g g's values over all inputs in { 0 , 1 } v \{0,1\}^v { 0,1}v。同时要求Verifier可evaluate g ( r ⃗ ) g(\vec{r}) g(r) at any desired input r ⃗ ∈ F v \vec{r}\in\mathbf{F}^v r∈Fv in linear time。
举例:
input x x x为the adjacency matrix of a graph, F ( x ) F(x) F(x) 为the number of triangles in that graph。
即,假设 G G G为 具有 n n n个顶点的无向图,其edge set为 E E E。假设 A ∈ { 0 , 1 } n × n A\in\{0,1\}^{n\times n} A∈{ 0,1}n×n为相应的adjacency matrix,即 A i , j = 1 A_{i,j}=1 Ai,j=1当且仅当 ( i , j ) ∈ E (i,j)\in E (i,j)∈E。(对于无向图,其邻接矩阵是对称的,且主对角线一定为0,存储空间实际仅需 n ( n − 1 ) / 2 n(n-1)/2 n(n−1)/2即可。)
而在counting triangles问题中,输入为邻接矩阵 A A A,输出要求为the number of vertex triples ( i , j , k ) (i,j,k) (i,j,k) that are all connected to each other by edges。
不将邻接矩阵 A A A看成是矩阵,而将其看成是a function f A f_A fA mapping { 0 , 1 } log n × { 0 , 1 } log n \{0,1\}^{\log n}\times \{0,1\}^{\log n} { 0,1}logn×{ 0,1}logn to { 0 , 1 } \{0,1\} { 0,1},则可定义 f A ( x ⃗ , y ⃗ ) f_A(\vec{x},\vec{y}) fA(x,y),其中 x ⃗ , y ⃗ \vec{x},\vec{y} x,y为整数 i , j ∈ [ 1 , n ] i,j\in[1,n] i,j∈[1,n]的二进制表示,输出结果为 A i , j A_{i,j} Ai,j。
相应的,the number of triangels in G G G可简单表示为:
Δ = 1 6 ∑ x ⃗ , y ⃗ , z ⃗ ∈ { 0 , 1 } log n f A ( x ⃗ , y ⃗ ) ⋅ f A ( y ⃗ , z ⃗ ) ⋅ f A ( x ⃗ , z ⃗ ) \Delta=\frac{1}{6}\sum_{\vec{x},\vec{y},\vec{z}\in\{0,1\}^{\log n}}f_A(\vec{x},\vec{y})\cdot f_A(\vec{y},\vec{z})\cdot f_A(\vec{x},\vec{z}) Δ=61∑x,y,z∈{ 0,1}lognfA(x,y)⋅fA(y,z)⋅fA(x,z) ……(2)
以上方程式(2)中的 1 6 \frac{1}{6} 61 是因为针对的是无向图。
6 Δ = ∑ x ⃗ , y ⃗ , z ⃗ ∈ { 0 , 1 } log n f A ( x ⃗ , y ⃗ ) ⋅ f A ( y ⃗ , z ⃗ ) ⋅ f A ( x ⃗ , z ⃗ ) 6\Delta=\sum_{\vec{x},\vec{y},\vec{z}\in\{0,1\}^{\log n}}f_A(\vec{x},\vec{y})\cdot f_A(\vec{y},\vec{z})\cdot f_A(\vec{x},\vec{z}) 6Δ=∑x,y,z∈{ 0,1}lognfA(x,y)⋅fA(y,z)⋅fA(x,z)
设 F \mathbf{F} F为a finite field,其field size p ≥ n 3 p\geq n^3 p≥n3且 p p p为prime,同时将矩阵 A A A中的所有元素都看成是 F \mathbf{F} F域内的元素,则选择足够大的 p p p值以保证 6 Δ 6\Delta 6Δ 在 [ 0 , p − 1 ] [0,p-1] [0,p−1]范围内。
假设 f ~ A \tilde{f}_A f~A为the MLE of f A f_A fA over F \mathbf{F} F,则可定义 ( 3 log n ) (3\log n) (3logn)-variate polynomial g g g为:
g ( X , Y , Z ) = f ~ A ( X , Y ) ⋅ f ~ A ( Y , Z ) ⋅ f ~ A ( X , Z ) g(X,Y,Z)=\tilde{f}_A(X,Y)\cdot \tilde{f}_A(Y,Z)\cdot \tilde{f}_A(X,Z) g(X,Y,Z)=f~A(X,Y)⋅f~A(Y,Z)⋅f~A(X,Z)
从而满足 6 Δ = ∑ x , y , z ∈ { 0 , 1 } log n g ( x , y , z ) 6\Delta=\sum_{x,y,z\in\{0,1\}^{\log n}}g(x,y,z) 6Δ=∑x,y,z∈{ 0,1}logng(x,y,z)。
整个IP(interactive proof) 过程需要 3 log n 3\log n 3logn轮,每轮Prover将发送3个field elements。
而Verifier的runtime主要在于:
evaluate g g g at single input ( r 1 , r 2 , r 3 ) ∈ F 3 log n (r_1,r_2,r_3)\in\mathbf{F}^{3\log n} (r1,r2,r3)∈F3logn,即相当于evaluate f ~ A \tilde{f}_A f~A at three inputs ( r 1 , r 2 ) , ( r 2 , r 3 ) , ( r 1 , r 3 ) (r_1,r_2),(r_2,r_3),(r_1,r_3) (r1,r2),(r2,r3),(r1,r3)。借助Multilinear Extension Lemma 仅需 O ( n 2 ) O(n^2) O(n2) time。
Prover的runtime为:【该runtime matches the naive algorithm for counting triangles that iterates over all triples of vertices in G G G and checks if they are all connected to each other。】【Prover端可直接运行the best-known algorithm to solve the triangles problem,然后仅需做额外多一点点工作来证明the answer is correct。当前不存在有任何其它IPs或argument systems可实现super-efficiency for the prover的同时,keep the proof length sublinear in the input size。】
compute all of its prescribed messages in O ( n 3 ) O(n^3) O(n3) time。
当前已知的最快的count triangles算法,其需要matrix multiplication time (superlinear in the input size),而借助sum-check protocol的速度更优。
此外,借助sum-check protocol可实现super-efficient IP for matrix-powering。如已知任意的 n × n n\times n n×n矩阵 A A A over field F \mathbf{F} F,该IP可计算any desired entry of the powered matrix A k A^k Ak。整个IP的round和communication cost为 O ( log ( k ) ⋅ log n ) O(\log(k)\cdot \log n) O(log(k)⋅logn),而verifier的runtime为 O ( n 2 + log ( k ) ⋅ log n ) O(n^2+\log(k)\cdot \log n) O(n2+log(k)⋅logn)。
Goldwasser, Kalai和Rothblum (GKR) 2008年论文《Delegating Computation: Interactive Proofs for Muggles》中正是利用了matrix-powering protocol证明了:
all problems solvable in logarithmic space have an IP with a quasilinear-time verifier, polynomial time prover, and polylogarithmic proof length。
该proof的核心思想为:
excute any Turing Machine M M M that uses s s s bits of space可reduce 为 the problem of computing a single entry of A 2 s A^{2^s} A2s for a certain matrix A A A ( A A A is in fact the configuration graph of M M M)。
因此,one can just apply the matrix-powering IP to A A A to determine the output of M M M。当 A A A为huge matrix时(至少有 2 s 2^s 2s行和 2 s 2^s 2s列),则configuration graph具有a ton of structure,借助matrix-powering IP,使得Verifier evaluate f ~ A \tilde{f}_A f~A at a single input的时间为 O ( s ⋅ n ) O(s\cdot n) O(s⋅n),当 s s s为logarithmic in the input size时,即意味着Verifier in the IP的runtime为 O ( n log n ) O(n\log n) O(nlogn)。
在GKR论文中,构建了an arithmetic circuit for computing A 2 s A^{2^s} A2s and then apply a sophisticated IP for arithmetic circuit evaluation to that circuit。
5. sum-check protocol + zero-knowledge
sum-check protocol 本身不具备zero-knowledge属性,而在 Wahby等人2018年论文《Hyrax Doubly-efficient zkSNARKs without trusted setup》中,实现了a zero-knowledge variant for the sum-check protocol:
借助“commit-and-prove”技术,在第2节的每一轮,Prover不再直接给Verifier 发送 多项式 g j ( X j ) g_j(X_j) gj(Xj),而是利用commitment的同态属性,对该多项式进行commit。
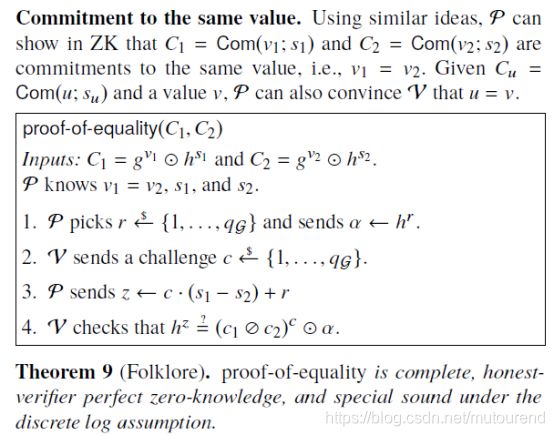
在讨论具体的zero-knowledge sum-check protocol实现细节之前,先介绍3个基于commitment的sub-protocol:
5.1 直观版 zero-knowledge sum-check protocol
整个sum-check protocol包含 v v v轮,每一轮对应 g g g中的一个变量。【利用“commit-and-prove”,添加zero-knowledge属性。】
第1轮:
- Prover:计算polynomial g 1 ( X 1 ) g_1(X_1) g1(X1),同时声明 g 1 ( X 1 ) = ∑ x 2 , ⋯ , x v ∈ { 0 , 1 } v − 1 g ( X 1 , x 2 , ⋯ , x v ) = c 0 , 1 + c 1 , 1 X 1 + c 2 , 1 X 1 2 g_1(X_1)=\sum_{x_2,\cdots,x_v}\in\{0,1\}^{v-1}g(X_1,x_2,\cdots,x_v)=c_{0,1}+c_{1,1}X_1+c_{2,1}X_1^2 g1(X1)=∑x2,⋯,xv∈{ 0,1}v−1g(X1,x2,⋯,xv)=c0,1+c1,1X1+c2,1X12。
若 g 1 g_1 g1是正确的,则有 H = g 1 ( 0 ) + g 1 ( 1 ) H=g_1(0)+g_1(1) H=g1(0)+g1(1)。
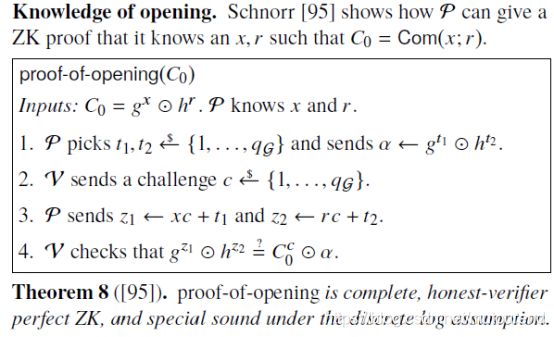
Prover对多项式的系数进行commit, δ c 0 , 1 = C o m ( c 0 , 1 ) , δ c 1 , 1 = C o m ( c 1 , 1 ) , δ c 2 , 1 = C o m ( c 2 , 1 ) \delta_{c_{0,1}}=Com(c_{0,1}),\delta_{c_{1,1}}=Com(c_{1,1}),\delta_{c_{2,1}}=Com(c_{2,1}) δc0,1=Com(c0,1),δc1,1=Com(c1,1),δc2,1=Com(c2,1),将这些commitment值发送给Verifier。 - Prover & Verifier:对 δ c 0 , 1 、 δ c 1 , 1 、 δ c 2 , 1 \delta_{c_{0,1}}、\delta_{c_{1,1}}、\delta_{c_{2,1}} δc0,1、δc1,1、δc2,1运行
proof-of-opening。 - Verifier:
【由于 g 1 ( 0 ) + g 1 ( 1 ) = 2 c 0 , 1 + c 1 , 1 + c 2 , 1 g_1(0)+g_1(1)=2c_{0,1}+c_{1,1}+c_{2,1} g1(0)+g1(1)=2c0,1+c1,1+c2,1,利用Pedersen commitment的加法同态属性,对于 H = g 1 ( 0 ) + g 1 ( 1 ) H=g_1(0)+g_1(1) H=g1(0)+g1(1)有:】
验证 C o m ( H ; 0 ) = δ c 0 , 1 2 ⋅ δ c 1 , 1 ⋅ δ c 2 , 1 Com(H;0)=\delta_{c_{0,1}}^2\cdot\delta_{c_{1,1}}\cdot \delta_{c_{2,1}} Com(H;0)=δc0,12⋅δc1,1⋅δc2,1是否成立,若成立,则发送random challenege r 1 ← F r_1\leftarrow \mathbf{F} r1←F。
第2轮:
- Prover:计算polynomial g 2 ( X 2 ) g_2(X_2) g2(X2),同时声明 g 2 ( X 2 ) = ∑ ( x 3 , ⋯ , x v ) v − 2 g ( r 1 , X 2 , x 3 , ⋯ , x v ) = c 0 , 2 + c 1 , 2 X 2 + c 2 , 2 X 2 2 g_2(X_2)=\sum_{(x_3,\cdots,x_v)^{v-2}}g(r_1,X_2,x_3,\cdots,x_v)=c_{0,2}+c_{1,2}X_2+c_{2,2}X_2^2 g2(X2)=∑(x3,⋯,xv)v−2g(r1,X2,x3,⋯,xv)=c0,2+c1,2X2+c2,2X22。
若 g 2 g_2 g2是正确的,则有 g 2 ( 0 ) + g 2 ( 1 ) = g 1 ( r 1 ) g_2(0)+g_2(1)=g_1(r_1) g2(0)+g2(1)=g1(r1)。
Prover对多项式的系数进行commit, δ c 0 , 2 = C o m ( c 0 , 2 ) , δ c 1 , 2 = C o m ( c 1 , 2 ) , δ c 2 , 2 = C o m ( c 2 , 2 ) \delta_{c_{0,2}}=Com(c_{0,2}),\delta_{c_{1,2}}=Com(c_{1,2}),\delta_{c_{2,2}}=Com(c_{2,2}) δc0,2=Com(c0,2),δc1,2=Com(c1,2),δc2,2=Com(c2,2),将这些commitment值发送给Verifier。 - Prover & Verifier:对 δ c 0 , 2 、 δ c 1 , 2 、 δ c 2 , 2 \delta_{c_{0,2}}、\delta_{c_{1,2}}、\delta_{c_{2,2}} δc0,2、δc1,2、δc2,2运行
proof-of-opening。 - Verifier:
【由于 g 1 ( r 1 ) = c 0 , 1 + c 1 , 1 ⋅ r 1 + c 2 , 1 ⋅ r 1 2 g_1(r_1)=c_{0,1}+c_{1,1}\cdot r_1+c_{2,1}\cdot r_1^2 g1(r1)=c0,1+c1,1⋅r1+c2,1⋅r12 及 g 2 ( 0 ) + g 2 ( 1 ) = 2 c 0 , 2 + c 1 , 2 + c 2 , 2 g_2(0)+g_2(1)=2c_{0,2}+c_{1,2}+c_{2,2} g2(0)+g2(1)=2c0,2+c1,2+c2,2,利用Pedersen commitment的加法同态属性,对于 g 2 ( 0 ) + g 2 ( 1 ) = g 1 ( r 1 ) g_2(0)+g_2(1)=g_1(r_1) g2(0)+g2(1)=g1(r1)有:】
验证 δ c 0 , 2 2 ⋅ δ c 1 , 2 ⋅ δ c 2 , 2 = δ c 0 , 1 ⋅ δ c 1 , 1 r 1 ⋅ δ c 2 , 1 r 1 2 \delta_{c_{0,2}}^2\cdot\delta_{c_{1,2}}\cdot \delta_{c_{2,2}}=\delta_{c_{0,1}}\cdot\delta_{c_{1,1}}^{r_1}\cdot \delta_{c_{2,1}}^{r_1^2} δc0,22⋅δc1,2⋅δc2,2=δc0,1⋅δc1,1r1⋅δc2,1r12是否成立,若成立,则发送random challenege r 2 ← F r_2\leftarrow \mathbf{F} r2←F。
⋮ \vdots ⋮
第 j > 1 j>1 j>1轮:
- Prover:计算polynomial g j ( X j ) g_j(X_j) gj(Xj),同时声明 g j ( X j ) = ∑ ( x j + 1 , ⋯ , x v ) v − j g ( r 1 , ⋯ , r j − 1 , X j , x j + 1 , ⋯ , x v ) = c 0 , j + c 1 , j X j + c 2 , j X j 2 g_j(X_j)=\sum_{(x_{j+1},\cdots,x_v)^{v-j}}g(r_1,\cdots,r_{j-1},X_j,x_{j+1},\cdots,x_v)=c_{0,j}+c_{1,j}X_j+c_{2,j}X_j^2 gj(Xj)=∑(xj+1,⋯,xv)v−jg(r1,⋯,rj−1,Xj,xj+1,⋯,xv)=c0,j+c1,jXj+c2,jXj2。
若 g j g_j gj是正确的,则有 g j ( 0 ) + g j ( 1 ) = g j − 1 ( r j − 1 ) g_j(0)+g_j(1)=g_{j-1}(r_{j-1}) gj(0)+gj(1)=gj−1(rj−1)。
Prover对多项式的系数进行commit, δ c 0 , j = C o m ( c 0 , j ) , δ c 1 , j = C o m ( c 1 , j ) , δ c 2 , j = C o m ( c 2 , j ) \delta_{c_{0,j}}=Com(c_{0,j}),\delta_{c_{1,j}}=Com(c_{1,j}),\delta_{c_{2,j}}=Com(c_{2,j}) δc0,j=Com(c0,j),δc1,j=Com(c1,j),δc2,j=Com(c2,j),将这些commitment值发送给Verifier。 - Prover & Verifier:对 δ c 0 , j 、 δ c 1 , j 、 δ c 2 , j \delta_{c_{0,j}}、\delta_{c_{1,j}}、\delta_{c_{2,j}} δc0,j、δc1,j、δc2,j运行
proof-of-opening。 - Verifier:
【由于 g j − 1 ( r j − 1 ) = c 0 , j − 1 + c 1 , j − 1 ⋅ r j − 1 + c 2 , j − 1 ⋅ r j − 1 2 g_{j-1}(r_{j-1})=c_{0,j-1}+c_{1,j-1}\cdot r_{j-1}+c_{2,{j-1}}\cdot r_{j-1}^2 gj−1(rj−1)=c0,j−1+c1,j−1⋅rj−1+c2,j−1⋅rj−12 及 g j ( 0 ) + g j ( 1 ) = 2 c 0 , j + c 1 , j + c 2 , j g_j(0)+g_j(1)=2c_{0,j}+c_{1,j}+c_{2,j} gj(0)+gj(1)=2c0,j+c1,j+c2,j,利用Pedersen commitment的加法同态属性,对于 g j ( 0 ) + g j ( 1 ) = g j − 1 ( r j − 1 ) g_j(0)+g_j(1)=g_{j-1}(r_{j-1}) gj(0)+gj(1)=gj−1(rj−1)有:】
验证 δ c 0 , j 2 ⋅ δ c 1 , j ⋅ δ c 2 , j = δ c 0 , j − 1 ⋅ δ c 1 , j − 1 r j − 1 ⋅ δ c 2 , j − 1 r j − 1 2 \delta_{c_{0,j}}^2\cdot\delta_{c_{1,j}}\cdot \delta_{c_{2,j}}=\delta_{c_{0,j-1}}\cdot\delta_{c_{1,j-1}}^{r_{j-1}}\cdot \delta_{c_{2,j-1}}^{r_{j-1}^2} δc0,j2⋅δc1,j⋅δc2,j=δc0,j−1⋅δc1,j−1rj−1⋅δc2,j−1rj−12是否成立,若成立,则发送random challenege r j ← F r_j\leftarrow \mathbf{F} rj←F。
⋮ \vdots ⋮
最后一轮:
- Prover:计算polynomial g v ( X v ) g_v(X_v) gv(Xv),同时声明 g ( r 1 , ⋯ , r v − 1 , X v ) = c 0 , v + c 1 , v X v + c 2 , v X v 2 g(r_1,\cdots,r_{v-1},X_v)=c_{0,v}+c_{1,v}X_v+c_{2,v}X_v^2 g(r1,⋯,rv−1,Xv)=c0,v+c1,vXv+c2,vXv2。
若 g v g_v gv是正确的,则有 g v ( 0 ) + g v ( 1 ) = g v − 1 ( r v − 1 ) g_v(0)+g_v(1)=g_{v-1}(r_{v-1}) gv(0)+gv(1)=gv−1(rv−1)。
Prover对多项式的系数进行commit, δ c 0 , v = C o m ( c 0 , v ) , δ c 1 , v = C o m ( c 1 , v ) , δ c 2 , v = C o m ( c 2 , v ) \delta_{c_{0,v}}=Com(c_{0,v}),\delta_{c_{1,v}}=Com(c_{1,v}),\delta_{c_{2,v}}=Com(c_{2,v}) δc0,v=Com(c0,v),δc1,v=Com(c1,v),δc2,v=Com(c2,v),将这些commitment值发送给Verifier。 - Prover & Verifier:对 δ c 0 , v 、 δ c 1 , v 、 δ c 2 , v \delta_{c_{0,v}}、\delta_{c_{1,v}}、\delta_{c_{2,v}} δc0,v、δc1,v、δc2,v运行
proof-of-opening。 - Verifier:
【由于 g v − 1 ( r v − 1 ) = c 0 , v − 1 + c 1 , v − 1 ⋅ r v − 1 + c 2 , v − 1 ⋅ r v − 1 2 g_{v-1}(r_{v-1})=c_{0,v-1}+c_{1,v-1}\cdot r_{v-1}+c_{2,{v-1}}\cdot r_{v-1}^2 gv−1(rv−1)=c0,v−1+c1,v−1⋅rv−1+c2,v−1⋅rv−12 及 g v ( 0 ) + g v ( 1 ) = 2 c 0 , v + c 1 , v + c 2 , v g_v(0)+g_v(1)=2c_{0,v}+c_{1,v}+c_{2,v} gv(0)+gv(1)=2c0,v+c1,v+c2,v,利用Pedersen commitment的加法同态属性,对于 g v ( 0 ) + g v ( 1 ) = g v − 1 ( r v − 1 ) g_v(0)+g_v(1)=g_{v-1}(r_{v-1}) gv(0)+gv(1)=gv−1(rv−1)有:】
验证 δ c 0 , v 2 ⋅ δ c 1 , v ⋅ δ c 2 , v = δ c 0 , v − 1 ⋅ δ c 1 , v − 1 r v − 1 ⋅ δ c 2 , v − 1 r v − 1 2 \delta_{c_{0,v}}^2\cdot\delta_{c_{1,v}}\cdot \delta_{c_{2,v}}=\delta_{c_{0,v-1}}\cdot\delta_{c_{1,v-1}}^{r_{v-1}}\cdot \delta_{c_{2,v-1}}^{r_{v-1}^2} δc0,v2⋅δc1,v⋅δc2,v=δc0,v−1⋅δc1,v−1rv−1⋅δc2,v−1rv−12是否成立,若成立,则Verifier选择random challenge r v ← F r_v\leftarrow \mathbf{F} rv←F并evaluates g ( r 1 , ⋯ , r v ) g(r_1,\cdots,r_v) g(r1,⋯,rv) with a single oracle query to g g g。
【由于 g v ( r v ) = c 0 , v + c 1 , v ⋅ r v + c 2 , v ⋅ r v 2 g_{v}(r_{v})=c_{0,v}+c_{1,v}\cdot r_{v}+c_{2,v}\cdot r_{v}^2 gv(rv)=c0,v+c1,v⋅rv+c2,v⋅rv2 ,利用Pedersen commitment的加法同态属性,对于 g v ( r v ) = g ( r 1 , ⋯ , r v ) g_v(r_v)=g(r_1,\cdots,r_v) gv(rv)=g(r1,⋯,rv)有:】
Verifier验证 C o m ( g ( r 1 , ⋯ , r v ) ; 0 ) = δ c 0 , v ⋅ δ c 1 , v r v ⋅ δ c 2 , v r v 2 Com(g(r_1,\cdots,r_v);0)=\delta_{c_{0,v}}\cdot\delta_{c_{1,v}}^{r_{v}}\cdot \delta_{c_{2,v}}^{r_{v}^2} Com(g(r1,⋯,rv);0)=δc0,v⋅δc1,vrv⋅δc2,vrv2是否成立,若成立,则Verifier可信任 H = g 1 ( 0 ) + g 1 ( 1 ) H=g_1(0)+g_1(1) H=g1(0)+g1(1)。
5.2 reduce cost版 zero-knowledge sum-check protocol
【具体参考Hyrax论文第4和第5章内容。】
在以上“5.1 直观版”中,Prover为每一轮的每个多项式系数都单独生成发送相应的commitment,同时需在每一轮为每个commitment都运行proof-of-opening,存在的问题是:
- proof size会很长;
- Verifier需运行expensive crytographic operations。
可记住multi-commitment scheme(即Pedersen vector commitment)来reduce the communication and number of cryptographic operations for the verifier。
以 v = 3 v=3 v=3为例,可将“5.1 直观版”中Verifier在每一轮验证的关系表示为 2 c 0 , j + c 1 , j + c 2 , j − c 0 , j − 1 − c 1 , j − 1 ⋅ r j − 1 − c 2 , j − 1 ⋅ r j − 1 2 = 0 2c_{0,j}+c_{1,j}+c_{2,j}-c_{0,j-1}-c_{1,j-1}\cdot r_{j-1}-c_{2,{j-1}}\cdot r_{j-1}^2=0 2c0,j+c1,j+c2,j−c0,j−1−c1,j−1⋅rj−1−c2,j−1⋅rj−12=0,在最后一轮额外增加了 g v ( r v ) = c 0 , v + c 1 , v ⋅ r v + c 2 , v ⋅ r v 2 g_{v}(r_{v})=c_{0,v}+c_{1,v}\cdot r_{v}+c_{2,v}\cdot r_{v}^2 gv(rv)=c0,v+c1,v⋅rv+c2,v⋅rv2关系判断,可将该关系以matrix-vector product表示为:
[ 2 1 1 0 0 0 0 0 0 − 1 − r 1 − r 1 2 2 1 1 0 0 0 0 0 0 − 1 − r 2 − r 2 2 2 1 1 0 0 0 0 0 0 1 r 3 r 3 2 ] ⋅ [ c 0 , 1 c 1 , 1 c 2 , 1 c 0 , 2 c 1 , 2 c 2 , 2 c 0 , 3 c 1 , 3 c 2 , 3 ] = M ⋅ π ⃗ = [ M ⃗ 1 M ⃗ 2 M ⃗ 3 M ⃗ 4 ] ⋅ π ⃗ = [ H 0 0 g 3 ( r 3 ) ] \begin{bmatrix} 2 & 1 & 1 & 0 & 0 & 0 & 0 & 0 & 0\\ -1 & -r_1 & -r_1^2 & 2 & 1 & 1 & 0 & 0 & 0\\ 0 & 0 & 0 & -1 & -r_2 & -r_2^2 & 2 & 1 & 1\\ 0 & 0 & 0 & 0 & 0 & 0 & 1 & r_3 & r_3^2 \end{bmatrix}\cdot \begin{bmatrix} c_{0,1}\\ c_{1,1}\\ c_{2,1}\\ c_{0,2}\\ c_{1,2}\\ c_{2,2}\\ c_{0,3}\\ c_{1,3}\\ c_{2,3} \end{bmatrix}=\mathbf{M}\cdot \vec{\pi}=\begin{bmatrix} \vec{M}_1\\ \vec{M}_2\\ \vec{M}_3\\ \vec{M}_4 \end{bmatrix}\cdot \vec{\pi}=\begin{bmatrix} H\\ 0\\ 0\\ g_3(r_3) \end{bmatrix} ⎣⎢⎢⎡2−1001−r1001−r120002−1001−r2001−r2200021001r3001r32⎦⎥⎥⎤⋅⎣⎢⎢⎢⎢⎢⎢⎢⎢⎢⎢⎢⎢⎡c0,1c1,1c2,1c0,2c1,2c2,2c0,3c1,3c2,3⎦⎥⎥⎥⎥⎥⎥⎥⎥⎥⎥⎥⎥⎤=M⋅π=⎣⎢⎢⎢⎡M1M2M3M4⎦⎥⎥⎥⎤⋅π=⎣⎢⎢⎡H00g3(r3)⎦⎥⎥⎤ ……(5)
其中 π ⃗ = [ c 0 , 1 , c 1 , 1 , c 2 , 1 , c 0 , 2 , c 1 , 2 , c 2 , 2 , c 0 , 3 , c 1 , 3 , c 2 , 3 ] \vec{\pi}=[c_{0,1},c_{1,1},c_{2,1},c_{0,2},c_{1,2},c_{2,2},c_{0,3},c_{1,3},c_{2,3}] π=[c0,1,c1,1,c2,1,c0,2,c1,2,c2,2,c0,3,c1,3,c2,3] 为Prover witness。
将矩阵 M \mathbf{M} M的每一行 k k k引入随机系数 ρ k \rho_k ρk,然后行加,可将 v + 1 v+1 v+1个验证压缩为1个验证:
[ 2 ∗ ρ 1 − 1 ∗ ρ 2 , 1 ∗ ρ 1 − r 1 ∗ ρ 2 , 1 ∗ ρ 1 − r 1 2 ∗ ρ 2 , 2 ∗ ρ 2 − 1 ∗ ρ 3 , 1 ∗ ρ 2 − r 2 ∗ ρ 3 , 1 ∗ ρ 2 − r 2 2 ∗ ρ 3 , 2 ∗ ρ 3 + 1 ∗ ρ 4 , 1 ∗ ρ 3 + r 3 ∗ ρ 4 , 1 ∗ ρ 3 + r 3 2 ∗ ρ 4 ] ⋅ [ c 0 , 1 c 1 , 1 c 2 , 1 c 0 , 2 c 1 , 2 c 2 , 2 c 0 , 3 c 1 , 3 c 2 , 3 ] = < ∑ ρ k ⋅ M ⃗ k , π ⃗ > = < M ⃗ , π ⃗ > = [ H ∗ ρ 1 + g 3 ( r 3 ) ∗ ρ 4 ] [2*\rho_1-1*\rho_2,1*\rho_1-r_1*\rho_2, 1*\rho_1-r_1^2*\rho_2, 2*\rho_2-1*\rho_3,1*\rho_2-r_2*\rho_3 ,1*\rho_2-r_2^2*\rho_3 , 2*\rho_3+1*\rho_4,1*\rho_3+r_3*\rho_4, 1*\rho_3+r_3^2*\rho_4]\cdot \begin{bmatrix} c_{0,1}\\ c_{1,1}\\ c_{2,1}\\ c_{0,2}\\ c_{1,2}\\ c_{2,2}\\ c_{0,3}\\ c_{1,3}\\ c_{2,3} \end{bmatrix}=<\sum\rho_k\cdot \vec{M}_k, \vec{\pi}>=<\vec{M}, \vec{\pi}>=\begin{bmatrix} H*\rho_1+g_3(r_3)*\rho_4 \end{bmatrix} [2∗ρ1−1∗ρ2,1∗ρ1−r1∗ρ2,1∗ρ1−r12∗ρ2,2∗ρ2−1∗ρ3,1∗ρ2−r2∗ρ3,1∗ρ2−r22∗ρ3,2∗ρ3+1∗ρ4,1∗ρ3+r3∗ρ4,1∗ρ3+r32∗ρ4]⋅⎣⎢⎢⎢⎢⎢⎢⎢⎢⎢⎢⎢⎢⎡c0,1c1,1c2,1c0,2c1,2c2,2c0,3c1,3c2,3⎦⎥⎥⎥⎥⎥⎥⎥⎥⎥⎥⎥⎥⎤=<∑ρk⋅Mk,π>=<M,π>=[H∗ρ1+g3(r3)∗ρ4]
以上可转为 proof-of-dot-prod 证明,但是,sum-check protocol中要求Prover必须先commit c 0 , j , c 1 , j , c 2 , j c_{0,j},c_{1,j},c_{2,j} c0,j,c1,j,c2,j 然后Verifier在发送 r j r_j rj,因此Prover不能 直接对 π ⃗ \vec{\pi} π 所有内容进行commit。
Prover需commit to π ⃗ \vec{\pi} π incrmentally,using one group element per round of the sum-check。即在sum-check protocol的每一轮:
- Prover commit to a vector encoding the coefficients of that round’s polynomial,即有commitment α j = C o m ( ( c 0 , j , c 1 , j , c 2 , j ) ; r α j ) \alpha_j=Com((c_{0,j},c_{1,j},c_{2,j});r_{\alpha_j}) αj=Com((c0,j,c1,j,c2,j);rαj);
- Verifier responds with random challenge r j r_j rj。
直到最后Prover has committed to all of its messages for the sum-check,运行如下sum-check protocol:
6. sum-check protocol + succinct
以实现sub-linear verification cost 和 sub-linear communication cost。
参考资料
[1] Justin Thaler博客 The Unreasonable Power of the Sum-Check Protocol
[2] utexas大学课件 Lecture 3: The Sum Check Protocol
[3] Justin Thaler 在georgetown大学的课件 The Sum-Check Protocol
[4] adjacency matrix 邻接矩阵
[5] Gorka Irazoqui Apecechea medium博客 Spartan: zkSNARKS without trusted setup