k8s-安装dashboard
前提:
有一个k8s集群
安装:
1.到github获取配置文件
github下面给出方法说使用下面的直接执行就可以了,原来我安装的时候确实可以,但是最近不知道为何找不到地址。
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.5/aio/deploy/recommended.yaml
上面很明显给出了地址aio/deploy/recommended.yaml
所以我们找到配置文件:https://github.com/kubernetes/dashboard/tree/master/aio/deploy

vim recommended.yaml
2. 然后将recommended.yaml文件内容粘贴复制到本地
3.部署:
[root@master dashboard]# kubectl apply -f recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
4.暴露svc端口
找到dashboard的SVC,发现是ClusterIP类型的,因为我想在宿主机访问,所以要暴露端口
[root@master cert]# kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.96.140.126 <none> 8000/TCP 32m
kubernetes-dashboard ClusterIP 10.101.224.123 <none> 443/TCP 32m
暴露端口:
修改svc为NodePort类型:
kubectl patch svc kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}' -n kubernetes-dashboard
找到暴露端口为:31526(注意是https)
[root@master cert]# kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.96.140.126 <none> 8000/TCP 33m
kubernetes-dashboard NodePort 10.101.224.123 <none> 443:31526/TCP 33m
这样在我们宿主机浏览器就能访问:
https://192.168.10.180:31526/
显示不安全,我们点击高级继续访问,之后为:
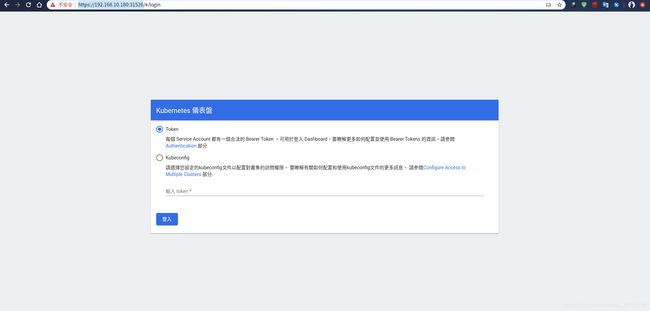
登录之后需要人认证,认证有两种方式kubeconfig模式和融科你模式:
我使用的token模式:
5.创建token
我是基于最高权限admin创建的:
创建secret:
[root@master token]# cat admin-role.yaml
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: admin
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
roleRef:
kind: ClusterRole
name: cluster-admin
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: ServiceAccount
name: admin
namespace: kube-system
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin
namespace: kube-system
labels:
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
kubectl create -f admin-role.yaml
找到secret:
[root@master token]# kubectl -n kube-system get secret|grep admin-token
admin-token-ftkl9 kubernetes.io/service-account-token 3 22s
获取token:
kubectl -n kube-system describe secret admin-token-ftkl9
[root@master token]# kubectl -n kube-system describe secret admin-token-ftkl9
Name: admin-token-ftkl9
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: admin
kubernetes.io/service-account.uid: 9a247b1d-f9d9-4d45-813e-2a6448c7a279
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1066 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IkFPY0FvODhsbVU5SUxDQmN4RUF3eUdfbWE2LW1Fc09EY3BMekEzUDg2N2sifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi10b2tlbi1mdGtsOSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjlhMjQ3YjFkLWY5ZDktNGQ0NS04MTNlLTJhNjQ0OGM3YTI3OSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTphZG1pbiJ9.eI2iqcL_LMLXDTbKhPzn2fiiNIaRavzB8-fOrU_xFOFpmUbrUw98HXogMBdmVIWbJ3z83KUvVC_-oANHALUC-QpCqjOBGFmQSYIRPAJ_Fwq9qK80Yqc3SkXjbXAchlgBeIF-pUrr8eoemvNTPyJgxj8uA4ewHI2StcWIFpvLmxNzFB7xVc1_ta9nQ7BfIVzjYB9m8qVqO4gB8SNKXHVUa8bHykDy6Y4WygZ8fdbaoC8-9Yb04ukAuHlj4Hif7gB2CLLVQ97AbL6ygMMUUja-0zM-PgyUUaV4PEh_Kd1p_ophzbCHL-8QivB6edwSiMgbFgH60LnqMf5IJYuQK3gYUw
或者直接获取token
[root@master token]# kubectl -n kube-system get secret admin-token-ftkl9 -o jsonpath={.data.token}|base64 -d
eyJhbGciOiJSUzI1NiIsImtpZCI6IkFPY0FvODhsbVU5SUxDQmN4RUF3eUdfbWE2LW1Fc09EY3BMekEzUDg2N2sifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi10b2tlbi1mdGtsOSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjlhMjQ3YjFkLWY5ZDktNGQ0NS04MTNlLTJhNjQ0OGM3YTI3OSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTphZG1pbiJ9.eI2iqcL_LMLXDTbKhPzn2fiiNIaRavzB8-fOrU_xFOFpmUbrUw98HXogMBdmVIWbJ3z83KUvVC_-oANHALUC-QpCqjOBGFmQSYIRPAJ_Fwq9qK80Yqc3SkXjbXAchlgBeIF-pUrr8eoemvNTPyJgxj8uA4ewHI2StcWIFpvLmxNzFB7xVc1_ta9nQ7BfIVzjYB9m8qVqO4gB8SNKXHVUa8bHykDy6Y4WygZ8fdbaoC8-9Yb04ukAuHlj4Hif7gB2CLLVQ97AbL6ygMMUUja-0zM-PgyUUaV4PEh_Kd1p_ophzbCHL-8QivB6edwSiMgbFgH60LnqMf5IJYuQK3gYUw
将token填写到登录界面的token中:
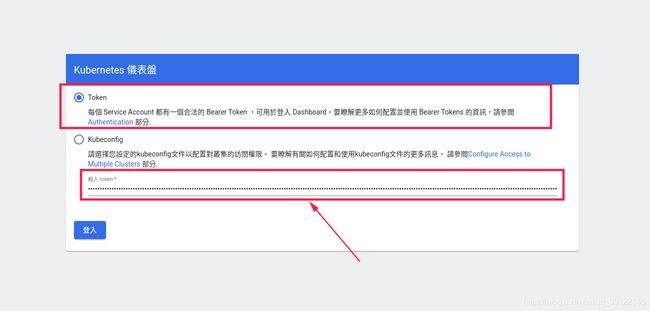
然后我们就能访问了:
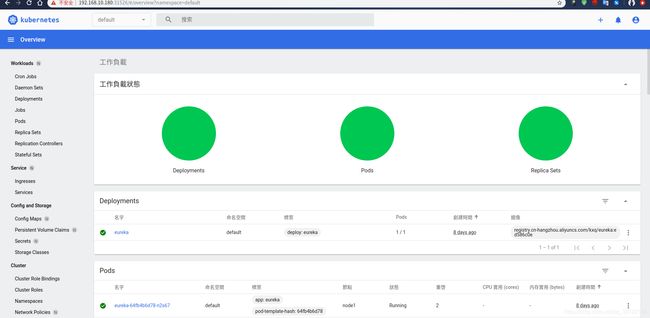
参考:
官网:https://kubernetes.io/zh/docs/tasks/access-application-cluster/web-ui-dashboard/
其他大牛:
https://jimmysong.io/kubernetes-handbook/guide/auth-with-kubeconfig-or-token.html
https://andrewpqc.github.io/2018/04/25/k8s-dashboard-auth/