iptables filter表小案例
需求:把80、22、21端口放行,22端口指定ip段访问
[root@wsl-001 ~]# vim /usr/local/sbin/iptables.sh
[root@wsl-001 ~]# sh /usr/local/sbin/iptables.sh
[root@wsl-001 ~]# iptables -nvL
Chain INPUT (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
29 2012 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT tcp -- * * 172.16.79.0/24 0.0.0.0/0 tcp dpt:22
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:21
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 15 packets, 1360 bytes)
pkts bytes target prot opt in out source destination
[root@wsl-001 ~]# cat /usr/local/sbin/iptables.sh
#!/bin/bash
ipt="/usr/sbin/iptables"
$ipt -F
$ipt -P INPUT DROP
$ipt -P OUTPUT ACCEPT
$ipt -P FORWARD ACCEPT
$ipt -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
$ipt -A INPUT -s 172.16.79.0/24 -p tcp --dport 22 -j ACCEPT
$ipt -A INPUT -p tcp --dport 80 -j ACCEPT
$ipt -A INPUT -p tcp --dport 21 -j ACCEPT
icmp示例
禁外网ping本机
上面的脚本是已经实现了得
[root@wsl-001 ~]# iptables -I INPUT -p icmp --icmp-type 8 -j DROP
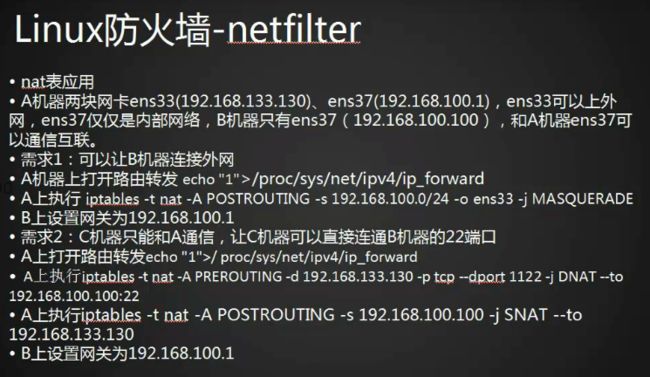
iptables nat表应用(上)
需求:A拥有两块网卡,内网和外网网卡;B只有一块内网网卡;B通过内网链接到A访问外网
首先增加A机器的网卡
查看到增加了一个网卡ens37
通过ifconfig配置网卡
[root@localhost ~]# ifconfig ens37 192.168.100.1/24
此配置只是临时IP,重启机器或者重启网络就没有了
需要在文件中配置
[root@localhost ~]# ifconfig
eno16777736: flags=4163 mtu 1500
inet 192.168.12.128 netmask 255.255.255.0 broadcast 192.168.12.255
inet6 fe80::20c:29ff:fe92:105d prefixlen 64 scopeid 0x20
ether 00:0c:29:92:10:5d txqueuelen 1000 (Ethernet)
RX packets 623 bytes 43399 (42.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 289 bytes 31355 (30.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
ens37: flags=4163 mtu 1500
inet6 fe80::fe29:ca66:ee98:e65 prefixlen 64 scopeid 0x20
ether 00:0c:29:92:10:67 txqueuelen 1000 (Ethernet)
RX packets 123 bytes 42066 (41.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 252 bytes 45240 (44.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73 mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10
loop txqueuelen 1 (Local Loopback)
RX packets 64 bytes 6128 (5.9 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 64 bytes 6128 (5.9 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@localhost ~]# ifconfig ens37 192.168.100.1/24
B机器网卡设置
用上面同样的方法设置IP为192.168.100.100/24
然后关掉A的外网网卡
[root@localhost ~]# ifdown eno16777736
ping B的IP地址发现能ping通就没问题了
ptables nat表应用(中)
A机器内核转发需要修改内核信息,打开端口转发
[root@localhost ~]# cat /proc/sys/net/ipv4/ip_forward
0
[root@localhost ~]# echo "1" > !$
echo "1" > /proc/sys/net/ipv4/ip_forward
[root@localhost ~]# !cat
cat /proc/sys/net/ipv4/ip_forward
1
A机器增加一条nat规则
[root@localhost ~]# iptables -t nat -A POSTROUTING -s 192.168.100.0/24 -o eno16777736 -j MASQUERADE
[root@localhost ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
304 76863 PREROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0
304 76863 PREROUTING_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
304 76863 PREROUTING_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
70 6947 OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
70 6947 POSTROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0
70 6947 POSTROUTING_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
70 6947 POSTROUTING_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 MASQUERADE all -- * eno16777736 192.168.100.0/24 0.0.0.0/0
Chain OUTPUT_direct (1 references)
pkts bytes target prot opt in out source destination
Chain POSTROUTING_ZONES (1 references)
pkts bytes target prot opt in out source destination
7 886 POST_public all -- * eno16777736 0.0.0.0/0 0.0.0.0/0 [goto]
16 1311 POST_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto]
Chain POSTROUTING_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain POSTROUTING_direct (1 references)
pkts bytes target prot opt in out source destination
Chain POST_public (2 references)
pkts bytes target prot opt in out source destination
70 6947 POST_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
70 6947 POST_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
70 6947 POST_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
Chain POST_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain POST_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain POST_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain PREROUTING_ZONES (1 references)
pkts bytes target prot opt in out source destination
8 580 PRE_public all -- eno16777736 * 0.0.0.0/0 0.0.0.0/0 [goto]
106 31585 PRE_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto]
Chain PREROUTING_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain PREROUTING_direct (1 references)
pkts bytes target prot opt in out source destination
Chain PRE_public (2 references)
pkts bytes target prot opt in out source destination
304 76863 PRE_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
304 76863 PRE_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
304 76863 PRE_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
Chain PRE_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain PRE_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain PRE_public_log (1 references)
pkts bytes target prot opt in out source destination
B机器设置网关
[root@localhost ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.100.0 0.0.0.0 255.255.255.0 U 0 0 0 ens33
[root@localhost ~]# route add default gw 192.168.100.1
[root@localhost ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.100.1 255.255.255.0 U 0 0 0 ens33
192.168.100.0 0.0.0.0 255.255.255.0 U 0 0 0 ens33
这时候Ping A机器的外网IP地址就可以Ping通了
iptables nat表应用(下)
端口映射
[root@localhost ~]# iptables -t nat -A PREROUTING -d 192.168.12.128 -p tcp --dport 1122 -j DNAT --to 192.168.100.100:22
[root@localhost ~]# iptables -t nat -A POSTROUTING -s 192.168.100.100 -j SNAT --to 192.168.12.128
这个时候链接A机器外网IP端口1122就可以ssh连接B机器了
如果出现问题使用iptables -F清空规则后再添加
扩展
1. iptables应用在一个网段 http://www.aminglinux.com/bbs/thread-177-1-1.html
2. sant,dnat,masquerade http://www.aminglinux.com/bbs/thread-7255-1-1.html
3. iptables限制syn速率 http://www.aminglinux.com/bbs/thread-985-1-1.htmlhttp://jamyy.us.to/blog/2006/03/206.html