主要内容:
1.准备环境
2.常见的远程连接工具
3.ssh相关的软件包
4.ssh服务端的配置文件
5.ssh认证方式
6.批量管理
一、准备环境
m01 : 公网ip:10.0.0.61;私网ip:172.16.1.61
backup: 公网ip: 10.0.0.41;私网ip:172.16.1.7
二、远程连接工具
1.ssh
2.telnet 服务
(1)直接使用telnet服务端口号为23进行登录
(2)在本地shell用命令:telnet [email protected]登录
3.http超文本传输协议
4.https 加密
三、ssh相关的软件包
openssh-clients-7.4p1-16.el7.x86_64
openssh-server-7.4p1-16.el7.x86_64
1.客户端命令
(1)ssh
参数:-p(小写) 指定端口号
[root@m01 ~]# ssh -p22 10.0.0.41
Last login: Mon May 27 16:46:26 2019 from 10.0.0.61
[root@backup ~]#
执行命令后退出:
[root@m01 ~]# ssh -p22 10.0.0.41 hostname -I
10.0.0.41 172.16.1.41
[root@m01 ~]# ssh -p22 10.0.0.41 hostname -I |awk '{print $2}'
172.16.1.41
(2)scp
参数: -P(大写) 指定端口号
-r 复制目录
[root@m01 ~]# scp -r -P22 /etc/ 172.16.1.41:/tmp
[root@backup ~]# ll /tmp/
total 4
drwxr-xr-x 10 root root 237 May 27 16:51 etc
-rw-r--r-- 1 root root 4 May 27 08:53 hostname
drwx------ 3 root root 17 May 26 09:19 systemd-private-2269d417884e40c1836d9ba2f5b92bbb-chronyd.service-U28w4h
drwx------ 2 root root 6 May 23 14:32 vmware-root_6052-692291465
drwx------ 2 root root 6 May 26 09:19 vmware-root_6792-2857044539
(3)sftp:上传或下载 相当于lrzsz中的rz和sz
参数:-P(大写) 指定端口号
sftp 主机名或ip:远程连接其他其他主机
[root@m01 ~]# sftp 172.16.1.41
Connected to 172.16.1.41.
sftp>
[root@m01 ~]# sftp -P22 172.16.1.41
Connected to 172.16.1.41.
sftp>
四、ssh服务端的配置文件
1./etc/ssh/sshd_conf---ssh服务端配置文件
(1)Port 22:端口号
[root@m01 ~]# ss -lntup |grep sshd
tcp LISTEN 0 128 *:22 *:* users:(("sshd",pid=7161,fd=3))
tcp LISTEN 0 128 :::22 :::* users:(("sshd",pid=7161,fd=4))
[root@m01 ~]# systemctl reload sshd.service
[root@m01 ~]# ss -lntup |grep sshd
tcp LISTEN 0 128 *:52113 *:* users:(("sshd",pid=7161,fd=3))
tcp LISTEN 0 128 :::52113 :::* users:(("sshd",pid=7161,fd=4))
[root@m01 ~]# grep Port /etc/ssh/sshd_config
Port 52113
#GatewayPorts no
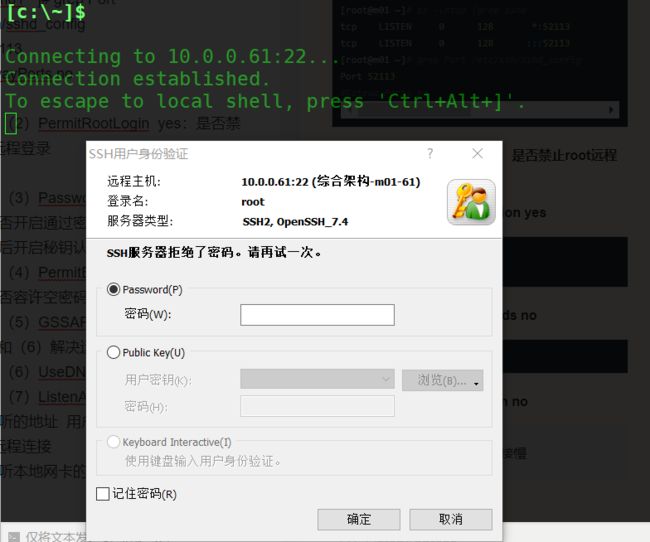
(2)PermitRootLogin yes:是否禁止root远程登录
[root@m01 ~]# grep PermitR /etc/ssh/sshd_config
PermitRootLogin no
# the setting of "PermitRootLogin without-password".
[root@m01 ~]# systemctl reload sshd.service
(3)PasswordAuthentication yes:是否开启通过密码登录(认证)(以后开启秘钥认证是可以改为no)
(4)PermitEmptyPasswords no:是否容许空密码,一般关闭
(5)GSSAPIAuthentication no
(6)UseDNS no
(5)和(6)解决远程连接慢
(7)ListenAddress:监听的地址 用户可以通过那个地址(ip)远程连接(只能监听本地网卡的ip地址)
[root@m01 ~]# systemctl reload sshd.service
[root@m01 ~]# grep ListenAddress /etc/ssh/sshd_config
#ListenAddress 0.0.0.0
ListenAddress 172.16.1.61
#ListenAddress 10.0.0.61:52113
#ListenAddress ::
[root@backup ~]# ssh 10.0.0.61
ssh: connect to host 10.0.0.61 port 22: Connection refused
[root@backup ~]# ssh 172.16.1.61
[email protected]'s password:
Last login: Mon May 27 17:09:32 2019 from 172.16.1.41
[root@m01 ~]#
2.不同的网段 通过不同的端口
ListenAddress 172.16.1.61:22
ListenAddress 10.0.0.61:52113
[root@m01 ~]# systemctl reload sshd.service
[root@m01 ~]# grep ListenAddress /etc/ssh/sshd_config
#ListenAddress 0.0.0.0
ListenAddress 172.16.1.61:22
ListenAddress 10.0.0.61:52113
#ListenAddress ::
[root@m01 ~]# ss -lntup |grep sshd
tcp LISTEN 0 128 10.0.0.61:52113 *:* users:(("sshd",pid=7161,fd=3))
tcp LISTEN 0 128 172.16.1.61:22 *:* users:(("sshd",pid=7161,fd=4))
[root@m01 ~]#
[root@backup ~]# ssh -p52113 10.0.0.61
[email protected]'s password:
Last login: Mon May 27 17:10:11 2019 from 172.16.1.41
[root@m01 ~]# logout
Connection to 10.0.0.61 closed.
[root@backup ~]# ssh -p22 172.16.1.61
[email protected]'s password:
Last login: Mon May 27 17:13:37 2019 from 10.0.0.41
3./etc/ssh/ssh_conf:ssh客户端配置文件
五、 ssh的认证方式
1.密码认证
2.秘钥认证(免密码登录/秘钥登录)
(1)创建钥匙
[root@m01 ~]# #创建钥匙
[root@m01 ~]# ssh-keygen -t dsa
Generating public/private dsa key pair.
Enter file in which to save the key (/root/.ssh/id_dsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_dsa.
Your public key has been saved in /root/.ssh/id_dsa.pub.
The key fingerprint is:
SHA256:c9hqXpQCc25TClXtL4kwHSxGQ+mIg6KZQvQer0OlcF0 root@m01
The key's randomart image is:
+---[DSA 1024]----+
| o=+.. |
| . E+.o . |
|. ....=+.o.o |
|.o.+oo.*+=... |
|o++ =. So=. o |
|= + . . B. o . |
|. . . o . . |
| o o . |
| . . |
+----[SHA256]-----+
[root@m01 ~]# ll ~/.ssh/
total 12
-rw------- 1 root root 668 May 27 17:18 id_dsa
-rw-r--r-- 1 root root 598 May 27 17:18 id_dsa.pub
-rw-r--r-- 1 root root 686 May 27 12:30 known_hosts
2.发送公钥
[root@m01 ~]# ssh-copy-id -i ~/.ssh/id_dsa.pub 172.16.1.41
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_dsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
[email protected]'s password:
Permission denied, please try again.
[email protected]'s password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '172.16.1.41'"
and check to make sure that only the key(s) you wanted were added.
[root@m01 ~]# ssh 172.16.1.41
Last failed login: Mon May 27 17:19:34 CST 2019 from 172.16.1.61 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Mon May 27 16:47:09 2019 from 10.0.0.61
[root@backup ~]# ll ~/.ssh/
total 8
-rw------- 1 root root 1196 May 27 17:19 authorized_keys
六、批量管理
1.xshell上键入回话
2.pssh(epel)
(1)参数
-h:指定管理及其的列表
用法:[user@]host[:port]
[email protected]:22或172.16.1.41;两种方法均可
[root@m01 ~]# vim hosts.txt
172.16.1.41
172.16.1.7
-P(大写):输出到屏幕
[root@m01 ~]# pssh -P -h /root/hosts.txt hostname
172.16.1.41: backup
[1] 17:28:08 [SUCCESS] 172.16.1.41
172.16.1.7: web01
[2] 17:28:08 [SUCCESS] 172.16.1.7
-A:手动输入密码 前提密码一样
(2)命令
prsync -azh /root/hosts.txt /etc/hostname /tmp
[root@m01 ~]# prsync -azh /root/hosts.txt /etc/hostname /tmp
[1] 17:30:09 [SUCCESS] 172.16.1.41
[2] 17:30:09 [SUCCESS] 172.16.1.7
[root@m01 ~]# ssh 172.16.1.41
Last login: Mon May 27 17:29:00 2019 from 10.0.0.61
[root@backup ~]# cat /tmp/hostname
m01
[root@backup ~]# logout
Connection to 172.16.1.41 closed.
[root@m01 ~]# ssh 172.16.1.7
Last login: Mon May 27 17:29:37 2019 from 172.16.1.61
[root@web01 ~]# cat /tmp/hostname
m01