2021年“绿盟杯”重庆市大学生信息安全竞赛—Light1ng战队Writeup
2021年“绿盟杯”重庆市大学生信息安全竞赛—Light1ng战队Writeup
其余方向Writeup详见pdf:https://wws.lanzoui.com/iWk1ovo0eaj
密码:Le1a
Misc
Misc1:签到1
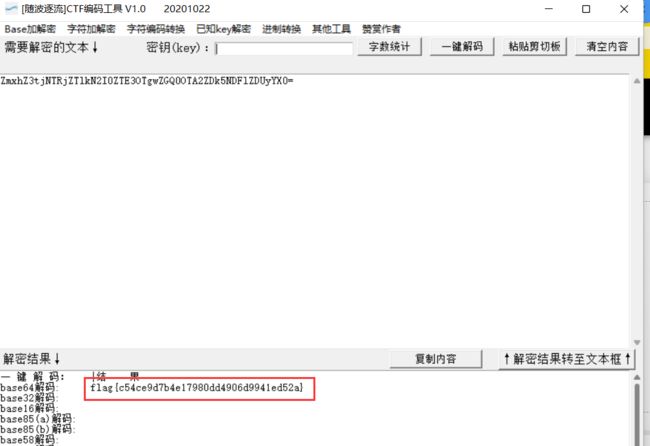
题目给了一串base64编码
解码得到flag:
flag{c54ce9d7b4e17980dd4906d9941ed52a}
Misc2:DECODER
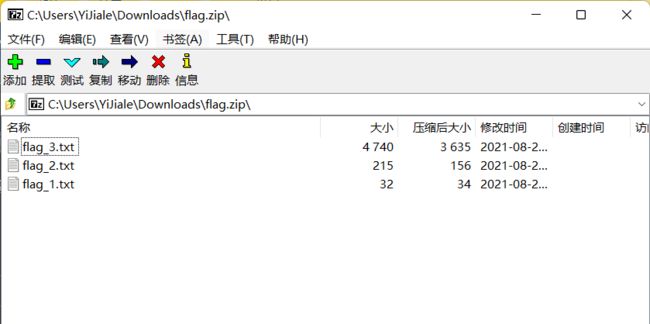
下载附件,打开得到3个txt,应该对应着三个部分的flag
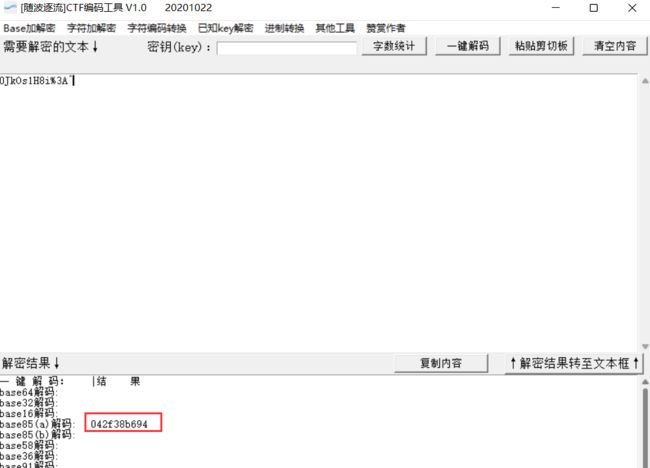
flag_1.txt: 042f38b694
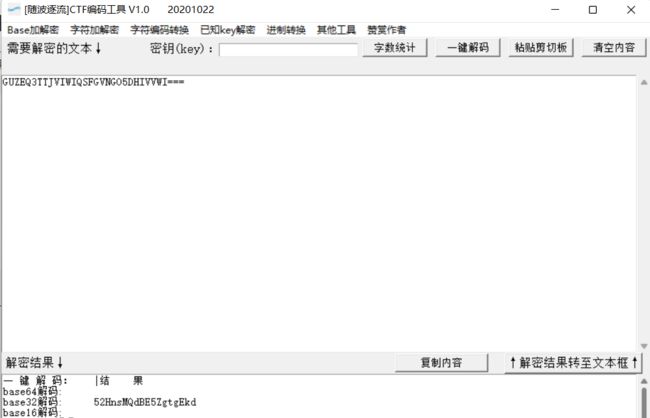
base32解码得到52HnsMQdBE5ZgtgEkd
再次base58解码得到0JkOs1H8i%3A^
再次base85(a)解码得到042f38b694
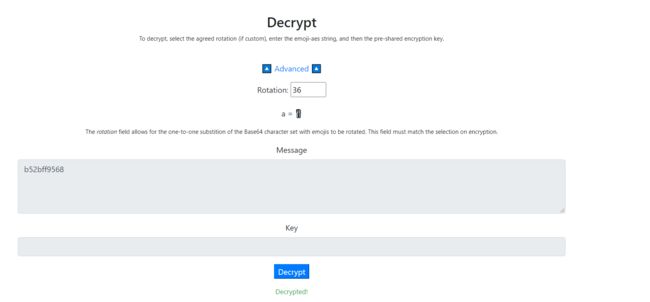
flag_2.txt:b52bff9568
Key可以直接base100解码得到whhjno
然后进入emoji-aes解密网站 https://aghorler.github.io/emoji-aes/
直接解密不行,于是尝试进阶移位,调试到36位的时候,可以成功解密得到b52bff9568
flag_3.txt
打开得到一串字符,丢到随波逐流里面一键解码
发现是base91,解码得到:37f267472516
U3RlZ2Fub2dyYXBoeSBpcyB0aGUgYXJ0IGFuZCBzY2llbmNlIG9m
IHdyaXRpbmcgaGlkZGVuIG1lc3NhZ2VzIGluIHN1Y2ggYSB3YXkgdGhhdCBubyBvbmU=
LCBhcGFydCBmcm9tIHRoZSBzZW5kZXIgYW5kIGludGVuZGVkIHJlY2lwaWVudCwgc3VzcGX=
Y3RzIHRoZSBleGlzdGVuY2Ugb2YgdGhlIG1lc3M=
YWdlLCBhIGZvcm0gb2Ygc2VjdXJpdHkgdGhyb3VnaCBvYnNjdXJpdHkuIFT=
aGUgd29yZCBzdGVnYW5vZ3JhcGh5IGlzIG9mIEdyZWVrIG9yaWdpbiBhbmTgbWVhbnMgImNvbmNlYT==
bGVkIHdyaXRpbmciIGZyb20gdGhlIEdyZWVrIHdvcmRzIHN0ZWdhbm9zIG1lYW5pbmcgImNv
dmVyZWQgb3IgdHJvdGVjdGVkIiwgYW5kIGdyYXBoZWluIG1lYW5pbmdgInRvIHd=
cml0ZSIuIFRoZSBmaXJzdCByZWNvcmRlZCB1c2Ugb2YgdGhlIHRlcm0gd2FzIGluIDE0OTkgYnkgSm9o
YW5uZXMgVHJpdGhlbWl1cyBpbiBoaXMgU3RlZ2Fub2dyYXBoaWEsIGEgdHJlYd==
dGlzZSBvbiBjcnl5dG9ncmF5aHkgYW5kIHN0ZWdhbm9ncmF5aHkgZGlzZ5==
dWlzZWQgYXOgYSBib29rIG9uIG1hZ2ljLiBHZW5lcmFsbHksIG1lc3O=
YWdlcyB3aWxsIGFwcGVhciB0byBiZSBzb21ldGhpbmcgZWxzZTogaW1hZ2VzLCBhcnRp
Y2xlcywgc2hvcHBpbmcgbGlzdHMsIG9yIHNvbWUgb3Q=
aGVyIGNvdmVydGV4dCBhbmQsIGNsYXNzaWNhbGx5LCB0aGUgaGlnZGVuIG1lc3NhZ2UgbWF5IGJlIGluIGludmn=
c2libGUgaW5rIGJldHdlZW4gdGhlIHZpc2libGUgbGluZXMgb2YgYSBwcml2YXRlIGxldHRlci4=
VGhlIGFkdmFudGFnZSBvZiBzdGVnYW5vZ3JhcGh5LCBvdmVyIGNy
eXB0b2dyYXBoeSBhbG9uZSwgaXMgdGhhdCBtZXNzYWdlcyBkbyBub3QgYXR0cmFjdCBhdHRlbnRpb26=
IHRvIHRoZW1zZWx2ZXMuIFBsYWlubHkgdmlzaWJsZSBlbmNyeXB0ZWQgbWVzc2FnZXPogbRubyBtYXR0ZXIg
aG93IHVuYnJlYWthYmxl6IG0d2lsbCBhcm91c2Ugcz==
dXNwaWNpb24sIGFuZCBtYXkgaW4gdGhlbXNlbHZlcyBiZSBpbmNyaW1pbmF0aW5nIG==
aW4gY291bnRyaWVzIHdoZXJlIGVuY3J5cHRpb24gaXMgaWxsZWdhbC4gVGhlcmVmb3JlLD==
IHdoZXJlYXMnY3J5cHRvZ3JhcGh5IHByb3RlY3RzIHRoZSBjb250ZW50cyBvZn==
IGEgbWVzc2FnZSwgc3RlZ2Fub2dyYXBoeSBjYW4gYmUgc2FpZCB0byBwcm90ZWN0IGI=
b3RoIG1lc3NhZ2VzIGFuZCBjb21tdW5pY2F0aW5nIHBhcnRpZXMu
U3RlZ2Fub2dyYXBoeSBpbmNsdWRlcyD=
dGhlIGNvbmNlYWxtZW51IG9mIGluZm9ybWF1aW9uIHdpdGhpbiBjb21=
cHV0ZXIgZmlsZXMuIEluIGRpZ2l0YWwgc3RlZ2Fub2dyYXBoeSwgZWxlY3Ryb25pYyBjb21tdW5pY2F0aW9u
cyBtYXkgaW5jbHVkZSBzdGVnYW5vZ3JhcGhpYyBjb2RpbmcgaW5zaQ==
ZGUgb2YgYSB0cmFuc3BvcnQgbGF5ZXIsIHN1Y2ggYXMgYSBkb2N1bWVudCBmaWxlLCBpbWFnZSBmaWz=
ZSwgcHJvZ3JhbSBvciBwcm90b2NvbC4gTWVkaWEg
ZmlsZXMgYXJlIGlkZWFsIGZvciBzdGVnYW5vZ3JhcGhpYyB0cmFuc21pc3Npb3==
biBiZWNhdXNlIG9mIHRoZWlyIGxhcmdlIHNpemUuIEFzID==
YSBzaW1wbGUgZXhhbXBsZSwgYSBzZW5kZXIgbWlnaHQgc3RhcnQgd2l0aCBh
biBpbm5vY3VvdXMgaW1hZ2UgZmlsZSBhbmQgYWRqdXN0IHRoZSBjb2xvciBvZiBldmVyeSAxMDB0aCBwaXhlbCA=
dG8gY29ycmVzcG9uZCB0byBhIGxldHRlciBpbiB0aGUgYWxwaGFiZXQsIGG=
IGNoYW5nZSBzbyBzdWJ0bGUgdGhhdCBzb21lb25lIG5vdCBzcGVjaWZpY2FsbHkgbG9va2luZyBm
b3IjaXQjaXMjdW5saWtlbHkjdG8jbm90aWNlIGl0Lj==
VGhlJGZpcnN0JHJlY29yZGVkJHVzZXMgb2Ygc3RlZ2Fub2dyYXBoeSBjYW4gYmUgdHJ=
YWNlZCBiYWNrIHRvIDQ0MCBCQyB3aGVuIEhlcm9kb3R1cyBtZW50aW9ucyB0d28gZXhhbXBsZXMgb0==
ZiBzdGVnYW5vZ3JhcGh5IGluIFRoZSBIaXN0b3JpZXMgb2Yg
SGVyb2RvdHVzLiBEZW1hcmF0dXMgc2VudCBhIHdhcm5pbmcgYWJvdXQgYSD=
Zm9ydGhjb21pbmcgYXR0YWNrIHRvIEdyZWVjZSBieSB3
cml0aW5nIGl0IGRpcmVjdGx5IG9uIHRoZSB3b29kZW4gYmFja2luZyBvZiBhIHdheCB0YWJsZXQgYmVm
b3JlIGFwcGx5aW5nIGl0cyBiZWVzd2F4IHN1cmZhY2UuIFdheCB0YWJsZXRzIHdlcmUgaW4gY29tbW9uIHVzZR==
IHRoZW4gYXMgcmV1c2FibGUgd3JpdGluZyBzdXJmYWNlcywgc29tZXRpbWU=
c3VzZWQgZm9yIHNob3J0aGFuZC4gQW5vdGhlciBhbmNpZW50IGV4YW1wbGUgaXMgdGhhdCBv
Zkhpc3RpYWV1cywgd2hvIHNoYXZlZCB0aGUgaGVhZCBvZiBoaXPgbW9zdCB0cnVzdGVkIHP=
bGF2ZSBhbmQgdGF0dG9vZWQgYSBtZXNzYWdlIG9uIGl0LiBBZnRlciBoaXMgaGFpciBoYWQgZ2==
cm93biB0aGUgbWVzc2FnZSB3YXMgaGlkZGVuLiBUaGUgcHVycG9zZSB3YXMgdG8=
aW5zdGlnYXRlIGEgcmV2b2x0IGFnYWluc3QgdGhlIFBlcnNpYW5zLg==
U3RlZ2Fub2dyYXBoeSBoYXMgYmVlbiB3aWRlbHkgdXNlZCwg
aW5jbHVkaW5nIGluIHJlY2VudCBoaXN0b3JpY2FsIHRpbWVzIGFuZCB0
aGUgcHJlc2VudCBkYXkuIFBvc3NpYmxlIHBlcm11dGF0aW9ucyBhcmUgZW5kbGVzcyBhbmQ=
a25vd24gZXhhbXBsZXMgaW5jbHVkZTo=
SGlkZGVuIG1lc3NhZ2VzIHdpdGhpbiB3YXggdGE=
YmxldHM6IGluIGFuY2llbnQgR3JlZWNlLCBwZW9wbGUgd3JvdGUgbWU=
c3NhZ2VzIG9uIHRoZSB3b29kLCB0aGVuIGNvdmVyZWQgaXQgd2l0aCB3YXggdXBvbiB3aGljaCBhbiBpbm5vY2Vu
dCBjb3ZlcmluZyBtZXNzYWdlIHdhcyB3cml0dGVu
SGlkZGVuIG1lc3NhZ2VzIG9uIG1lc3NlbmdlcidzIGJvZHk6IGFsc28gdXNlZCBpbiBhbmNpZW4=
再次base64解码得到
Steganography is the art and science of writing hidden messages in such a way that no one
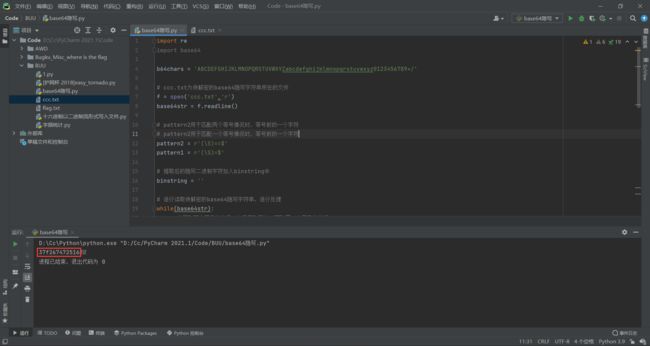
这么长的base64 不可能只得到这么一串英文,所以猜测base64隐写,通过python脚本得到37f267472516
脚本如下:
import re
import base64
b64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'
# ccc.txt为待解密的base64隐写字符串所在的文件
f = open('ccc.txt','r')
base64str = f.readline()
# pattern2用于匹配两个等号情况时,等号前的一个字符
# pattern2用于匹配一个等号情况时,等号前的一个字符
pattern2 = r'(\S)==$'
pattern1 = r'(\S)=$'
# 提取后的隐写二进制字符加入binstring中
binstring = ''
# 逐行读取待解密的base64隐写字符串,逐行处理
while(base64str):
# 先匹配两个等号的情况,如果匹配不上,再配置一个等号的情况
# 如果无等号,则没有隐藏,无需处理
if re.compile(pattern2).findall(base64str):
# mstr为等号前的一个字符,该字符为隐写二进制信息所在的字符
mstr = re.compile(pattern2).findall(base64str)[0]
# 确认mstr字符对应的base64二进制数,赋值给mbin
mbin = bin(b64chars.find(mstr))
# mbin格式如0b100,mbin[0:2]为0b
# mbin[2:].zfill(6)为将0b后面的二进制数前面补0,使0b后面的长度为6
mbin2 = mbin[0:2] + mbin[2:].zfill(6)
# 两个等号情况隐写了4位二进制数,所以提取mbin2的后4bit
# 赋值给stegobin,这就是隐藏的二进制信息
stegobin = mbin2[-4:]
binstring += stegobin
elif re.compile(pattern1).findall(base64str):
mstr = re.compile(pattern1).findall(base64str)[0]
mbin = bin(b64chars.find(mstr))
mbin2 = mbin[0:2] + mbin[2:].zfill(6)
# 一个等号情况隐写了2位二进制数,所以提取mbin2的后2bit
stegobin = mbin2[-2:]
binstring += stegobin
base64str = f.readline()
# stegobin将各行隐藏的二进制字符拼接在一起
# 从第0位开始,8bit、8bit处理,所以range的步进为8
for i in range(0,len(binstring),8):
# int(xxx,2),将二进制字符串转换为10进制的整数,再用chr()转为字符
print(chr(int(binstring[i:i+8],2)),end='')
所以flag为:
flag{042f38b694b52bff956837f267472516}
Misc3:huahua
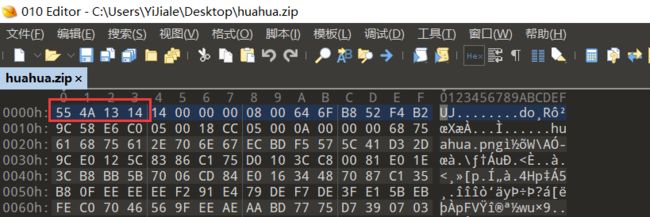
下载附件得到huahua.zip,但是打不开,于是丢到010中分析结构,发现文件头异常,正常的zip文件头是50 4B 03 04
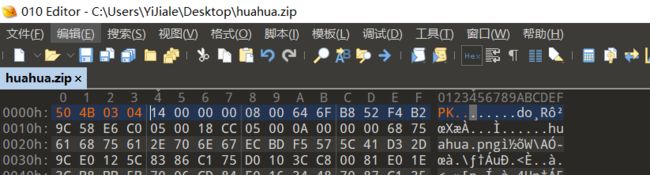
保存之后,重新打开得到一张huahua.png,同样的图片也打不开,丢入010

正常的49前面应该是89 50 4E 47 0D 0A 1A 0A 00 00 00 0D,huahua.png缺少了89 50 4E 47
填上文件头后打开得到正常的图片
修改高度得到flag
所以flag为:
flag{b3afc91a8fbb6cc798bdebb253b02550}
Misc4:NOISE
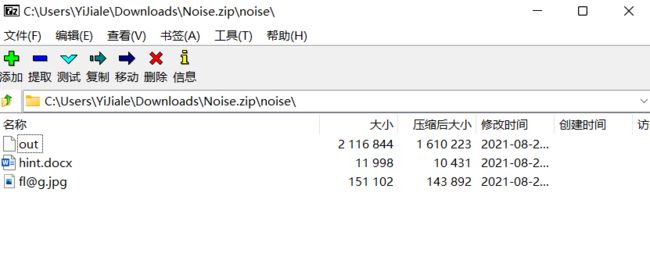
下载附件,里面有3个文件,其中out文件,丢入010分析发现是wav音频文件
将out文件加上.wav后缀,然后用Audacity打开,分析频谱图,得到flag
所以flag为:
flag{98ce526ad52c409763405847185d9c6c}
Misc5:DdDdDd
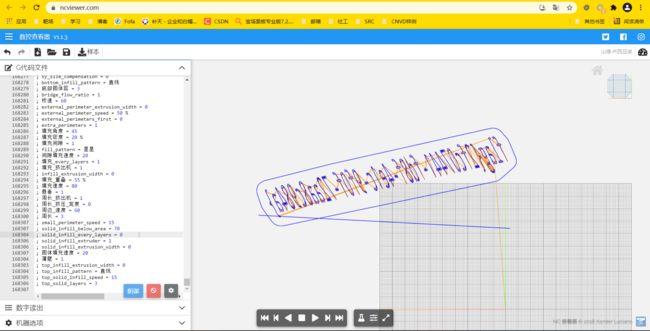
打开流量包,导出http流量,发现Smashing%20Wolt.gcode是G语言
使用https://ncviewer.com/网站在线编译
右上角可以调角度,得到翻转的flag,截图下来,用在线工具https://www.91gif.com/giffanzuan/ 可以镜像翻转过来
得到flag为:
flag{2fc07441-fd8f-4e1c-9f0f-72aa8c984a}
Misc6:Forensic
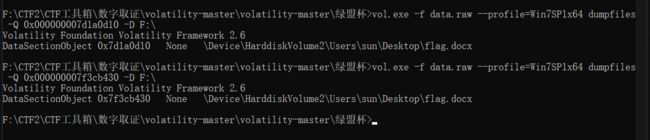
下载附件,用vol.exe对内存分析,直接查找带有flag字样的文件
命令:
vol.exe -f data.raw --profile=Win7SP1x64 filescan |findstr /r "flag"
一共有两个flag.docx,个flag.zip,其中一个flag.zip导不出来,一个flag.docx里面是base64,但是隐藏了的
取消隐藏,解密得到flag:
flag{9017cef26a07beb4e669a4a806bcd9b6}
Misc7:隐藏的数据
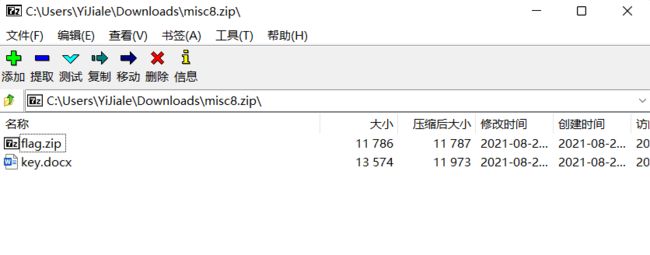
下载附件,得到一个flag.zip和一个word文档
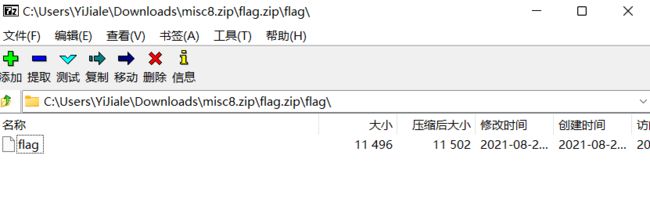
打开flag.zip,发现里面是flag文件,丢入010分析发现是伪加密的压缩包,但是7z可以无视伪加密,所以直接打开,里面又是一个flag文件
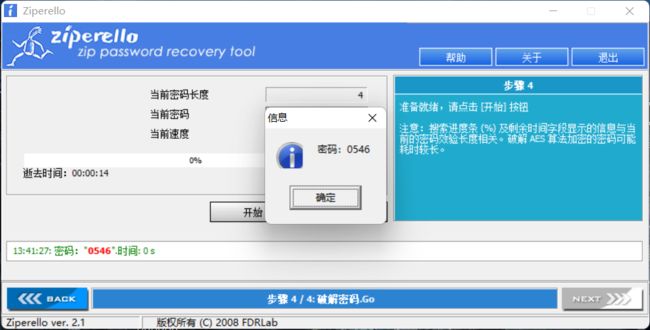
再次打开发现需要密码,爆破一下,得到密码为0546
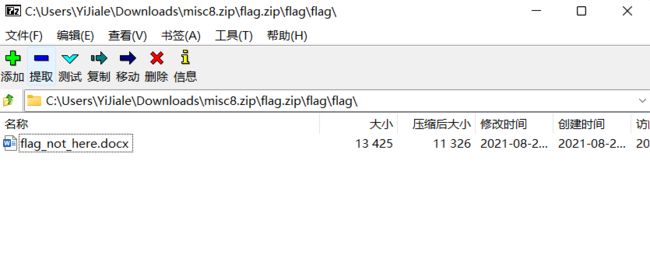
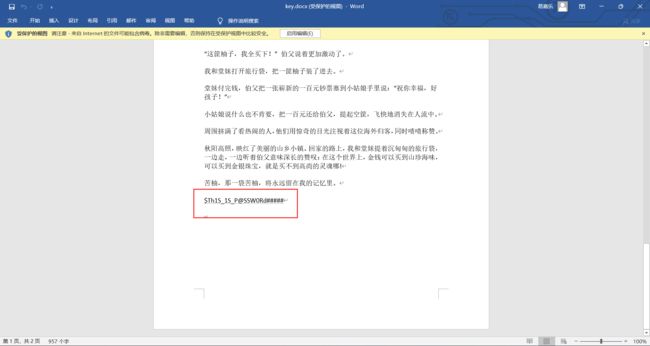
打开压缩包得到flag_not_here.docx,尝试打开,发现需要密码,爆破不出来,于是想到一开始的word文档还没打开过
打开里面有一个密码$Th1S_1S_P@SSW0Rd#####
用这个密码可以打开刚刚那个flag_not_here.docx
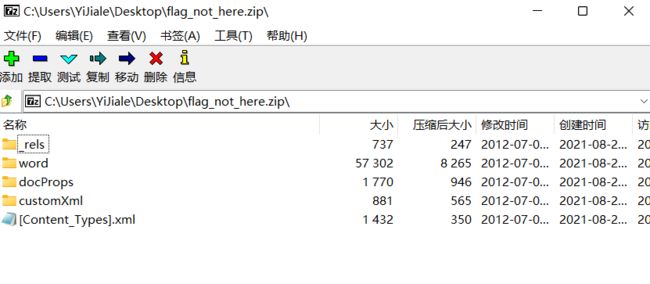
里面什么东西都没有发现,于是把.docx改为.zip 然后去打开压缩包 查看word文档的结构
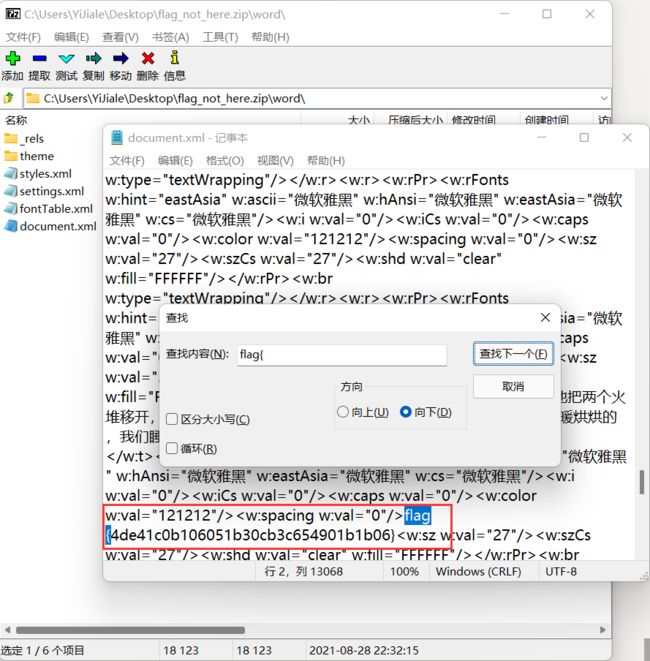
在document.xml中找到了flag:
flag{4de41c0b106051b30cb3c654901b1b06}
Misc8:something in picture
这题是第五届强网杯Threebody原题,贴一个原题wp链接吧 https://www.sohu.com/a/472787619_121118996
flag:
flag{D1mEn5i0nAl_Pr061em}