HTTPS请求握手失败javax.net.ssl.SSLHandshakeException: Received fatal alert: handshake_failu
报错信息:
main, handling exception: javax.net.ssl.SSLHandshakeException: Received fatal alert: handshake_failure
错误解析:https请求时三次握手失败

分析原因:因为我司使用jdk1.8,而对方对接公司使用jdk7
什么操作都不做的情况下报错如下图:
main, handling exception: javax.net.ssl.SSLException: Received fatal alert: protocol_version
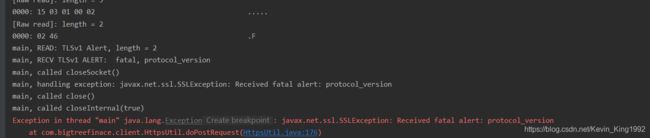
明显是客户端与服务端TLS版本不一致导致的,1.8默认是TLSv1.2,1.7默认支持是TLSv1;
解决的办法很多:
1.启动jvm加参数:-Dhttps.protocols=TLSv1.2,TLSv1.1
2.http发送的时候,设置,如:
SSLContext sslContext = SSLContexts.createDefault();
SSLConnectionSocketFactory sslsf = new SSLConnectionSocketFactory(sslContext,
new String[]{
"TLSv1.2","TLSv1.1","TLSv1","SSLv3"},
null,
new NoopHostnameVerifier());
CloseableHttpClient httpClient = HttpClients.custom()
.setSSLSocketFactory(sslsf)
.build();
System.setProperty("https.protocols", "TLSv1.2,TLSv1.1,TLSv1,SSLv3");
以上三种方法都可以解决TLSv1.2 报错protocol_version的问题;
解决完上面的protocol_version之后,会继续报文章开头握手的错误,解决方法如下:
解决方案第三方框架:Bouncy Castle
<dependency>
<groupId>org.bouncycastle</groupId>
<artifactId>bcprov-ext-jdk15on</artifactId>
<version>1.58</version>
</dependency>
import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.io.DataOutputStream;
import java.io.FileInputStream;
import java.io.IOException;
import java.io.InputStream;
import java.io.OutputStream;
import java.net.InetAddress;
import java.net.InetSocketAddress;
import java.net.Socket;
import java.net.UnknownHostException;
import java.security.KeyStore;
import java.security.Principal;
import java.security.SecureRandom;
import java.security.Security;
import java.security.cert.CertificateExpiredException;
import java.security.cert.CertificateFactory;
import java.util.Hashtable;
import java.util.LinkedList;
import java.util.List;
import javax.net.ssl.HandshakeCompletedListener;
import javax.net.ssl.SSLPeerUnverifiedException;
import javax.net.ssl.SSLSession;
import javax.net.ssl.SSLSessionContext;
import javax.net.ssl.SSLSocket;
import javax.net.ssl.SSLSocketFactory;
import javax.security.cert.X509Certificate;
import org.bouncycastle.crypto.tls.*;
import org.bouncycastle.crypto.tls.Certificate;
import org.bouncycastle.jce.provider.BouncyCastleProvider;
public class TLSSocketConnectionFactory extends SSLSocketFactory {
static {
if (Security.getProvider(BouncyCastleProvider.PROVIDER_NAME) == null) {
Security.addProvider(new BouncyCastleProvider());
}
}
@Override
public Socket createSocket(Socket socket, final String host, int port,
boolean arg3) throws IOException {
if (socket == null) {
socket = new Socket();
}
if (!socket.isConnected()) {
socket.connect(new InetSocketAddress(host, port));
}
final TlsClientProtocol tlsClientProtocol = new TlsClientProtocol(socket.getInputStream(), socket.getOutputStream(), new SecureRandom());
return _createSSLSocket(host, tlsClientProtocol);
}
@Override
public String[] getDefaultCipherSuites() {
return null;
}
@Override
public String[] getSupportedCipherSuites() {
return null;
}
@Override
public Socket createSocket(String host, int port) throws IOException, UnknownHostException {
throw new UnsupportedOperationException();
}
@Override
public Socket createSocket(InetAddress host, int port) throws IOException {
throw new UnsupportedOperationException();
}
@Override
public Socket createSocket(String host, int port, InetAddress localHost, int localPort) throws IOException, UnknownHostException {
return null;
}
@Override
public Socket createSocket(InetAddress address, int port, InetAddress localAddress, int localPort) throws IOException {
throw new UnsupportedOperationException();
}
private SSLSocket _createSSLSocket(final String host, final TlsClientProtocol tlsClientProtocol) {
return new SSLSocket() {
private java.security.cert.Certificate[] peertCerts;
@Override
public InputStream getInputStream() throws IOException {
return tlsClientProtocol.getInputStream();
}
@Override
public OutputStream getOutputStream() throws IOException {
return tlsClientProtocol.getOutputStream();
}
@Override
public synchronized void close() throws IOException {
tlsClientProtocol.close();
}
@Override
public void addHandshakeCompletedListener(HandshakeCompletedListener arg0) {
}
@Override
public boolean getEnableSessionCreation() {
return false;
}
@Override
public String[] getEnabledCipherSuites() {
return null;
}
@Override
public String[] getEnabledProtocols() {
return null;
}
@Override
public boolean getNeedClientAuth() {
return false;
}
@Override
public SSLSession getSession() {
return new SSLSession() {
@Override
public int getApplicationBufferSize() {
return 0;
}
@Override
public String getCipherSuite() {
throw new UnsupportedOperationException();
}
@Override
public long getCreationTime() {
throw new UnsupportedOperationException();
}
@Override
public byte[] getId() {
throw new UnsupportedOperationException();
}
@Override
public long getLastAccessedTime() {
throw new UnsupportedOperationException();
}
@Override
public java.security.cert.Certificate[] getLocalCertificates() {
throw new UnsupportedOperationException();
}
@Override
public Principal getLocalPrincipal() {
throw new UnsupportedOperationException();
}
@Override
public int getPacketBufferSize() {
throw new UnsupportedOperationException();
}
@Override
public X509Certificate[] getPeerCertificateChain() throws SSLPeerUnverifiedException {
return null;
}
@Override
public java.security.cert.Certificate[] getPeerCertificates() throws SSLPeerUnverifiedException {
return peertCerts;
}
@Override
public String getPeerHost() {
throw new UnsupportedOperationException();
}
@Override
public int getPeerPort() {
return 0;
}
@Override
public Principal getPeerPrincipal() throws SSLPeerUnverifiedException {
return null;
}
@Override
public String getProtocol() {
throw new UnsupportedOperationException();
}
@Override
public SSLSessionContext getSessionContext() {
throw new UnsupportedOperationException();
}
@Override
public Object getValue(String arg0) {
throw new UnsupportedOperationException();
}
@Override
public String[] getValueNames() {
throw new UnsupportedOperationException();
}
@Override
public void invalidate() {
throw new UnsupportedOperationException();
}
@Override
public boolean isValid() {
throw new UnsupportedOperationException();
}
@Override
public void putValue(String arg0, Object arg1) {
throw new UnsupportedOperationException();
}
@Override
public void removeValue(String arg0) {
throw new UnsupportedOperationException();
}
};
}
@Override
public String[] getSupportedProtocols() {
return null;
}
@Override
public boolean getUseClientMode() {
return false;
}
@Override
public boolean getWantClientAuth() {
return false;
}
@Override
public void removeHandshakeCompletedListener(HandshakeCompletedListener arg0) {
}
@Override
public void setEnableSessionCreation(boolean arg0) {
}
@Override
public void setEnabledCipherSuites(String[] arg0) {
}
@Override
public void setEnabledProtocols(String[] arg0) {
}
@Override
public void setNeedClientAuth(boolean arg0) {
}
@Override
public void setUseClientMode(boolean arg0) {
}
@Override
public void setWantClientAuth(boolean arg0) {
}
@Override
public String[] getSupportedCipherSuites() {
return null;
}
@Override
public void startHandshake() throws IOException {
tlsClientProtocol.connect(new DefaultTlsClient() {
@SuppressWarnings("unchecked")
@Override
public Hashtable<Integer, byte[]> getClientExtensions() throws IOException {
Hashtable<Integer, byte[]> clientExtensions = super.getClientExtensions();
if (clientExtensions == null) {
clientExtensions = new Hashtable<Integer, byte[]>();
}
//Add host_name
byte[] host_name = host.getBytes();
final ByteArrayOutputStream baos = new ByteArrayOutputStream();
final DataOutputStream dos = new DataOutputStream(baos);
dos.writeShort(host_name.length + 3);
dos.writeByte(0);
dos.writeShort(host_name.length);
dos.write(host_name);
dos.close();
clientExtensions.put(ExtensionType.server_name, baos.toByteArray());
return clientExtensions;
}
@Override
public TlsAuthentication getAuthentication() throws IOException {
return new TlsAuthentication() {
@Override
public void notifyServerCertificate(Certificate serverCertificate) throws IOException {
try {
KeyStore ks = _loadKeyStore();
CertificateFactory cf = CertificateFactory.getInstance("X.509");
List<java.security.cert.Certificate> certs = new LinkedList<java.security.cert.Certificate>();
boolean trustedCertificate = false;
for (org.bouncycastle.asn1.x509.Certificate c : ((org.bouncycastle.crypto.tls.Certificate) serverCertificate).getCertificateList()) {
java.security.cert.Certificate cert = cf.generateCertificate(new ByteArrayInputStream(c.getEncoded()));
certs.add(cert);
String alias = ks.getCertificateAlias(cert);
if (alias != null) {
if (cert instanceof java.security.cert.X509Certificate) {
try {
((java.security.cert.X509Certificate) cert).checkValidity();
trustedCertificate = true;
} catch (CertificateExpiredException cee) {
// Accept all the certs!
}
}
} else {
// Accept all the certs!
}
}
if (!trustedCertificate) {
// Accept all the certs!
}
peertCerts = certs.toArray(new java.security.cert.Certificate[0]);
} catch (Exception ex) {
ex.printStackTrace();
throw new IOException(ex);
}
}
@Override
public TlsCredentials getClientCredentials(CertificateRequest certificateRequest) throws IOException {
return null;
}
private KeyStore _loadKeyStore() throws Exception {
FileInputStream trustStoreFis = null;
try {
KeyStore localKeyStore = null;
String trustStoreType = System.getProperty("javax.net.ssl.trustStoreType") != null ? System.getProperty("javax.net.ssl.trustStoreType") : KeyStore.getDefaultType();
String trustStoreProvider = System.getProperty("javax.net.ssl.trustStoreProvider") != null ? System.getProperty("javax.net.ssl.trustStoreProvider") : "";
if (trustStoreType.length() != 0) {
if (trustStoreProvider.length() == 0) {
localKeyStore = KeyStore.getInstance(trustStoreType);
} else {
localKeyStore = KeyStore.getInstance(trustStoreType, trustStoreProvider);
}
char[] keyStorePass = null;
String str5 = System.getProperty("javax.net.ssl.trustStorePassword") != null ? System.getProperty("javax.net.ssl.trustStorePassword") : "";
if (str5.length() != 0) {
keyStorePass = str5.toCharArray();
}
localKeyStore.load(trustStoreFis, keyStorePass);
if (keyStorePass != null) {
for (int i = 0; i < keyStorePass.length; i++) {
keyStorePass[i] = 0;
}
}
}
return localKeyStore;
} finally {
if (trustStoreFis != null) {
trustStoreFis.close();
}
}
}
};
}
});
} // startHandshake
};
}
}
/**
* @author Kevin
*/
public class HttpsUrlConnectionForTLS {
public HttpURLConnection createConnection(URI uri) throws IOException {
URL url = uri.toURL();
URLConnection connection = url.openConnection();
HttpsURLConnection httpsURLConnection = (HttpsURLConnection) connection;
httpsURLConnection.setSSLSocketFactory(new TLSSocketConnectionFactory());
return httpsURLConnection;
}
public static void main(String[] args) throws Exception {
String apiUrl = BIGTREE_URL;
/*接口参数包装*/
String json = "{\"userName\":\"test\",\"userType\":\"02\"}";
Map paramMap = JSONObject.parseObject(json, Map.class);
String newparams = JSON.toJSONString(paramMap);
System.out.println(apiUrl);
/*每次接口调用生成随机加密字符串*/
String x_bigtree_nonce = Utils.makeRandomStr(16);
//AES加密(去掉空格和换行)
String aesJsonStr = Utils.encrypt(newparams, ACCESS_KEY, x_bigtree_nonce).replaceAll(REPLACE_STR, "");
//签名规则
String signRule = ACCESS_KEY + aesJsonStr + X_BIGTREE_APPID + x_bigtree_nonce;
//MD5签名(去掉空格和换行)
String sign = Utils.md5(signRule.replaceAll(REPLACE_STR, ""));
Map<String, String> param = new HashMap<String, String>();
param.put("data", URLEncoder.encode(aesJsonStr, "UTF-8"));
System.out.println("nonce:" + x_bigtree_nonce + ",sign:" + sign);
System.out.println("sign:" + sign);
System.out.println("data:" + param.get("data"));
System.out.println("requestParam:" + JSON.toJSONString(param));
// post请求是将参数放在请求体里面传过去的;这里将entity放入post请求体中
Map<String, String> headers = new HashMap<String, String>();
headers.put("Content-Type", "application/json;charset=utf8");
headers.put("x-bigtree-appid", X_BIGTREE_APPID);
headers.put("x-bigtree-nonce", x_bigtree_nonce);
headers.put("x-bigtree-sign", sign);
headers.put("Content-Type", "application/json;charset=utf-8");
doPost(apiUrl, JSON.toJSONString(param), headers);
}
private static void doPost(String url, String body, Map<String, String> headers) {
HttpsUrlConnectionForTLS httpsUrlConnectionMessageSender = new HttpsUrlConnectionForTLS();
HttpURLConnection connection;
try {
connection = httpsUrlConnectionMessageSender.createConnection(new URI(url));
connection.setDoOutput(true);
connection.setDoInput(true);
connection.setRequestMethod("POST");
connection.setUseCaches(false);
connection.setInstanceFollowRedirects(true);
if (headers != null && headers.size() > 0) {
for (String key : headers.keySet()) {
connection.setRequestProperty(key, headers.get(key));
}
}
connection.connect();
//POST请求
OutputStreamWriter os = null;
String json = "";
os = new OutputStreamWriter(connection.getOutputStream());
os.write(body);
os.flush();
json = getResponse(connection);
System.out.println(json);
if (connection != null) {
connection.disconnect();
}
} catch (IOException e) {
e.printStackTrace();
} catch (URISyntaxException e) {
e.printStackTrace();
}
}
public static String getResponse(HttpURLConnection Conn) throws IOException {
InputStream is;
if (Conn.getResponseCode() >= 400) {
is = Conn.getErrorStream();
} else {
is = Conn.getInputStream();
}
String response = "";
byte buff[] = new byte[512];
int b = 0;
while ((b = is.read(buff, 0, buff.length)) != -1) {
response += new String(buff, 0, b);
}
is.close();
return response;
}
}
参考:https://www.iteye.com/blog/ligaosong-2356346