linux cpu飙高到100%----中了挖矿程序
感谢:简书SilentBillows
一 定位问题
1.发现cpu异常,查看对应的进程信息
[root@versionlibrary /]# top
top - 10:56:10 up 15 min, 1 user, load average: 7.28, 7.24, 4.90
Tasks: 209 total, 5 running, 204 sleeping, 0 stopped, 0 zombie
%Cpu(s): 96.5 us, 3.5 sy, 0.0 ni, 0.0 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st
KiB Mem : 14350456 total, 9786680 free, 3711836 used, 851940 buff/cache
KiB Swap: 0 total, 0 free, 0 used. 10211252 avail Mem
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
2588 root 20 0 427364 10708 2160 S 351.1 0.1 37:09.70 trace
3146 git 20 0 721696 472444 3584 R 23.8 3.3 0:05.11 bundle
3913 root 20 0 160904 5656 4308 S 6.5 0.0 0:00.28 sshd
3926 git 20 0 15260 992 824 R 6.5 0.0 0:00.20 git-upload-pack
1573 git 20 0 741896 472932 6100 S 3.3 3.3 0:06.82 bundle
1247 root 20 0 7440132 1.0g 33756 S 1.3 7.3 1:24.70 java
1 root 20 0 128096 6612 4128 S 1.0 0.0 0:03.30 systemd
2.查看进程发现是挖矿进程在执行
[root@versionlibrary /]# ps -aux|grep trace
root 2588 393 0.0 427364 10708 ? Sl 10:46 47:20 ./trace --algo cn/double -r 32 -R 32 --keepalive --no-color --donate-level 1 --max-cpu-usage 95 --cpu-priority 3 --print-time 25 --threads 4 --url xcash.herominers.com:10441 --user XCBzxb7igt5YvbwtYCMPkEWRATpzrMYvU2PpTDi89bon7fYnJgYSeRS8EN5LLnPxgkgfsf3k1DZVn1bzccTFBNhpPGbJGBh1dBkirZd6xsV2GE --pass 82b08f03 --keepalive
root 4276 0.0 0.0 112704 988 pts/0 S+ 10:58 0:00 grep --color=auto trace
3.确定是挖矿病毒,查看进程的执行文件链接到哪里,发现是jenkins的工作目录,最后结果发现是jenkins的漏洞导致自动创建CI计划,进行启动挖矿脚本
[root@versionlibrary /]# ls -l /proc/2588/exe
lrwxrwxrwx. 1 root root 0 May 9 11:02 /proc/2588/exe -> /var/lib/jenkins/jobs/Jenkins
4.查看虚机密码是否被破解登录
如果发现未知ip登录需要及时更换密码
[root@versionlibrary tmp]# last
pmpd pts/0 139.219.10.210 Thu May 9 10:43 still logged in
reboot system boot 3.10.0-862.11.6. Thu May 9 10:40 - 15:37 (04:56)
wtmp begins Thu May 9 10:38:19 2019
5.查找挖矿文件
挖矿问价一般是会存在 tmp目录下,tmp目录的访问权限是最大的,以下为99sy
[root@versionlibrary tmp]# ls
99sy gitaly-ruby543509877 jna4381594195372702638jar tmpWL1Ry7
akuma2730798493513952938jar hsperfdata_root moni.lod winstone2324068653960260627.jar
cmd.n jetty-0.0.0.0-8888-war-_-any-4425982404102692602.dir systemd-private-5f9d4e2c4e0344579491ce38011cc2ff-chronyd.service-Ncy1Um winstone6735906110175988793.jar
conf.n jetty-0.0.0.0-8888-war-_-any-997583922652054084.dir tmp0F_O0f
gates.lod jna-3506402
6.检查定时任务脚本
一般矿机病毒创建定时脚本来恢复被删除的矿机程序和矿机程序的恢复,重启.
[root@versionlibrary tmp]# crontab -l
0 3 * * * /bin/sh /root/backup.sh
二,解决问题
找到问题导致的原因之后就能够针对这些原因去修复.
- 第一时间先切断外出的流量,及时止损,确定损失范围(目前权限原因损失的是出口流量)
- 增强对于流量出口的限制.像目前网上已经暴露的一些矿机池的IP源.
- 修改服务器密码,找到矿机程序并删除,检查是否有非自己创建的定时任务
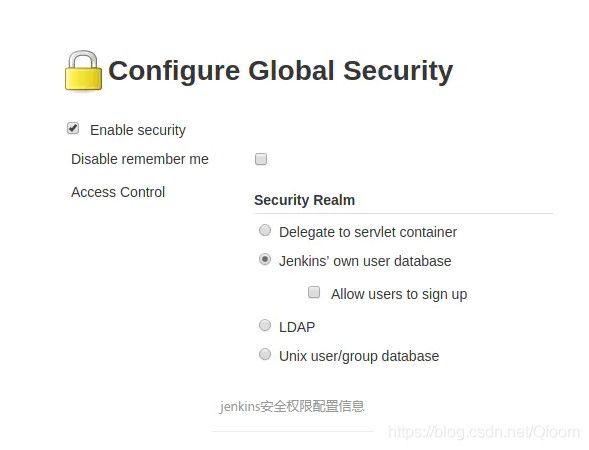
- 针对本次矿机的植入原因是jenkins的高威漏洞(CVE-2018-1999002,CVE-2018-1999043)导致,仔细排查,此次中招的是漏洞是CVE-2018-1999043漏洞,升级到最新的jenkins,修改jenkins的配置
针对高危漏洞CVE-2018-1999002,需要开启Enable security 和取消 Allow users to sign up的选项
三 防范
- jenkins,nexus,redis 都存在可能植入矿机程序的漏洞,对应的服务器做好流量的出入控制.
- 定时修复服务器的密码,关注对应漏洞的发布和及时响应针对漏洞的版本升级.
- jenkins可能通过跨域访问植入(访问了恶意网站导致jenkins cookie泄露 ),chrome的话可以载入一些检测挖矿脚本的插件,推荐两个
MinerBlock
github地址:https://github.com/xd4rker/MinerBlock
No Coin
github地址:https://github.com/keraf/NoCoin/
ps:不会用,下载下来之后