话不多说,直接拖进IDA, F5 查看主函数伪C代码,这里打印21个字符串。
v0 = sub_8048460(dword_804A03C);
printf("%c", v0);
fflush(stdout);
v1 = sub_8048460(dword_804A044);
printf("%c", v1);
fflush(stdout);
v2 = sub_8048460(dword_804A0E0);
printf("%c", v2);
fflush(stdout);
v3 = sub_8048460(dword_804A050);
printf("%c", v3);
fflush(stdout);
v4 = sub_8048460(dword_804A058);
printf("%c", v4);
fflush(stdout);
v5 = sub_8048460(dword_804A0E4);
printf("%c", v5);
fflush(stdout);
v6 = sub_8048460(dword_804A064);
printf("%c", v6);
fflush(stdout);
v7 = sub_8048460(dword_804A0E8);
printf("%c", v7);
fflush(stdout);
v8 = sub_8048460(dword_804A070);
printf("%c", v8);
fflush(stdout);
v9 = sub_8048460(dword_804A078);
printf("%c", v9);
fflush(stdout);
v10 = sub_8048460(dword_804A080);
printf("%c", v10);
fflush(stdout);
v11 = sub_8048460(dword_804A088);
printf("%c", v11);
fflush(stdout);
v12 = sub_8048460(dword_804A090);
printf("%c", v12);
fflush(stdout);
v13 = sub_8048460(dword_804A098);
printf("%c", v13);
fflush(stdout);
v14 = sub_8048460(dword_804A0A0);
printf("%c", v14);
fflush(stdout);
v15 = sub_8048460(dword_804A0A8);
printf("%c", v15);
fflush(stdout);
v16 = sub_8048460(dword_804A0B0);
printf("%c", v16);
fflush(stdout);
v17 = sub_8048460(dword_804A0B8);
printf("%c", v17);
fflush(stdout);
v18 = sub_8048460(dword_804A0C0);
printf("%c", v18);
fflush(stdout);
v19 = sub_8048460(dword_804A0C8);
printf("%c", v19);
fflush(stdout);
v20 = sub_8048460(dword_804A0D0);
printf("%c", v20);
fflush(stdout);
printf("\n");
return 0;
}
在分析sub_8048460函数:
switch ( a1 )
{
case 0:
v2 = byte_804A021 ^ byte_804A020;
break;
case 1:
v2 = byte_804A023 ^ byte_804A022;
break;
case 2:
v2 = byte_804A025 ^ byte_804A024;
break;
case 3:
v2 = byte_804A027 ^ byte_804A026;
break;
case 4:
v2 = byte_804A029 ^ byte_804A028;
break;
case 5:
v2 = byte_804A02B ^ byte_804A02A;
break;
case 6:
v2 = byte_804A02D ^ byte_804A02C;
break;
case 7:
v2 = byte_804A02F ^ byte_804A02E;
break;
case 8:
v2 = byte_804A031 ^ byte_804A030;
break;
case 9:
v2 = byte_804A033 ^ byte_804A032;
break;
case 10:
v2 = byte_804A035 ^ byte_804A034;
break;
case 11:
v2 = byte_804A037 ^ byte_804A036;
break;
case 12:
v2 = byte_804A039 ^ byte_804A038;
break;
case 13:
v2 = byte_804A03B ^ byte_804A03A;
break;
default:
v2 = 0;
break;
}
return v2;
}
参看大佬文章,发现全是奇地址 ^ 偶地址,并且前四个按照之间参数顺序传进sub_8048460所触发的case语句的偶地址对应的字符串会得到 f l * g 。
已知了所有偶地址存储的值和18个传进sub_8048460的参数,还有dword_804A0E0,dword_804A0E4,dword_804A0E8未知,不过没关系。写个脚本先把已知的算出来一下。
a ={
"0":0x61,
"1":0x67,
"2":0x69,
"3":0x6e,
"4":0x62,
"5":0x65,
"6":0x66,
"7":0x6a,
"8":0x6d,
"9":0x6c,
"a":0x7b,
"b":0x7a,
"c":0x7d,
"d":0x5f
}
b = "691a8b231d4527231c"
c="0123456789abc"
flag = ""
for i in b:
flag += chr(a[i])
print(flag)
emmmmm,脑洞一下。
猜测一下结果为:flag{amzing_beijing}.
想要实在点儿,那就爆破吧,再上脚本。
a ={
"0":0x61,
"1":0x67,
"2":0x69,
"3":0x6e,
"4":0x62,
"5":0x65,
"6":0x66,
"7":0x6a,
"8":0x6d,
"9":0x6c,
"a":0x7b,
"b":0x7a,
"c":0x7d,
"d":0x5f
}
b = "69{q}1a{w}8{e}b231d4527231c"
c="0123456789abc"
flag = ""
for i in c:
for j in c:
for k in c:
b = b.format(q=i,w=j,e=k)
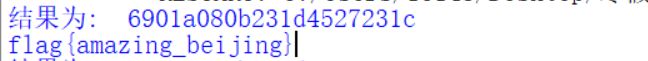
print("结果为: ",b)
for i in b:
flag += chr(a[i])
print(flag)
得到结果:flag{amzing_beijing}.