[root@logstash-1 tmp]# yum install -y openldap openldap-*
[root@logstash-1 tmp]# rpm -qa | grep ldap
openldap-2.4.44-25.el7_9.x86_64
openldap-servers-sql-2.4.44-25.el7_9.x86_64
openldap-devel-2.4.44-25.el7_9.x86_64
openldap-clients-2.4.44-25.el7_9.x86_64
openldap-servers-2.4.44-25.el7_9.x86_64
[root@logstash-1 tmp]# systemctl start slapd
[root@logstash-1 tmp]# systemctl status slapd
● slapd.service - OpenLDAP Server Daemon
Loaded: loaded (/usr/lib/systemd/system/slapd.service; disabled; vendor preset: disabled)
Active: active (running) since 三 2022-03-23 12:10:13 CST; 16s ago
Docs: man:slapd
man:slapd-config
man:slapd-hdb
man:slapd-mdb
file:///usr/share/doc/openldap-servers/guide.html
Process: 32127 ExecStart=/usr/sbin/slapd -u ldap -h ${SLAPD_URLS} $SLAPD_OPTIONS (code=exited, status=0/SUCCESS)
Process: 32112 ExecStartPre=/usr/libexec/openldap/check-config.sh (code=exited, status=0/SUCCESS)
Main PID: 32149 (slapd)
Tasks: 2
Memory: 10.6M
CGroup: /system.slice/slapd.service
└─32149 /usr/sbin/slapd -u ldap -h ldapi:/// ldap:///
3月 23 12:10:12 logstash-1 systemd[1]: Starting OpenLDAP Server Daemon...
3月 23 12:10:12 logstash-1 runuser[32115]: pam_unix(runuser:session): session opened for user ldap by (uid=0)
3月 23 12:10:12 logstash-1 runuser[32115]: pam_unix(runuser:session): session closed for user ldap
3月 23 12:10:12 logstash-1 slapd[32127]: @(#) $OpenLDAP: slapd 2.4.44 (Feb 23 2022 17:11:27) $
[email protected]:/builddir/build/BUILD/openldap-2.4.44/openldap-2.4.44/servers/slapd
3月 23 12:10:13 logstash-1 slapd[32127]: tlsmc_get_pin: INFO: Please note the extracted key file will not be protected with a PIN any more, however it will be still p...ermissions.
3月 23 12:10:13 logstash-1 slapd[32149]: hdb_db_open: warning - no DB_CONFIG file found in directory /var/lib/ldap: (2).
Expect poor performance for suffix "dc=my-domain,dc=com".
3月 23 12:10:13 logstash-1 slapd[32149]: slapd starting
3月 23 12:10:13 logstash-1 systemd[1]: Started OpenLDAP Server Daemon.
Hint: Some lines were ellipsized, use -l to show in full.
[root@logstash-1 tmp]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/
alock __db.001 __db.002 __db.003 dn2id.bdb id2entry.bdb log.0000000001
[root@logstash-1 tmp]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/
alock __db.001 __db.002 __db.003 dn2id.bdb id2entry.bdb log.0000000001
[root@logstash-1 tmp]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[root@logstash-1 tmp]# chown ldap:ldap /var/lib/ldap/DB_CONFIG
[root@logstash-1 tmp]# systemctl restart slapd
[root@logstash-1 tmp]# slappasswd
New password:
Re-enter new password:
{SSHA}xxJiWxxxxxxx[root@logstash-1 ~]# vim rootpwd.ldif
[root@logstash-1 ~]# cat rootpwd.ldif
dn: olcDatabase={0}config,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}xxJiWxxxxxxxxxx
[root@logstash-1 ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f rootpwd.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={0}config,cn=config"
[root@logstash-1 ~]# echo $?
0
[root@logstash-1 ~]# ls /etc/openldap/schema/*.ldif | while read f; do ldapadd -Y EXTERNAL -H ldapi:/// -f $f; done
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=collective,cn=schema,cn=config"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=corba,cn=schema,cn=config"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=core,cn=schema,cn=config"
ldap_add: Other (e.g., implementation specific) error (80)
additional info: olcAttributeTypes: Duplicate attributeType: "2.5.4.2"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=cosine,cn=schema,cn=config"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=duaconf,cn=schema,cn=config"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=dyngroup,cn=schema,cn=config"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=inetorgperson,cn=schema,cn=config"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=java,cn=schema,cn=config"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=misc,cn=schema,cn=config"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=nis,cn=schema,cn=config"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=openldap,cn=schema,cn=config"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=pmi,cn=schema,cn=config"
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=ppolicy,cn=schema,cn=config"
[root@logstash-1 ~]# slappasswd
New password:
Re-enter new password:
{SSHA}t/1pi/xNTx4Yh8Gxxxxxxx
[root@logstash-1 ~]# vi domain.ldif
[root@logstash-1 ~]# cat domain.ldif
dn: olcDatabase={0}config,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}xxJiWLtr00An3af5iOE9xKgTjdB0TGb7
[root@logstash-1 ~]# cat domain.ldif
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth"
read by dn.base="cn=Manager,dc=test,dc=com" read by * none
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=test,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=Manager,dc=test,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}t/1pi/xNTx4Yh8GOM7kJR9K4buSF4jOg
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcAccess
olcAccess: {0}to attrs=userPassword,shadowLastChange by
dn="cn=Manager,dc=test,dc=com" write by anonymous auth by self write by * none
olcAccess: {1}to dn.base="" by * read
olcAccess: {2}to * by dn="cn=Manager,dc=test,dc=com" write by * read
[root@logstash-1 ~]# ldapmodify -Y EXTERNAL -H ldapi:/// -f domain.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={1}monitor,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
modifying entry "olcDatabase={2}hdb,cn=config"
[root@logstash-1 ~]# vim basedomain.ldif
[root@logstash-1 ~]# ldapadd -x -D cn=Manager,dc=test,dc=com -W -f basedomain.ldif
Enter LDAP Password:
adding new entry "dc=test,dc=com"
adding new entry "cn=Manager,dc=test,dc=com"
adding new entry "ou=People,dc=test,dc=com"
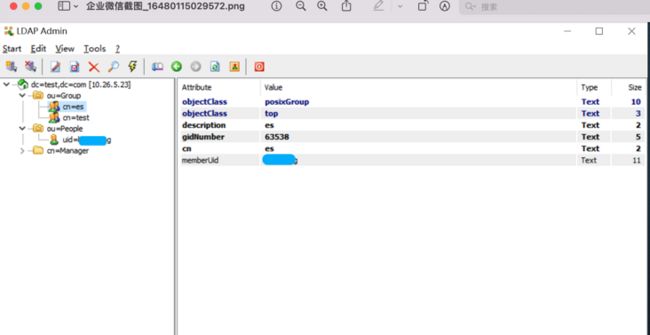
adding new entry "ou=Group,dc=test,dc=com"
[root@logstash-1 ~]# ldapsearch -LLL -W -x -D "cn=Manager,dc=test,dc=com" -H ldap://localhost -b "dc=test,dc=com"
Enter LDAP Password:
dn: dc=test,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: test com
dc: test
dn: cn=Manager,dc=test,dc=com
objectClass: organizationalRole
cn: Manager
description: Directory Manager
dn: ou=People,dc=test,dc=com
objectClass: organizationalUnit
ou: People
dn: ou=Group,dc=test,dc=com
objectClass: organizationalUnit
ou: Group
[root@logstash-1 ~]#
设置passwd