OCP集群内的AKO功能测试
NSX ALB + Harbor + OpenShift 4.8 UPI安装配置实验笔记系列目录
目录
NSX ALB + Harbor + OpenShift 4.8 UPI安装配置实验笔记系列目录
1 基本功能测试
1.1 AVI DNS功能测试
1.2 查看AKO安装前已发布的应用route的变化
1.2.1 查看avi-demo-route yaml
1.2.2 查看NSX ALB中的Virtual Service
1.2.3 不修改测试主机的hosts记录访问avi-demo网址
1.2.4 清理主机hosts记录并测试
1.2.5 查看AVI中对应Virtual Service后的服务池
1.2.6 以HTTPS方式访问测试
1.3 4层load balancer的应用发布
1.3.1 新建4层的LB应用发布
1.3.2 查看AVI中的Virtual Service
1.3.3 访问验证
1.4 Ingress服务在NSX ALB中的体现
2 AVI TSL卸载测试
2.1 部署支持https的nginx服务
2.2 发布nginx服务
2.2.1 常规http服务发布
2.2.2 发布Termination为edge的Https服务
2.2.3 发布Termination为passthrough的Https服务
2.2.4 发布Termination为reencrypt的Https服务
3 Gateway API测试
3.1 创建gateway-class
3.2 创建gateway
3.3 发布服务
3.4 结果测试
1 基本功能测试
1.1 AVI DNS功能测试
此LAB环境中AVI内启用了两个DNS Service,IP分别为192.168.150.10和192.168.170.10,这两个DNS服务分别承载于不同的SE Group。
经测试,OCP环境中发布服务域名可以同时被这两个DNS服务解析。
结果如下图:
1.2 查看AKO安装前已发布的应用route的变化
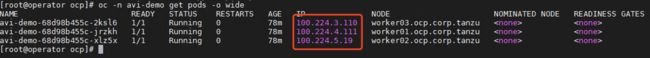
1.2.1 查看avi-demo-route yaml
1.2.2 查看NSX ALB中的Virtual Service
在AVI的Virtual Service中已自动生成了一个VIP为192.168.180.35的服务:
![]()
1.2.3 不修改测试主机的hosts记录访问avi-demo网址
1.2.4 清理主机hosts记录并测试
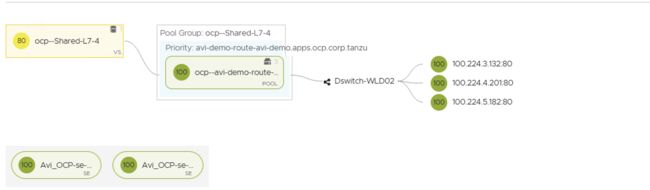
1.2.5 查看AVI中对应Virtual Service后的服务池
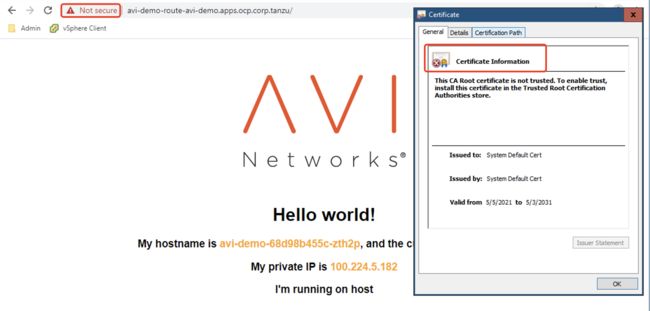
1.2.6 以HTTPS方式访问测试
以https的方式访问https://avi-demo-route-avi-demo.apps.ocp.corp.tanzu/ 同样可以打开AVI-DEMO的测试链接,如下图:
这是因为AVI做了SSL卸载,具体如下图:
1.3 4层load balancer的应用发布
1.3.1 新建4层的LB应用发布
kubectl -n avi-demo expose deploy/avi-demo --port=80 --target-port=80 --name=avi-demo-lb --type=LoadBalancer
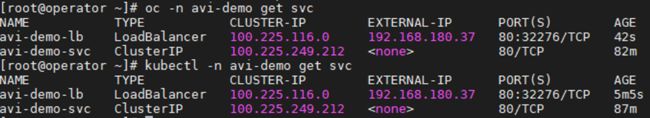
oc -n avi-demo get svc1.3.2 查看AVI中的Virtual Service
1.3.3 访问验证
通过IP或域名均可访问,结果如下:
1.4 Ingress服务在NSX ALB中的体现
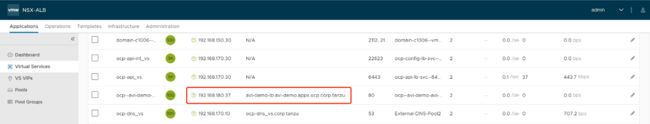
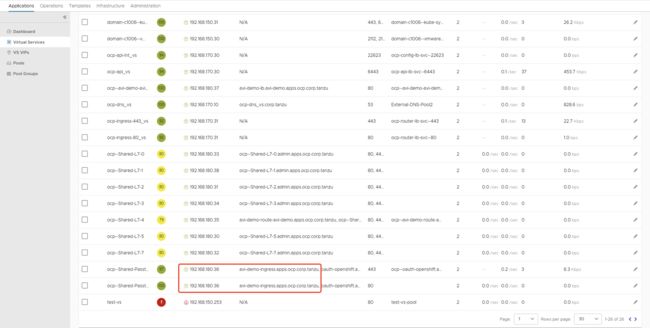
在“在OCP集群内部署测试应用”中的第5节内ingress发布了“edge”和“passthrough”两种模式,如下图:
我们在NSX ALB中查看AKO的同步结果信息如下图:
如上图所示,avi-demo-ingress-dege模式的并未在NSX ALB中体现,passthrough模式的服务同步至了NSX ALB中,但此处仅为4层LB模式:
我们将avi-demo-ingress-dege在hosts文件中设定记录,如下:
192.168.170.31 avi-demo-ingress-edge.apps.ocp.corp.tanzu
通过IE分别测试这两个网址,发现avi-demo-ingress.apps.ocp.corp.tanzu无法访问。在Operator主机使用curl得到结果如下:
根据返回码“302”可得知被redirect。查看对应ingress route配置,“insecureEdgeTerminationPolicy: Redirect”得知不安全的访问将被重定向,因此处为对应ingress自动生成的route,此处配置无法更改为Allow:
2 AVI TSL卸载测试
2.1 部署支持https的nginx服务
1). 生成自签名证书与密钥:
openssl req -newkey rsa:2048 -nodes -keyout nginx.key -x509 -days 3650 -out nginx.crt2). 创建nginx项目:
oc new-project nginx-demo3). 向nginx-demo项目中导入Secret,并命名为nginx-certs-keys:
oc create secret generic nginx-certs-keys --from-file=/root/cert/nginx.crt --from-file=/root/cert/nginx.key -n nginx-demo4). 配置默认的配置文件:
vi default.conf
server {
listen 80 default_server;
listen [::]:80 default_server ipv6only=on;
listen 443 ssl;
root /usr/share/nginx/html;
index index.html;
server_name localhost;
ssl_certificate /etc/nginx/ssl/nginx.crt;
ssl_certificate_key /etc/nginx/ssl/nginx.key;
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:50m;
ssl_session_tickets off;
# modern configuration. tweak to your needs.
ssl_protocols TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
ssl_prefer_server_ciphers on;
# HSTS (ngx_http_headers_module is required) (15768000 seconds = 6 months)
add_header Strict-Transport-Security max-age=15768000;
# OCSP Stapling ---
# fetch OCSP records from URL in ssl_certificate and cache them
ssl_stapling on;
ssl_stapling_verify on;
location / {
try_files $uri $uri/ =404;
}
}
5). 使用default.conf文件为Nginx创建configmap:
oc -n nginx-demo create configmap nginx-configmap --from-file=/root/cert/default.conf
oc get configmaps
oc describe configmaps nginx-configmap6). 创建pod和service:
oc adm policy add-scc-to-user anyuid -z default
cat << EOF > nginx-demo.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx
namespace: nginx-demo
spec:
replicas: 3
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
volumes:
- name: secret-volume
secret:
secretName: nginx-certs-keys
- name: configmap-volume
configMap:
name: nginx-configmap
containers:
- name: nginx
image: "map.corp.tanzu/apps/nginx-unprivileged:latest"
ports:
- containerPort: 80
- containerPort: 443
volumeMounts:
- name: nginx1-config
mountPath: /etc/nginx/nginx.conf
subPath: nginx.conf
volumeMounts:
- mountPath: /etc/nginx/ssl
name: secret-volume
- mountPath: /etc/nginx/conf.d
name: configmap-volume
---
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
namespace: nginx-demo
spec:
selector:
app: nginx
ports:
- protocol: TCP
port: 80
targetPort: 80
name: http
- protocol: TCP
port: 443
targetPort: 443
name: https
EOF
oc apply -f nginx-demo.yaml2.2 发布nginx服务
2.2.1 常规http服务发布
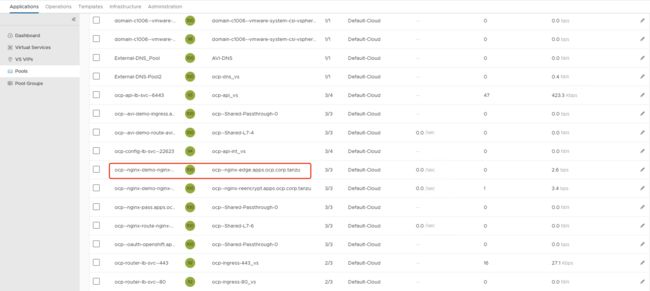
oc expose svc nginx-svc --name=nginx-route可以看到AVI中已自动生成记录:
在Operator操作机中使用curl访问http和https均可,此处https能访问的原因与1.2.6相同。
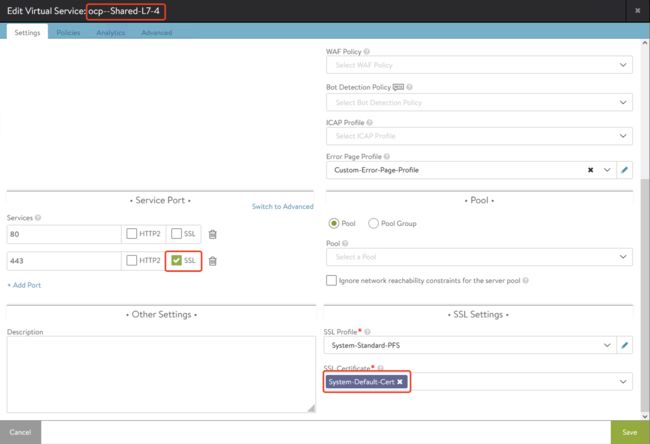
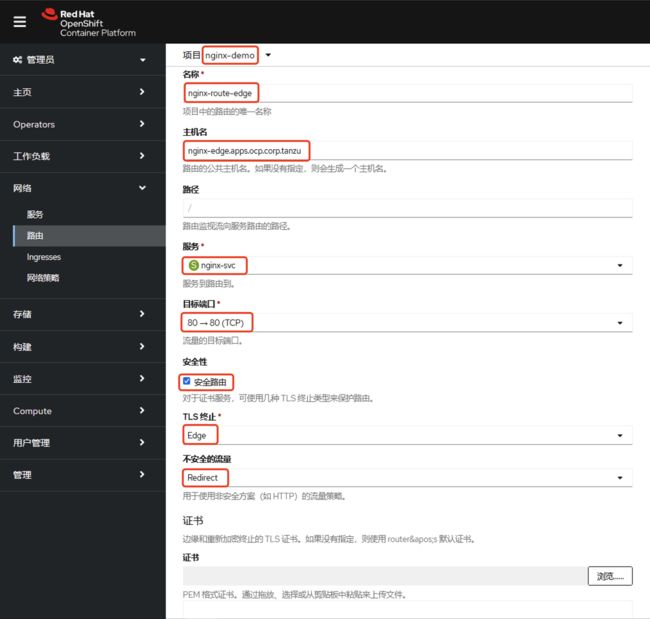
2.2.2 发布Termination为edge的Https服务
1). 打开NSXALB的 System-Default-Cert。
2). 进入OCP GUI新建路由,并且在证书与私钥部分输入NSXALB中System-Default-Cert的值,然后创建route:
具体yaml如下:
piVersion: route.openshift.io/v1
kind: Route
metadata:
name: nginx-edge
namespace: nginx-demo
spec:
host: nginx-edge.apps.ocp.corp.tanzu
to:
kind: Service
name: nginx-svc
weight: 100
port:
targetPort: http
tls:
termination: edge
certificate: |
-----BEGIN CERTIFICATE-----
MIIDRTCCAi2gAwIBAgIUSGdsEmU6K3zBiUmtwsQ52S5yEJswDQYJKoZIhvcNAQEL
BQAwHjEcMBoGA1UEAwwTU3lzdGVtIERlZmF1bHQgQ2VydDAeFw0yMTA1MDYwMjMw
MTFaFw0zMTA1MDQwMjMwMTFaMB4xHDAaBgNVBAMME1N5c3RlbSBEZWZhdWx0IENl
cnQwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDe+q8lem+lvAtWg0kS
86lXhvpyG2wC7hPrS3E7ih2RDMbmDHtvyIxVNE/lF+HsDBOrxC5EWVuPpd+c84ec
7jCTeBMVeAYiMo/BYCFx+Oqe9dtGiwwmVpmf0Ft/PiVaJ27UDOr8s1M1T8x2BAe9
S6+du+H7QMWuPLZvkvoN/5BtwaJVKfNedVMYLht7B0pGx5IovB9DEXPJTGIP0YK/
7o0lC+ZvxsgMDYkQz1QGPPddfc/MZ4Py3MY8KB3txxwwPnv20goMGy9rJXQwSTB/
xa5BMn8ml8nVPRQvNsy7kyTY2h4SeZFMYJxQ/3DYVE6HIymec5BjskFVB4hH9C4j
dIdtAgMBAAGjezB5MAkGA1UdEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wg
R2VuZXJhdGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBQ0xRoXx0XoPIgIVp5R7Mh5
cPTjqDAfBgNVHSMEGDAWgBQ0xRoXx0XoPIgIVp5R7Mh5cPTjqDANBgkqhkiG9w0B
AQsFAAOCAQEAtm5O3gN0klWo2UztWC6eGCqNDDMKRNhbPYhq17vMj42xejcjvYZC
Yb5qj3ioHo9qOxleJjKvRGGt5F6j0cw5jo51910KbyH8/wet1wYq5jttIvQ15D33
JTP+02FW+ASis0wMT/DtbgxE2TjdTU424Ff83xAYQ2Atcal01E3gbNkH+ziqx4Yd
4Flgr9E7tT9zWxsLQTA7t9Zy9xMT3j1tJGwJXrVC1NJfdUCrLhP9ROHs5TiBuegF
0WpXnbod4YRqkMGBw8Vy/E9Y0JBf2RCS8eXAr5y//B5dsw9+pJuG4gymnNa1IPtj
9FP9PiS2AnRMpO5u716eGQNM3wx3eZxRSg==
-----END CERTIFICATE-----
key: |
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDe+q8lem+lvAtW
g0kS86lXhvpyG2wC7hPrS3E7ih2RDMbmDHtvyIxVNE/lF+HsDBOrxC5EWVuPpd+c
84ec7jCTeBMVeAYiMo/BYCFx+Oqe9dtGiwwmVpmf0Ft/PiVaJ27UDOr8s1M1T8x2
BAe9S6+du+H7QMWuPLZvkvoN/5BtwaJVKfNedVMYLht7B0pGx5IovB9DEXPJTGIP
0YK/7o0lC+ZvxsgMDYkQz1QGPPddfc/MZ4Py3MY8KB3txxwwPnv20goMGy9rJXQw
STB/xa5BMn8ml8nVPRQvNsy7kyTY2h4SeZFMYJxQ/3DYVE6HIymec5BjskFVB4hH
9C4jdIdtAgMBAAECggEBAMGQ5RKn4twBDeagOYNWOp9c8XS1EWLJwkj0SOvizh/o
85EpLM6xTgF5VBIQVXNQWJM3zuJOoAlneWMKlaNJsqmSBx8P/mMZeWnpRZ9m8mXk
D+KBOp7ddqchfQxMqqhEqxUx0ZxlH8qb52ZbwUw2s9E+FMLES9chpU3eTWxxerOL
UZ3u9T2y671bULzl8AzoIawTQLEIctx9TYL+iZ23asNU4eg86WSetARdwTuzC/BF
hFFRV1KrBpBD7zJdf2ylSmxq4VWOosWFZRQJyip5wZUXtBcQ/cWqpsm2N4mi+rpf
K0yIrsBnRPKjOxXopEOrJEDN+qQcYS4g22GfNJ6HopECgYEA9hN6kHwlN/TPkMSM
/X47fYf0OENOO6VqgFPyH35WpJkKvItuEhqFo03DuqUq6M8qZariIhqibsR42Fdy
zaPDsAqPOoSDpNpBdRG3NWdKQdMHX5KKWx1xK+hq1FGvpihTbDooBML9/JNajVm0
CjVu1OyV24MnGfZxMePrN89SO+MCgYEA5/jAIQpp+2wylC3oO9DFnKCvzFdb0L/l
pw5FmfQ/OZ6+PNufUEKZFW1vG8aHnCzfY+iVKhoFkCGxLqDNN1aflztqL0OzJnkF
7lZ/jtSSeuOEKL7QMjF8Z1R4s4g0ppr0bVwt7qBcY+dLAwYWfhzTc5TS1m+WDi11
ckvL9BbGMG8CgYAiGczwXOPjfz+MdlB7iJTB7qc/bMRYq7G4mumAx8dGBBdizYex
Zo+Cc/Jd2Sm7HYpokGfKBhrgcsW0ZVn5eWpS6QO0Pkzn+X78tDnJYsj9mjr5WZtm
yQu34/t59N/8jLYS13RYRJVh/SGdWQMELyduxmJ2CxTOGkLRgR5Fm6tvtQKBgQCN
OYDm3Ks3OWD1m5lGSUz1lVJRymGIjjunX+X525xeXQmejWrJdzIxvGUneM94wkzi
S2f8sMjwPcLcC2PErAUPEkoMKmA4LPfyaVDRSRNAo6EDGWAxHrWJRwEQ8/xx7eaf
ab5BB/oXjGm7loo9DxmgxVsy1854JS7afdDWcsMIGwKBgAn9o2pM0MGPr96ShILD
f8y9fvMGDw1GWCjIJW0j9QwCid7wLEKuw2JUASUOxmEjtyg7aChSIEy9q6V5WRX9
/hx28WXM2oTEiEOuNVskaArv4nFsODeZfCAESr4z/anChbOqtr+OxvI18afCNj/1
Fk1LPCucPIA+B2bwXxwiZU04
-----END PRIVATE KEY-----
insecureEdgeTerminationPolicy: Redirect
wildcardPolicy: None3). 检测发部结果
4). 查看NSXALB内的VS
![]()
2.2.3 发布Termination为passthrough的Https服务
1). 进入OCP GUI新建路由,
具体yaml如下:
piVersion: route.openshift.io/v1
kind: Route
metadata:
name: nginx-passthrough
namespace: nginx-demo
spec:
host: nginx-pass.apps.ocp.corp.tanzu
to:
kind: Service
name: nginx-svc
weight: 100
port:
targetPort: https
tls:
termination: passthrough
insecureEdgeTerminationPolicy: Redirect
wildcardPolicy: None2). 检测发部结果:
3). 查看NSXALB内的VS
![]()
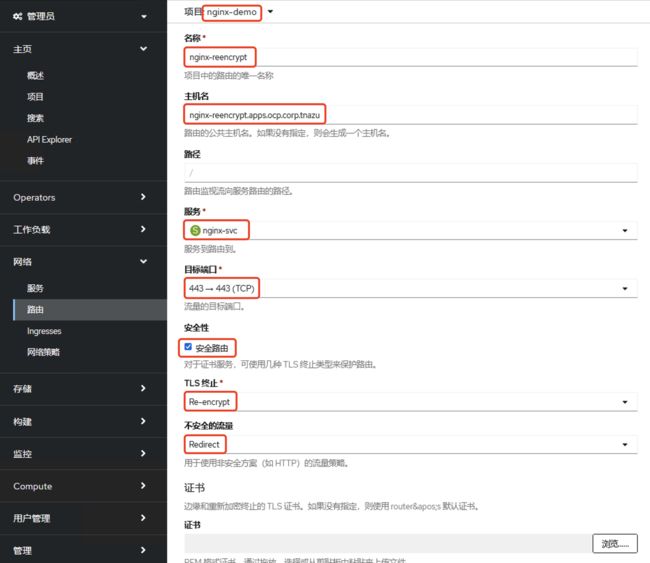
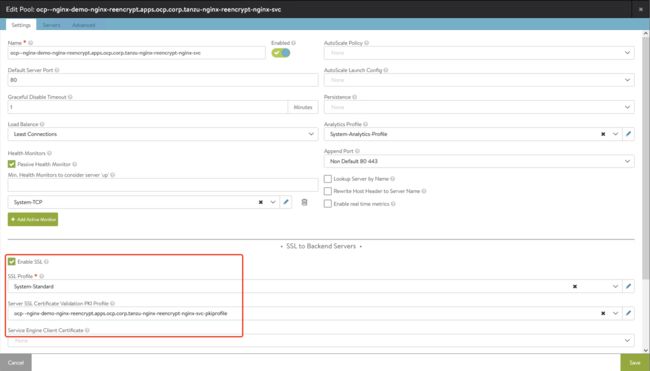
2.2.4 发布Termination为reencrypt的Https服务
1). 进入OCP GUI新建路由,
具体yaml如下:
kind: Route
apiVersion: route.openshift.io/v1
metadata:
name: nginx-reencrypt
namespace: nginx-demo
spec:
host: nginx-reencrypt.apps.ocp.corp.tanzu
to:
kind: Service
name: nginx-svc
weight: 100
port:
targetPort: https
tls:
termination: reencrypt
certificate: |
-----BEGIN CERTIFICATE-----
MIIDRTCCAi2gAwIBAgIUSGdsEmU6K3zBiUmtwsQ52S5yEJswDQYJKoZIhvcNAQEL
BQAwHjEcMBoGA1UEAwwTU3lzdGVtIERlZmF1bHQgQ2VydDAeFw0yMTA1MDYwMjMw
MTFaFw0zMTA1MDQwMjMwMTFaMB4xHDAaBgNVBAMME1N5c3RlbSBEZWZhdWx0IENl
cnQwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDe+q8lem+lvAtWg0kS
86lXhvpyG2wC7hPrS3E7ih2RDMbmDHtvyIxVNE/lF+HsDBOrxC5EWVuPpd+c84ec
7jCTeBMVeAYiMo/BYCFx+Oqe9dtGiwwmVpmf0Ft/PiVaJ27UDOr8s1M1T8x2BAe9
S6+du+H7QMWuPLZvkvoN/5BtwaJVKfNedVMYLht7B0pGx5IovB9DEXPJTGIP0YK/
7o0lC+ZvxsgMDYkQz1QGPPddfc/MZ4Py3MY8KB3txxwwPnv20goMGy9rJXQwSTB/
xa5BMn8ml8nVPRQvNsy7kyTY2h4SeZFMYJxQ/3DYVE6HIymec5BjskFVB4hH9C4j
dIdtAgMBAAGjezB5MAkGA1UdEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wg
R2VuZXJhdGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBQ0xRoXx0XoPIgIVp5R7Mh5
cPTjqDAfBgNVHSMEGDAWgBQ0xRoXx0XoPIgIVp5R7Mh5cPTjqDANBgkqhkiG9w0B
AQsFAAOCAQEAtm5O3gN0klWo2UztWC6eGCqNDDMKRNhbPYhq17vMj42xejcjvYZC
Yb5qj3ioHo9qOxleJjKvRGGt5F6j0cw5jo51910KbyH8/wet1wYq5jttIvQ15D33
JTP+02FW+ASis0wMT/DtbgxE2TjdTU424Ff83xAYQ2Atcal01E3gbNkH+ziqx4Yd
4Flgr9E7tT9zWxsLQTA7t9Zy9xMT3j1tJGwJXrVC1NJfdUCrLhP9ROHs5TiBuegF
0WpXnbod4YRqkMGBw8Vy/E9Y0JBf2RCS8eXAr5y//B5dsw9+pJuG4gymnNa1IPtj
9FP9PiS2AnRMpO5u716eGQNM3wx3eZxRSg==
-----END CERTIFICATE-----
key: |
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDe+q8lem+lvAtW
g0kS86lXhvpyG2wC7hPrS3E7ih2RDMbmDHtvyIxVNE/lF+HsDBOrxC5EWVuPpd+c
84ec7jCTeBMVeAYiMo/BYCFx+Oqe9dtGiwwmVpmf0Ft/PiVaJ27UDOr8s1M1T8x2
BAe9S6+du+H7QMWuPLZvkvoN/5BtwaJVKfNedVMYLht7B0pGx5IovB9DEXPJTGIP
0YK/7o0lC+ZvxsgMDYkQz1QGPPddfc/MZ4Py3MY8KB3txxwwPnv20goMGy9rJXQw
STB/xa5BMn8ml8nVPRQvNsy7kyTY2h4SeZFMYJxQ/3DYVE6HIymec5BjskFVB4hH
9C4jdIdtAgMBAAECggEBAMGQ5RKn4twBDeagOYNWOp9c8XS1EWLJwkj0SOvizh/o
85EpLM6xTgF5VBIQVXNQWJM3zuJOoAlneWMKlaNJsqmSBx8P/mMZeWnpRZ9m8mXk
D+KBOp7ddqchfQxMqqhEqxUx0ZxlH8qb52ZbwUw2s9E+FMLES9chpU3eTWxxerOL
UZ3u9T2y671bULzl8AzoIawTQLEIctx9TYL+iZ23asNU4eg86WSetARdwTuzC/BF
hFFRV1KrBpBD7zJdf2ylSmxq4VWOosWFZRQJyip5wZUXtBcQ/cWqpsm2N4mi+rpf
K0yIrsBnRPKjOxXopEOrJEDN+qQcYS4g22GfNJ6HopECgYEA9hN6kHwlN/TPkMSM
/X47fYf0OENOO6VqgFPyH35WpJkKvItuEhqFo03DuqUq6M8qZariIhqibsR42Fdy
zaPDsAqPOoSDpNpBdRG3NWdKQdMHX5KKWx1xK+hq1FGvpihTbDooBML9/JNajVm0
CjVu1OyV24MnGfZxMePrN89SO+MCgYEA5/jAIQpp+2wylC3oO9DFnKCvzFdb0L/l
pw5FmfQ/OZ6+PNufUEKZFW1vG8aHnCzfY+iVKhoFkCGxLqDNN1aflztqL0OzJnkF
7lZ/jtSSeuOEKL7QMjF8Z1R4s4g0ppr0bVwt7qBcY+dLAwYWfhzTc5TS1m+WDi11
ckvL9BbGMG8CgYAiGczwXOPjfz+MdlB7iJTB7qc/bMRYq7G4mumAx8dGBBdizYex
Zo+Cc/Jd2Sm7HYpokGfKBhrgcsW0ZVn5eWpS6QO0Pkzn+X78tDnJYsj9mjr5WZtm
yQu34/t59N/8jLYS13RYRJVh/SGdWQMELyduxmJ2CxTOGkLRgR5Fm6tvtQKBgQCN
OYDm3Ks3OWD1m5lGSUz1lVJRymGIjjunX+X525xeXQmejWrJdzIxvGUneM94wkzi
S2f8sMjwPcLcC2PErAUPEkoMKmA4LPfyaVDRSRNAo6EDGWAxHrWJRwEQ8/xx7eaf
ab5BB/oXjGm7loo9DxmgxVsy1854JS7afdDWcsMIGwKBgAn9o2pM0MGPr96ShILD
f8y9fvMGDw1GWCjIJW0j9QwCid7wLEKuw2JUASUOxmEjtyg7aChSIEy9q6V5WRX9
/hx28WXM2oTEiEOuNVskaArv4nFsODeZfCAESr4z/anChbOqtr+OxvI18afCNj/1
Fk1LPCucPIA+B2bwXxwiZU04
-----END PRIVATE KEY-----
destinationCACertificate: |-
-----BEGIN CERTIFICATE-----
MIIDdzCCAl+gAwIBAgIJAKNpgh6rsBdjMA0GCSqGSIb3DQEBCwUAMFIxCzAJBgNV
BAYTAlhYMRUwEwYDVQQHDAxEZWZhdWx0IENpdHkxHDAaBgNVBAoME0RlZmF1bHQg
Q29tcGFueSBMdGQxDjAMBgNVBAMMBW5naW54MB4XDTIyMDUxMDE0MDc0NFoXDTMy
MDUwNzE0MDc0NFowUjELMAkGA1UEBhMCWFgxFTATBgNVBAcMDERlZmF1bHQgQ2l0
eTEcMBoGA1UECgwTRGVmYXVsdCBDb21wYW55IEx0ZDEOMAwGA1UEAwwFbmdpbngw
ggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDlLruPV8gyyaZ9vxJ+KrqC
f2jOawZ6+50cu5qVThhnvlQxTH4+MhDmGetg8EcOqs2q7/SYMA3KTkreTkcE6mc8
5uTLm0Cz7tBvEnK4kQbHyEUwPUEUewfDZwJfLtUV8B4JqWy811+GJKxsWu6A4rt0
A6L5LUlijLx6G15aeyT/kXuO337IBD7kBgXjAm/gWOTXj2iLWP77xhuLohhvwcSc
9ff34Ug8ZldWVYrMRmAYf+xtQzsR765cp4XuYdaGizKsBFiqzorIP1J7exy/VSWq
dogEKSgAkjJVj20HobZwwLdksukuMIzMxXcaX0xs9ekbjc0stMaJR9d8xL32uBnD
AgMBAAGjUDBOMB0GA1UdDgQWBBRKHGAAFK4Z90U3ENg9dIT6aDHxjzAfBgNVHSME
GDAWgBRKHGAAFK4Z90U3ENg9dIT6aDHxjzAMBgNVHRMEBTADAQH/MA0GCSqGSIb3
DQEBCwUAA4IBAQAGZHWExc7vVXYR3HBdcqi5AULWNGwAVk9hl4Ulr2dxdd0sEW/o
KHruS6K7QUYr1xBW+n6Ut3YwpAxXOca8Ce5+tbhOaSWEm0SA2Q4pYlSPQiEOJxq0
3EGqkCDXoOjFlHgfG8W4BncMlzewHINljXhRrDRmPTQuef/80mM/zYXX+Cq7EILt
clTPOSyxuHFmSteUpjyauOt5RPGZL4HFbIEjjwwMcrIRMseq2d49eo+V+xlHd+8M
QOaEvtCM285Za2tdtuPBLss+dd4JglN9Hstjcna9x/lAe1TdtsTt7JnKpCuro6xI
BFW3Dk75tmK4OJch6EVl12HmGjo63guanFrE
-----END CERTIFICATE-----
insecureEdgeTerminationPolicy: Redirect
wildcardPolicy: None2). 检测发布结果:
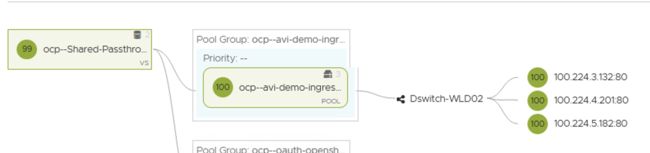
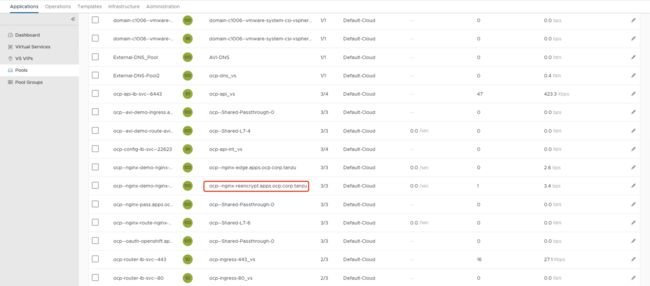
3). 查看NSXALB内的VS和Pool:
![]()
3 Gateway API测试
在创建L4负载时,默认情况下会一直使用新的VIP地址,这种情况下VIP地址会随着业务应用的发布快速消耗。要改善这一情况,可使用Gateway对像来实现利用已存在的VIP来为新的应用提供服务,以便实现VIP地址的节约。
3.1 创建gateway-class
cat << EOF > gw-class.yaml
apiVersion: networking.x-k8s.io/v1alpha1
kind: GatewayClass
metadata:
name: nsxalb-gateway-class
spec:
controller: ako.vmware.com/avi-lb
EOF
oc apply -f gw-class.yaml 3.2 创建gateway
cat << EOF > gw.yaml
kind: Gateway
apiVersion: networking.x-k8s.io/v1alpha1
metadata:
name: gateway-01
namespace: default
spec:
gatewayClassName: nsxalb-gateway-class
listeners:
- protocol: TCP
port: 80
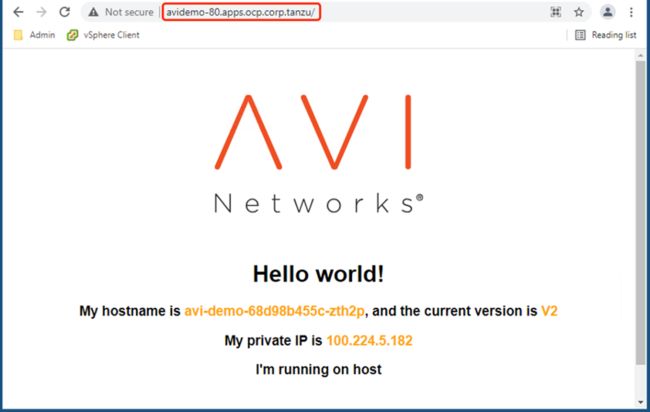
hostname: avidemo-8080.apps.ocp.corp.tanzu
routes:
selector:
matchLabels:
ako.vmware.com/gateway-namespace: default
ako.vmware.com/gateway-name: gateway-01
group: v1
kind: Service
- protocol: TCP
port: 8080
hostname: avidemo-80.apps.ocp.corp.tanzu
routes:
selector:
matchLabels:
ako.vmware.com/gateway-namespace: default
ako.vmware.com/gateway-name: gateway-01
group: v1
kind: Service
EOF
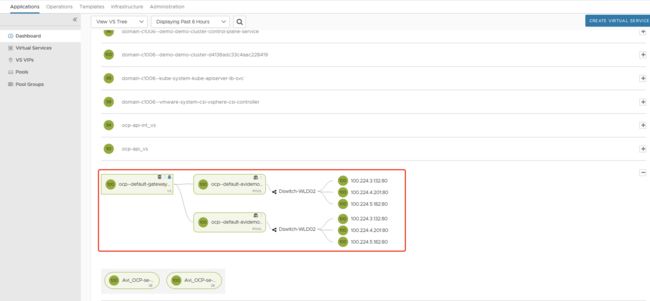
oc apply -f gw.yaml此处GW建好后,在NSXALB GUI的VS中已可以看到对应对像
3.3 发布服务
cat << EOF > gw-app-svc.yaml
apiVersion: v1
kind: Service
metadata:
name: avidemo-8080
namespace: avi-demo
labels:
ako.vmware.com/gateway-name: gateway-01
ako.vmware.com/gateway-namespace: default
spec:
type: ClusterIP
ports:
- port: 8080
name: eighty-eighty
targetPort: 80
protocol: TCP
selector:
app: avi-demo
---
apiVersion: v1
kind: Service
metadata:
name: avidemo-80
namespace: avi-demo
labels:
ako.vmware.com/gateway-name: gateway-01
ako.vmware.com/gateway-namespace: default
spec:
type: ClusterIP
ports:
- port: 80
name: eighty-eighty
targetPort: 80
protocol: TCP
selector:
app: avi-demo
EOF
oc apply -f gw-app-svc.yaml3.4 结果测试
![]()