OpenShift 4 - 在 Jenkins 的 CI/CD 中用 RHACS 对镜像进行安全扫描
《OpenShift / RHEL / DevSecOps 汇总目录》
文本已在 OpenShift 4.11 + RHACS 3.71.0 环境中进行验证。
文章目录
- 安装 DevOps 环境
-
- 安装配置 Nexus 环境
- 安装 Jenkins 环境
- 安装 Sonar 环境
- 使用 RHACS 客户端扫描 Nexus 中的 Image
- 在 Jenkins 中使用 RHACS 扫描镜像
-
- 配置 RHACS
- 创建并运行 Jenkins CI/CD Pipeline
- 排查问题
- 参考
本文使用在 OpenShift 中使用由 Jenkins、Nexus、Sonarqube、RHACS 组成的 DevSecOps CICD Pipeline 环境对应用镜像进行安全扫描检查。

请在开始以下操作前先完成 OpenShift + RHACS 环境安装。
安装 DevOps 环境
- 从 github 下载 openshift-demo:
$ git clone https://github.com/liuxiaoyu-git/openshift-demo && cd openshift-demo/bin
- 执行以下脚本创建 OpenShift 项目。
$ ./setup_cicd_projects.sh
安装配置 Nexus 环境
- 编辑 setup_nexus.sh 文件,可适当调整 NEXUS_PVC_SIZE 大小。
NEXUS_PVC_SIZE="300Gi"
JENKINS_PVC_SIZE="10Gi"
SONAR_PVC_SIZE="10Gi"
- 执行命令安装 Nexus 环境。
$ ./setup_nexus.sh
- 完成安装后会提示 Nexus 的 admin 和 jenkins 用户的密码都保存在 nexus_password.txt 文件中了。
- 执行以下命令,获取 Nexus 控制台的访问地址。然后用浏览器访问 Nexus 控制台,分别用 admin 和 jenkins 用户登录。
$ echo https://$(oc get route nexus -n ci-cd -o jsonpath='{.spec.host}')
- 在 Nexus 控制台中的 Users 页面中修改 admin 和 jenkins 用户的密码,然后将新的密码更新到 nexus_password.txt 文件中。

- 并确认在 Browse 页面中有 docker 的仓库,它便是 Nexus 的 Container Image Registry 仓库。
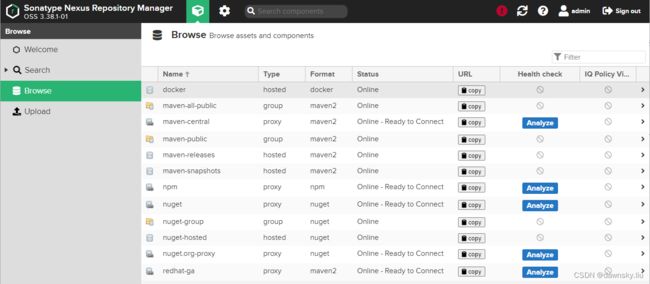
- 执行以下命令,获取 Nexus 提供的 Image Registry 访问地址。
$ NEXUS_REGISTRY=$(oc get route nexus-registry -n ci-cd -o jsonpath='{.spec.host}') && echo $NEXUS_REGISTRY
- 执行命令,向 Nexus 镜像仓库导入镜像。
$ yum install skopeo -y
$ NEXUS_PASSWORD=<PASSWORD>
$ allImages="backend:v1 backend:11-ubuntu backend:CVE-2020-36518 frontend-js:v1 frontend-js:node log4shell:latest backend-native:v1 backend-native:v1-distroless"
$ for image in $allImages
do
echo "############## Copy $image ##############"
skopeo copy --src-tls-verify=true --dest-tls-verify=false --src-no-creds --dest-username admin --dest-password $NEXUS_PASSWORD \
docker://quay.io/voravitl/$image docker://$NEXUS_REGISTRY/$image
done
安装 Jenkins 环境
$ ./setup_jenkins.sh
安装 Sonar 环境
$ ./setup_sonar.sh
在安装完 Jenkins、Nexus、Sonar 后确认在 ci-cd 项目中应该部署好了以下资源:

使用 RHACS 客户端扫描 Nexus 中的 Image
- 从 RHACS 控制台页面下载 RHACS 客户端程序 roxctl 。

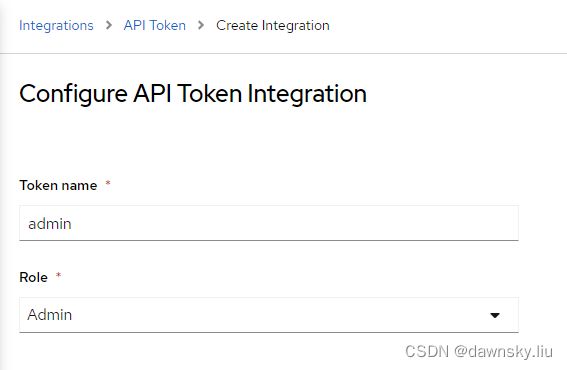
- 在 RHACS 中的 Integration 中创建一个 API Token,其中 Role 选择 Admin 类型。将生成的内容复制到 bin 目录下的 acs-token 文件中。
- 执行命令,用客户端程序检查 Nexus 中的容器镜像违规情况。
$ ROX_CENTRAL_ADDRESS=$(oc get route central -n stackrox -o jsonpath='{.spec.host}'):443
$ roxctl --insecure-skip-tls-verify -e ${ROX_CENTRAL_ADDRESS} image check --image=${NEXUS_REGISTRY}/backend:v1 --output=table --token-file=acs-token
Policy check results for image: nexus-registry-ci-cd.apps.cluster-k8qw5.k8qw5.sandbox638.opentlc.com/backend:v1
(TOTAL: 1, LOW: 1, MEDIUM: 0, HIGH: 0, CRITICAL: 0)
+--------------------------------+----------+--------------+--------------------------------+--------------------------------+--------------------------------+
| POLICY | SEVERITY | BREAKS BUILD | DESCRIPTION | VIOLATION | REMEDIATION |
+--------------------------------+----------+--------------+--------------------------------+--------------------------------+--------------------------------+
| Red Hat Package Manager in | LOW | - | Alert on deployments with | - Image includes component | Run `rpm -e --nodeps $(rpm -qa |
| Image | | | components of the Red | 'microdnf' (version | '*rpm*' '*dnf*' '*libsolv*' |
| | | | Hat/Fedora/CentOS package | 3.8.0-2.el8.x86_64) | '*hawkey*' 'yum*')` in the |
| | | | management system. | | image build for production |
| | | | | - Image includes | containers. |
| | | | | component 'rpm' (version | |
| | | | | 4.14.3-23.el8.x86_64) | |
+--------------------------------+----------+--------------+--------------------------------+--------------------------------+--------------------------------+
WARN: A total of 1 policies have been violated
- 执行命令,用客户端程序扫描 Nexus 中的容器镜像 CVE。
$ roxctl --insecure-skip-tls-verify -e ${ROX_CENTRAL_ADDRESS} image scan --image=${NEXUS_REGISTRY}/backend:v1 --output=table --token-file=acs-token
Scan results for image: nexus-registry-ci-cd.apps.cluster-k8qw5.k8qw5.sandbox638.opentlc.com/backend:v1
(TOTAL-COMPONENTS: 41, TOTAL-VULNERABILITIES: 86, LOW: 37, MODERATE: 0, IMPORTANT: 0, CRITICAL: 0)
+------------------------+---------------------------+------------------+-----------+---------------------------------------------------------+
| COMPONENT | VERSION | CVE | SEVERITY | LINK |
+------------------------+---------------------------+------------------+-----------+---------------------------------------------------------+
| arc | 2.10.2.final | CVE-2005-2945 | LOW | https://nvd.nist.gov/vuln/detail/CVE-2005-2945 |
+ + +------------------+-----------+---------------------------------------------------------+
| | | CVE-2005-2992 | LOW | https://nvd.nist.gov/vuln/detail/CVE-2005-2992 |
+------------------------+---------------------------+------------------+-----------+---------------------------------------------------------+
...
...
+------------------------+---------------------------+------------------+-----------+---------------------------------------------------------+
| systemd-libs | 239-58.el8.x86_64 | CVE-2018-20839 | MODERATE | https://access.redhat.com/security/cve/CVE-2018-20839 |
+ + +------------------+-----------+---------------------------------------------------------+
| | | CVE-2021-3997 | MODERATE | https://access.redhat.com/security/cve/CVE-2021-3997 |
+------------------------+---------------------------+------------------+-----------+---------------------------------------------------------+
WARN: A total of 86 vulnerabilities were found in 41 components
- 执行命令,用客户端程序检查 Deployment 的配置违规情况。
$ roxctl --insecure-skip-tls-verify -e ${ROX_CENTRAL_ADDRESS} deployment check --file=../manifests/backend-bad-example.yaml --token-file=acs-token
Policy check results for deployments: [backend-v2]
(TOTAL: 2, LOW: 0, MEDIUM: 2, HIGH: 0, CRITICAL: 0)
+--------------------------------+----------+---------------+------------+--------------------------------+--------------------------------+--------------------------------+
| POLICY | SEVERITY | BREAKS DEPLOY | DEPLOYMENT | DESCRIPTION | VIOLATION | REMEDIATION |
+--------------------------------+----------+---------------+------------+--------------------------------+--------------------------------+--------------------------------+
| No resource requests or limits | MEDIUM | - | backend-v2 | Alert on deployments that have | - CPU limit set to 0 cores for | Specify the requests and |
| specified | | | | containers without resource | container 'backend' | limits of CPU and Memory for |
| | | | | requests and limits | | your deployment. |
| | | | | | - CPU request set to 0 cores | |
| | | | | | for container 'backend' | |
| | | | | | | |
| | | | | | - Memory limit set to 0 MB for | |
| | | | | | container 'backend' | |
| | | | | | | |
| | | | | | - Memory request set to 0 MB | |
| | | | | | for container 'backend' | |
+--------------------------------+----------+---------------+------------+--------------------------------+--------------------------------+--------------------------------+
| Pod Service Account Token | MEDIUM | - | backend-v2 | Protect pod default service | - Deployment mounts the | Add |
| Automatically Mounted | | | | account tokens from compromise | service account tokens. | `automountServiceAccountToken: |
| | | | | by minimizing the mounting | | false` or a value distinct |
| | | | | of the default service | - Namespace has name 'default' | from 'default' for the |
| | | | | account token to only those | | `serviceAccountName` key |
| | | | | pods whose application | - Service Account is set to | to the deployment's Pod |
| | | | | requires interaction with the | 'default' | configuration. |
| | | | | Kubernetes API. | | |
+--------------------------------+----------+---------------+------------+--------------------------------+--------------------------------+--------------------------------+
WARN: A total of 2 policies have been violated
在 Jenkins 中使用 RHACS 扫描镜像
配置 RHACS
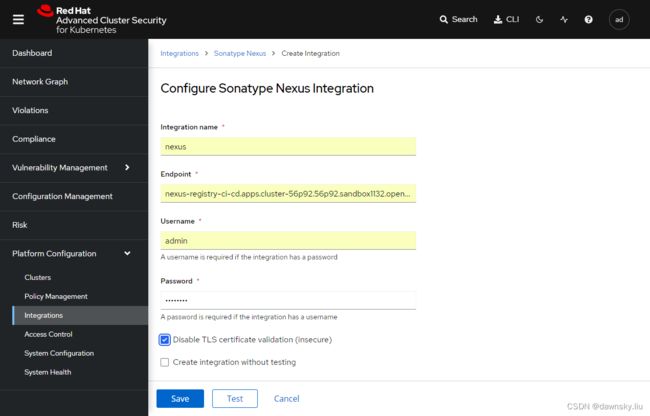
- (可选)在 RHACS 控制台进入 Integrations 菜单,然后找到并进入 Sonatype Nexus。点击 New Integration 按钮,然后在以下界面中使用 $NEXUS_REGISTRY 作为 Endpoint 创建一个 Nexus Integration。
- 执行命令,根据 acs-token 文件生成 secret。该 secret 会在 Jenkins 中被使用。
$ oc create secret generic stackrox-token -n ci-cd --from-file=token=acs-token
创建并运行 Jenkins CI/CD Pipeline
- 执行以下命令,创建基于 pipeline 流程的构建配置。
$ cat ../manifests/backend-build-stackrox-pipeline.yaml | sed 's/value: NEXUS_REGISTRY/value: '$NEXUS_REGISTRY'/' | oc create -n ci-cd -f -
$ oc get buildconfig -n ci-cd
NAME TYPE FROM LATEST
backend-build-stackrox-pipeline JenkinsPipeline Git@cve 1
- 执行命令,运行 backend-build-stackrox-pipeline。
$ oc start-build backend-build-stackrox-pipeline
-
在 Jenkins 中可以看到提示,即发现构建的镜像中包含的 Violation 违规项目。

如果在 Jenkins 中安装了 Blue Ocean 插件,可以看到以下执行结果。
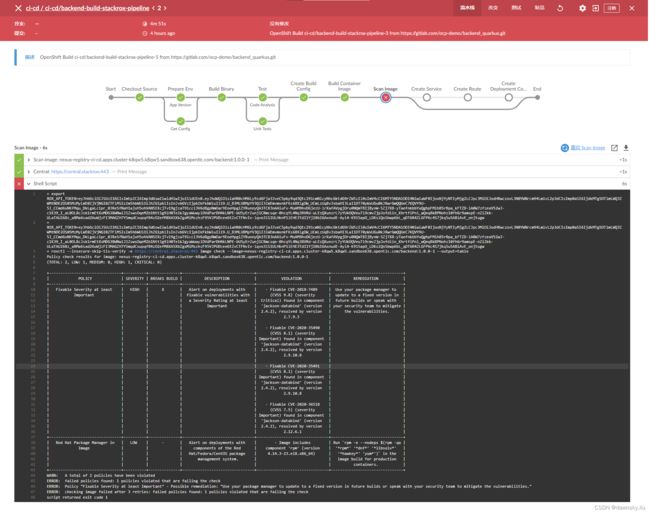
-
确认此时在 Nexus 中的 docker repository 中也有生成的 tag 为 1.0.0-1 容器镜像了。
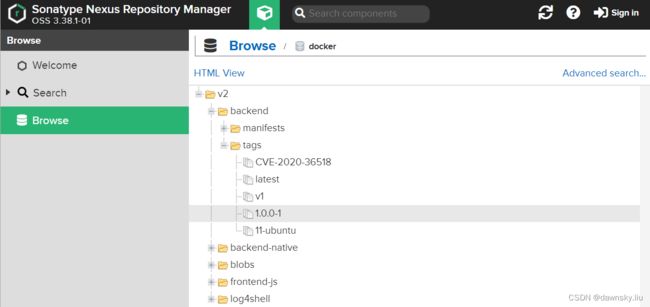
-
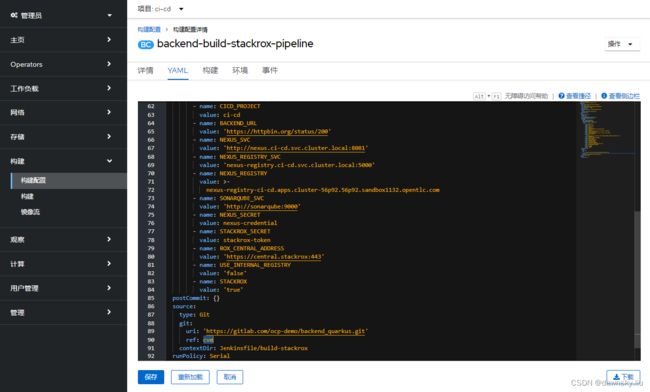
在 OpenShift 控制台管理员视图中修改名为 backend-build-stackrox-pipeline 配置构建,将下图中的 ref: cve 修改为 ref: master。
source:
contextDir: Jenkinsfile/build-stackrox
git:
ref: master
uri: https://gitlab.com/ocp-demo/backend_quarkus.git
- 再次执行命令,运行 backend-build-stackrox-pipeline。确认 Jenkins Pipeline 可以成功完成运行,这说明 master 分支的应用代码不再有违规了。
$ oc start-build backend-build-stackrox-pipeline

如果在 Jenkins 中安装了 Blue Ocean 插件,可以看到以下执行结果。

8. 确认在 dev 项目中已经有部署成功的 backend 应用了。

排查问题
以下问题是由于 ACS 的 scanner 组件无法访问造成的,请确认该组件对应的 Pod 运行正常。
ERROR: checking image failed after 3 retries: could not check build-time alerts: rpc error: code = Internal desc = image enrichment error: error scanning image: nexus-registry-ci-cd.apps.cluster-k8qw5.k8qw5.sandbox638.opentlc.com/backend:v1 error: scanning "nexus-registry-ci-cd.apps.cluster-k8qw5.k8qw5.sandbox638.opentlc.com/backend:v1" with scanner "Stackrox Scanner": Get "https://scanner.stackrox.svc:8080/scanner/sha/sha256:1fb8cb4ceb8153b374d85017c83f167fd99ce7039b6e2162d64de1c16e1d06de": dial tcp 172.30.5.237:8080: i/o timeout
参考
https://github.com/rhthsa/openshift-demo