学习日记——(路由与交换技术)ACL访问控制列表
一、相关概念知识
ACL(访问控制列表):是一种基于包过滤的访问控制列表。可以根据设定的条件对接口上的数据包进行过滤,允许其通过或丢弃。ACL广泛应用于路由器和三层交换机。
ACL的作用:1、在路由器接口处,决定哪种类型的通信数据被转发,哪种类型的通信数据被阻塞(检查和过滤数据包)
2、限制网络流量,提高网络性能
3、限制或减少路由更新的内容
4、提供网络访问的安全级别
ACL的工作原理:
ACL使用包过滤技术,在路由器上读取OSI七层模型的第三次和第四层包头中的信息,如源地址、目的地址、源端口、目的端口;根据预先定义好的规则,对包进行过滤,从而达到访问控制的目的。不过,ACL技术有一些局限性,由于ACL是包过滤技术,过滤的仅仅只是第三层和第四层包头中的部分信息。例:无法识别到具体的人或识别到内部的应用权限等。假如要达到“端到端”的控制效果,需要和系统级及应用级的访问权限控制结合使用
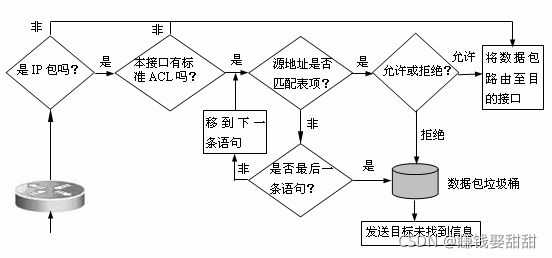
下图是ACL的工作流程
第一步:判断是否为IP包,如果不是,则将数据包直接传输到目的接口
第二步:判断该接口有没有配置ACL,如果没有,也是直接传输
第三步:判断包中的源地址是否符合ACL数据库中的某一个(将ACL表中的数据逐一跟源地址比较),如果不是,则判断下一条语句是否跟源地址一样
第四步:是否允许,拒绝的话则将该数据包丢弃
标准IP访问控制列表:
- 标准访问列表只允许过滤源地址
- 可以用于阻止某一特定网络的所有通信流量或者拒绝某一协议簇的所有通信流量
- 标准访问控制列表检查路由数据包的源地址,从而允许或拒绝基于网络、子网或主机IP地址的所有通信流量通过路由器的接口
- 适用于只控制访问的源网络的情况,端口号是1~99
扩展IP访问控制列表:
- 扩展访问列表允许过滤源地址、目的地址和上层应用数据
- 扩展访问列表既检查数据包的源地址,也检查数据包的目的地址,还检查数据包的特定协议类型,端口号等
- 扩展访问列表更具有灵活性和和可扩充性
- 可以对同一地址允许使用某些协议通信流量通过,而拒绝其他协议的通信流量通过,编号范围为:100~199
命名访问控制列表:
- 在标准与扩展访问控制列表中均要使用表号,而在命名访问控制列表中使用一个字母或数字组合的字符串来代替前面所使用的数字。
- 使用命名访问控制列表可以用来删除某一条特定的控制条目,这样,可以在使用过程中方便地进行修改。
二、例子
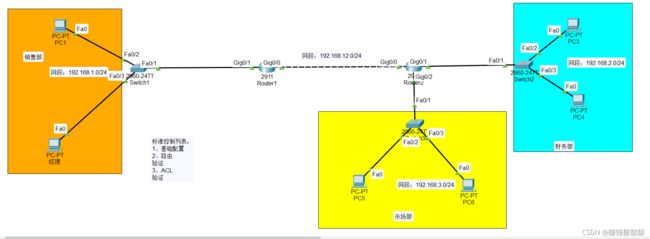
1、某企业销售部、市场部的网络和财务部的网络通过两台路由器相连,整个网络配置动态路由协议,保证网络正常通信。要求在路由器上配置标准ACL,允许销售部经理的主机能访问财务部和市场部,但拒绝销售部的其他主机访问。您作为公司的网络管理,如何实现企业的要求。
简单的拓扑结构:
相关代码:
R1:
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#host R1
R1(config)#int
R1(config)#interface g
R1(config)#interface gigabitEthernet 0/0
R1(config-if)#ip add
R1(config-if)#ip address 192.168.12.1 255.255.255.0
R1(config-if)#no sh
R1(config-if)#no shutdown
R1(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/0, changed state to up
R1(config-if)#e
R1(config-if)#exit
R1(config)#interface gigabitEthernet 0/1
R1(config-if)#ip address 192.168.1.254 255.255.255.0
R1(config-if)#no sh
R1(config-if)#no shutdown
R1(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/1, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up
R1(config-if)#e
R1(config-if)#exit
R1(config)#
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to up
R1(config)#rou
配置RIP动态路由协议
R1(config)#router rip
R1(config-router)#net
R1(config-router)#network 192.168.12.0
R1(config-router)#network 192.168.1.0
R1(config-router)#ver
R1(config-router)#version 2
R1(config-router)#end
R1#
%SYS-5-CONFIG_I: Configured from console by console
配置后的路由表
R1#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static routeGateway of last resort is not set
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, GigabitEthernet0/1
L 192.168.1.254/32 is directly connected, GigabitEthernet0/1
R 192.168.2.0/24 [120/1] via 192.168.12.2, 00:00:29, GigabitEthernet0/0
R 192.168.3.0/24 [120/1] via 192.168.12.2, 00:00:29, GigabitEthernet0/0
192.168.12.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.12.0/24 is directly connected, GigabitEthernet0/0
L 192.168.12.1/32 is directly connected, GigabitEthernet0/0
R2:
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#host R2
R2(config)#int
配置接口的IP地址
R2(config)#interface g
R2(config)#interface gigabitEthernet 0/0
R2(config-if)#ip add
R2(config-if)#ip address 192.168.12.2 255.255.255.0
R2(config-if)#no sh
R2(config-if)#no shutdown
R2(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to up
R2(config-if)#e
R2(config-if)#exit
R2(config)#interface gigabitEthernet 0/1
R2(config-if)#ip address 192.168.2.254 255.255.255.0
R2(config-if)#no sh
R2(config-if)#no shutdown
R2(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/1, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up
R2(config-if)#e
R2(config-if)#exit
R2(config)#interface gigabitEthernet 0/2
R2(config-if)#ip address 192.168.3.254 255.255.255.0
R2(config-if)#no sh
R2(config-if)#no shutdown
R2(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/2, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/2, changed state to up
R2(config-if)#e
R2(config-if)#exit
R2(config)#rou
R2(config)#router r
配置RIP动态路由协议
R2(config)#router rip
R2(config-router)#net
R2(config-router)#network 192.168.12.0
R2(config-router)#network 192.168.2.0
R2(config-router)#network 192.168.3.0
R2(config-router)#ver
R2(config-router)#version 2
R2(config-router)#end
R2#
%SYS-5-CONFIG_I: Configured from console by console
R2#show ip rou
R2#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is not set
R 192.168.1.0/24 [120/1] via 192.168.12.1, 00:00:15, GigabitEthernet0/0
192.168.2.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.2.0/24 is directly connected, GigabitEthernet0/1
L 192.168.2.254/32 is directly connected, GigabitEthernet0/1
192.168.3.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.3.0/24 is directly connected, GigabitEthernet0/2
L 192.168.3.254/32 is directly connected, GigabitEthernet0/2
192.168.12.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.12.0/24 is directly connected, GigabitEthernet0/0
L 192.168.12.2/32 is directly connected, GigabitEthernet0/0
R2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#acc
配置ACL标准控制列表
R2(config)#access-list 1 p
R2(config)#access-list 1 permit ho
R2(config)#access-list 1 permit host 192.168.1.2 允许经理的主机通过
R2(config)#ac
R2(config)#access-list 1 d
R2(config)#access-list 1 deny 192.168.1.0 0.0.0.255 拒绝1.0网段的主机通过
R2(config)#int 注:上面两句的顺序不能反,否则效果就不一样了。
R2(config)#interface g
R2(config)#interface gigabitEthernet 0/0 设置接口,为输入(in)还是输出(out)
像本例:经理的主机数据包从0/0进入其他网段的,所以为in
R2(config-if)#ip ac
R2(config-if)#ip access-group 1 in
R2(config-if)#end
R2#
%SYS-5-CONFIG_I: Configured from console by console
R2#show ac
R2#show access-lists 查看ACL列表的情况
Standard IP access list 1
10 permit host 192.168.1.2
20 deny 192.168.1.0 0.0.0.255
R2#
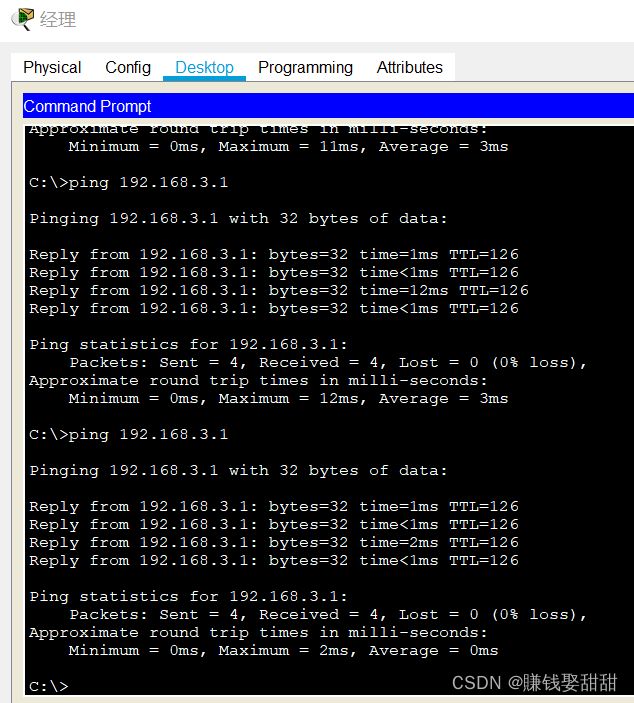
结果:
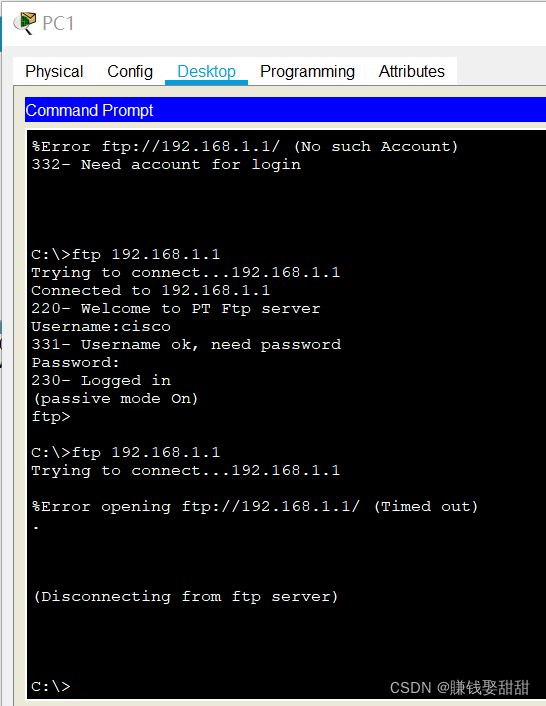
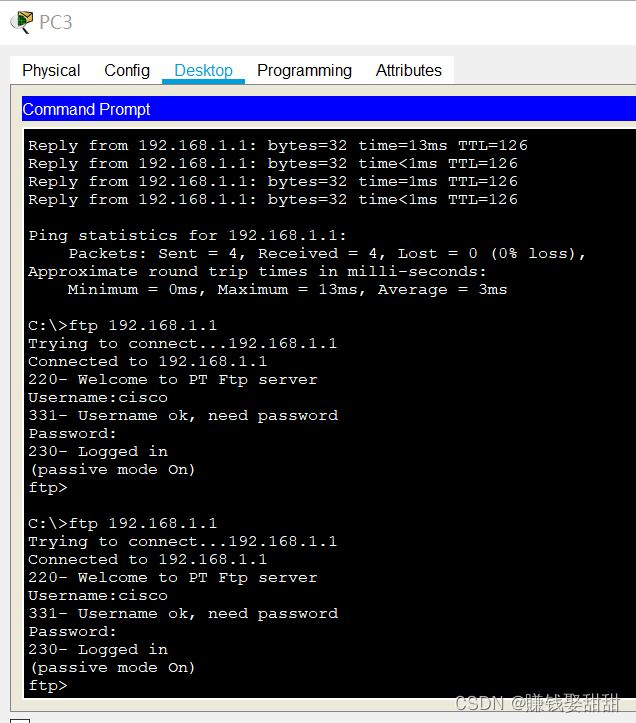
主机1 配置ACL后ping不通其他网段了
经理的主机还是可以
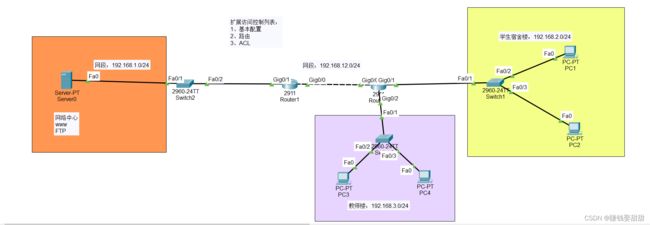
2、某学校的网管中心、教师办公楼和学生宿舍楼分属不同的三个网段,它们之间用路由器进行信息传递。网管中心架设一台服务器作为WWW和FTP服务器,WWW服务器允许所有人访问,而FTP服务器只允许教师办公楼访问。您是学校的网络管理员,如何实现这一要求。
拓扑结构:
服务器的界面:
相关代码:
R1:
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hos
Router(config)#hostname R1
R1(config)#int
配置IP地址
R1(config)#interface g
R1(config)#interface gigabitEthernet 0/0
R1(config-if)#ip add
R1(config-if)#ip address 192.168.12.1 255.255.255.0
R1(config-if)#no sh
R1(config-if)#no shutdown
R1(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/0, changed state to up
R1(config-if)#e
R1(config)#interface gigabitEthernet 0/1
R1(config-if)#ip address 192.168.1.254 255.255.255.0
R1(config-if)#no sh
R1(config-if)#no shutdown
R1(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/1, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up
R1(config-if)#e
R1(config-if)#exit
R1(config)#
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to up
R1(config)#rou
配置RIP动态路由协议
R1(config)#router rip
R1(config-router)#net
R1(config-router)#network 192.168.12.0
R1(config-router)#network 192.168.1.0
R1(config-router)#er
R1(config-router)#ver
R1(config-router)#version 2
R1(config-router)#end
R1#
%SYS-5-CONFIG_I: Configured from console by console
R1#show ip rou
R1#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is not set
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, GigabitEthernet0/1
L 192.168.1.254/32 is directly connected, GigabitEthernet0/1
R 192.168.2.0/24 [120/1] via 192.168.12.2, 00:00:08, GigabitEthernet0/0
R 192.168.3.0/24 [120/1] via 192.168.12.2, 00:00:08, GigabitEthernet0/0
192.168.12.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.12.0/24 is directly connected, GigabitEthernet0/0
L 192.168.12.1/32 is directly connected, GigabitEthernet0/0
R1#
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#acc
R1(config)#access-list 100 p
R1(config)#access-list 100 permit t
R1(config)#access-list 100 permit tcp 192.168.3.0 0.0.0.255 h
R1(config)#access-list 100 permit tcp 192.168.3.0 0.0.0.255 host 192.168.1.1 e
R1(config)#access-list 100 permit tcp 192.168.3.0 0.0.0.255 host 192.168.1.1 eq
配置ACL表
R1(config)#access-list 100 permit tcp 192.168.3.0 0.0.0.255 host 192.168.1.1 eq 80
R1(config)#access-list 100 permit tcp 192.168.3.0 0.0.0.255 host 192.168.1.1 eq ftp
R1(config)#access-list 100 permit tcp 192.168.2.0 0.0.0.255 host 192.168.1.1 eq www
R1(config)#access-list 100 deny tcp 192.168.2.0 0.0.0.255 host 192.168.1.1 eq ftp
R1(config)#access-list 100 permit ip any any
进入接口配置 数据输入与输出
R1(config)#int
R1(config)#interface g
R1(config)#interface gigabitEthernet 0/1
R1(config-if)#ac
R1(config-if)#ip acc
R1(config-if)#ip access-group 100 out
R1(config-if)#end
R1#show ac
查看ACL表
R1#show access-lists
Extended IP access list 100
10 permit tcp 192.168.3.0 0.0.0.255 host 192.168.1.1 eq www
20 permit tcp 192.168.3.0 0.0.0.255 host 192.168.1.1 eq ftp
30 permit tcp 192.168.2.0 0.0.0.255 host 192.168.1.1 eq www
40 deny tcp 192.168.2.0 0.0.0.255 host 192.168.1.1 eq ftp
50 permit ip any any
R2:
Router>en
Router#conf t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#hos
Router(config)#hostname R2
R2(config)#int
接口IP的配置
R2(config)#interface g
R2(config)#interface gigabitEthernet 0/0
R2(config-if)#ip add
R2(config-if)#ip address 192.168.12.2 255.255.255.0
R2(config-if)#no sh
R2(config-if)#no shutdown
R2(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to up
R2(config-if)#
R2(config-if)#e
R2(config-if)#exit
R2(config)#interface gigabitEthernet 0/1
R2(config-if)#ip address 192.168.2.254 255.255.255.0
R2(config-if)#no sh
R2(config-if)#no shutdown
R2(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/1, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up
R2(config-if)#e
R2(config-if)#exit
R2(config)#interface gigabitEthernet 0/2
R2(config-if)#ip address 192.168.3.254 255.255.255.0
R2(config-if)#no sh
R2(config-if)#no shutdown
R2(config-if)#
%LINK-5-CHANGED: Interface GigabitEthernet0/2, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/2, changed state to up
R2(config-if)#e
R2(config-if)#exit
R2(config)#rou
R2(config)#router r
RIP动态路由的配置
R2(config)#router rip
R2(config-router)#net
R2(config-router)#network 192.168.12.0
R2(config-router)#network 192.168.2.0
R2(config-router)#network 192.168.3.0
R2(config-router)#ver
R2(config-router)#version 2
R2(config-router)#end
R2#
%SYS-5-CONFIG_I: Configured from console by console
R2#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is not set
R 192.168.1.0/24 [120/1] via 192.168.12.1, 00:00:14, GigabitEthernet0/0
192.168.2.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.2.0/24 is directly connected, GigabitEthernet0/1
L 192.168.2.254/32 is directly connected, GigabitEthernet0/1
192.168.3.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.3.0/24 is directly connected, GigabitEthernet0/2
L 192.168.3.254/32 is directly connected, GigabitEthernet0/2
192.168.12.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.12.0/24 is directly connected, GigabitEthernet0/0
L 192.168.12.2/32 is directly connected, GigabitEthernet0/0
R2#
结果:
配置ACL扩展访问控制列表后,不能访问FTP
教师的主机没有影响
注意:以上ACL要在那个路由器配置需要考虑整个网络,才可以使配置更合理。
这篇文章就写到这里啦,哪些不好的欢迎指正。