- ARM驱动学习之4小结
JT灬新一
嵌入式C++arm开发学习linux
ARM驱动学习之4小结#include#include#include#include#include#defineDEVICE_NAME"hello_ctl123"MODULE_LICENSE("DualBSD/GPL");MODULE_AUTHOR("TOPEET");staticlonghello_ioctl(structfile*file,unsignedintcmd,unsignedlo
- react-intl——react国际化使用方案
苹果酱0567
面试题汇总与解析java开发语言中间件springboot后端
国际化介绍i18n:internationalization国家化简称,首字母+首尾字母间隔的字母个数+尾字母,类似的还有k8s(Kubernetes)React-intl是React中最受欢迎的库。使用步骤安装#usenpmnpminstallreact-intl-D#useyarn项目入口文件配置//index.tsximportReactfrom"react";importReactDOMf
- Linux CTF逆向入门
蚁景网络安全
linux运维CTF
1.ELF格式我们先来看看ELF文件头,如果想详细了解,可以查看ELF的manpage文档。关于ELF更详细的说明:e_shoff:节头表的文件偏移量(字节)。如果文件没有节头表,则此成员值为零。sh_offset:表示了该section(节)离开文件头部位置的距离+-------------------+|ELFheader|---++--------->+-------------------
- Windows安装ciphey编码工具,附一道ciscn编码题例
im-Miclelson
CTF工具网络安全
TA是什么一款智能化的编码分析解码工具,对于CTF中复杂性编码类题目可以快速攻破。编码自动分析解码的神器。如何安装Windows环境Python3.864位(最新的版本不兼容,32位的也不行)PIP直接安装pipinstallciphey-ihttps://pypi.mirrors.ustc.edu.cn/simple/安装后若是出现报错请根据错误代码行数找到对应文件,r修改成rb即可。使用标准语
- 2005年高考英语北京卷 - 阅读理解C
让文字更美
Howcouldwepossiblythinkthatkeepinganimalsincagesinunnaturalenvironments-mostlyforentertainmentpurposes-isfairandrespectful?我们怎么可能认为把动物关在非自然环境的笼子里——主要是为了娱乐目的——是公平和尊重的呢?Zooofficialssaytheyareconcernedab
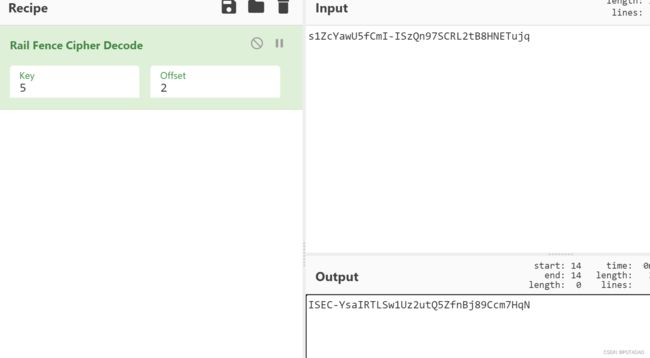
- CTF-bugku-crypto-[7+1+0]-base64解码之后做偏移
沧海一粟日尽其用
算法安全python
CTF-bugku-crypto-[7+1+0]-base64解码之后做偏移1.题目2.解题思路2.1base64编码原理2.2解题思路2.2.1base64解码找规律2.2.2破解思路3.解题脚本4.flag5.附EASCII码表1.题目提示信息:7+1+0?格式bugku{xxxxx}密文:4nXna/V7t2LpdLI44mn0fQ==要求:破解密文获得flag2.解题思路2.1base64
- CTF常见编码及加解密(超全)第二篇
不会代码的小徐
编码密码网络安全密码学预编码
HTML实体编码简述:字符实体是用一个编号写入HTML代码中来代替一个字符,在使用浏览器访问网页时会将这个编号解析还原为字符以供阅读。举例:highlighter-HTML明文:hello,world.十进制:hello,world.十六进制:hel
- CTF——web方向学习攻略
一则孤庸
CTF网络安全CTF
1计算机基础操作系统:熟悉Linux命令,方便使用Kali。网络技术:HCNA、CCNA。编程能力:拔高项,有更好。2web应用HTTP协议:必须掌握web开发框架web安全测试3数据库数据库基本操作SQL语句数据库优化4刷题
- CTF——web总结
oliveira-time
ctfweb安全
解题思路做题先看源码关注可下载的资源(zip压缩包)抓包寻找可能存在的加密信息(base64)不管三七二十一先扫描目录再说ps:正常的应该是先扫描目录,然后发现后台进行爆破,发现爆破困难,然后去社工找其他信息。CTF——web个人总结_ctfweb-CSDN博客
- VueTreeselect el-tree-select 多选
小小并不小
Vueelementjsvue.jsjavascript
1、VueTreeselect是一个多选组件npminstall--save@riophae/vue-treeselect全部代码//importthecomponentimportTreeselectfrom'@riophae/vue-treeselect'//importthestylesimport'@riophae/vue-treeselect/dist/vue-treeselect.cs
- ctf逆向解题——Bomb二进制炸弹
Funkypantss
BombPhase1在输入阶段将由文件输入的字符存储在input中,在phase1,该阶段将原字符串存储到rdi中,调用pases_1函数进行字符串比较。image进入phase1函数,该函数将原字符串rdi与预先设定的字符串“BorderrelationswithCanadahaveneverbeenbetter.”(存储在rsi中)进行比较,用于比较的函数是strings_not_equal,
- 【CTF】MISC常用工具集锦/使用方法简介
不会代码的小徐
misc网络安全测试工具
前言#MISC题型多变而且工具繁杂,因此自己花时间整理了一份工具列表,以便日后参考用流畅地阅读这篇博客,你可能需要:Python2.7.18+Python3.8+任何一个更高版本的Python,使用conda管理Linux虚拟机,kali即可流畅访问Google/GitHub等站点的网络通用工具#PuzzleSolver#专为misc手打造的瑞士军刀(?),整合了多种脚本(base,字频分析,pn
- 网络安全的相关比赛有哪些?需要掌握哪些必备技能?
网安学习
web安全安全网络安全的相关比赛有哪
01、CTF(夺旗赛)这是一种最常见的网络安全竞技形式,要求参赛者在限定时间内解决一系列涉及密码学、逆向工程、漏洞利用、取证分析等领域的挑战,获取标志(flag)并提交得分。通过举办CTF来培养网络安全人才,已经发展成为了国际网络安全圈的共识。CTF赛事可以分为线上赛和线下赛,线上赛通常是解题模式(Jeopardy),线下赛通常是攻防模式(Attack-Defense)。CTF赛事的代表性线下赛事
- 第四部分:1---文件内核对象,文件描述符,输出重定向
S+叮当猫
LinuxCentOS算法linux服务器
目录structfile内核对象:如何读写文件?文件描述符在文件描述符表中的分配规则:输出重定向初步解析:dup2实现复制文件描述符:structfile内核对象:structfile是在内核空间中创建的用于描述文件的结构体,每当一个文件被打开时,内核会为该文件创建一个对应的structfile结构体,并在文件描述符表中为其分配一个文件描述符。基于文件的定义(文件=内容+属性),structfil
- 网络攻防WEB入门指南
youhao108
网络攻防web渗透测试网络安全网络攻防
网络攻防WEB入门指南(大佬绕路)文章目录前言学习网络攻防该如何入门前言我对网络攻防的理解,分为比赛和实战两个部分,两者所学习的知识虽有共通之处,但还是有很大区别,我也在向实战的状态转换,不过二者入门所要掌握的知识差别不大。下面主要从网络攻防竞赛角度,也就是知名的CTF夺旗赛,来谈谈网络攻防知识如何入门。学习网络攻防该如何入门常规CTF比赛主要分为线上做题,以及线下AWD攻防(AttackWith
- 软考 - 系统架构设计师 - 设计模式
小林想被监督学习
系统架构设计师系统架构设计模式
目录概念创建型设计模式抽象工厂模式(AbstractFactoryPattern)优点缺点应用场景总结构建器模式(BuilderPattern)优点缺点应用场景工厂方法模式(factorymethod)优点缺点应用场景原型模式(prototype)优点缺点应用场景单例模式(Singleton)优点缺点应用场景结构型设计模式适配器模式(Adapter)优点缺点应用场景桥接模式(Bridge)优点缺点
- ctfshow web入门 ssrf web351~web360
kikkeve
ctfshowphpweb安全安全
目录SSRF基础web351web352、353web354web355web356web357web358web359web360SSRF基础SSRF(Server-SideRequestForgery:服务器端请求伪造)就是让服务器去请求服务器的资源,因为我们远程请求不到。curl_init():初始curl会话curl_setopt():会话设置curl_exec():执行curl会话,获取
- flutter 一键打出不同包名、应用名、版本名、签名、应用图标、版本号的安装包
Sindyue
flutter
1.build.gradle文件中配置不同的应用信息flavorDimensions"app"productFlavors{app1{//配置包名manifestPlaceholders=[str:"releaseStr",package_name:"com.example.demo1"]applicationId"com.example.demo1"versionCode1versionName
- CTF 竞赛密码学方向学习路径规划
David Max
CTF学习笔记密码学ctf信息安全
目录计算机科学基础计算机科学概念的引入、兴趣的引导开发环境的配置与常用工具的安装WattToolkit(Steam++)、机场代理Scoop(Windows用户可选)常用Python库SageMathLinux小工具yafuOpenSSLMarkdown编程基础Python其他编程语言、算法与数据结构(可选)数学基础离散数学与抽象代数复杂性分析密码学的正式学习兴趣的培养做题小技巧系统学习需要了解并
- MySQL8.0新特性~最左前缀匹配原则被打破了
进击的CJR
mysqlmysql
测试在MySQL8.0.25和mysql5.7.33中创建如下CREATETABLEt1(f1INTNOTNULL,f2INTNOTNULL,PRIMARYKEY(f1,f2));INSERTINTOt1VALUES(1,1),(1,2),(1,3),(1,4),(1,5),(2,1),(2,2),(2,3),(2,4),(2,5);INSERTINTOt1SELECTf1,f2+5FROMt1;
- hackcon ctf 2018 | pwn wp
fantasy_learner
BOF漏洞点:栈溢出利用过程栈溢出跳转callMeMaybe函数获得flagexpSheSellsSeaShells90流程分析:给出了输入的栈地址有一个栈溢出点没有nx利用过程:根据以上三点,得出可以使用ret2shellcode使用shellcraft生成shellcode利用栈溢出,输入并跳转到shellcodeexpSimpleYetElegent150这道题目做了最久,卡在了能否根据_d
- BUUCTF 2021-10-4 Pwn
Ch1lkat
BUUCTFPwnlinuxpwn
文章目录保持手感echo分析EXPPwnme1分析EXPwdb_2018_1st_babyheap分析EXPFSOPhouseoforange_hitcon_2016分析前置知识House_of_orangeFSOPEXPzctf_2016_note3分析EXPgyctf_2020_document分析EXP动态调试复现护网杯_gettingstart分析EXPpicoctf_2018_buffe
- C# 关于多线程同步不同实现方式
語衣
C#知识补充c#开发语言
栏目总目录AutoResetEventclassMainClass{//thearrayofconsumerthreadsprivatestaticListconsumers=newList();//thetaskqueueprivatestaticQueuetasks=newQueue();//thesynchronisationobjectforlockingthetaskqueuepriva
- Android里的设计模式
jim_dayday_up
#Android_基础知识设计模式java开发语言
一:设计模式分类经典的23种设计模式是由ErichGamma、RichardHelm、RalphJohnson和JohnVlissides(合称“GangofFour”)在他们的书《设计模式:可复用面向对象软件的基础》中定义的。以下是这些设计模式的分类和简要介绍。1.1创建型模式单例模式(Singleton):确保一个类只有一个实例,并提供一个全局访问点。抽象工厂模式(AbstractFactor
- 软考——简单记忆设计模式
Yeira
设计模式pythonjava
抽象工厂模式(AbstractFactory):提供一个接口,可以创建一系列相关或相互依赖的对象,而无需指定它们具体的类。(一个接口创建相关对象,无需具体的类)构建器模式(Builder):将一个复杂类的表示与其构造相分离,使得相同的构建过程能够得出不同的表示。(相同是构造,不同的表示)工厂方法模式(FactoryMethod):定义一个创建对象的接口,但由子类决定需要实例化哪一个类。工厂方法使得
- 【软考】设计模式之抽象工厂模式
王佑辉
软考设计模式软考
目录1.说明2.应用场景3.结构图4.构成5.适用性6.优点7.缺点8.java示例1.说明1.提供一个创建一系列相关或相互依赖对象的接口,而无须指定它们具体的类。2.抽象工厂模式(AbstractFactoryPattern)是一种创建型设计模式。3.抽象工厂模式用于系统的产品族,而不仅仅是一个等级结构;一个等级的抽象类只能创建一个等级的产品,而抽象工厂模式能创建多个等级的产品。2.应用场景1.
- 30、基于SelectFromModel和LassoCV的特征选择
凌晨思索
30、基于SelectFromModel和LassoCV的特征选择importmatplotlib.pyplotaspltimportnumpyasnpfromsklearn.datasetsimportload_diabetesfromsklearn.feature_selectionimportSelectFromModelfromsklearn.linear_modelimportLasso
- 【鸿蒙HarmonyOS开发笔记】使用@Preview装饰器预览组件
Luxine.
鸿蒙HarmonyOS开发笔记前端分享笔记华为harmonyos
概述ArkTS应用/服务支持组件预览,要求compileSdkVersion为8或以上。组件预览支持实时预览,不支持动态图和动态预览。组件预览通过在组件前添加注解@Preview实现,在单个源文件中,最多可以使用10个@Preview装饰自定义组件。@Preview的使用参考如下示例@Preview({title:'FoodImage'})@ComponentstructFoodImageDisp
- vue3+tesseract 图片文字提取
妙明元心
javascriptvue.jsecmascript
github:https://github.com/naptha/tesseract.js可实现多语言识别,中英文混合识别demo如下:importTesseractfrom"tesseract.js"//方式1:Tesseract.recognize('http://localhost:5173/vue.jpg','eng+chi_sim',).then((d)=>{console.log(d.
- iOS M1芯片Mac上Xcode模拟器报错解决
aven_kang
真机编译可以通过,模拟器失败,出现以下错误...,buildingforiOSSimulator,butlinkinginobjectfilebuiltforiOS,file'...'或者couldnotfindmodulefortarget'x86_64-apple-ios-simulator'解决方案一1.添加arm64到项目PEROJECT和TARGETS的ExcludedArchitect
- 开发者关心的那些事
圣子足道
ios游戏编程apple支付
我要在app里添加IAP,必须要注册自己的产品标识符(product identifiers)。产品标识符是什么?
产品标识符(Product Identifiers)是一串字符串,它用来识别你在应用内贩卖的每件商品。App Store用产品标识符来检索产品信息,标识符只能包含大小写字母(A-Z)、数字(0-9)、下划线(-)、以及圆点(.)。你可以任意排列这些元素,但我们建议你创建标识符时使用
- 负载均衡器技术Nginx和F5的优缺点对比
bijian1013
nginxF5
对于数据流量过大的网络中,往往单一设备无法承担,需要多台设备进行数据分流,而负载均衡器就是用来将数据分流到多台设备的一个转发器。
目前有许多不同的负载均衡技术用以满足不同的应用需求,如软/硬件负载均衡、本地/全局负载均衡、更高
- LeetCode[Math] - #9 Palindrome Number
Cwind
javaAlgorithm题解LeetCodeMath
原题链接:#9 Palindrome Number
要求:
判断一个整数是否是回文数,不要使用额外的存储空间
难度:简单
分析:
题目限制不允许使用额外的存储空间应指不允许使用O(n)的内存空间,O(1)的内存用于存储中间结果是可以接受的。于是考虑将该整型数反转,然后与原数字进行比较。
注:没有看到有关负数是否可以是回文数的明确结论,例如
- 画图板的基本实现
15700786134
画图板
要实现画图板的基本功能,除了在qq登陆界面中用到的组件和方法外,还需要添加鼠标监听器,和接口实现。
首先,需要显示一个JFrame界面:
public class DrameFrame extends JFrame { //显示
- linux的ps命令
被触发
linux
Linux中的ps命令是Process Status的缩写。ps命令用来列出系统中当前运行的那些进程。ps命令列出的是当前那些进程的快照,就是执行ps命令的那个时刻的那些进程,如果想要动态的显示进程信息,就可以使用top命令。
要对进程进行监测和控制,首先必须要了解当前进程的情况,也就是需要查看当前进程,而 ps 命令就是最基本同时也是非常强大的进程查看命令。使用该命令可以确定有哪些进程正在运行
- Android 音乐播放器 下一曲 连续跳几首歌
肆无忌惮_
android
最近在写安卓音乐播放器的时候遇到个问题。在MediaPlayer播放结束时会回调
player.setOnCompletionListener(new OnCompletionListener() {
@Override
public void onCompletion(MediaPlayer mp) {
mp.reset();
Log.i("H
- java导出txt文件的例子
知了ing
javaservlet
代码很简单就一个servlet,如下:
package com.eastcom.servlet;
import java.io.BufferedOutputStream;
import java.io.IOException;
import java.net.URLEncoder;
import java.sql.Connection;
import java.sql.Resu
- Scala stack试玩, 提高第三方依赖下载速度
矮蛋蛋
scalasbt
原文地址:
http://segmentfault.com/a/1190000002894524
sbt下载速度实在是惨不忍睹, 需要做些配置优化
下载typesafe离线包, 保存为ivy本地库
wget http://downloads.typesafe.com/typesafe-activator/1.3.4/typesafe-activator-1.3.4.zip
解压r
- phantomjs安装(linux,附带环境变量设置) ,以及casperjs安装。
alleni123
linuxspider
1. 首先从官网
http://phantomjs.org/下载phantomjs压缩包,解压缩到/root/phantomjs文件夹。
2. 安装依赖
sudo yum install fontconfig freetype libfreetype.so.6 libfontconfig.so.1 libstdc++.so.6
3. 配置环境变量
vi /etc/profil
- JAVA IO FileInputStream和FileOutputStream,字节流的打包输出
百合不是茶
java核心思想JAVA IO操作字节流
在程序设计语言中,数据的保存是基本,如果某程序语言不能保存数据那么该语言是不可能存在的,JAVA是当今最流行的面向对象设计语言之一,在保存数据中也有自己独特的一面,字节流和字符流
1,字节流是由字节构成的,字符流是由字符构成的 字节流和字符流都是继承的InputStream和OutPutStream ,java中两种最基本的就是字节流和字符流
类 FileInputStream
- Spring基础实例(依赖注入和控制反转)
bijian1013
spring
前提条件:在http://www.springsource.org/download网站上下载Spring框架,并将spring.jar、log4j-1.2.15.jar、commons-logging.jar加载至工程1.武器接口
package com.bijian.spring.base3;
public interface Weapon {
void kil
- HR看重的十大技能
bijian1013
提升能力HR成长
一个人掌握何种技能取决于他的兴趣、能力和聪明程度,也取决于他所能支配的资源以及制定的事业目标,拥有过硬技能的人有更多的工作机会。但是,由于经济发展前景不确定,掌握对你的事业有所帮助的技能显得尤为重要。以下是最受雇主欢迎的十种技能。 一、解决问题的能力 每天,我们都要在生活和工作中解决一些综合性的问题。那些能够发现问题、解决问题并迅速作出有效决
- 【Thrift一】Thrift编译安装
bit1129
thrift
什么是Thrift
The Apache Thrift software framework, for scalable cross-language services development, combines a software stack with a code generation engine to build services that work efficiently and s
- 【Avro三】Hadoop MapReduce读写Avro文件
bit1129
mapreduce
Avro是Doug Cutting(此人绝对是神一般的存在)牵头开发的。 开发之初就是围绕着完善Hadoop生态系统的数据处理而开展的(使用Avro作为Hadoop MapReduce需要处理数据序列化和反序列化的场景),因此Hadoop MapReduce集成Avro也就是自然而然的事情。
这个例子是一个简单的Hadoop MapReduce读取Avro格式的源文件进行计数统计,然后将计算结果
- nginx定制500,502,503,504页面
ronin47
nginx 错误显示
server {
listen 80;
error_page 500/500.html;
error_page 502/502.html;
error_page 503/503.html;
error_page 504/504.html;
location /test {return502;}}
配置很简单,和配
- java-1.二叉查找树转为双向链表
bylijinnan
二叉查找树
import java.util.ArrayList;
import java.util.List;
public class BSTreeToLinkedList {
/*
把二元查找树转变成排序的双向链表
题目:
输入一棵二元查找树,将该二元查找树转换成一个排序的双向链表。
要求不能创建任何新的结点,只调整指针的指向。
10
/ \
6 14
/ \
- Netty源码学习-HTTP-tunnel
bylijinnan
javanetty
Netty关于HTTP tunnel的说明:
http://docs.jboss.org/netty/3.2/api/org/jboss/netty/channel/socket/http/package-summary.html#package_description
这个说明有点太简略了
一个完整的例子在这里:
https://github.com/bylijinnan
- JSONUtil.serialize(map)和JSON.toJSONString(map)的区别
coder_xpf
jqueryjsonmapval()
JSONUtil.serialize(map)和JSON.toJSONString(map)的区别
数据库查询出来的map有一个字段为空
通过System.out.println()输出 JSONUtil.serialize(map): {"one":"1","two":"nul
- Hibernate缓存总结
cuishikuan
开源sshjavawebhibernate缓存三大框架
一、为什么要用Hibernate缓存?
Hibernate是一个持久层框架,经常访问物理数据库。
为了降低应用程序对物理数据源访问的频次,从而提高应用程序的运行性能。
缓存内的数据是对物理数据源中的数据的复制,应用程序在运行时从缓存读写数据,在特定的时刻或事件会同步缓存和物理数据源的数据。
二、Hibernate缓存原理是怎样的?
Hibernate缓存包括两大类:Hib
- CentOs6
dalan_123
centos
首先su - 切换到root下面1、首先要先安装GCC GCC-C++ Openssl等以来模块:yum -y install make gcc gcc-c++ kernel-devel m4 ncurses-devel openssl-devel2、再安装ncurses模块yum -y install ncurses-develyum install ncurses-devel3、下载Erang
- 10款用 jquery 实现滚动条至页面底端自动加载数据效果
dcj3sjt126com
JavaScript
无限滚动自动翻页可以说是web2.0时代的一项堪称伟大的技术,它让我们在浏览页面的时候只需要把滚动条拉到网页底部就能自动显示下一页的结果,改变了一直以来只能通过点击下一页来翻页这种常规做法。
无限滚动自动翻页技术的鼻祖是微博的先驱:推特(twitter),后来必应图片搜索、谷歌图片搜索、google reader、箱包批发网等纷纷抄袭了这一项技术,于是靠滚动浏览器滚动条
- ImageButton去边框&Button或者ImageButton的背景透明
dcj3sjt126com
imagebutton
在ImageButton中载入图片后,很多人会觉得有图片周围的白边会影响到美观,其实解决这个问题有两种方法
一种方法是将ImageButton的背景改为所需要的图片。如:android:background="@drawable/XXX"
第二种方法就是将ImageButton背景改为透明,这个方法更常用
在XML里;
<ImageBut
- JSP之c:foreach
eksliang
jspforearch
原文出自:http://www.cnblogs.com/draem0507/archive/2012/09/24/2699745.html
<c:forEach>标签用于通用数据循环,它有以下属性 属 性 描 述 是否必须 缺省值 items 进行循环的项目 否 无 begin 开始条件 否 0 end 结束条件 否 集合中的最后一个项目 step 步长 否 1
- Android实现主动连接蓝牙耳机
gqdy365
android
在Android程序中可以实现自动扫描蓝牙、配对蓝牙、建立数据通道。蓝牙分不同类型,这篇文字只讨论如何与蓝牙耳机连接。
大致可以分三步:
一、扫描蓝牙设备:
1、注册并监听广播:
BluetoothAdapter.ACTION_DISCOVERY_STARTED
BluetoothDevice.ACTION_FOUND
BluetoothAdapter.ACTION_DIS
- android学习轨迹之四:org.json.JSONException: No value for
hyz301
json
org.json.JSONException: No value for items
在JSON解析中会遇到一种错误,很常见的错误
06-21 12:19:08.714 2098-2127/com.jikexueyuan.secret I/System.out﹕ Result:{"status":1,"page":1,&
- 干货分享:从零开始学编程 系列汇总
justjavac
编程
程序员总爱重新发明轮子,于是做了要给轮子汇总。
从零开始写个编译器吧系列 (知乎专栏)
从零开始写一个简单的操作系统 (伯乐在线)
从零开始写JavaScript框架 (图灵社区)
从零开始写jQuery框架 (蓝色理想 )
从零开始nodejs系列文章 (粉丝日志)
从零开始编写网络游戏
- jquery-autocomplete 使用手册
macroli
jqueryAjax脚本
jquery-autocomplete学习
一、用前必备
官方网站:http://bassistance.de/jquery-plugins/jquery-plugin-autocomplete/
当前版本:1.1
需要JQuery版本:1.2.6
二、使用
<script src="./jquery-1.3.2.js" type="text/ja
- PLSQL-Developer或者Navicat等工具连接远程oracle数据库的详细配置以及数据库编码的修改
超声波
oracleplsql
在服务器上将Oracle安装好之后接下来要做的就是通过本地机器来远程连接服务器端的oracle数据库,常用的客户端连接工具就是PLSQL-Developer或者Navicat这些工具了。刚开始也是各种报错,什么TNS:no listener;TNS:lost connection;TNS:target hosts...花了一天的时间终于让PLSQL-Developer和Navicat等这些客户
- 数据仓库数据模型之:极限存储--历史拉链表
superlxw1234
极限存储数据仓库数据模型拉链历史表
在数据仓库的数据模型设计过程中,经常会遇到这样的需求:
1. 数据量比较大; 2. 表中的部分字段会被update,如用户的地址,产品的描述信息,订单的状态等等; 3. 需要查看某一个时间点或者时间段的历史快照信息,比如,查看某一个订单在历史某一个时间点的状态, 比如,查看某一个用户在过去某一段时间内,更新过几次等等; 4. 变化的比例和频率不是很大,比如,总共有10
- 10点睛Spring MVC4.1-全局异常处理
wiselyman
spring mvc
10.1 全局异常处理
使用@ControllerAdvice注解来实现全局异常处理;
使用@ControllerAdvice的属性缩小处理范围
10.2 演示
演示控制器
package com.wisely.web;
import org.springframework.stereotype.Controller;
import org.spring