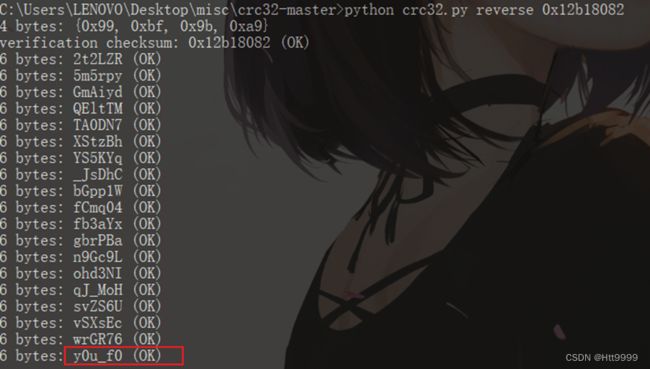
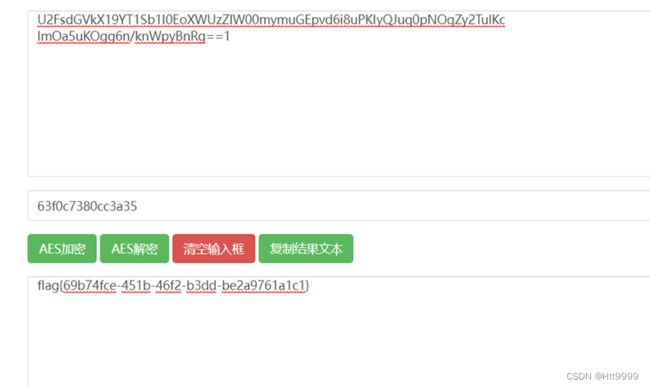
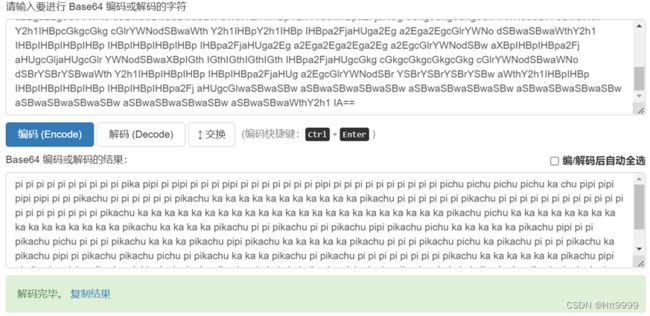
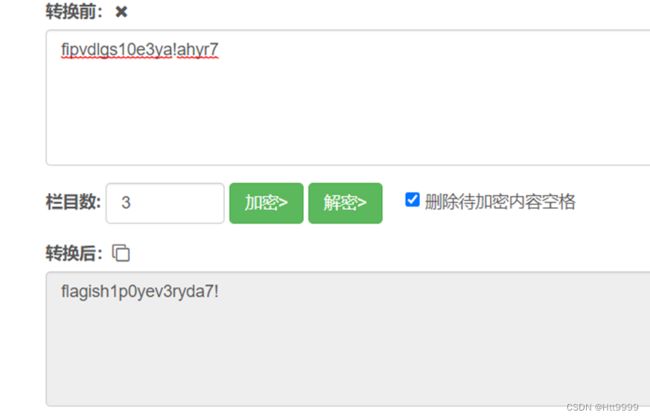
- 什么是证书吊销列表?CRL 解释
WoTrusSSL
sslhttps
数字证书是安全在线互动的支柱,用于验证身份和确保加密通信。但是,当这些证书被盗用或滥用时,必须立即撤销它们以维持信任。这就是证书撤销列表(CRL)的作用所在。CRL由证书颁发机构(CA)维护,对于识别和撤销已撤销的证书,防止其造成危害至关重要。在本指南中,我们将探讨什么是CRL、它们如何运作以及为什么它们对网络安全至关重要。什么是证书吊销列表(CRL)?证书吊销列表(CRL)是证书颁发机构(CA)
- .NET 一款基于BGInfo的红队内网渗透工具
dot.Net安全矩阵
网络.net安全.netcoreweb安全矩阵
01阅读须知此文所提供的信息只为网络安全人员对自己所负责的网站、服务器等(包括但不限于)进行检测或维护参考,未经授权请勿利用文章中的技术资料对任何计算机系统进行入侵操作。利用此文所提供的信息而造成的直接或间接后果和损失,均由使用者本人负责。本文所提供的工具仅用于学习,禁止用于其他方面02基本介绍在内网渗透过程中,白名单绕过是红队常见的技术需求。Sharp4Bginfo.exe是一款基于微软签名工具
- 计算机科学与技术
柳依依@
学习前端c4前端后端
计算机科学是一个庞大且关联性强的学科体系,初学者常面临以下痛点:-**知识点零散**:容易陷入"只见树木不见森林"的学习困境-**方向不明确**:面对海量技术栈不知从何入手-**体系缺失**:难以建立完整的知识网络1.计算机基础-计算机组成原理-冯·诺依曼体系-CPU/内存/IO设备-操作系统-进程与线程-内存管理-文件系统-计算机网络-TCP/IP模型-HTTP/HTTPS-网络安全2.编程能力
- 2025年网络安全人员薪酬趋势
程序员肉肉
web安全安全网络安全计算机信息安全程序员
2025年网络安全人员薪酬趋势一、网络安全行业为何成“香饽饽”?最近和几个朋友聊起职业规划,发现一个有趣的现象:不管原来是程序员、运维还是产品经理,都想往网络安全领域跳槽。问原因,答案出奇一致——“听说这行工资高”。确实,从2025年的数据来看,网络安全行业的薪资水平不仅跑赢了大多数IT岗位,甚至成了“技术岗里的天花板”。但高薪背后到底有哪些门道?哪些职位最赚钱?城市和经验如何影响收入?今天我们就
- 第三章:网络安全基础——构建企业数字防线
阿贾克斯的黎明
网络安全web安全安全
目录第三章:网络安全基础——构建企业数字防线3.1网络协议安全深度解析3.1.1TCP/IP协议栈安全漏洞图谱3.1.2关键安全协议剖析3.2网络攻击全景防御3.2.1OWASPTop102023最新威胁3.2.2高级持续性威胁(APT)防御3.3网络安全设备部署指南3.3.1下一代防火墙(NGFW)配置要点3.3.2IDS/IPS系统部署方案3.4企业网络架构安全设计3.4.1安全分区最佳实践3
- 数字经济时代科技创业的巨大潜力
2025年3月,42岁的字节跳动创始人张一鸣以655亿美元身家成为中国新首富。这位"80后"企业家白手起家的故事,展现了数字经济时代科技创业的巨大潜力。本文将带您了解张一鸣的成功秘诀,分析网络安全行业的最新趋势,并为计算机专业学生提供实用建议。张一鸣的成功之道张一鸣的财富增长主要得益于字节跳动的全球化布局和技术创新。2024年上半年,公司营收达730亿美元,其中海外收入占比23%。旗下TikTok
- 网络安全行业核心人才需求与职业发展路径
Gappsong874
安全网络安全程序人生职场和发展
在数字化浪潮席卷全球的今天,数据已成为驱动经济、重塑社会的核心资产。从智慧城市到工业互联网,从移动支付到远程医疗,数字技术深度融入人类生活的每个角落。然而,技术赋能的另一面是风险的指数级放大——网络攻击手段日益复杂,数据泄露事件频发,关键基础设施面临瘫痪威胁,甚至国家安全与公民隐私也暴露在未知风险之中。在此背景下,网络安全早已超越技术范畴,成为关乎国家战略、企业存续与个人权益的“数字生命线”。无论
- 网安学习NO.12
下一代防火墙(Next-GenerationFirewall,简称NGFW)是在传统防火墙基础上发展而来的新一代网络安全防护设备,其核心目标是解决传统防火墙在复杂网络环境(如云计算、移动办公、加密流量激增等)中“防护维度不足、威胁识别滞后、功能单一”等痛点,通过融合多元安全能力,实现对网络流量更精准、更智能、更全面的管控与防御。一、下一代防火墙与传统防火墙的核心差异传统防火墙主要依赖“端口-协议”
- 【WEB安全】任意URL跳转
1.1.漏洞介绍URL跳转漏洞(URLRedirectionVulnerability)又叫开放重定向漏洞(OpenRedirectVulnerability),是一种常见的网络安全漏洞,它存在于许多网站和应用程序中。该漏洞的根本原因是没有对用户提供的URL进行充分的验证和过滤,导致攻击者可以通过构造恶意URL,将用户重定向到任意的网站或应用程序中。1.2.漏洞危害以攻击用户客户端为主,对服务器本
- 网络安全核心技术解析:权限提升(Privilege Escalation)攻防全景
引言在网络安全攻防对抗中,权限提升(PrivilegeEscalation)是攻击链条中关键的「破局点」。攻击者通过突破系统权限壁垒,往往能以有限权限为跳板,最终掌控整个系统控制权。本文将从攻击原理、技术路径、实战案例到防御体系,全方位解析这一网络空间的「钥匙窃取」艺术。一、权限提升的本质与分类1.1核心定义权限提升指攻击者通过技术手段,将当前运行进程或用户的权限等级突破系统预设的访问控制机制,获
- 网络安全|填志愿选学校,选哪个学校更出洞?——漏洞库
网安导师小李
网络安全编程程序员web安全网络安全自动化运维pythonjava
这篇只讲国内漏洞挖掘这一点,在出洞数量上遥遥领先的一般是安全厂商的队伍,但是其中不乏高校、个人的身影。数据来源仅供参考,如果数据涉及错漏,欢迎指正。漏洞库CVE是国际公认最大的漏洞信息库,除此之外国内的漏洞官方信息公开渠道有:国家信息安全漏洞共享平台(CNVD):隶属于国家互联网应急中心(CNCERT),是CNCERT联合国内重要信息系统单位、基础电信运营商、网络安全厂商和软件厂商共同建立的平台。
- SMTPman,smtp的端口号是多少全面解析配置
SMTPman,smtp的端口号是多少全面解析配置在电子邮件传输中,SMTPman,smtp的端口号是多少是每个网络管理员和邮件服务用户都关心的问题。SMTP是邮件发送的核心协议,而了解SMTPman,smtp的端口号是多少,对配置邮件服务器和客户端至关重要。SMTPman,smtp的端口号是多少及其基本定义SMTP协议通常使用端口号25,但随着网络安全需求的提升,端口号已逐渐多样化。SMTPma
- 系统开发过程中,如何保证数据的安全性和隐私性?
hunzi_1
web安全安全
在商城系统开发过程中,保证数据的安全性和隐私性是至关重要的,以下是一些关键的措施:一、网络安全防护方面使用安全协议在数据传输过程中,应采用如HTTPS(HypertextTransferProtocolSecure)协议。它通过SSL/TLS(SecureSocketsLayer/TransportLayerSecurity)加密通道来传输数据,对用户在商城网站上输入的账号密码、信用卡信息等敏感数
- 网络安全工程师的职业规划?(非常详细),零基础入门到精通,看这一篇就够了
QXXXD
黑客兼职副业网络安全web安全安全网络跳槽数据库android
文章目录前言一、就业工作岗位众多网络工程师的个人职业规划一、网络工程师的职业优势二、网络工程师解读计算机网络安全工程师怎么发展职业规划文末福利前言网络安全专业网络安全专业就业前景怎么样?有哪些就业方向?一、就业工作岗位众多网络安全专业毕业生就业的岗位较多,可以在计算机科学与技术、信息通信、电子商务、互联网金融、电子政务等领域从事相关工作。也可以在***机关事业单位,银行、保险、证券等金融机构,电信
- 国际刑事法院ICC遭遇复杂网络攻击
攻击事件概况国际刑事法院(ICC,InternationalCriminalCourt)正在调查一起上周发现并成功遏制的复杂网络攻击事件。2025年6月30日,该机构正式宣布遭受了具有针对性的高级网络攻击,其防御系统及时发现并控制了事态发展。国际刑事法院在声明中表示:"上周晚些时候,国际刑事法院检测到一起新型、复杂且具有针对性的网络安全事件,目前该事件已得到控制。这是近年来国际刑事法院遭遇的第二起
- EDR、NDR、XDR工作原理和架构及区别
hao_wujing
安全
大家读完觉得有帮助记得关注和点赞!!!EDR、NDR、XDR是网络安全中关键的检测与响应技术,它们在覆盖范围、数据源和响应机制上有显著差异。以下是它们的工作原理和架构详解:---###一、EDR(端点检测与响应)####⚙️**工作原理**1.**数据采集**:在终端设备(PC、服务器等)部署代理,实时监控进程、文件操作、网络连接、注册表变更等行为数据。2.**威胁检测**:-**签名匹配**:比
- Netstat高级分析工具:Windows与Linux双系统兼容的精准筛查利器
Netstat高级分析工具:Windows与Linux双系统兼容的精准筛查利器在网络安全运维中,快速识别可疑连接是防御入侵的关键一步。本文将介绍一款我本人开发的原创高效的双系统兼容Netstat信息分析工具,大幅提升恶意连接筛查效率。一、Netstat分析在安全运维中的核心价值作为网络安全工程师,我们每天都需要处理大量网络连接数据。netstat-ano命令是分析网络连接的基础工具,但在实际工作中
- 【实战总结】WMIC在HW行动中的4类关键应用
WMIC命令完全指南:网络安全运维工程师的深度实践手册关键词:WMIC命令、Windows管理、网络安全运维、系统信息收集、进程分析、自动化审计【实战总结】WMIC在HW行动中的4类关键应用1.前言在Windows环境下的网络安全运维中,WMIC(WindowsManagementInstrumentationCommand-line)是一个强大但常被低估的管理工具。它通过WMI(WindowsM
- 标准引领|美创参编两项国家标准正式发布!
安全发展标准先行近日,国家标准化领域传来喜讯!杭州美创科技股份有限公司深度参与编制的两项国家标准,于2025年6月30日正式发布,并将于2026年1月1日起正式实施。GB/T20988-2025《网络安全技术信息系统灾难恢复规范》GB/T45909-2025《网络安全技术数字水印技术实现指南》GB/T20988-2025《网络安全技术信息系统灾难恢复规范》GB/T20988-2025《网络安全技术
- 国产飞腾主板,赋能网络安全防御硬手段
当前,网络安全形势严峻,网络攻击手段不断翻新,从数据泄露到电脑中毒,企业、机构乃至国家的数字资产都面临着巨大风险。在此背景下,国产硬件技术的突破对筑牢网络安全防线意义重大。高能计算机基于市场需求,联合飞腾推出国产飞腾网络安全主板GM-N201F-D,成为网络安全防御体系中至关重要的一环。在数字化转型加速的当下,网络数据量呈爆发式增长,对网络安全设备的数据处理能力提出了更高要求。飞腾主板搭载飞腾D2
- 【网络安全】利用 Cookie Sandwich 窃取 HttpOnly Cookie
秋说
web安全XSS
未经许可,不得转载。文章目录引言Cookie三明治原理解析ApacheTomcat行为Python框架行为窃取HttpOnly的PHPSESSIDCookie第一步:识别XSS漏洞第二步:发现反射型Cookie参数第三步:通过Cookie降级实现信息泄露第四步:整合攻击流程修复建议引言本文将介绍一种名为“CookieSandwich”(Cookie三明治)的技术,该技术可用于在特定服务器上绕过Ht
- dict协议在网络安全中的应用与风险分析
Bruce_xiaowei
笔记渗透测试总结经验web安全网络安全伪协议
dict://协议在网络安全中的应用与风险分析作为一名网络安全工程师,我经常遇到各种协议被滥用的情况。今天我们将深入探讨一个较少被提及但极具价值的协议——dict://,分析其在攻击面中的潜在风险与实际防御策略。协议基础:理解dict://的本质dict://是基于DICT协议(RFC2229)实现的URI方案,主要用于查询字典数据库。其基本结构如下:dict://[;@][:]/::默认端口:2
- 想转行网络安全,可以先看看过来人的建议
孤独的汤姆
web安全安全
在当前就业形势下,不少朋友面临转行的困境。网络安全作为一个热门领域,自然也吸引了许多人的目光。本文将就转行网络安全这一话题,提供一些切实可行的建议。网络安全行业概况网络安全涵盖了从基础的脚本编写到高级的漏洞研究等多个层面。该领域包括但不限于:渗透测试、漏洞评估、恶意软件分析、入侵检测、信息安全管理等。这些内容的复杂性不一,从基础的安全监控到复杂的安全架构设计都涉及其中。这就意味着,尽管有些领域可能
- 常见的网络攻击方式及防御措施
神的孩子都在歌唱
计算机网络原理网络运维服务器
常见的网络攻击方式及防御措施:全面解析网络安全威胁前言肝文不易,点个免费的赞和关注,有错误的地方请指出,看个人主页有惊喜。作者:神的孩子都在歌唱在信息化高速发展的今天,网络安全威胁无处不在,不论是个人用户、企业组织,甚至是政府部门,都面临着各种形式的网络攻击。今天,神唱就来带大家一起深入了解常见的网络攻击方式以及如何有效防御这些攻击。一.网络攻击的基本概念1.1什么是网络攻击?网络攻击是指攻击者通
- 网络工具Fing Network Tools v12.10.2专业版,WiFi设备扫描神器
米豆学社
网络工具
[软件名称]:网络工具FingNetworkTools[软件大小]:49.2MB[下载通道]:夸克盘|迅雷盘软件介绍《FingNetworkTools》v12.10.2专业版|WiFi安全卫士,一键检测所有联网设备✨核心功能设备扫描–实时发现WiFi网络中的所有连接设备,识别陌生入侵者⚡网络诊断–速度测试+延迟分析,找出Netflix卡顿真凶️安全防护–入侵检测+防火墙功能,守护家庭网络安全高级工
- CTFSHOW-WEB-36D杯
wyjcxyyy
前端android
给你shell这道题对我这个新手还是有难度的,花了不少时间。首先f12看源码,看到?view_source,点进去看源码location.href=\'./index.php\'');if(!isset($_GET['code'])){show_source(__FILE__);exit();}else{$code=$_GET['code'];if(!preg_match($secret_waf,
- 网络安全-反弹shell详解(攻击,检测与防御)
程序员鱼
web安全网络安全单片机服务器linuxuni-app
反弹Shell:详解、攻击、检测与防御反弹Shell(ReverseShell)是一种网络安全领域中常见的攻击技术,通常用于远程控制受害者的计算机。本文旨在从网络安全的角度详细介绍反弹Shell的工作原理,实施方法以及如何检测和防御这类攻击。一、Shell的简介与原理1.1什么是Shell?Shell在计算机系统中指的是一个用户界面,用于访问操作系统的服务。在网络安全中,攻击者常利用Shell来控
- 116道网络安全面试真题(附答案),建议收藏!
程序员肉肉
web安全面试安全网络安全计算机程序员
116道网络安全面试真题(附答案),建议收藏!随着国家对网络安全的重视度,促使这个职业也变得炙手可热,越来越多的年轻人为进入安全领域在做准备。******数以百计的面试,为何迟迟无法顺利入职?********能力无疑是至关重要的,可却有不少能力不比已入职的同事差却应聘失败的人,那到底该如何做呢?为了帮助大家更快地拿到心仪Offer,我们给小伙伴们整理了一份**《网络安全工程师超高频面试真题》,结合
- 标题:2025传统制造业护网实战指南:从合规防御到智能免疫的体系化进阶
上海云盾商务经理杨杨
网络
引言2025年,随着《工业互联网企业网络安全》三项国家标准全面实施,护网行动已从“合规检查”升级为“能力对抗”。传统制造业在数字化转型浪潮中,面临设备老旧、人才短缺、供应链风险激增等挑战,41.5%的企业计划年内增加安全预算。本文将结合新规要求与行业最佳实践,深度解析传统制造业如何构建“技术-管理-运营”三位一体的护网防御体系。一、传统制造业的护网困境:三大核心矛盾1.设备老旧化vs安全新标准历史
- 网络安全之如何设置云服务器禁止 ping?两种设置方法教你搞定 云服务器无法ping通、ping不通云主机、Linux禁止ping、ICMP屏蔽、网络安全最佳实践 sysctl.conf配置
代码简单说
运维宝典限时特惠服务器web安全linux服务器禁止ping云服务器禁止ping服务器禁止ping的方法
云主机如何设置云服务器禁止ping?两种设置方法教你搞定标签:云服务器无法ping通、ping不通云主机、Linux禁止ping、ICMP屏蔽、网络安全最佳实践、sysctl.conf配置前几天上线了一个测试服务,总有安全团队扫端口,还时不时用ping探测存活,我开始思考:云服务器到底要不要禁ping?一、禁ping的好处和坏处作为一名前端转全栈开发的程序员,我越来越觉得网络安全不能忽视。“pin
- java杨辉三角
3213213333332132
java基础
package com.algorithm;
/**
* @Description 杨辉三角
* @author FuJianyong
* 2015-1-22上午10:10:59
*/
public class YangHui {
public static void main(String[] args) {
//初始化二维数组长度
int[][] y
- 《大话重构》之大布局的辛酸历史
白糖_
重构
《大话重构》中提到“大布局你伤不起”,如果企图重构一个陈旧的大型系统是有非常大的风险,重构不是想象中那么简单。我目前所在公司正好对产品做了一次“大布局重构”,下面我就分享这个“大布局”项目经验给大家。
背景
公司专注于企业级管理产品软件,企业有大中小之分,在2000年初公司用JSP/Servlet开发了一套针对中
- 电驴链接在线视频播放源码
dubinwei
源码电驴播放器视频ed2k
本项目是个搜索电驴(ed2k)链接的应用,借助于磁力视频播放器(官网:
http://loveandroid.duapp.com/ 开放平台),可以实现在线播放视频,也可以用迅雷或者其他下载工具下载。
项目源码:
http://git.oschina.net/svo/Emule,动态更新。也可从附件中下载。
项目源码依赖于两个库项目,库项目一链接:
http://git.oschina.
- Javascript中函数的toString()方法
周凡杨
JavaScriptjstoStringfunctionobject
简述
The toString() method returns a string representing the source code of the function.
简译之,Javascript的toString()方法返回一个代表函数源代码的字符串。
句法
function.
- struts处理自定义异常
g21121
struts
很多时候我们会用到自定义异常来表示特定的错误情况,自定义异常比较简单,只要分清是运行时异常还是非运行时异常即可,运行时异常不需要捕获,继承自RuntimeException,是由容器自己抛出,例如空指针异常。
非运行时异常继承自Exception,在抛出后需要捕获,例如文件未找到异常。
此处我们用的是非运行时异常,首先定义一个异常LoginException:
/**
* 类描述:登录相
- Linux中find常见用法示例
510888780
linux
Linux中find常见用法示例
·find path -option [ -print ] [ -exec -ok command ] {} \;
find命令的参数;
- SpringMVC的各种参数绑定方式
Harry642
springMVC绑定表单
1. 基本数据类型(以int为例,其他类似):
Controller代码:
@RequestMapping("saysth.do")
public void test(int count) {
}
表单代码:
<form action="saysth.do" method="post&q
- Java 获取Oracle ROWID
aijuans
javaoracle
A ROWID is an identification tag unique for each row of an Oracle Database table. The ROWID can be thought of as a virtual column, containing the ID for each row.
The oracle.sql.ROWID class i
- java获取方法的参数名
antlove
javajdkparametermethodreflect
reflect.ClassInformationUtil.java
package reflect;
import javassist.ClassPool;
import javassist.CtClass;
import javassist.CtMethod;
import javassist.Modifier;
import javassist.bytecode.CodeAtt
- JAVA正则表达式匹配 查找 替换 提取操作
百合不是茶
java正则表达式替换提取查找
正则表达式的查找;主要是用到String类中的split();
String str;
str.split();方法中传入按照什么规则截取,返回一个String数组
常见的截取规则:
str.split("\\.")按照.来截取
str.
- Java中equals()与hashCode()方法详解
bijian1013
javasetequals()hashCode()
一.equals()方法详解
equals()方法在object类中定义如下:
public boolean equals(Object obj) {
return (this == obj);
}
很明显是对两个对象的地址值进行的比较(即比较引用是否相同)。但是我们知道,String 、Math、I
- 精通Oracle10编程SQL(4)使用SQL语句
bijian1013
oracle数据库plsql
--工资级别表
create table SALGRADE
(
GRADE NUMBER(10),
LOSAL NUMBER(10,2),
HISAL NUMBER(10,2)
)
insert into SALGRADE values(1,0,100);
insert into SALGRADE values(2,100,200);
inser
- 【Nginx二】Nginx作为静态文件HTTP服务器
bit1129
HTTP服务器
Nginx作为静态文件HTTP服务器
在本地系统中创建/data/www目录,存放html文件(包括index.html)
创建/data/images目录,存放imags图片
在主配置文件中添加http指令
http {
server {
listen 80;
server_name
- kafka获得最新partition offset
blackproof
kafkapartitionoffset最新
kafka获得partition下标,需要用到kafka的simpleconsumer
import java.util.ArrayList;
import java.util.Collections;
import java.util.Date;
import java.util.HashMap;
import java.util.List;
import java.
- centos 7安装docker两种方式
ronin47
第一种是采用yum 方式
yum install -y docker
- java-60-在O(1)时间删除链表结点
bylijinnan
java
public class DeleteNode_O1_Time {
/**
* Q 60 在O(1)时间删除链表结点
* 给定链表的头指针和一个结点指针(!!),在O(1)时间删除该结点
*
* Assume the list is:
* head->...->nodeToDelete->mNode->nNode->..
- nginx利用proxy_cache来缓存文件
cfyme
cache
user zhangy users;
worker_processes 10;
error_log /var/vlogs/nginx_error.log crit;
pid /var/vlogs/nginx.pid;
#Specifies the value for ma
- [JWFD开源工作流]JWFD嵌入式语法分析器负号的使用问题
comsci
嵌入式
假如我们需要用JWFD的语法分析模块定义一个带负号的方程式,直接在方程式之前添加负号是不正确的,而必须这样做:
string str01 = "a=3.14;b=2.71;c=0;c-((a*a)+(b*b))"
定义一个0整数c,然后用这个整数c去
- 如何集成支付宝官方文档
dai_lm
android
官方文档下载地址
https://b.alipay.com/order/productDetail.htm?productId=2012120700377310&tabId=4#ps-tabinfo-hash
集成的必要条件
1. 需要有自己的Server接收支付宝的消息
2. 需要先制作app,然后提交支付宝审核,通过后才能集成
调试的时候估计会真的扣款,请注意
- 应该在什么时候使用Hadoop
datamachine
hadoop
原帖地址:http://blog.chinaunix.net/uid-301743-id-3925358.html
存档,某些观点与我不谋而合,过度技术化不可取,且hadoop并非万能。
--------------------------------------------万能的分割线--------------------------------
有人问我,“你在大数据和Hado
- 在GridView中对于有外键的字段使用关联模型进行搜索和排序
dcj3sjt126com
yii
在GridView中使用关联模型进行搜索和排序
首先我们有两个模型它们直接有关联:
class Author extends CActiveRecord {
...
}
class Post extends CActiveRecord {
...
function relations() {
return array(
'
- 使用NSString 的格式化大全
dcj3sjt126com
Objective-C
格式定义The format specifiers supported by the NSString formatting methods and CFString formatting functions follow the IEEE printf specification; the specifiers are summarized in Table 1. Note that you c
- 使用activeX插件对象object滚动有重影
蕃薯耀
activeX插件滚动有重影
使用activeX插件对象object滚动有重影 <object style="width:0;" id="abc" classid="CLSID:D3E3970F-2927-9680-BBB4-5D0889909DF6" codebase="activex/OAX339.CAB#
- SpringMVC4零配置
hanqunfeng
springmvc4
基于Servlet3.0规范和SpringMVC4注解式配置方式,实现零xml配置,弄了个小demo,供交流讨论。
项目说明如下:
1.db.sql是项目中用到的表,数据库使用的是oracle11g
2.该项目使用mvn进行管理,私服为自搭建nexus,项目只用到一个第三方 jar,就是oracle的驱动;
3.默认项目为零配置启动,如果需要更改启动方式,请
- 《开源框架那点事儿16》:缓存相关代码的演变
j2eetop
开源框架
问题引入
上次我参与某个大型项目的优化工作,由于系统要求有比较高的TPS,因此就免不了要使用缓冲。
该项目中用的缓冲比较多,有MemCache,有Redis,有的还需要提供二级缓冲,也就是说应用服务器这层也可以设置一些缓冲。
当然去看相关实现代代码的时候,大致是下面的样子。
[java]
view plain
copy
print
?
public vo
- AngularJS浅析
kvhur
JavaScript
概念
AngularJS is a structural framework for dynamic web apps.
了解更多详情请见原文链接:http://www.gbtags.com/gb/share/5726.htm
Directive
扩展html,给html添加声明语句,以便实现自己的需求。对于页面中html元素以ng为前缀的属性名称,ng是angular的命名空间
- 架构师之jdk的bug排查(一)---------------split的点号陷阱
nannan408
split
1.前言.
jdk1.6的lang包的split方法是有bug的,它不能有效识别A.b.c这种类型,导致截取长度始终是0.而对于其他字符,则无此问题.不知道官方有没有修复这个bug.
2.代码
String[] paths = "object.object2.prop11".split("'");
System.ou
- 如何对10亿数据量级的mongoDB作高效的全表扫描
quentinXXZ
mongodb
本文链接:
http://quentinXXZ.iteye.com/blog/2149440
一、正常情况下,不应该有这种需求
首先,大家应该有个概念,标题中的这个问题,在大多情况下是一个伪命题,不应该被提出来。要知道,对于一般较大数据量的数据库,全表查询,这种操作一般情况下是不应该出现的,在做正常查询的时候,如果是范围查询,你至少应该要加上limit。
说一下,
- C语言算法之水仙花数
qiufeihu
c算法
/**
* 水仙花数
*/
#include <stdio.h>
#define N 10
int main()
{
int x,y,z;
for(x=1;x<=N;x++)
for(y=0;y<=N;y++)
for(z=0;z<=N;z++)
if(x*100+y*10+z == x*x*x
- JSP指令
wyzuomumu
jsp
jsp指令的一般语法格式: <%@ 指令名 属性 =”值 ” %>
常用的三种指令: page,include,taglib
page指令语法形式: <%@ page 属性 1=”值 1” 属性 2=”值 2”%>
include指令语法形式: <%@include file=”relative url”%> (jsp可以通过 include