Illustration for .NET framework
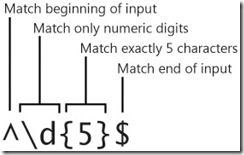
1. Analysis of a regular expression
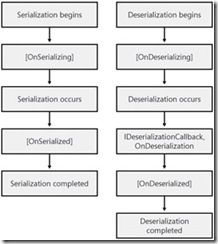
2. You can use serialization events to run methods during different phases of the serialization and deserialization process
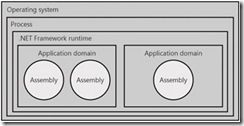
3. Application domains keep assemblies separate within a single process
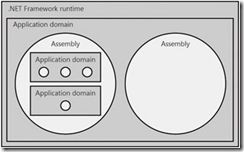
4. Assemblies can host child application domains
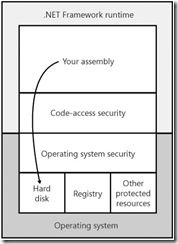
5. CAS complements, but does not replace, role-based security
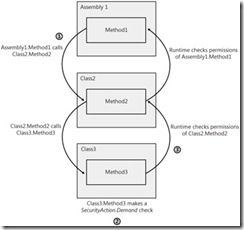
6. Demand checks all callers for a permission
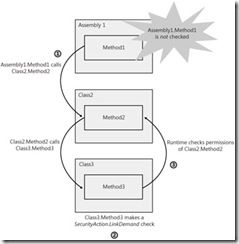
7. LinkDemand checks only the immediate caller
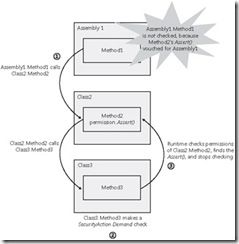
8. Assert blocks demand checks, increasing performance and allowing underprivileged code to call methods with CAS permission requirements
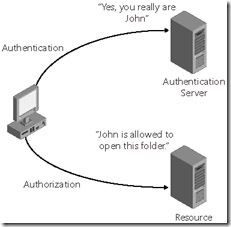
9. To access a resource, a user must be authenticated and then authorized
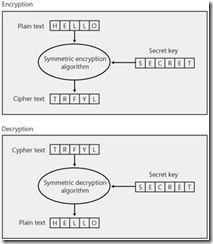
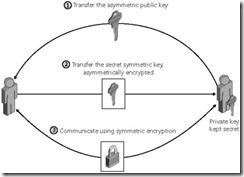
10. Symmetric encryption uses the same key for both encryption and decryption
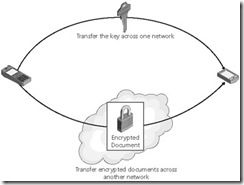
11. Symmetric key encryption requires separately exchanging both the key and the encrypted document
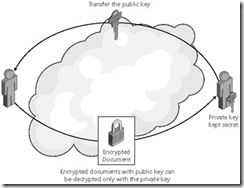
12. Asymmetric cryptography uses separate keys for encryption and decryption
13. Combine asymmetric and symmetric algorithms to optimize both security and performance