看一眼就会的k8s权限管理手把手教学
Kubernetes
Kubernetes使用RBAC授权
- Kubernetes
- 一、API概述
-
- 1.Role 和 ClusterRole
- 1.RoleBinding和ClusterRoleBinding
- 二、使用步骤(Role及RoleBinding为例)
-
- 1、创建user用户证书
- 2、创建集群、用户
-
-
- 1、创建集群配置文件
- 2、创建基于集群和新用户的上下文
-
- 3、给yuantu用户授予权限
-
-
- 1、建立角色
- 2、将角色绑定到用户yuantu
- 3、使用用户yuantu测试
- 4、查看role、rolebinding
- 5、删除权限
-
- 4、为linux系统用户k8s-yuantu与k8s集群用户yuantu相关联
-
-
- 1、将集群配置文件copy到系统用户k8s-yuantu的默认目录下,更改文件权限k8s-yuantu
- 2、切换成k8s-yuantu用户,就可以访问k8s集群中yuantu用户的有权访问的资源
-
注意: 文章配置的k8s-yuantu用户为linux系统用户; 而yuantu用户为k8s集群中对应的用户。RBAC(Role base access control)基于角色的访问控制
kubectl create deployment nginx --image=nginx -n kube-public
useradd k8s-yuantu
passwd k8s-yuantu
cd /home/k8s-yuantu
一、API概述
Role #角色,基于名称空间下的资源
RoleBinding #角色绑定,基于名称空间下的资源
ClusterRole #集群角色,基于集群级别下的资源
ClusterRoleBinding #集群角色绑定,基于集群级别下的资源
其中,Role和Role是针对于名称空间级别,授予其所在名称空间范围内的许可权限。而ClusterRole和ClusterRoleBinding是针对于集群级别,授予其所在集群范围内的许可权限。
1.Role 和 ClusterRole
Role是一系列的权限的集合,例如一个Role可以包含读取 Pod 的权限和列出 Pod 的权限, ClusterRole 跟 Role 类似,但是可以在集群中全局使用。
Role只能授予单个namespace 中资源的访问权限。
1.RoleBinding和ClusterRoleBinding
RoleBinding是将Role中定义的权限授予给用户或用户组。它包含一个subjects列表(users,groups ,service accounts),并引用该Role。RoleBinding在某个namespace 内授权,ClusterRoleBinding适用在集群范围内使用。
RoleBinding可以引用相同namespace下定义的Role。
二、使用步骤(Role及RoleBinding为例)
1、创建user用户证书
创建私钥
umask 077; openssl genrsa -out yuantu.key 2048
openssl req -new -key yuantu.key -out yuantu.csr -subj "/CN=yuantu"
![]()
如果定义组,则组可以作为权限分配的主体,比如:
openssl req -new -key yuantu.key -out yuantu.csr -subj "/CN=yuantu/O=yuantu-admin"
角色授权绑定文件可以定义如下:
subjects:
apiGroup: rbac.authorization.k8s.io
kind: Group
name: yuantu-admin
用服务端CA签署并创建证书
openssl x509 -req -in yuantu.csr -CA /etc/kubernetes/pki/ca.crt -CAkey /etc/kubernetes/pki/ca.key -CAcreateserial -out yuantu.crt -days 365
查看证书
openssl x509 -in yuantu.crt -text -noout
2、创建集群、用户
export KUBE_APISERVER="https://192.168.122.30:6443"
![]()
1、创建集群配置文件
kubectl config set-cluster kubernetes --certificate-authority=/etc/kubernetes/pki/ca.crt --embed-certs=true --server=${KUBE_APISERVER} --kubeconfig=kube-config
![]()
注意:使用ca.crt证书,作为集群授权证书,当前目录下生成kube-config配置文件
kubectl config set-credentials yuantu --client-certificate=/home/k8s-yuantu/yuantu.crt --embed-certs=true --client-key=/home/k8s-yuantu/yuantu.key --kubeconfig=kube-config
![]()
注意:
- 在kube-config集群配置文件中查看user 名为 yuantu
- 采用客户端证书和私钥
2、创建基于集群和新用户的上下文
kubectl config set-context yuantu@kubernetes --cluster=kubernetes --user=yuantu --kubeconfig=kube-config
kubectl config use-context yuantu@kubernetes --kubeconfig=kube-config
注意: 上下文名称为 yuantu@kubernetes
集群名称为kubernetes
用户名称为yuantu
3、给yuantu用户授予权限
1、建立角色
kubectl create role pods-reader --verb=get,list,watch --resource=pods -n kube-public -o yaml > role-demo.yaml
cat role-demo.yaml
![]()
注:这些资源对象的修改会立即生效的
--verb:是动作名称如:get,list,watch等。
--resource:是资源类型如:pods,deploy,svc等;注意这里如果写入namespaces是无用的,因为role就是在namespace级别的,而namespaces选项是集群级别的。
--dry-run:运行这条命令,但不生效,常用于测试。
--role:是集群中现已存在的role资源对象。
--user:填写集群中现已存在的用户。或创建完rolebinding后创建这个用户。
--clusterrole:是集群中现已存在的clusterrole资源对象。
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
creationTimestamp: "2022-11-18T03:21:39Z"
name: pods-reader
namespace: kube-public
resourceVersion: "26736"
selfLink: /apis/rbac.authorization.k8s.io/v1/namespaces/kube-public/roles/pods-reader
uid: 09e3bf04-913a-46ce-9463-be36e3d24e78
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
2、将角色绑定到用户yuantu
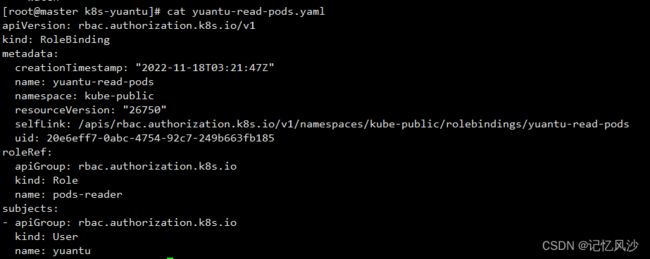
kubectl create rolebinding yuantu-read-pods --role=pods-reader --user=yuantu --namespace=kube-public -o yaml > yuantu-read-pods.yaml
cat yuantu-read-pods.yaml
![]()
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: "2022-11-18T03:21:47Z"
name: yuantu-read-pods
namespace: kube-public
resourceVersion: "26750"
selfLink: /apis/rbac.authorization.k8s.io/v1/namespaces/kube-public/rolebindings/yuantu-read-pods
uid: 20e6eff7-0abc-4754-92c7-249b663fb185
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: pods-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: yuantu
3、使用用户yuantu测试
kubectl config use-context yuantu@kubernetes --kubeconfig=kube-config
查看权限
kubectl get pods -n kube-public --kubeconfig=kube-config
NAME READY STATUS RESTARTS AGE
nginx-554b9c67f9-xrxl6 1/1 Running 0 15m
其他无权限
kubectl get pods --kubeconfig=kube-config
kubectl get deployment --kubeconfig=kube-config
Error from server (Forbidden): pods is forbidden: User "yuantu" cannot list resource "pods" in API group "" in the namespace "default"
Error from server (Forbidden): deployments.extensions is forbidden: User "yuantu" cannot list resource "deployments" in API group "extensions" in the namespace "default"
4、查看role、rolebinding
kubectl get role -n kube-public
NAME AGE
kubeadm:bootstrap-signer-clusterinfo 21d
pods-reader 7m39s
system:controller:bootstrap-signer 21d
kubectl get rolebinding -n kube-public
NAME AGE
kubeadm:bootstrap-signer-clusterinfo 21d
system:controller:bootstrap-signer 21d
yuantu-read-pods 9m58s
5、删除权限
解除角色绑定
kubectl delete rolebinding yuantu-read-pods -n kube-public
rolebinding.rbac.authorization.k8s.io "yuantu-read-pods" deleted
删除角色
kubectl delete role pods-reader -n kube-public
role.rbac.authorization.k8s.io "pods-reader" deleted
4、为linux系统用户k8s-yuantu与k8s集群用户yuantu相关联
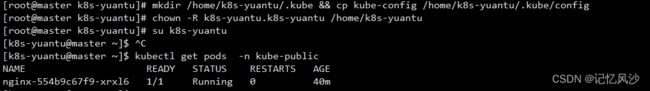
1、将集群配置文件copy到系统用户k8s-yuantu的默认目录下,更改文件权限k8s-yuantu
mkdir /home/k8s-yuantu/.kube && cp kube-config /home/k8s-yuantu/.kube/config
chown -R k8s-yuantu.k8s-yuantu /home/k8s-yuantu
2、切换成k8s-yuantu用户,就可以访问k8s集群中yuantu用户的有权访问的资源
su k8s-yuantu
kubectl get pods -n kube-public
NAME READY STATUS RESTARTS AGE
nginx-554b9c67f9-xrxl6 1/1 Running 0 40m