在eNSP模拟器上使用usg6000v实现双机热备(旁路部署,上下行连接三层设备的主备备份组网)
在eNSP模拟器上使用usg6000v实现双机热备(旁路部署,上三下三,主备模式)
-
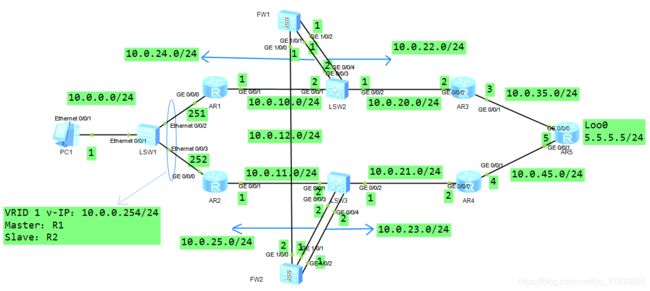
- 拓扑图
- 设备选型
- 实验要求
- 操作步骤
- 结果验证
拓扑图
设备选型
PC1设备为PC型终端设备
LSW1设备为S3700型交换机
LSW2-3为S5700型交换机
AR1-5为AR2220型路由器
FW1-2为USG6000型防火墙
实验要求
1.完成所有设备的初始化配置(命名,接口IP,FW设备的安全区域划分)
2.在AR1-2设备上部署VRRP备份组,用于内网设备的网关
3.底层部署OSPF,Trust区域(内网区域)为OSPF10,Untrust区域(外网区域)为OSPF20并在FW设备上双向引入
4.防火墙上开启HRP协议,配置心跳接口,追踪业务端口,并指定FW2设备为备份设备
5.在两个核心交换机(LSW2-3)上配置策略路由,调整来回流量路径使其经过防火墙
6.主设备上根据业务需求配置安全策略
7.为实现主备链路的及时切换,需要创建BFD会话(R1<–>FW1,FW1<–>R5)
8.在连接终端设备的VRRP备份组以及防火墙的HRP协议上都联动已创建好的BFD会话实现主备角色的一致切换
操作步骤
1.设备初始化配置
sysname R1
#
interface GigabitEthernet0/0/0
ip address 10.0.0.251 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.0.10.1 255.255.255.0
AR2:
sysname R2
#
interface GigabitEthernet0/0/0
ip address 10.0.0.252 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.0.11.1 255.255.255.0
AR3:
sysname R3
#
interface GigabitEthernet0/0/0
ip address 10.0.20.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.0.35.3 255.255.255.0
AR4:
sysname R4
#
interface GigabitEthernet0/0/0
ip address 10.0.21.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.0.45.4 255.255.255.0
AR5:
sysname R5
#
interface GigabitEthernet0/0/0
ip address 10.0.35.5 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 10.0.45.5 255.255.255.0
#
interface LoopBack0
ip address 5.5.5.5 255.255.255.0
LSW2:
sysname Sw2
#
undo info-center enable
#
vlan batch 10 20 30 40
#
interface Vlanif10
ip address 10.0.10.2 255.255.255.0
#
interface Vlanif20
ip address 10.0.20.1 255.255.255.0
#
interface Vlanif30
ip address 10.0.24.2 255.255.255.0
#
interface Vlanif40
ip address 10.0.22.2 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 20
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 30
#
interface GigabitEthernet0/0/4
port link-type access
port default vlan 40
LSW3:
sysname Sw3
#
undo info-center enable
#
vlan batch 10 20 30 40
#
interface Vlanif10
ip address 10.0.11.2 255.255.255.0
#
interface Vlanif20
ip address 10.0.21.1 255.255.255.0
#
interface Vlanif30
ip address 10.0.25.2 255.255.255.0
#
interface Vlanif40
ip address 10.0.23.2 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 20
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 30
#
interface GigabitEthernet0/0/4
port link-type access
port default vlan 40
FW1:
sysname Fw1
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.0.12.1 255.255.255.0
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.0.24.1 255.255.255.0
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.0.22.1 255.255.255.0
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/2
FW2:
sysname Fw2
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.0.12.2 255.255.255.0
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.0.25.1 255.255.255.0
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 10.0.23.1 255.255.255.0
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/2
2.在AR1-2设备上部署VRRP备份组
AR1:
interface GigabitEthernet0/0/0
vrrp vrid 1 virtual-ip 10.0.0.254
vrrp vrid 1 priority 120
vrrp vrid 1 preempt-mode timer delay 10
AR2:
interface GigabitEthernet0/0/0
vrrp vrid 1 virtual-ip 10.0.0.254
3.部署OSPF,Trust区域(内网区域)为OSPF10,UNtrust区域(外网区域)为OSPF20并在FW设备上双向引入
AR1:
ospf 10
area 0.0.0.0
network 10.0.0.0 0.0.0.255
network 10.0.10.0 0.0.0.255
AR2:
ospf 10
area 0.0.0.0
network 10.0.0.0 0.0.0.255
network 10.0.11.0 0.0.0.255
AR3:
ospf 20
area 0.0.0.0
network 10.0.20.0 0.0.0.255
network 10.0.35.0 0.0.0.255
AR4:
ospf 20
area 0.0.0.0
network 10.0.21.0 0.0.0.255
network 10.0.45.0 0.0.0.255
AR5:
ospf 20
area 0.0.0.0
network 5.5.5.0 0.0.0.255
network 10.0.35.0 0.0.0.255
network 10.0.45.0 0.0.0.255
LSW2:
ospf 10
area 0.0.0.0
network 10.0.10.0 0.0.0.255
network 10.0.24.0 0.0.0.255
#
ospf 20
area 0.0.0.0
network 10.0.20.0 0.0.0.255
network 10.0.22.0 0.0.0.255
LSW3:
ospf 10
area 0.0.0.0
network 10.0.11.0 0.0.0.255
network 10.0.25.0 0.0.0.255
#
ospf 20
area 0.0.0.0
network 10.0.23.0 0.0.0.255
network 10.0.21.0 0.0.0.255
FW1:
ospf 10
import-route ospf 20
area 0.0.0.0
network 10.0.24.0 0.0.0.255
#
ospf 20
import-route ospf 10
area 0.0.0.0
network 10.0.22.0 0.0.0.255
FW2:
ospf 10
import-route ospf 20
area 0.0.0.0
network 10.0.25.0 0.0.0.255
#
ospf 20
import-route ospf 10
area 0.0.0.0
network 10.0.23.0 0.0.0.255
4.防火墙上开启HRP协议,配置心跳接口,追踪业务端口,并指定FW2设备为备份设备
FW1:
hrp enable
hrp interface GigabitEthernet1/0/0 remote 10.0.12.2
hrp track interface GigabitEthernet1/0/1
hrp track interface GigabitEthernet1/0/2
FW2:
hrp enable
hrp standby-device //指定当前设备为备份设备
hrp interface GigabitEthernet1/0/0 remote 10.0.12.1
hrp track interface GigabitEthernet1/0/1
hrp track interface GigabitEthernet1/0/2
5.在两个核心交换机(LSW2-3)上配置策略路由,调整来回流量路径使其经过防火墙
LSW2:
acl number 2000
rule 10 permit source 10.0.0.0 0.0.0.255
//创建基本ACL用来筛选需要重定向的内网流量
#
interface GigabitEthernet0/0/1
traffic-redirect inbound acl 2000 ip-nexthop 10.0.24.1
//调用刚才创建的ACL,使用Traffic-redirect工具进行流量重定向
#
acl number 2001
rule 10 permit source 5.5.5.0 0.0.0.255
//创建基本ACL用来筛选需要重定向的外网流量
#
interface GigabitEthernet0/0/2
traffic-redirect inbound acl 2001 ip-nexthop 10.0.22.1
//调用刚才创建的ACL,使用Traffic-redirect工具进行流量重定向
注:流量重定向也可使用Traffic-Policy工具完成
LSW3:
acl number 2000
rule 5 permit source 10.0.0.0 0.0.0.255
#
acl number 2001
rule 5 permit source 5.5.5.0 0.0.0.255
#
interface GigabitEthernet0/0/1
traffic-redirect inbound acl 2000 ip-nexthop 10.0.25.1
#
interface GigabitEthernet0/0/2
traffic-redirect inbound acl 2001 ip-nexthop 10.0.23.1
6.主设备(FW1)上根据业务需求配置安全策略
FW1:
security-policy
rule name t2u
source-zone trust
destination-zone untrust
source-address 10.0.0.0 mask 255.255.255.0
destination-address 5.5.5.5 mask 255.255.255.255
action permit
7.为实现主备链路的及时切换,需要创建BFD会话(R1<–>FW1,FW1<–>R5)
R1:
bfd
#
bfd 1 bind peer-ip 10.0.22.1 source-ip 10.0.10.1 //指向FW1设备的上游接口的BFD会话
discriminator local 10
discriminator remote 22
commit
FW1:
bfd
#
bfd 1 bind peer-ip 10.0.10.1 source-ip 10.0.22.1 //回指R1设备的BFD会话
discriminator local 22
discriminator remote 10
commit
bfd 2 bind peer-ip 10.0.35.5 source-ip 10.0.22.1 //指向R5设备的BFD会话
discriminator local 20
discriminator remote 35
commit
R5:
bfd
#
bfd 2 bind peer-ip 10.0.22.1 source-ip 10.0.35.5 //回指FW1设备的BFD会话
discriminator local 35
discriminator remote 20
commit
8.在连接终端设备的VRRP备份组以及防火墙的HRP协议上都联动已创建好的BFD会话实现主备角色的一致切换
AR1:
interface GigabitEthernet0/0/0
vrrp vrid 1 track bfd-session 10 reduced 30 //VRRP备份组联动BFD会话,惩罚值为30
FW1:
hrp track bfd-session 20 //探测FW1到AR5的区间链路
hrp track bfd-session 22 //探测FW1到AR1的区间链路
结果验证
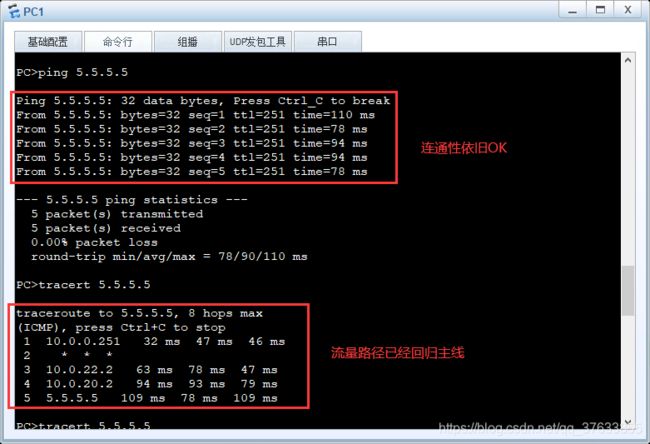
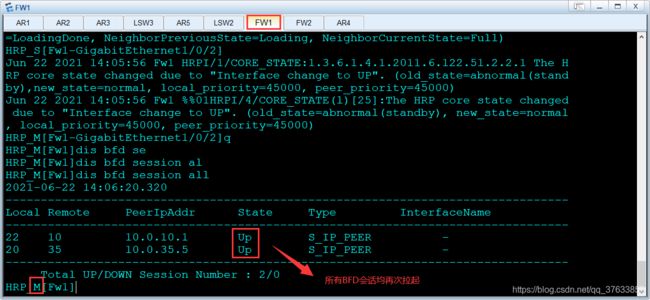
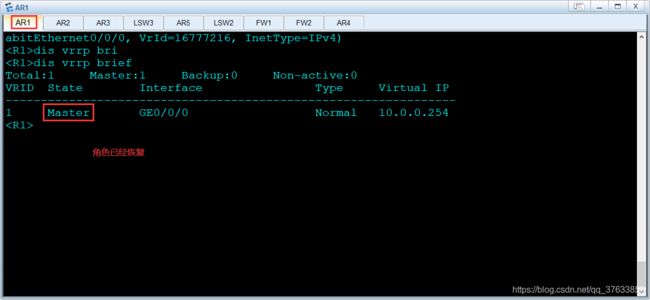
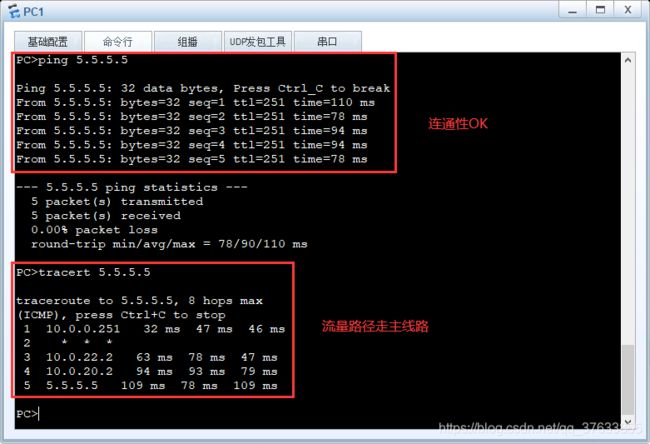
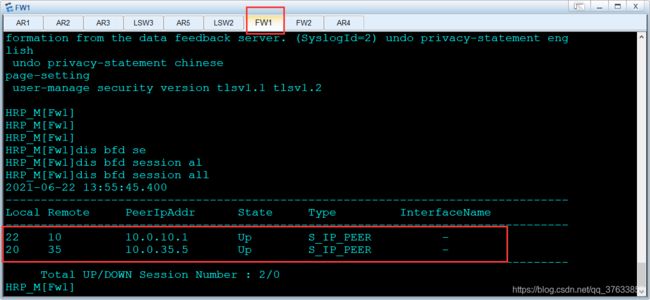
1.无故障情况下
连通性&流量路径:
BFD会话状态(以中间设备FW1为参考):
VRRP备份组主备角色:
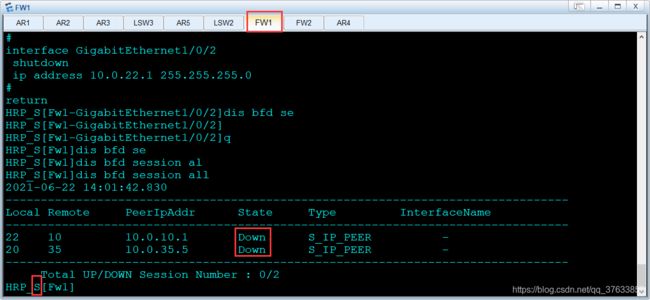
2.故障模拟,在BFD会话覆盖的链路上找端口down掉(本案例选择FW1设备端口)
FW1设备关闭主链路对应端口:
interface GigabitEthernet1/0/2
shutdown
连通性&流量路径:
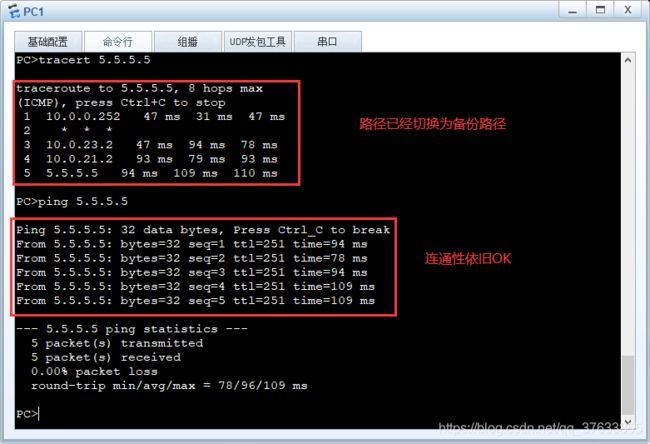
BFD会话状态(以中间设备FW1为参考):
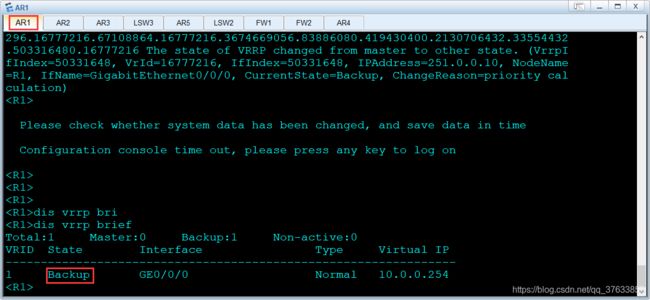
VRRP备份组主备角色:
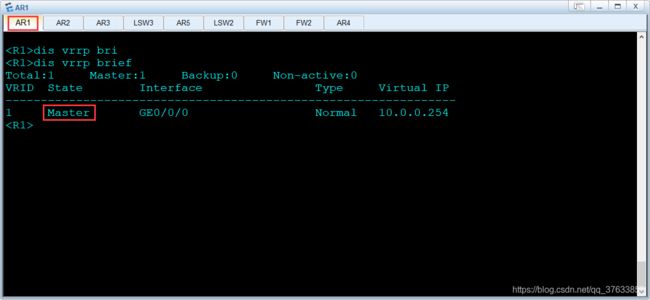
3.故障恢复
FW1:
interface GigabitEthernet1/0/2
undo shutdown