陇原战役 Misc题目WriteUP WP CTF竞赛
soEasyCheckin
base32,但有问题,倒数出现了0$,0–>O,$—>S,得到一串hex。 结果hex那里又有问题,具体是出在83¥6988ee这里 根据规律,每6个字节的第1个字节为e,然后把¥替换成e 得到社会主义核心价值观编码,但是还是有个地方是错误的,中间有一段为:和谐斃明平 然后把他那个斃随便改一下,我改的“富强” 解码得到的SET{Qi2Xin1Xie2Li4-Long3Yuan0Zhan4Yi4} 根据拼音,可以知道是Yuan2 所以最终flag为:
SET{Qi2Xin1Xie2Li4-Long3Yuan2Zhan4Yi4}
打败病毒
下载压缩包,解压后是HMCL和Minecraftn
查看MC核心,发现被修改过
查看附带的文件,只有一个存档
猜测flag在存档或者核心里,创建帐户,启动游戏,进入存档
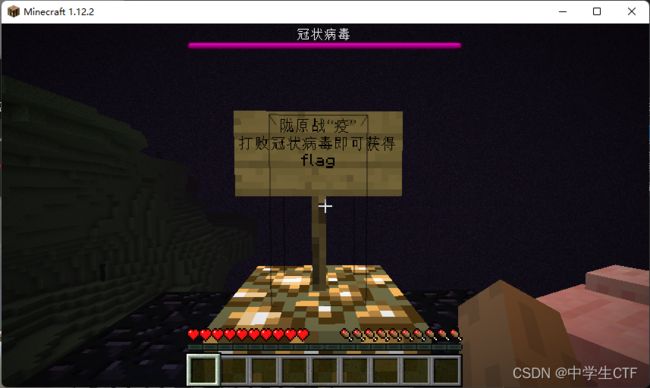
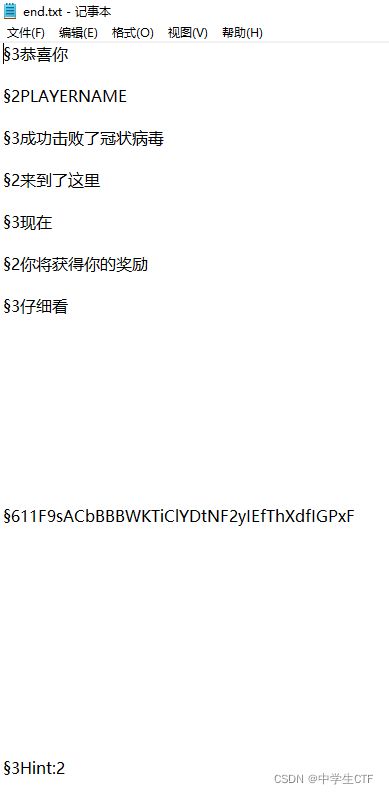
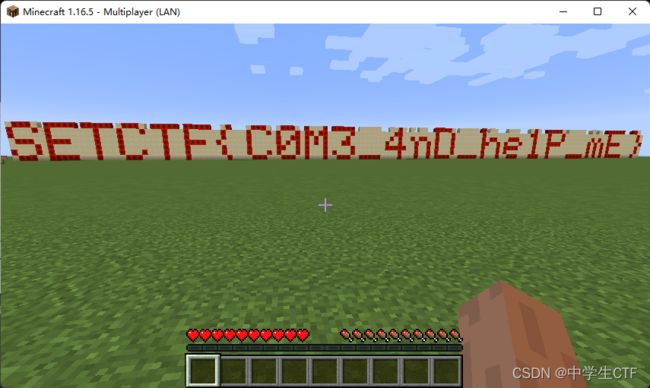
可以看到冠状病毒在游戏里是末影龙,flag在终末之诗
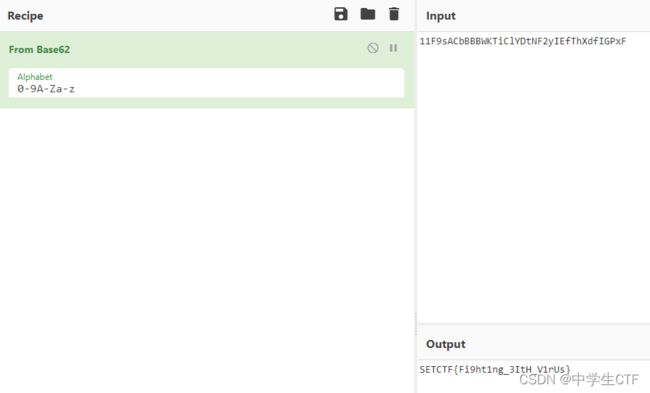
类似Base64串和提示可以猜测为Base62,放到CyberChef解码
SOS
下载压缩包,解压后是HMCL和Minecraft
查看MC核心,没有被修改
查看附带的文件,有一个存档和一个资源包
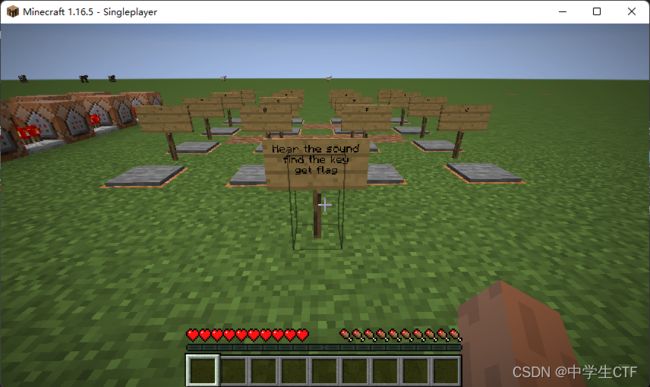
猜测flag在资源包或者存档里,创建帐户,启动游戏,进入存档
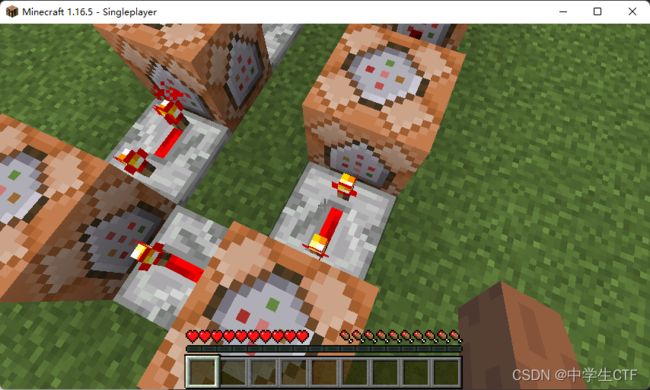
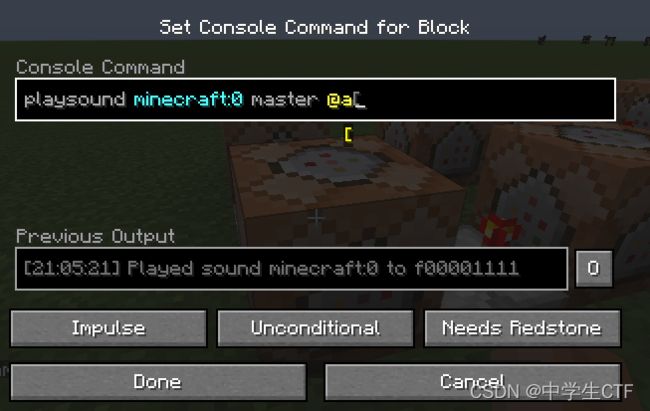
听到有拨号音,旁边红石电路在工作,调整速度
中继器调到3后可以听到清晰的拨号音,顺序查看命令方块可知为0-9,在资源包中找到0-9
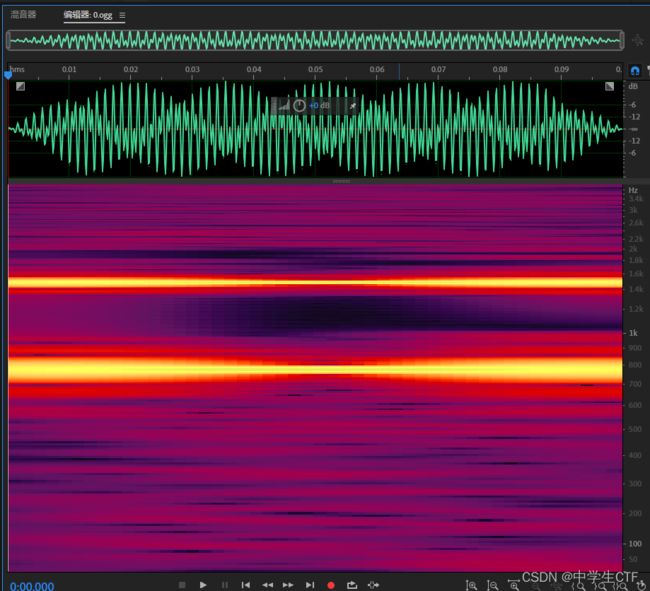
使用Audition查看,得到DTMF音对应的字符
0-9解出来6830AB1C75,踩对应的字符得到flag
附赠原版DTMF资源包文件分享
EasySteg
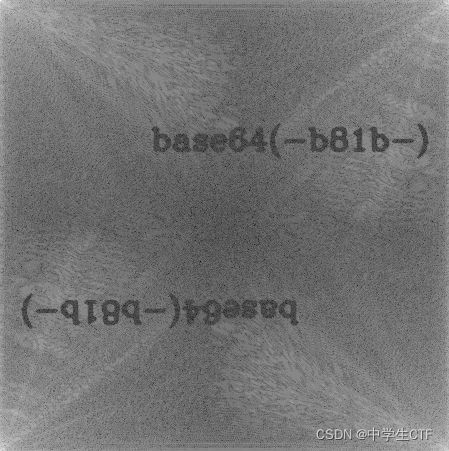
jk.png 盲水印提出:-b81b-
base64之后是LWI4MWIt
注释有东西
tab和空格转10
分出一张图片
oursecret解密,密码是LWI4MWIt
得到
n9S2B3I6U6L1O3R2F3Y1G2H3v9N2M1Z1D6T1h18o16u17b9s7r4g8f10a14m2i20p2e14w7q2y8P1J2E2C1V1A1j4k5x5t3c6824956{13217d9748365402511221058710}1l4Q1W1z1
结合上面的01二进制,猜测是哈夫曼树
#!/usr/bin/env python
# -*- coding: utf-8 -*-
# 统计字符出现频率,生成映射表
def count_frequency(text):
chars = []
ret = []
for char in text:
if char in chars:
continue
else:
chars.append(char)
ret.append((char, text.count(char)))
return ret
# 节点类
class Node:
def __init__(self, frequency):
self.left = None
self.right = None
self.father = None
self.frequency = frequency
def is_left(self):
return self.father.left == self
# 创建叶子节点
def create_nodes(frequency_list):
return [Node(frequency) for frequency in frequency_list]
# 创建Huffman树
def create_huffman_tree(nodes):
queue = nodes[:]
while len(queue) > 1:
queue.sort(key=lambda item: item.frequency)
node_left = queue.pop(0)
node_right = queue.pop(0)
node_father = Node(node_left.frequency + node_right.frequency)
node_father.left = node_left
node_father.right = node_right
node_left.father = node_father
node_right.father = node_father
queue.append(node_father)
queue[0].father = None
return queue[0]
# Huffman编码
def huffman_encoding(nodes, root):
huffman_code = [''] * len(nodes)
for i in range(len(nodes)):
node = nodes[i]
while node != root:
if node.is_left():
huffman_code[i] = '0' + huffman_code[i]
else:
huffman_code[i] = '1' + huffman_code[i]
node = node.father
return huffman_code
# 编码整个字符串
def encode_str(text, char_frequency, codes):
ret = ''
for char in text:
i = 0
for item in char_frequency:
if char == item[0]:
ret += codes[i]
i += 1
return ret
# 解码整个字符串
def decode_str(huffman_str, char_frequency, codes):
ret = ''
while huffman_str != '':
i = 0
for item in codes:
if item in huffman_str and huffman_str.index(item) == 0:
ret += char_frequency[i][0]
huffman_str = huffman_str[len(item):]
i += 1
return ret
if __name__ == '__main__':
char_frequency=[('n', 9), ('S', 2), ('B', 3), ('I', 6), ('U', 6), ('L', 1), ('O', 3), ('R', 2), ('F', 3), ('Y', 1), ('G', 2), ('H', 3), ('v', 9), ('N', 2), ('M', 1), ('Z', 1), ('D', 6), ('T', 1), ('h', 18), ('o', 16), ('u', 17), ('b', 9), ('s', 7), ('r', 4), ('g', 8), ('f', 10), ('a', 14), ('m', 2), ('i', 20), ('p', 2), ('e', 14), ('w', 7), ('q', 2), ('y', 8), ('P', 1), ('J', 2), ('E', 2), ('C', 1), ('V', 1), ('A', 1), ('j', 4), ('k', 5), ('x', 5), ('t', 3), ('c', 6), ('8', 24), ('9', 56), ('{', 1), ('3', 217), ('d', 97), ('4', 83), ('6', 54), ('0', 25), ('1', 12), ('2', 10), ('5', 8), ('7', 10), ('}', 1), ('l', 4), ('Q', 1), ('W', 1), ('z', 1)]
nodes = create_nodes([item[1] for item in char_frequency])
root = create_huffman_tree(nodes)
codes = huffman_encoding(nodes, root)
huffman_str = '1110111111000100001111000011010001101111100110100011110111100010100111110111001101111100011000111111111101011100011111100111000011010001111010011011111001110111100010000111001110011110111000111111100111011111011011101011110111110101101101101000110101011101011111111011110111101101110101111010011010110100011100100011010101111010111110110110111100011010111010111110110110111001001011011110100111010111111010111111011110111101001111010111110111101011100100111100101011011101110111111001010110100100110111110011111001101000111110111001011001110000111000011110000110111110011000011100001101100110100011100001111110011110000110110011010001110011101100001110110001001111111110010110011010001111011110110010011011111000001111100010010001001111101110110111111101101001001001011011101111101101101111001101001011011111100111110110110110110111110111010110111011110011111011011011010000110111111001111110111100111010111110011010011011110101001101110111100110110111101001101011101011111001101111011101101010111010111111001111110111010110110110101001101011111101001101000111010010111000010011001110111110111101101111101101110111010110100101101101101011010111111101111001110111111110011010110100101101111011011101100111001000001111001100100101011000000111100101011001000101100100000011001011001001000001111001100100101011000000111100101011001011111111001010001010001010010000011110011001001010110000001111001010110010001011001010001010000111100100000111100110010010101100000011110010101100101010010101100101010010000011110011001001010110000001111001010110010011001001010110000011011111001000001111001100100101011000000111100101000101000110111110010000001100101010010000011110011001001010010101100000011110010101100100010001001000011111110001010010000011110011001001010110000001111001010110010111111110010100010110001000100100000111100110010010101100000011110010100010100011011111001000000110010101001000001111001100100101011000000111100101011001001100100101011000001101111100100000111100110010010101100000011110010101100100010110010000001100101100100100000111100110010010101100000011110010100010100010100101011000001101111100100000111100110010010101100000011110010100101011001000101100100000011001011001001000001111001100100101011000000111100101011001011111111001010001010001010010000011110011001001010110000001111001010110010001000100100001111111000101001000001111001100100101011000000111100101011001000101100100000011001011001001000001111001100100101011000000111100101011001010100100000011001011111111001000001111001100100101011000000111100101011001000101100100000011001011001001000001111001100100101011000000111100101011001000100010010100100001111111000101001000001111001100100101011000000111100101011001010100100000011001011111111001000001111001100100101011000000111100101000101000101001010110000011011111001000001111001100100101011000000111100101000101000110111110010000001100000011110010000011110011001001010110000001111001010001010000001001010001010000111111011010011110011101011111011100001011010110101111010001111100110111110101111110110101010011101111101100100000101111011010111101101101110011001110001100011111001110010000010111100010111101111111101101101110000111010000101111110001100000110001110010100100000110000101110000100010110111100000101110011111110000111011010111101001101001101111101000100101111101101011111100111111001110001100001000011011111000001111100010011001110111101111111011111001000111000011101101110000111011011110011101111111011011010110100011111000100101111111011100000100000101110010111100011010110100011111101111001110101111010111011011100100110011101111100111101111100000001001001101001101111111101101011110111011110011101001101111010100110111011101011110011100000011010010111111000100110011101111101011110111110111'
origin_str = decode_str(huffman_str, char_frequency, codes)
print('Decode result:',origin_str)得到:
The text to encode:nSBIULORFYGHvNMIOUZSDTNhnoubuosrgfbouvasmruiohauiopewgvfbwuivpqynqwUPIFJDDBUEDUIDHBUIDCVHJIOAejikxneiwkyiohwehiooiuyhiosehfhuiaetyhovauieyrghfuotgvac89xcboiyuweagihniaweo{3d46303d39463d39383d41393d46303d39463d39323d38433d46303d39463d39383d38463d46303d39463d39333d39333d46303d39463d39303d39453d46303d39463d38453d41333d46303d3d39463d39373d42433d46303d39463d39323d38373d46303d39463d38453d41333d46303d39463d39303d39453d46303d39463d39383d41393d46303d39463d38433d39453d46303d39463d3d39383d41393d46303d39463d39323d38433d46303d39463d39373d42433d46303d39463d39383d41393d46303d39463d39333d41323d46303d39463d39383d41393d46303d39463d39373d3d42433d46303d39463d39333d41323d46303d39463d38433d39453d46303d39463d38453d41463d46303d39463d38443d3846}huilagsieufrcb78QWEGF678Rniolsdf149687189735489246avaeukighf6497ejixcnbmlolohnbasik2647893hasfhuvzxchbjkaefgyhuetyuhjadfxcvbn
16进制转字符串:
=F0=9F=98=A9=F0=9F=92=8C=F0=9F=98=8F=F0=9F=93=93=F0=9F=90=9E=F0=9F=8E=A3=F0==9F=97=BC=F0=9F=92=87=F0=9F=8E=A3=F0=9F=90=9E=F0=9F=98=A9=F0=9F=8C=9E=F0=9F==98=A9=F0=9F=92=8C=F0=9F=97=BC=F0=9F=98=A9=F0=9F=93=A2=F0=9F=98=A9=F0=9F=97==BC=F0=9F=93=A2=F0=9F=8C=9E=F0=9F=8E=AF=F0=9F=8D=8F
是Quoted-printable编码
解码得到:
尝试一番之后,可用emoji-cracker解决
https://github.com/pavelvodrazka/ctf-writeups/tree/d957cab439f796304bdb005e45b333cd83203c04/hackyeaster2018/challenges/egg17/files/cracker 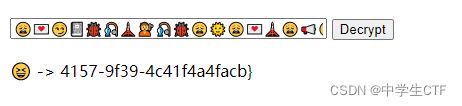
原图像是分数小波变换处理后的,算法很简单,简单处理一下
import cv2
import numpy as np
from pywt import dwt2, idwt2
D = cv2.imread('text_d.png',0)
zeros = np.ones(shape = H.shape)
rimg = idwt2((zeros,(D,D,D)), 'haar')
cv2.imwrite("output.png",np.uint8(rimg))
得到flag{156cca8e
flag{156cca8e-b81b-4157-9f39-4c41f4a4facb}
checkin
part 1
根据题目描述,关注到截图软件 snipaste,从其历史截图的缓存中发现 veracrypt 的密码:
part 2
将桌面上的 flag.vhd 挂载为本地磁盘后,解密得到 task.py cip.png 以及 flag.zip ,查看 flag.zip 注释可以发现提示 who is invited? ,那么我们解密 cip.png 即可得到邀请函,exp如下:
# from PIL import Image
# import sys
#
# # if len(sys.argv) != 3:
# # print("Usage: %s [infile] [outfile]" % sys.argv[0])
# # sys.exit(1)
#
# image = Image.open("cip.png").convert("F")
# width, height = image.size
# result = Image.new("F", (width, height))
#
# ROUNDS = 32
#
# f = open('tuples.csv', 'w')
# for i in range(width):
# for j in range(height):
# value = 0
# di, dj = 1337, 42
# for k in range(ROUNDS):
# di, dj = (di * di + dj) % width, (dj * dj + di) % height
# f.write('%d,%d\n' % (di,dj))
# value += image.getpixel(((i + di) % width, (j + dj + (i + di)//width) % height))
# result.putpixel((i, j), value / ROUNDS)
#
# f.close()
# result = result.convert("RGB")
# result.save("cip2.png")
from PIL import Image
image = Image.open("cip.png").convert("F")
width, height = image.size
result = Image.new("F", (width, height))
ROUNDS = 32
lines = iter(open('tuples.csv', 'r').readlines()[::-1])
for i in range(width):
for j in range(height):
value = 0
for k in range(ROUNDS):
line = next(lines)
di = int(line.split(",")[0])
dj = int(line.split(",")[1])
value += image.getpixel(((i - di) % width, (j - dj + (i - di)//width) % height))
result.putpixel((i, j), value / ROUNDS)
result = result.convert("RGB")
result.show()
result.save("out.png")即可得到邀请函中的名字是 every ctfer
part 3
flag.data 是 /dev/input/event* 中的键盘记录,这一点已经在比赛当中的hint给出,解析即可得到flag,exp如下:
#!/usr/bin/python
import struct
import time
import sys
infile_path = "./flag.data"
FORMAT = 'llHHI'
EVENT_SIZE = struct.calcsize(FORMAT)
#open file in binary mode
in_file = open(infile_path, "rb")
event = in_file.read(EVENT_SIZE)
keys = {
"0" : "[NULL]",
"1" : "[ESC]",
"2" : "1",
"3" : "2",
"4" : "3",
"5" : "4",
"6" : "5",
"7" : "6",
"8" : "7",
"9" : "8",
"10" : "9",
"11" : "0",
"12" : "-",
"13" : "=",
"14" : "[BACKSPACE]",
"15" : "[TAB]",
"16" : "q",
"17" : "w",
"18" : "e",
"19" : "r",
"20" : "t",
"21" : "y",
"22" : "u",
"23" : "i",
"24" : "o",
"25" : "p",
"26" : "[",
"27" : "]",
"28" : "[ENTER]",
"29" : "[LEFT_CTRL]",
"30" : "a",
"31" : "s",
"32" : "d",
"33" : "f",
"34" : "g",
"35" : "h",
"36" : "j",
"37" : "k",
"38" : "l",
"39" : ";",
"40" : "'",
"41" : "`",
"42" : "[LEFT_SHIFT]",
"43" : "\\",
"44" : "z",
"45" : "x",
"46" : "c",
"47" : "v",
"48" : "b",
"49" : "n",
"50" : "m",
"51" : ",",
"52" : ".",
"53" : "/",
"54" : "[RIGHT_SHIFT]",
"55" : "[GRAY*]",
"56" : "[LEFT_ALT]",
"57" : "[SPACE]",
"58" : "[CAPS]",
"59" : "[F1]",
"60" : "[F2]",
"61" : "[F3]",
"62" : "[F4]",
"63" : "[F5]",
"64" : "[F6]",
"65" : "[F7]",
"66" : "[F8]",
"67" : "[F9]",
"68" : "[F10]",
"69" : "[NUM_LOCK]",
"70" : "[SCROLL_LOCK]",
"71" : "[PAD_7]",
"72" : "[PAD_8]",
"73" : "[PAD_9]",
"74" : "[GRAY_MINUS]",
"75" : "[PAD_4]",
"76" : "[PAD_5]",
"77" : "[PAD_6]",
"78" : "[GRAY_PLUS]",
"79" : "[PAD_3]",
"80" : "[PAD_2]",
"81" : "[PAD_1]",
"82" : "[PAD_0/INS]",
"83" : "[PAD_./DEL]",
"84" : "[PRTSCR/SYSRQ]",
"87" : "[F11]",
"88" : "[F12]",
"90" : "PAUSE/BREAK",
"91" : "[INSERT]",
"92" : "[HOME]",
"93" : "[PG_UP]",
"94" : "[GRAY/]",
"95" : "[DELETE]",
"96" : "[END]",
"97" : "[PG_DN]",
"98" : "[RIGHT_ALT]",
"99" : "[RIGHT_CTRL]",
"100" : "[UP_ARROW]",
"101" : "[LEFT_ARROW]",
"102" : "[DOWN_ARROW]",
"103" : "[RIGHT_ARROW]",
"104" : "[GRAY_ENTER]",
"105" : "[MOUSE]",
"183" : "[PRTSC]"
}
count = 0
while event:
count += 1
(tv_sec, tv_usec, type, code, value) = struct.unpack(FORMAT, event)
if type != 0 or code != 0 or value != 0:
# print("Event type %u, code %u, value %u at %d.%d" % \
# (type, code, value, tv_sec, tv_usec))
if count == 3:
print(count, end="")
print(" ", end="")
print(keys[str(code)], end="")
else:
# Events with code, type and value == 0 are "separator" events
count = 0
print()
event = in_file.read(EVENT_SIZE)
in_file.close()SET{Wow_Y0u_c4n_r3A11y_Forensic}