中小型网络模型(ensp模拟)
拓扑图
目标概括
PC能够获取动态IP,能够ping通cloud的IP
VLAN间正常通讯,三台交换机互相ping通,内网能访问防火墙
本机模拟外网,通过SSH访问防火墙三个指定端口,管理三台交换机
网络结构
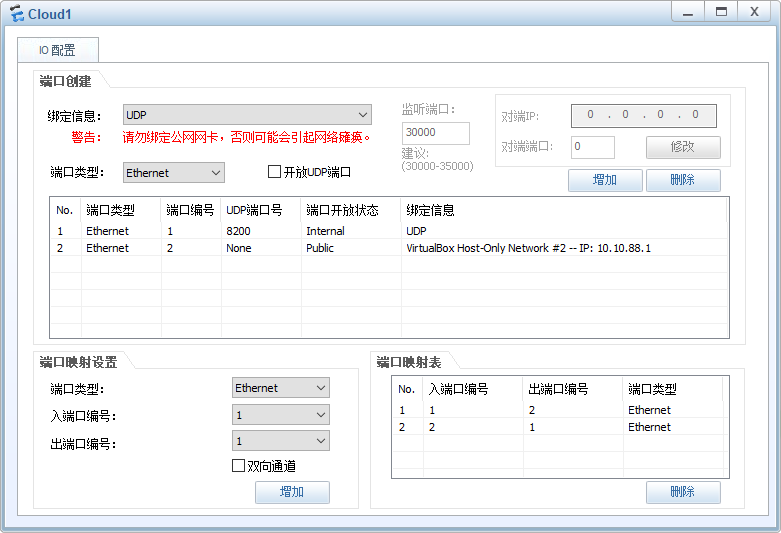
CLOUD模拟外网
防火墙及右边所有设备模拟内网
VLAN10连接防火墙
VLAN20网络设备管理
VLAN30和40为终端接入
设备配置清单
设备 |
接口 |
规则 |
防火墙 |
g1/0/0 g1/0/1 |
IP:10.10.88.57/24 IP:10.0.1.254/25 |
核心交换机01 |
g0/0/1 g0/0/2 g0/0/3 Vlan10 Vlan20 Vlan30 Vlan40 |
Vlan10 串口 串口 IP:10.0.1.253/25 IP:10.0.2.1/24 IP:10.0.3.1/24 IP:10.0.4.1/24 |
接入交换机02 |
e0/0/1 e0/0/2-11 e0/0/12-22 Vlan20 Vlan30 Vlan40 |
串口 Vlan30 Vlan40 IP:10.0.2.2/24 无需配置 无需配置 |
接入交换机03 |
e0/0/1 e0/0/2-11 e0/0/12-22 Vlan20 Vlan30 Vlan40 |
串口 Vlan30 Vlan40 IP:10.0.2.3/24 无需配置 无需配置 |
PC |
网卡 |
DHCP |
配置过程
网络配置
接口
CLOUD
防火墙
#配置g1/0/0和g1/0/1接口
#允许https、ping和ssh访问
[FW]int g1/0/0
[FW-GigabitEthernet1/0/0]ip add 10.10.88.57 24
[FW-GigabitEthernet1/0/0]service-manage https permit
[FW-GigabitEthernet1/0/0]service-manage ping permit
[FW-GigabitEthernet1/0/0]service-manage ssh permit
[FW-GigabitEthernet1/0/0]q
[FW]int g1/0/1
[FW-GigabitEthernet1/0/1]ip add 10.0.1.254 24
[FW-GigabitEthernet1/0/1]service-manage https permit
[FW-GigabitEthernet1/0/1]service-manage ping permit
[FW-GigabitEthernet1/0/1]service-manage ssh permit
[FW-GigabitEthernet1/0/1]q
#安全域配置
#将g1/0/1加入trust区域,g1/0/0加入dmz区域
[FW]firewall zone trust
[FW-zone-trust]add int g1/0/1
[FW-zone-trust]q
[FW]firewall zone dmz
[FW-zone-dmz]add int g1/0/0
[FW-zone-dmz]q核心交换机(01)
#创建配置VLAN
[HX_01]vlan batch 10 20 30 40
#设置该vlan地址和网段
[HX_01]int vlan10
[HX_01-Vlanif10]ip add 10.0.1.253 25
[HX_01-Vlanif10]q
[HX_01]int vlan20
[HX_01-Vlanif20]ip add 10.0.2.1 24
[HX_01-Vlanif20]q
[HX_01]int vlan30
[HX_01-Vlanif30]ip add 10.0.3.1 24
#启用DHCP匹配↓
[HX_01-Vlanif30]dhcp select global
[HX_01-Vlanif30]q
[HX_01]int vlan40
[HX_01-Vlanif40]ip add 10.0.4.1 24
#启用DHCP匹配↓
[HX_01-Vlanif40]dhcp select global
[HX_01-Vlanif40]q
#划分VLAN至指定端口
[HX_01]int g0/0/1
[HX_01-GigabitEthernet0/0/1]port link-type access
[HX_01-GigabitEthernet0/0/1]port default vlan 10
#将g0/0/2切换至串口模式,允许vlan20,30,40通过该端口
[HX_01-GigabitEthernet0/0/1]int g0/0/2
[HX_01-GigabitEthernet0/0/2]port link-type trunk
[HX_01-GigabitEthernet0/0/2]port trunk allow-pass vlan 20 30 40
#将g0/0/3切换至串口模式,允许vlan20,30,40通过该端口
[HX_01-GigabitEthernet0/0/2]int g0/0/3
[HX_01-GigabitEthernet0/0/3]port link-type trunk
[HX_01-GigabitEthernet0/0/3]port trunk allow-pass vlan 20 30 40
[HX_01-GigabitEthernet0/0/3]q
#创建DHCP地址池vlan30,指定网关,网段,DNS↓
[HX_01]ip pool vlan30
[HX_01-ip-pool-vlan30]gateway-list 10.0.3.1
[HX_01-ip-pool-vlan30]network 10.0.3.0 mask 255.255.255.0
[HX_01-ip-pool-vlan30]dns-list 10.0.3.1
[HX_01-ip-pool-vlan30]q
#创建DHCP地址池vlan40,指定网关,网段,DNS↓
[HX_01]ip pool vlan40
[HX_01-ip-pool-vlan40]gateway-list 10.0.4.1
[HX_01-ip-pool-vlan40]network 10.0.4.0 mask 255.255.255.0
[HX_01-ip-pool-vlan40]dns-list 10.0.4.1
[HX_01-ip-pool-vlan40]q
#启用DHCP服务,配置相关规则
[HX_01]dhcp enable
[HX_01]dhcp server ping packet 3
[HX_01]dhcp server ping timeout 100接入交换机(02)
[JR_02]vlan batch 20 30 40
#设置本机管理地址
[JR_02]int vlan20
[JR_02-Vlanif20]ip add 10.0.2.2 24
[JR_02-Vlanif20]q
#设置为串口模式,允许vlan20,30,40通信
[JR_02]int Ethernet0/0/1
[JR_02-Ethernet0/0/1]port link-type trunk
[JR_02-Ethernet0/0/1]port trunk allow-pass vlan 20 30 40
[JR_02-Ethernet0/0/1]q
#创建端口组,将指定范围端口号加入端口组,用以批量设置
[JR_02]port-group 1
[JR_02-port-group-1]group-member Ethernet0/0/2 to Ethernet0/0/11
[JR_02-port-group-1]port link-type access
[JR_02-Ethernet0/0/2]port link-type access
[JR_02-Ethernet0/0/3]port link-type access
[JR_02-Ethernet0/0/4]port link-type access
[JR_02-Ethernet0/0/5]port link-type access
[JR_02-Ethernet0/0/6]port link-type access
[JR_02-Ethernet0/0/7]port link-type access
[JR_02-Ethernet0/0/8]port link-type access
[JR_02-Ethernet0/0/9]port link-type access
[JR_02-Ethernet0/0/10]port link-type access
[JR_02-Ethernet0/0/11]port link-type access
[JR_02-port-group-1]port default vlan 30
[JR_02-Ethernet0/0/2]port default vlan 30
[JR_02-Ethernet0/0/3]port default vlan 30
[JR_02-Ethernet0/0/4]port default vlan 30
[JR_02-Ethernet0/0/5]port default vlan 30
[JR_02-Ethernet0/0/6]port default vlan 30
[JR_02-Ethernet0/0/7]port default vlan 30
[JR_02-Ethernet0/0/8]port default vlan 30
[JR_02-Ethernet0/0/9]port default vlan 30
[JR_02-Ethernet0/0/10]port default vlan 30
[JR_02-Ethernet0/0/11]port default vlan 30
[JR_02-port-group-1]q
#创建端口组,将指定范围端口号加入端口组,用以批量设置
[JR_02]port-group 2
[JR_02-port-group-2]group-member Ethernet0/0/12 to Ethernet0/0/22
[JR_02-port-group-2]port link-type access
[JR_02-Ethernet0/0/12]port link-type access
[JR_02-Ethernet0/0/13]port link-type access
[JR_02-Ethernet0/0/14]port link-type access
[JR_02-Ethernet0/0/15]port link-type access
[JR_02-Ethernet0/0/16]port link-type access
[JR_02-Ethernet0/0/17]port link-type access
[JR_02-Ethernet0/0/18]port link-type access
[JR_02-Ethernet0/0/19]port link-type access
[JR_02-Ethernet0/0/20]port link-type access
[JR_02-Ethernet0/0/21]port link-type access
[JR_02-Ethernet0/0/22]port link-type access
[JR_02-port-group-2]port default vlan 40
[JR_02-Ethernet0/0/12]port default vlan 40
[JR_02-Ethernet0/0/13]port default vlan 40
[JR_02-Ethernet0/0/14]port default vlan 40
[JR_02-Ethernet0/0/15]port default vlan 40
[JR_02-Ethernet0/0/16]port default vlan 40
[JR_02-Ethernet0/0/17]port default vlan 40
[JR_02-Ethernet0/0/18]port default vlan 40
[JR_02-Ethernet0/0/19]port default vlan 40
[JR_02-Ethernet0/0/20]port default vlan 40
[JR_02-Ethernet0/0/21]port default vlan 40
[JR_02-Ethernet0/0/22]port default vlan 40
[JR_02-port-group-2]q接入交换机(03)
[JR_03]vlan batch 20 30 40
#设置本机管理地址
[JR_03]int vlan20
[JR_03-Vlanif20]ip add 10.0.2.3 24
[JR_03-Vlanif20]q
#设置为串口模式,允许vlan20,30,40通信
[JR_03]int Ethernet0/0/1
[JR_03-Ethernet0/0/1]port link-type trunk
[JR_03-Ethernet0/0/1]port trunk allow-pass vlan 20 30 40
[JR_03-Ethernet0/0/1]q
#创建端口组,将指定范围端口号加入端口组,用以批量设置
[JR_03]port-group 1
[JR_03-port-group-1]group-member Ethernet0/0/2 to Ethernet0/0/11
[JR_03-port-group-1]port link-type access
[JR_03-Ethernet0/0/2]port link-type access
[JR_03-Ethernet0/0/3]port link-type access
[JR_03-Ethernet0/0/4]port link-type access
[JR_03-Ethernet0/0/5]port link-type access
[JR_03-Ethernet0/0/6]port link-type access
[JR_03-Ethernet0/0/7]port link-type access
[JR_03-Ethernet0/0/8]port link-type access
[JR_03-Ethernet0/0/9]port link-type access
[JR_03-Ethernet0/0/10]port link-type access
[JR_03-Ethernet0/0/11]port link-type access
[JR_03-port-group-1]port default vlan 30
[JR_03-Ethernet0/0/2]port default vlan 30
[JR_03-Ethernet0/0/3]port default vlan 30
[JR_03-Ethernet0/0/4]port default vlan 30
[JR_03-Ethernet0/0/5]port default vlan 30
[JR_03-Ethernet0/0/6]port default vlan 30
[JR_03-Ethernet0/0/7]port default vlan 30
[JR_03-Ethernet0/0/8]port default vlan 30
[JR_03-Ethernet0/0/9]port default vlan 30
[JR_03-Ethernet0/0/10]port default vlan 30
[JR_03-Ethernet0/0/11]port default vlan 30
[JR_03-port-group-1]q
#创建端口组,将指定范围端口号加入端口组,用以批量设置
[JR_03]port-group 2
[JR_03-port-group-2]group-member Ethernet0/0/12 to Ethernet0/0/22
[JR_03-port-group-2]port link-type access
[JR_03-Ethernet0/0/12]port link-type access
[JR_03-Ethernet0/0/13]port link-type access
[JR_03-Ethernet0/0/14]port link-type access
[JR_03-Ethernet0/0/15]port link-type access
[JR_03-Ethernet0/0/16]port link-type access
[JR_03-Ethernet0/0/17]port link-type access
[JR_03-Ethernet0/0/18]port link-type access
[JR_03-Ethernet0/0/19]port link-type access
[JR_03-Ethernet0/0/20]port link-type access
[JR_03-Ethernet0/0/21]port link-type access
[JR_03-Ethernet0/0/22]port link-type access
[JR_03-port-group-2]port default vlan 40
[JR_03-Ethernet0/0/12]port default vlan 40
[JR_03-Ethernet0/0/13]port default vlan 40
[JR_03-Ethernet0/0/14]port default vlan 40
[JR_03-Ethernet0/0/15]port default vlan 40
[JR_03-Ethernet0/0/16]port default vlan 40
[JR_03-Ethernet0/0/17]port default vlan 40
[JR_03-Ethernet0/0/18]port default vlan 40
[JR_03-Ethernet0/0/19]port default vlan 40
[JR_03-Ethernet0/0/20]port default vlan 40
[JR_03-Ethernet0/0/21]port default vlan 40
[JR_03-Ethernet0/0/22]port default vlan 40
[JR_03-port-group-2]q路由
#防火墙
# ↓默认路由↓
[FW]ip route-static 0.0.0.0 0 10.10.88.1
[FW]ip route-static 10.0.2.0 24 10.0.1.253
[FW]ip route-static 10.0.3.0 24 10.0.1.253
[FW]ip route-static 10.0.4.0 24 10.0.1.253
# ↑三条回程路由↑
#核心交换机01
[HX_01]ip route-static 0.0.0.0 0 10.0.1.254
#接入交换机02
[JR_02]ip route-static 0.0.0.0 0 10.0.2.1
#接入交换机03
[JR_03]ip route-static 0.0.0.0 0 10.0.2.1策略配置
SSH
核心交换机(01)
#创建本地密钥对
[HX_01]rsa local-key-pair create
The key name will be: HX_01_Host
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
it will take a few minutes.
Input the bits in the modulus[default = 512]:1024
Generating keys...
....................++++++
...................++++++
................++++++++
........++++++++
#线路配置,认证模式aaa,接入模式ssh
[HX_01]user-interface vty 0 4
[HX_01-ui-vty0-4]authentication-mode aaa
[HX_01-ui-vty0-4]protocol inbound ssh
[HX_01-ui-vty0-4]q
#配置aaa,创建用户sxc,密码sun@xiaochuan,优先级3,服务类型ssh
[HX_01]aaa
[HX_01-aaa]local-user sxc password cipher sun@xiaochuan
[HX_01-aaa]local-user sxc privilege level 3
[HX_01-aaa]local-user sxc service-type ssh
[HX_01-aaa]q
#配置sxc用户的认证模式为password,用户服务模式stelnet,即ssh
[HX_01]ssh user sxc authentication-type password
[HX_01]ssh user sxc service-type stelnet
[HX_01]stelnet server enable接入交换机(02)
#创建本地密钥对
[JR_02]rsa local-key-pair create
The key name will be: JR_02_Host
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
it will take a few minutes.
Input the bits in the modulus[default = 512]:1024
Generating keys...
.....................++++++
.++++++
..........................................++++++++
............................++++++++
#线路配置,认证模式aaa,接入模式ssh
[JR_02]user-int vty 0 4
[JR_02-ui-vty0-4]authentication-mode aaa
[JR_02-ui-vty0-4]protocol inbound ssh
[JR_02-ui-vty0-4]q
#配置aaa,创建用户acz,密码AO#changzhang,优先级3,服务类型ssh
[JR_02]aaa
[JR_02-aaa]local-user acz password cipher AO#changzhang
[JR_02-aaa]local-user acz privilege level 3
[JR_02-aaa]local-user acz service-type ssh
[JR_02-aaa]q
#配置acz用户的认证类型为password,用户服务模式stelnet,即ssh
[JR_02]ssh user acz authentication-type password
[JR_02]ssh user acz service-type stelnet
[JR_02]stelnet server enable接入交换机(03)
#创建本地密钥对
[JR_03]rsa local-key-pair create
The key name will be: JR_03_Host
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
it will take a few minutes.
Input the bits in the modulus[default = 512]:1024
Generating keys...
.............................................++++++
..............++++++
.............++++++++
.....++++++++
#线路配置,认证模式aaa,接入模式ssh
[JR_03]user-int vty 0 4
[JR_03-ui-vty0-4]authentication-mode aaa
[JR_03-ui-vty0-4]protocol inbound ssh
[JR_03-ui-vty0-4]q
#配置aaa,创建用户cr,密码Chenrui$nmsl,优先级3,服务类型ssh
[JR_03]aaa
[JR_03-aaa]local-user cr password cipher Chenrui$nmsl
[JR_03-aaa]local-user cr privilege level 3
[JR_03-aaa]local-user cr service-type ssh
[JR_03-aaa]q
#配置cr用户的认证类型为password,用户服务模式stelnet,即ssh
[JR_03]ssh user cr authentication-type password
[JR_03]ssh user cr service-type stelnet
[JR_03]stelnet server enableNAT
#地址对象配置,指定各台设备的IP信息为地址对象
[FW]ip address-set FW type object
[FW-object-address-set-FW]address 0 10.10.88.57 mask 32
[FW-object-address-set-FW]q
[FW]ip address-set HX_01 type object
[FW-object-address-set-HX_01]address 0 10.0.2.1 mask 32
[FW-object-address-set-HX_01]q
[FW]ip address-set JR_02 type object
[FW-object-address-set-JR_02]address 0 10.0.2.2 mask 32
[FW-object-address-set-JR_02]q
[FW]ip address-set JR_03 type object
[FW-object-address-set-JR_03]address 0 10.0.2.3 mask 32
[FW-object-address-set-JR_03]q
#服务对象配置,指定所有端口访问防火墙的221为核心交换机01
[FW]ip service-set HX_01 type object 16
[FW-object-service-set-HX_01]service 0 protocol tcp source-port 0 to 65535 destination-port 221
[FW-object-service-set-HX_01]q
#服务对象配置,指定所有端口访问防火墙的222为接入交换机02
[FW]ip service-set JR_02 type object 17
[FW-object-service-set-JR_02]service 0 protocol tcp source-port 0 to 65535 destination-port 222
[FW-object-service-set-JR_02]q
#服务对象配置,指定所有端口访问防火墙的223为接入交换机03
[FW]ip service-set JR_03 type object 18
[FW-object-service-set-JR_03]service 0 protocol tcp source-port 0 to 65535 destination-port 223
[FW-object-service-set-JR_03]q
#NAT策略配置
#源NAT策略为PAT,即端口转换,内网10.0.3.0和10.0.4.0网段的设备都将以10.10.88.57的IP上的不同端口访问外网
#创建地址池nat_pat
[FW]nat address-group nat_pat
[FW-address-group-nat_pat]mode pat
[FW-address-group-nat_pat]section 10.10.88.57
[FW-address-group-nat_pat]q
[FW]nat-policy
[FW-policy-nat]rule name snat
[FW-policy-nat-rule-snat]source-zone trust
[FW-policy-nat-rule-snat]destination-zone dmz
[FW-policy-nat-rule-snat]source-address 10.0.3.0 mask 255.255.255.0
[FW-policy-nat-rule-snat]source-address 10.0.4.0 mask 255.255.255.0
[FW-policy-nat-rule-snat]action source-nat address-group nat_pat #调用地址池nat_pat
[FW-policy-nat-rule-snat]q
#目的NAT配置
[FW-policy-nat]rule name HX_01ssh
[FW-policy-nat-rule-HX_01ssh]source-zone dmz
[FW-policy-nat-rule-HX_01ssh]destination-address address-set FW #调用地址对象FW
[FW-policy-nat-rule-HX_01ssh]service HX_01 #调用服务对象HX_01,即访问该端口时使用下方规则
[FW-policy-nat-rule-HX_01ssh]action destination-nat static address-to-address address 10.0.2.1 22 #设置规则为访问10.10.88.57:221时映射为10.0.2.1:22
[FW-policy-nat-rule-HX_01ssh]q
[FW-policy-nat]rule name JR_02ssh
[FW-policy-nat-rule-JR_02ssh]source-zone dmz
[FW-policy-nat-rule-JR_02ssh]destination-address address-set FW #调用地址对象FW
[FW-policy-nat-rule-JR_02ssh]service JR_02 #调用服务对象JR_02,即访问该端口时使用下方规则
[FW-policy-nat-rule-JR_02ssh]action destination-nat static address-to-address address 10.0.2.2 22 #设置规则为访问10.10.88.57:222时映射为10.0.2.2:22
[FW-policy-nat-rule-JR_02ssh]q
[FW-policy-nat]rule name JR_03ssh
[FW-policy-nat-rule-JR_03ssh]source-zone dmz
[FW-policy-nat-rule-JR_03ssh]destination-address address-set FW #调用地址对象FW
[FW-policy-nat-rule-JR_03ssh]service JR_03 #调用服务对象JR_03,即访问该端口时使用下方规则
[FW-policy-nat-rule-JR_03ssh]action destination-nat static address-to-address address 10.0.2.3 22 #设置规则为访问10.10.88.57:223时映射为10.0.2.3:22
[FW-policy-nat-rule-JR_03ssh]q
[FW-policy-nat]q安全策略
#安全策略配置
[FW]security-policy
#trans规则是为了vlan30和40能够正常访问外网
[FW-policy-security]rule name trans
[FW-policy-security-rule-trans]source-zone trust
[FW-policy-security-rule-trans]destination-zone dmz
[FW-policy-security-rule-trans]source-address 10.0.3.0 mask 255.255.255.0
[FW-policy-security-rule-trans]source-address 10.0.4.0 mask 255.255.255.0
[FW-policy-security-rule-trans]action permit
[FW-policy-security-rule-trans]q
#inbound规则是防火墙测试能否ping通内网
[FW-policy-security]rule name inbound
[FW-policy-security-rule-inbound]source-zone local
[FW-policy-security-rule-inbound]destination-zone trust
[FW-policy-security-rule-inbound]action permit
[FW-policy-security-rule-inbound]q
#SSH规则是为了目的NAT能够访问内网三台交换机设备的22号端口
[FW-policy-security]rule name SSH
[FW-policy-security-rule-SSH]destination-zone trust
[FW-policy-security-rule-SSH]destination-address address-set HX_01
[FW-policy-security-rule-SSH]destination-address address-set JR_02
[FW-policy-security-rule-SSH]destination-address address-set JR_03
[FW-policy-security-rule-SSH]service protocol tcp source-port 0 to 65535 destination-port 22
[FW-policy-security-rule-SSH]action permit
[FW-policy-security-rule-SSH]q
[FW-policy-security]q信息全览
注:以下信息均不会加注释,请搭配目录酌情观看
防火墙
[FW]dis current-configuration
2023-01-27 08:59:45.160
!Software Version V500R005C10SPC300
#
sysname FW
#
domain suffix-separator @
#
undo info-center enable
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
update schedule location-sdb weekly Sun 07:36
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 02:44
update schedule av-sdb daily 02:44
update schedule sa-sdb daily 02:44
update schedule cnc daily 02:44
update schedule file-reputation daily 02:44
#
ip -instance default
ipv4-family
#
ip address-set FW type object
address 0 10.10.88.57 mask 32
#
ip address-set HX_01 type object
address 0 10.0.2.1 mask 32
#
ip address-set JR_02 type object
address 0 10.0.2.2 mask 32
#
ip address-set JR_03 type object
address 0 10.0.2.3 mask 32
#
ip service-set HX_01 type object 16
service 0 protocol tcp source-port 0 to 65535 destination-port 221
#
ip service-set JR_02 type object 17
service 0 protocol tcp source-port 0 to 65535 destination-port 222
#
ip service-set JR_03 type object 18
service 0 protocol tcp source-port 0 to 65535 destination-port 223
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl- ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%+y%LXfOu0)VhY2EY4#w,=-VtfEEpEt"KT-r]e]2DK)<&-Vw=@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%!zGv,cA#*8rm&VF`0z%+5qX#yB|`@vAYr~BNOm8U>+F4qX&5@%@%
level 15
manager-user admin
password cipher @%@%.ps5E|%ogV)z>:OEAt,;i+>4zUC>BJg;K)Z!gGA%UcvB+>7i@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding -instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.10.88.57 255.255.255.0
service-manage https permit
service-manage ping permit
service-manage ssh permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.0.1.254 255.255.255.0
service-manage https permit
service-manage ping permit
service-manage ssh permit
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
#
firewall zone untrust
set priority 5
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/0
#
ip route-static 0.0.0.0 0.0.0.0 10.10.88.1
ip route-static 10.0.2.0 255.255.255.0 10.0.1.253
ip route-static 10.0.3.0 255.255.255.0 10.0.1.253
ip route-static 10.0.4.0 255.255.255.0 10.0.1.253
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
nat address-group nat_pat 0
mode pat
section 0 10.10.88.57 10.10.88.57
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name trans
source-zone trust
destination-zone dmz
source-address 10.0.3.0 mask 255.255.255.0
source-address 10.0.4.0 mask 255.255.255.0
action permit
rule name inbound
source-zone local
destination-zone trust
action permit
rule name SSH
destination-zone trust
destination-address address-set HX_01
destination-address address-set JR_02
destination-address address-set JR_03
service protocol tcp source-port 0 to 65535 destination-port 22
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
rule name HX_01ssh
source-zone dmz
destination-address address-set FW
service HX_01
action destination-nat static address-to-address address 10.0.2.1 22
rule name JR_02ssh
source-zone dmz
destination-address address-set FW
service JR_02
action destination-nat static address-to-address address 10.0.2.2 22
rule name JR_03ssh
source-zone dmz
destination-address address-set FW
service JR_03
action destination-nat static address-to-address address 10.0.2.3 22
rule name snat
source-zone trust
destination-zone dmz
source-address 10.0.3.0 mask 255.255.255.0
source-address 10.0.4.0 mask 255.255.255.0
action source-nat address-group nat_pat
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return核心交换机(01)
[HX_01]dis cur
#
sysname HX_01
#
undo info-center enable
#
vlan batch 10 20 30 40
#
cluster enable
ntdp enable
ndp enable
#
undo nap slave enable
#
drop illegal-mac alarm
#
dhcp enable
#
dhcp server ping packet 3
dhcp server ping timeout 100
#
diffserv domain default
#
drop-profile default
#
ip pool vlan30
gateway-list 10.0.3.1
network 10.0.3.0 mask 255.255.255.0
dns-list 10.0.3.1
#
ip pool vlan40
gateway-list 10.0.4.1
network 10.0.4.0 mask 255.255.255.0
dns-list 10.0.4.1
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user sxc password cipher C+NDA+Z!_:ETGN]2]Q9J=Q!!
local-user sxc privilege level 3
local-user sxc service-type ssh
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface Vlanif10
ip address 10.0.1.253 255.255.255.128
#
interface Vlanif20
ip address 10.0.2.1 255.255.255.0
#
interface Vlanif30
ip address 10.0.3.1 255.255.255.0
dhcp select global
#
interface Vlanif40
ip address 10.0.4.1 255.255.255.0
dhcp select global
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 20 30 40
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 20 30 40
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
#
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface GigabitEthernet0/0/9
#
interface GigabitEthernet0/0/10
#
interface GigabitEthernet0/0/11
#
interface GigabitEthernet0/0/12
#
interface GigabitEthernet0/0/13
#
interface GigabitEthernet0/0/14
#
interface GigabitEthernet0/0/15
#
interface GigabitEthernet0/0/16
#
interface GigabitEthernet0/0/17
#
interface GigabitEthernet0/0/18
#
interface GigabitEthernet0/0/19
#
interface GigabitEthernet0/0/20
#
interface GigabitEthernet0/0/21
#
interface GigabitEthernet0/0/22
#
interface GigabitEthernet0/0/23
#
interface GigabitEthernet0/0/24
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 10.0.1.254
#
stelnet server enable
ssh user sxc
ssh user sxc authentication-type password
ssh user sxc service-type stelnet
#
user-interface con 0
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
#
return接入交换机(02)
[JR_02]dis cur
#
sysname JR_02
#
undo info-center enable
#
vlan batch 20 30 40
#
cluster enable
ntdp enable
ndp enable
#
undo nap slave enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user acz password cipher DYJ+N"+E!3NM"F..(DB+KQ!!
local-user acz privilege level 3
local-user acz service-type ssh
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface Vlanif20
ip address 10.0.2.2 255.255.255.0
#
interface MEth0/0/1
#
interface Ethernet0/0/1
port link-type trunk
port trunk allow-pass vlan 20 30 40
#
interface Ethernet0/0/2
port link-type access
port default vlan 30
#
interface Ethernet0/0/3
port link-type access
port default vlan 30
#
interface Ethernet0/0/4
port link-type access
port default vlan 30
#
interface Ethernet0/0/5
port link-type access
port default vlan 30
#
interface Ethernet0/0/6
port link-type access
port default vlan 30
#
interface Ethernet0/0/7
port link-type access
port default vlan 30
#
interface Ethernet0/0/8
port link-type access
port default vlan 30
#
interface Ethernet0/0/9
port link-type access
port default vlan 30
#
interface Ethernet0/0/10
port link-type access
port default vlan 30
#
interface Ethernet0/0/11
port link-type access
port default vlan 30
#
interface Ethernet0/0/12
port link-type access
port default vlan 40
#
interface Ethernet0/0/13
port link-type access
port default vlan 40
#
interface Ethernet0/0/14
port link-type access
port default vlan 40
#
interface Ethernet0/0/15
port link-type access
port default vlan 40
#
interface Ethernet0/0/16
port link-type access
port default vlan 40
#
interface Ethernet0/0/17
port link-type access
port default vlan 40
#
interface Ethernet0/0/18
port link-type access
port default vlan 40
#
interface Ethernet0/0/19
port link-type access
port default vlan 40
#
interface Ethernet0/0/20
port link-type access
port default vlan 40
#
interface Ethernet0/0/21
port link-type access
port default vlan 40
#
interface Ethernet0/0/22
port link-type access
port default vlan 40
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 10.0.2.1
#
stelnet server enable
ssh user acz
ssh user acz authentication-type password
ssh user acz service-type stelnet
#
user-interface con 0
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
#
port-group 1
group-member Ethernet0/0/2
group-member Ethernet0/0/3
group-member Ethernet0/0/4
group-member Ethernet0/0/5
group-member Ethernet0/0/6
group-member Ethernet0/0/7
group-member Ethernet0/0/8
group-member Ethernet0/0/9
group-member Ethernet0/0/10
group-member Ethernet0/0/11
#
port-group 2
group-member Ethernet0/0/12
group-member Ethernet0/0/13
group-member Ethernet0/0/14
group-member Ethernet0/0/15
group-member Ethernet0/0/16
group-member Ethernet0/0/17
group-member Ethernet0/0/18
group-member Ethernet0/0/19
group-member Ethernet0/0/20
group-member Ethernet0/0/21
group-member Ethernet0/0/22
#
return接入交换机(03)
[JR_03]dis cur
#
sysname JR_03
#
undo info-center enable
#
vlan batch 20 30 40
#
cluster enable
ntdp enable
ndp enable
#
undo nap slave enable
#
drop illegal-mac alarm
#
diffserv domain default
#
drop-profile default
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user cr password cipher #%;JE^SU`T5GXLFV]WQ&S1!!
local-user cr privilege level 3
local-user cr service-type ssh
local-user admin password simple admin
local-user admin service-type http
#
interface Vlanif1
#
interface Vlanif20
ip address 10.0.2.3 255.255.255.0
#
interface MEth0/0/1
#
interface Ethernet0/0/1
port link-type trunk
port trunk allow-pass vlan 20 30 40
#
interface Ethernet0/0/2
port link-type access
port default vlan 30
#
interface Ethernet0/0/3
port link-type access
port default vlan 30
#
interface Ethernet0/0/4
port link-type access
port default vlan 30
#
interface Ethernet0/0/5
port link-type access
port default vlan 30
#
interface Ethernet0/0/6
port link-type access
port default vlan 30
#
interface Ethernet0/0/7
port link-type access
port default vlan 30
#
interface Ethernet0/0/8
port link-type access
port default vlan 30
#
interface Ethernet0/0/9
port link-type access
port default vlan 30
#
interface Ethernet0/0/10
port link-type access
port default vlan 30
#
interface Ethernet0/0/11
port link-type access
port default vlan 30
#
interface Ethernet0/0/12
port link-type access
port default vlan 40
#
interface Ethernet0/0/13
port link-type access
port default vlan 40
#
interface Ethernet0/0/14
port link-type access
port default vlan 40
#
interface Ethernet0/0/15
port link-type access
port default vlan 40
#
interface Ethernet0/0/16
port link-type access
port default vlan 40
#
interface Ethernet0/0/17
port link-type access
port default vlan 40
#
interface Ethernet0/0/18
port link-type access
port default vlan 40
#
interface Ethernet0/0/19
port link-type access
port default vlan 40
#
interface Ethernet0/0/20
port link-type access
port default vlan 40
#
interface Ethernet0/0/21
port link-type access
port default vlan 40
#
interface Ethernet0/0/22
port link-type access
port default vlan 40
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 10.0.2.1
#
stelnet server enable
ssh user cr
ssh user cr authentication-type password
ssh user cr service-type stelnet
#
user-interface con 0
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
#
port-group 1
group-member Ethernet0/0/2
group-member Ethernet0/0/3
group-member Ethernet0/0/4
group-member Ethernet0/0/5
group-member Ethernet0/0/6
group-member Ethernet0/0/7
group-member Ethernet0/0/8
group-member Ethernet0/0/9
group-member Ethernet0/0/10
group-member Ethernet0/0/11
#
port-group 2
group-member Ethernet0/0/12
group-member Ethernet0/0/13
group-member Ethernet0/0/14
group-member Ethernet0/0/15
group-member Ethernet0/0/16
group-member Ethernet0/0/17
group-member Ethernet0/0/18
group-member Ethernet0/0/19
group-member Ethernet0/0/20
group-member Ethernet0/0/21
group-member Ethernet0/0/22
#
returnPC
所有PC除了主机名都是这个配置
结果验证
核心01
接入02
接入03
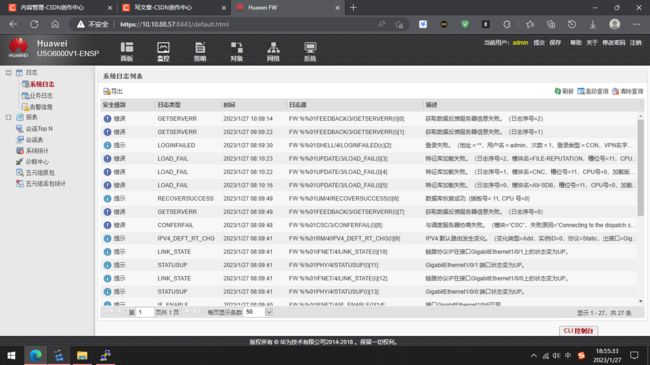
防火墙
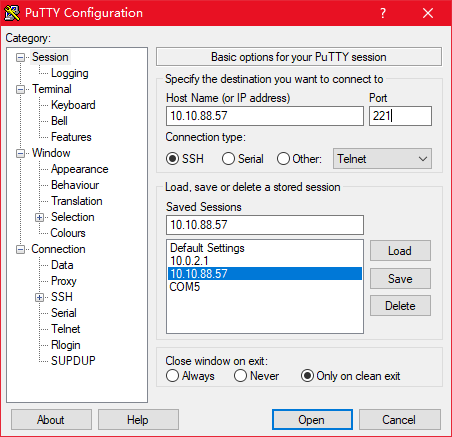
PC验证
问题总结
Cloud连通防火墙时,ping不通,检查防火墙的接口是否允许ping,再次检查虚拟网卡是否配置正确,应以防火墙为网关,检查本地防火墙或安全软件是否拦截了数据
交换机的管理地址ping不通时,检查接入交换机是否配置了默认路由
ping不了外网时应该检查是否配置好了vlan,回程路由,dhcp
一开始打算全用ensp来模拟,但是找不到应该用什么设备来验证ssh,索性更换成cloud用物理机验证
顺便放一下对我这篇文章有帮助的链接,cloud的解决办法还有ssh的解决办法
【原创】关于使用putty软件通过SSH方式登录时出现“Signature from server's host key is invalid”错误的解决方法
USG6000V防火墙WEB登录界面超详细配置过程
本文章的拓扑文件已上传,需要者自取
中小型网络模型(ensp模拟)
欢迎各位对我文章里存在的各种错误或者瑕疵进行批评,同时欢迎各位向我提出各种文章制作上的建议