BGP认证的原理配置
.2.3BGP认证
- 常见BGP攻击主要有两种:
- 建立非法BGP邻居关系,通告非法路由条目,干扰正常路由表。
- 发送大量非法BGP报文,路由器收到后上送CPU,导致CPU利用率升高
- BGP认证
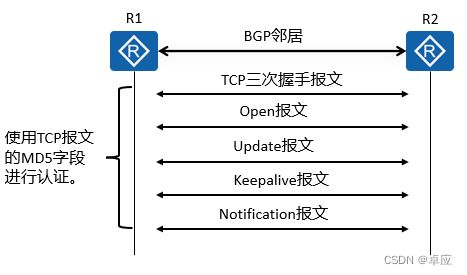
BGP认证分为MD5认证和Keychain认证,对BGP对等体关系进行认证可以预防非法BGP邻居建立。
- MD5认证
BGP使用TCP作为传输层协议,为提高BGP的安全性,可以在建立TCP连接时进行MD5认证。BGP的MD5认证只是为TCP连接设置MD5认证密码,由TCP完成认证。
- Keychain认证
BGP对等体两端必须都配置针对使用TCP连接的应用程序的Keychain认证,且配置的Keychain必须使用相同的加密算法和密码,才能正常建立TCP连接,交互BGP消息。
【技术要点】MD5与Keychain的区别
- MD5算法配置简单,配置后生成单一密码,需要人为干预才可以更换密码。
- Keychain具有一组密码,可以根据配置自动切换,但是配置过程较为复杂,适用于对安全性能要求比较高的网络。
- BGP的MD5认证与BGP的Keychain认证互斥。
- GTSM(Generalized TTL Security Mechanism,通用TTL安全保护机制)
BGP的GTSM功能检测IP报文头中的TTL(Time-to-Live)值是否在一个预先设置好的特定范围内,并对不符合TTL值范围的报文进行丢弃,这样就避免了网络攻击者模拟“合法”BGP报文攻击设备。
当攻击者模拟合法的BGP报文,对R2不断地发送非法报文进行攻击时,TTL值必然小于255。如果R2使能BGP的GTSM功能,将IBGP对等体报文的TTL的有效范围设为[255,255],系统会对所有BGP报文的TTL值进行检查,丢弃TTL值小于255的攻击报文,从而避免了因网络攻击报文导致CPU占用率高的问题。
3.4.5 BGP的安全性
1. 实验目的
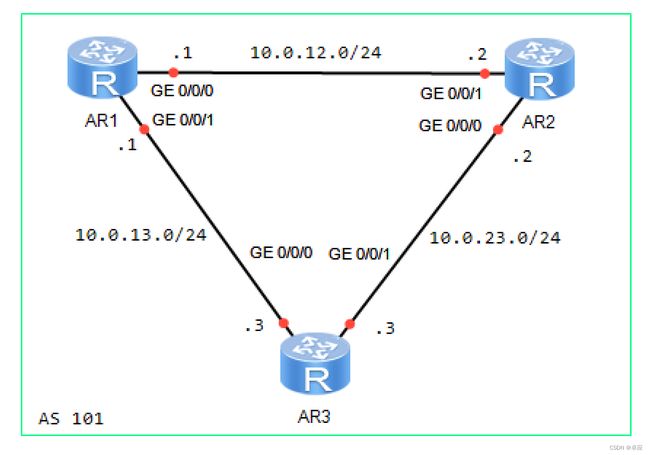
2. 实验拓扑
3. 实验步骤
实验视频指导:
华为Datacom网络工程师HCIP全套学习课程(全套理论+实验)-学习视频教程-腾讯课堂
- 配置IP地址
AR1的配置
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname AR1
[AR1]interface g0/0/0
[AR1-GigabitEthernet0/0/0]ip address 10.0.12.1 24
[AR1-GigabitEthernet0/0/0]quit
[AR1]interface g0/0/1
[AR1-GigabitEthernet0/0/1]ip address 10.0.13.1 24
[AR1-GigabitEthernet0/0/1]quit
[AR1]interface LoopBack 0
[AR1-LoopBack0]ip address 1.1.1.1 32
[AR1-LoopBack0]quit
AR2的配置
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname AR2
[AR2]interface g0/0/1
[AR2-GigabitEthernet0/0/1]ip address 10.0.12.2 24
[AR2-GigabitEthernet0/0/1]quit
[AR2]interface g0/0/0
[AR2-GigabitEthernet0/0/0]ip address 10.0.23.2 24
[AR2-GigabitEthernet0/0/0]quit
[AR2]interface LoopBack 0
[AR2-LoopBack0]ip address 2.2.2.2 32
[AR2-LoopBack0]quit
AR3的配置
Enter system view, return user view with Ctrl+Z.
[Huawei]undo info-center enable
Info: Information center is disabled.
[Huawei]sysname AR3
[AR3]interface g0/0/0
[AR3-GigabitEthernet0/0/0]ip address 10.0.13.3 24
[AR3-GigabitEthernet0/0/0]quit
[AR3]interface g0/0/1
[AR3-GigabitEthernet0/0/1]ip address 10.0.23.3 24
[AR3-GigabitEthernet0/0/1]quit
[AR3]interface LoopBack 0
[AR3-LoopBack0]ip address 3.3.3.3 32
[AR3-LoopBack0]quit
- 配置OSPF
AR1的配置
[AR1]ospf router-id 1.1.1.1
[AR1-ospf-1]area 0
[AR1-ospf-1-area-0.0.0.0]network 10.0.12.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]network 10.0.13.0 0.0.0.255
[AR1-ospf-1-area-0.0.0.0]network 1.1.1.1 0.0.0.0
[AR1-ospf-1-area-0.0.0.0]quit
AR2的配置
[AR2]ospf router-id 2.2.2.2
[AR2-ospf-1]area 0
[AR2-ospf-1-area-0.0.0.0]network 10.0.12.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]network 10.0.23.0 0.0.0.255
[AR2-ospf-1-area-0.0.0.0]network 2.2.2.2 0.0.0.0
[AR2-ospf-1-area-0.0.0.0]quit
AR3的配置
[AR3]ospf router-id 3.3.3.3
[AR3-ospf-1]area 0
[AR3-ospf-1-area-0.0.0.0]network 10.0.13.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]network 10.0.23.0 0.0.0.255
[AR3-ospf-1-area-0.0.0.0]network 3.3.3.3 0.0.0.0
[AR3-ospf-1-area-0.0.0.0]quit
- 配置BGP
AR1的配置
[AR1]bgp 101
[AR1-bgp]peer 2.2.2.2 as-number 101
[AR1-bgp]peer 2.2.2.2 connect-interface LoopBack 0
[AR1-bgp]peer 3.3.3.3 as-number 101
[AR1-bgp]peer 3.3.3.3 connect-interface LoopBack 0
[AR1-bgp]quit
AR2的配置
[AR2]bgp 101
[AR2-bgp]peer 1.1.1.1 as-number 101
[AR2-bgp]peer 1.1.1.1 connect-interface LoopBack 0
[AR2-bgp]peer 3.3.3.3 as-number 101
[AR2-bgp]peer 3.3.3.3 connect-interface LoopBack 0
[AR2-bgp]quit
AR3的配置
[AR3]bgp 101
[AR3-bgp]peer 1.1.1.1 as-number 101
[AR3-bgp]peer 2.2.2.2 as-number 101
[AR3-bgp]peer 1.1.1.1 connect-interface LoopBack 0
[AR3-bgp]peer 2.2.2.2 connect-interface LoopBack 0
[AR3-bgp]quit
4. 实验调试
- 在AR1与AR2之间配置MD5认证
[AR1]bgp 101
[AR1-bgp]peer 2.2.2.2 password cipher 1234
[AR1-bgp]quit
[AR2]bgp 101
[AR2-bgp]peer 1.1.1.1 password cipher 1234
[AR2-bgp]quit
【技术要点】MD5认证
- 在AR1上查看查看BGP对等体的认证信息。
[AR1]display bgp peer 2.2.2.2 verbose
BGP Peer is 2.2.2.2, remote AS 101
Type: IBGP link
BGP version 4, Remote router ID 10.0.23.2
Update-group ID: 1
BGP current state: Established, Up for 00h15m15s
BGP current event: RecvKeepalive
BGP last state: OpenConfirm
BGP Peer Up count: 1
Received total routes: 0
Received active routes total: 0
Advertised total routes: 0
Port: Local - 49215 Remote - 179
Configured: Connect-retry Time: 32 sec
Configured: Active Hold Time: 180 sec Keepalive Time:60 sec
Received : Active Hold Time: 180 sec
Negotiated: Active Hold Time: 180 sec Keepalive Time:60 sec
Peer optional capabilities:
Peer supports bgp multi-protocol extension
Peer supports bgp route refresh capability
Peer supports bgp 4-byte-as capability
Address family IPv4 Unicast: advertised and received
Received: Total 17 messages
Update messages 0
Open messages 1
KeepAlive messages 16
Notification messages 0
Refresh messages 0
Sent: Total 17 messages
Update messages 0
Open messages 1
KeepAlive messages 16
Notification messages 0
Refresh messages 0
Authentication type configured: MD5
Last keepalive received: 2023/01/30 15:30:24 UTC-08:00
Last keepalive sent : 2023/01/30 15:30:23 UTC-08:00
Minimum route advertisement interval is 15 seconds
Optional capabilities:
Route refresh capability has been enabled
4-byte-as capability has been enabled
Connect-interface has been configured
Peer Preferred Value: 0
Routing policy configured:
No routing policy is configured
通过以上输出可以看到认证的类型为MD5。
- 在AR1与AR3上设置key-chain认证
第一步:创建keychain
[AR1]keychain lw mode absolute //创建一个keychain名字叫lw,模式为绝对时间(也可以是周期性,比如每天)
[AR1-keychain]receive-tolerance 10 //接收容错时间为10分钟
[AR1-keychain]tcp-kind 182
[AR1-keychain]tcp-algorithm-id hmac-md5 50
[AR1-keychain]quit
【技术要点1】receive-tolerance
- 由于网络环境或者两端时间未同步等因素影响,key-id发送的报文可能存在延迟,即接收端在非活跃时间段收到发送端发送的报文,将导致因接收端处于非活跃状态而丢弃该报文,使协议报文传输中断。为了解决该问题,用户可以配置接收的容错时间,使接收段在配置的接收时间到达后再持续生效指定的时间,保证使接收端能处理发送端发送的所有报文,保证协议报文的正常处理。
- 配置接收容错时间将在接收时间的起始时间和结束时间同时增加相应的时间。
【技术要点2】receive-tolerance
- 对于TCP连接建立的认证交互,TCP使用增强的TCP认证选项。目前,不同的厂商使用不同的kind-value值代表增强的TCP认证选项。为了实现不同厂商设备之间的交互,用户可以选择配置kind-value,使通信两端设备的TCP类型一致。
- 配置kind-value值时,采用Keychain认证的通信双方必须是采用TCP建立连接的应用程序。否则配置的TCP认证不生效。
- 通信双方的TCP类型配置一致后,还需要指定通信双方相同的认证算法对应ID。
第二步:配置keychain中的key
AR1的配置
[AR1-keychain]key-id 1 //key1
[AR1-keychain-keyid-1]algorithm hmac-md5 //算法为hmac-md5
[AR1-keychain-keyid-1]key-string cipher joinlabs1 //密码为joinlabs1
[AR1-keychain-keyid-1]send-time utc 12:00 2023-01-30 to 17:00 2023-01-30 //发送时间
[AR1-keychain-keyid-1]receive-time utc 12:00 2023-01-30 to 17:00 2023-01-30 //接收时间
[AR1-keychain-keyid-1]quit
[AR1-keychain]key-id 2
[AR1-keychain-keyid-2]algorithm hmac-md5
[AR1-keychain-keyid-2]key-string cipher joinlabs2
[AR1-keychain-keyid-2]send-time utc 17:01 2023-01-30 to 18:00 2023-01-30
[AR1-keychain-keyid-2]receive-time utc 17:01 2023-01-30 to 18:00 2023-01-30
[AR1-keychain-keyid-2]quit
AR3的配置
[AR3]keychain lw mode absolute
[AR3-keychain]receive-tolerance 10
[AR3-keychain]tcp-kind 182
[AR3-keychain]tcp-algorithm-id hmac-md5 50
[AR3-keychain]quit
[AR3]keychain lw
[AR3-keychain]key-id 1
[AR3-keychain-keyid-1]algorithm hmac-md5
[AR3-keychain-keyid-1]key-string cipher joinlabs1
[AR3-keychain-keyid-1]send-time utc 12:00 2023-01-30 to 17:00 2023-01-30
[AR3-keychain-keyid-1]receive-time utc 12:00 2023-01-30 to 17:00 2023-01-30
[AR3-keychain-keyid-1]quit
[AR3-keychain]key-id 2
[AR3-keychain-keyid-2]algorithm hmac-md5
[AR3-keychain-keyid-2]key-string cipher joinlabs2
[AR3-keychain-keyid-2]send-time utc 17:01 2023-01-30 to 18:00 2023-01-30
[AR3-keychain-keyid-2]receive-time utc 17:01 2023-01-30 to 18:00 2023-01-30
[AR3-keychain-keyid-2]quit
- 配置keychain认证
[AR1]bgp 101
[AR1-bgp]peer 3.3.3.3 keychain lw
[AR1-bgp]quit
[AR3]bgp 101
[AR3-bgp]peer 1.1.1.1 keychain lw
[AR3-bgp]quit
- 查看当前处于Active状态的Key-id
Keychain Information:
---------------------
Keychain Name : lw
Timer Mode : Absolute
Receive Tolerance(min) : 10
TCP Kind : 182
TCP Algorithm IDs :
HMAC-MD5 : 50
HMAC-SHA1-12 : 2
HMAC-SHA1-20 : 6
MD5 : 3
SHA1 : 4
Number of Key IDs : 2
Active Send Key ID : 2
Active Receive Key IDs : 01 02
Default send Key ID : Not configured
Key ID Information:
-------------------
Key ID : 1
Key string : %$%$Z4^:U0Tz^.Lup[UrVa`+$UBU%$%$ (cipher)
Algorithm : HMAC-MD5
SEND TIMER :
Start time : 2023-01-30 12:00
End time : 2023-01-30 17:00
Status : Inactive
RECEIVE TIMER :
Start time : 2023-01-30 12:00
End time : 2023-01-30 17:00
Status : Active
Key ID : 2
Key string : %$%$H>04M1/+dUKY`5:znJ+/$Zh9%$%$ (cipher)
Algorithm : HMAC-MD5
SEND TIMER :
Start time : 2023-01-30 17:01
End time : 2023-01-30 18:00
Status : Active
RECEIVE TIMER :
Start time : 2023-01-30 17:01
End time : 2023-01-30 18:00
Status : Active
通过以上输出可以看到key1是inactive,key2是active
- 看BGP对等体是否已配置的认证类型是Keychain
BGP Peer is 3.3.3.3, remote AS 101
Type: IBGP link
BGP version 4, Remote router ID 10.0.13.3
Update-group ID: 1
BGP current state: Established, Up for 02h06m29s
BGP current event: KATimerExpired
BGP last state: OpenConfirm
BGP Peer Up count: 1
Received total routes: 0
Received active routes total: 0
Advertised total routes: 0
Port: Local - 49215 Remote - 179
Configured: Connect-retry Time: 32 sec
Configured: Active Hold Time: 180 sec Keepalive Time:60 sec
Received : Active Hold Time: 180 sec
Negotiated: Active Hold Time: 180 sec Keepalive Time:60 sec
Peer optional capabilities:
Peer supports bgp multi-protocol extension
Peer supports bgp route refresh capability
Peer supports bgp 4-byte-as capability
Address family IPv4 Unicast: advertised and received
Received: Total 128 messages
Update messages 0
Open messages 1
KeepAlive messages 127
Notification messages 0
Refresh messages 0
Sent: Total 128 messages
Update messages 0
Open messages 1
KeepAlive messages 127
Notification messages 0
Refresh messages 0
Authentication type configured: Keychain(lw)
Last keepalive received: 2023/01/30 17:21:22 UTC-08:00
Last keepalive sent : 2023/01/30 17:21:23 UTC-08:00
Minimum route advertisement interval is 15 seconds
Optional capabilities:
Route refresh capability has been enabled
4-byte-as capability has been enabled
Connect-interface has been configured
Peer Preferred Value: 0
Routing policy configured:
No routing policy is configured
【技术要点】MD5与KeyChain认证
MD5认证只能为TCP连接设置认证密码
Keychain认证除了可以为TCP连接设置认证密码外,还可以对BGP协议报文进行认证。
BGP MD5认证与BGP Keychain认证互斥。
思考:过了这段时间,BGP连接是不是会失效?
- 在AR2和AR3上面配置GTSM
[AR2]bgp 101
[AR2-bgp]peer 3.3.3.3 valid-ttl-hops 1 //在R1与R2间开启GTSM。由于两台路由器直连,因此TTL到达对方的有效范围是[255, 255],所以此处的valid-ttl-hops值取1。
[AR2-bgp]quit
[AR3]bgp 101
[AR3-bgp]peer 2.2.2.2 valid-ttl-hops 1
[AR3-bgp]quit
【技术要点】peer 3.3.3.3 valid-ttl-hops 1
- 在向邻居3.3.3.3发送BGP报文时,TTL为255
- 在接收邻居3.3.3.3发来的BGP报文时,要求报文的TTL大于等于255-1+1
- 被检测报文的TTL值有效范围为[ 255–hops+1, 255 ]
例如,对于EBGP直连路由,hops的取值为1,即有效的TTL值设为255。缺省情况下,参数hops取值为255,即TTL有效值范围为 [ 1, 255 ]。