已知p部分高位部分低位2道例题
文章目录
- 题一
-
- 题目描述:
- 题目分析:
- 题二
-
- 题目描述:
- 题目分析:
- 收获
-
- 1.
- 2.
- 3.
- 4.
题一
题目描述:
from Crypto.Util.number import *
from string import digits, ascii_letters, punctuation
from sympy import *
from random import *
from secret import flag
bytemap=digits+ascii_letters
while True:
rand_str = ''.join(sample(bytemap,35))
dots = b'A_S1mp13_P01y_pr0b13m' + bytes(rand_str.encode('utf-8')) + b'h0pe_u_3nj0y_th3_g4m3!'
p = bytes_to_long(dots)
q = bytes_to_long(dots[::-1])
if isprime(p) and isprime(q):
n = p * q
e = 0x10001
m = bytes_to_long(flag)
c = pow(m, e, n)
break
print(f'n = {n}')
print(f'c = {c}')
'''
e = 65537
n = 160508672993727358356100574316302368918534631512763166391965986459416715199014434847644161160721255203715386815079832158095605929815302757649142544200042372910754972968132210351705146824875858826811770334342006375827775154532627219377397067171480126883778382589913759906673058782641771905822391028460391246464115399357231839585151266124847230328797529208115402392357841549921
c = 44890366134356739026070529484575169308358584023921132030166935295829511775694646905781636144799301645824955711148476278048352767444326748892856410720229148435625075536672131990569624953503769758762262270319896220742551672641773475300480348064418068221385153263339673791806292988630895712258019379075857567539567061341157520204500506719761884664166941313528709164860727850793
'''
题目分析:
-
总的来说,值得注意和记录的就是bytes_to_long(x)能将x转化为它的256进制
-
还有一个知识点:
b'A_S1mp13_P01y_pr0b13m' + bytes(rand_str.encode('utf-8')) + b'h0pe_u_3nj0y_th3_g4m3!’ 在256进制下,是一个(21+35+22)位的数字 在2进制下,就是一个8 * (21+35+22)位的数字(一位字母转化为一位8bits二进制,故乘8) -
以下为解题代码:
# python
from Crypto.Util.number import *
p_high = b'A_S1mp13_P01y_pr0b13m'
p_low = b'h0pe_u_3nj0y_th3_g4m3!'
print(bytes_to_long(p_high))
print(bytes_to_long(p_low))
'''
p_high = 95541815817330350130425149533914010078810221917037
p_low = 38981813338547046700101524093008643321092413022090017
'''
# sage
n = 160508672993727358356100574316302368918534631512763166391965986459416715199014434847644161160721255203715386815079832158095605929815302757649142544200042372910754972968132210351705146824875858826811770334342006375827775154532627219377397067171480126883778382589913759906673058782641771905822391028460391246464115399357231839585151266124847230328797529208115402392357841549921
p_high = 95541815817330350130425149533914010078810221917037
p_low = 38981813338547046700101524093008643321092413022090017
mod1 = 256 ^ 22
mod2 = 256 ^ 57
PR.<x> = PolynomialRing(Zmod(n))
f = p_high * mod2 + x * mod1 + p_low
f = f.monic()
out_p = f.small_roots(2 ^ 280,beta = 0.4,epsilon = 0.03)
# 280 = 35 * 8
p = gcd(int(f(out_p[0])),n)
print(p)
'''
p = 17777533830541882333815981119159197905758393675130560629403650383690014411161496047927341536475256420928974390183963581379233984191390025279242558157263772543458912958743931816360146711329
'''
# python
import gmpy2
from Crypto.Util.number import *
p = 17777533830541882333815981119159197905758393675130560629403650383690014411161496047927341536475256420928974390183963581379233984191390025279242558157263772543458912958743931816360146711329
e = 65537
n = 160508672993727358356100574316302368918534631512763166391965986459416715199014434847644161160721255203715386815079832158095605929815302757649142544200042372910754972968132210351705146824875858826811770334342006375827775154532627219377397067171480126883778382589913759906673058782641771905822391028460391246464115399357231839585151266124847230328797529208115402392357841549921
c = 44890366134356739026070529484575169308358584023921132030166935295829511775694646905781636144799301645824955711148476278048352767444326748892856410720229148435625075536672131990569624953503769758762262270319896220742551672641773475300480348064418068221385153263339673791806292988630895712258019379075857567539567061341157520204500506719761884664166941313528709164860727850793
q = n // p
phi = (p-1)*(q-1)
print(gmpy2.gcd(e,phi))
d = gmpy2.invert(e,phi)
m = pow(c,d,n)
print(long_to_bytes(m))
- 得到:flag{th15_P01yn0m141_15_n0t_d1ff1cu1t!!}
题二
题目描述:
from Crypto.Util.number import getPrime, bytes_to_long
from secret import flag
p = getPrime(1024)
q = getPrime(1024)
n = p * q
e = 65537
hint1 = p >> 724
hint2 = q % (2 ** 265)
ct = pow(bytes_to_long(flag), e, n)
print(hint1)
print(hint2)
print(n)
print(ct)
题目分析:
# sage
p_high = 1514296530850131082973956029074258536069144071110652176122006763622293335057110441067910479
q_low = 40812438243894343296354573724131194431453023461572200856406939246297219541329623
n = 21815431662065695412834116602474344081782093119269423403335882867255834302242945742413692949886248581138784199165404321893594820375775454774521554409598568793217997859258282700084148322905405227238617443766062207618899209593375881728671746850745598576485323702483634599597393910908142659231071532803602701147251570567032402848145462183405098097523810358199597631612616833723150146418889589492395974359466777040500971885443881359700735149623177757865032984744576285054725506299888069904106805731600019058631951255795316571242969336763938805465676269140733371287244624066632153110685509892188900004952700111937292221969
mod = pow(2,265)
# python中求解p0
# import gmpy2
# n = 21815431662065695412834116602474344081782093119269423403335882867255834302242945742413692949886248581138784199165404321893594820375775454774521554409598568793217997859258282700084148322905405227238617443766062207618899209593375881728671746850745598576485323702483634599597393910908142659231071532803602701147251570567032402848145462183405098097523810358199597631612616833723150146418889589492395974359466777040500971885443881359700735149623177757865032984744576285054725506299888069904106805731600019058631951255795316571242969336763938805465676269140733371287244624066632153110685509892188900004952700111937292221969
# q_low = 40812438243894343296354573724131194431453023461572200856406939246297219541329623
# mod = pow(2,265)
# p0 = n * gmpy2.invert(q_low,mod) % mod
# print(p0)
p0 = 30417487794073877577997977068358253483488121930635899911316665665825597484019031
PR.<x> = PolynomialRing(Zmod(n))
for i in range(2 ** 5):
f = p_high * (2 ** 724) + (x * 32 + i) * mod + p0
f = f.monic()
out_p = f.small_roots(2 ^ 454,0.4)
if len(out_p) != 0:
print(out_p[0])
break
p = out_p[0] * 32 * mod + i * mod + p_high * (2 ^ 724) + p0
print(p)
'''
p = 133637329398256221348922087205912367118213472434713498908220867690672019569057789598459580146410501473689139466275052698529257254973211963162087316149628000798221014338373126500646873612341158676084318494058522014519669302359038980726479317742766438142835169562422371156257894374341629012755597863752154328407
'''
# python
import gmpy2
from Crypto.Util.number import *
p = 133637329398256221348922087205912367118213472434713498908220867690672019569057789598459580146410501473689139466275052698529257254973211963162087316149628000798221014338373126500646873612341158676084318494058522014519669302359038980726479317742766438142835169562422371156257894374341629012755597863752154328407
n = 21815431662065695412834116602474344081782093119269423403335882867255834302242945742413692949886248581138784199165404321893594820375775454774521554409598568793217997859258282700084148322905405227238617443766062207618899209593375881728671746850745598576485323702483634599597393910908142659231071532803602701147251570567032402848145462183405098097523810358199597631612616833723150146418889589492395974359466777040500971885443881359700735149623177757865032984744576285054725506299888069904106805731600019058631951255795316571242969336763938805465676269140733371287244624066632153110685509892188900004952700111937292221969
c = 19073695285772829730103928222962723784199491145730661021332365516942301513989932980896145664842527253998170902799883262567366661277268801440634319694884564820420852947935710798269700777126717746701065483129644585829522353341718916661536894041337878440111845645200627940640539279744348235772441988748977191513786620459922039153862250137904894008551515928486867493608757307981955335488977402307933930592035163126858060189156114410872337004784951228340994743202032248681976932591575016798640429231399974090325134545852080425047146251781339862753527319093938929691759486362536986249207187765947926921267520150073408188188
e = 65537
q = n // p
phi = (p-1)*(q-1)
print(gmpy2.gcd(e,phi))
d = gmpy2.invert(e,phi)
m = pow(c,d,n)
print(long_to_bytes(m))
- 得到:flag{ef5e1582-8116-4f61-b458-f793dc03f2ff}
收获
1.
bytes_to_long(x)能将x转化为它的256进制
2.
b'A_S1mp13_P01y_pr0b13m' + bytes(rand_str.encode('utf-8')) + b'h0pe_u_3nj0y_th3_g4m3!’
在256进制下,是一个(21+35+22)位的数字
在2进制下,就是一个8 * (21+35+22)位的数字(一位字母转化为一位8bits二进制,故乘8)
3.
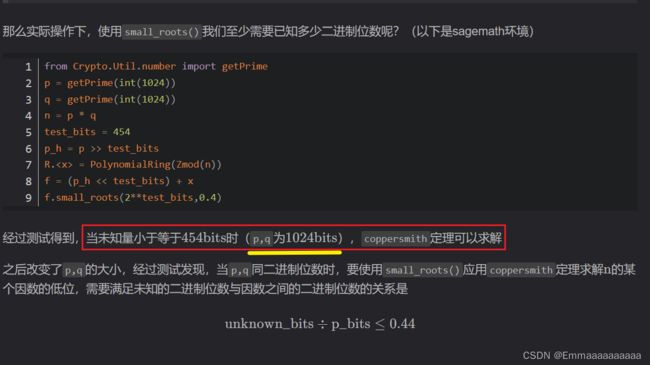
当未知量小于等于454bits时(p,q为1024bits),coppersmith定理可以求解
4.
f = p_high * (2 ** 724) + (x * 32 + i) * mod + p0
也可写为:
pbar = (p_high << 724) + p0
f = pbar + (x * 32 + i) * mod
不可写做:
f = (p_high << 724) + (x * 32 + i) * mod + p0 否则报错