0012-TIPS-pawnyable : Use-After-Free
原文
Linux Kernel PWN | 040203 Pawnyable之UAF
https://pawnyable.cafe/linux-kernel/LK01/use_after_free.html
题目下载
漏洞代码
#include 漏洞分析
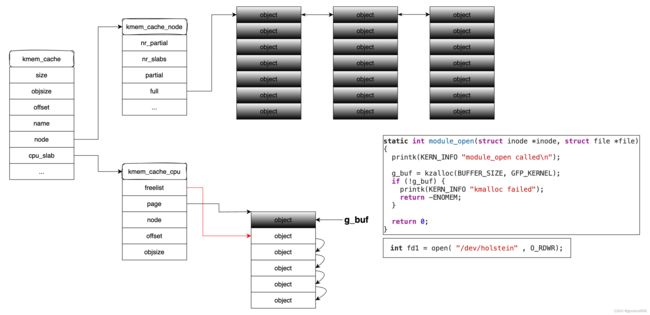
驱动可以被同时打开多次,g_buf指向最后一次打开时分配的堆对象 g_buf = kzalloc(BUFFER_SIZE, GFP_KERNEL);
#define BUFFER_SIZE 0x400
char *g_buf = NULL;
static int module_open(struct inode *inode, struct file *file)
{
printk(KERN_INFO "module_open called\n");
g_buf = kzalloc(BUFFER_SIZE, GFP_KERNEL);
if (!g_buf) {
printk(KERN_INFO "kmalloc failed");
return -ENOMEM;
}
return 0;
}
static int module_close(struct inode *inode, struct file *file)
{
printk(KERN_INFO "module_close called\n");
kfree(g_buf);
return 0;
}
第一次打开驱动
第二次打开驱动
关闭其中一个fd
close(fd),会调用module_close,将当前指向g_buf的堆对象空间释放掉,
同时可以通过堆喷占据g_buf释放掉的堆对象,
由于module_close在释放g_buf堆对象时,没有赋值NULL,可以通过另一个fdmodule_close对g_buf指向的堆对象进行读写,也就是修改堆喷对象占据的堆空间,从而进行利用提权。
漏洞利用
利用方式与0011-TIPS-pawnyable : Heap-Overflow一致
01_leak_kbase_and_heap
#include 02_exploit_bypass_kaslr_smap_smep
#include 03_exploit_userland_pivoting
#include 04_exploit_aaw_modprobe
#include 05_exploit_aar_aaw_cred
#include