0013-TIPS-pawnyable : Race-Condition
原文
Linux Kernel PWN | 040204 Pawnyable之竞态条件
Holstein v4: Race Condition
题目下载
漏洞代码
#include 漏洞分析
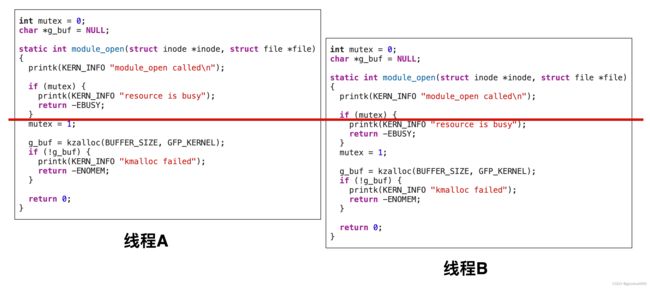
想要保证驱动,同一时刻只能被打开一次,但是可重入代码是用的全局变量进行的保护,这是漏洞点。
#define BUFFER_SIZE 0x400
int mutex = 0;
char *g_buf = NULL;
static int module_open(struct inode *inode, struct file *file)
{
printk(KERN_INFO "module_open called\n");
if (mutex) {
printk(KERN_INFO "resource is busy");
return -EBUSY;
}
mutex = 1;
g_buf = kzalloc(BUFFER_SIZE, GFP_KERNEL);
if (!g_buf) {
printk(KERN_INFO "kmalloc failed");
return -ENOMEM;
}
return 0;
}
static int module_close(struct inode *inode, struct file *file)
{
printk(KERN_INFO "module_close called\n");
kfree(g_buf);
mutex = 0;
return 0;
}
看下图,在线程A执行mutex=1之前,线程B绕过了if(mutex)检查,就可以同时多次打开驱动
产生条件竞争
先通过一个例子看看进程是如何分配文件描述符的
#include 结果
fd1 = 3
fd2 = 4
fd1 = 3
文件描述符0、1、2默认分配给了,标准输入、标准输出、标准错误
之后文件描述符从3开始分配,如果其中有多个描述符被关闭了,新的文件描述符从最小可用的数字进行分配
对于本题,如何赢得条件竞争
对于本驱动,在不打开额外文本的情况下,使用两个线程跑尝试是否可以赢得条件竞争
- 首先文件描述0、1、2 默认分配给了,标准输入、标准输出、标准错误
- 其次无论否可以赢得条件竞争,总会有一个线程打开驱动,获取文件描述符3,所以如果赢得条件竞争那文件描述符一个就是3,一个就是4
- 当有一个文件描述符是3是,另一个文件描述符不是4,需要关闭这两个文件文件描述符重新竞争
赢得条件竞争的代码如下
#include 条件竞争转UAF
在赢得条件竞争的基础上,题目还存在UAF漏洞,可以利用这个UAF提权
#define _GNU_SOURCE
#include