0014-TIPS-pawnyable : Double-Fetch && pt_regs
原文
Linux Kernel PWN | 040302 Pawnyable之双取
Double Fetch
题目下载
漏洞代码
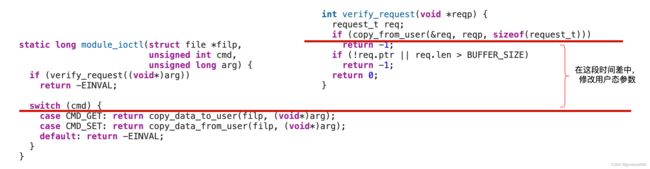
#include 漏洞点如下:
- 用户态调用ioctl传递到内核态的值
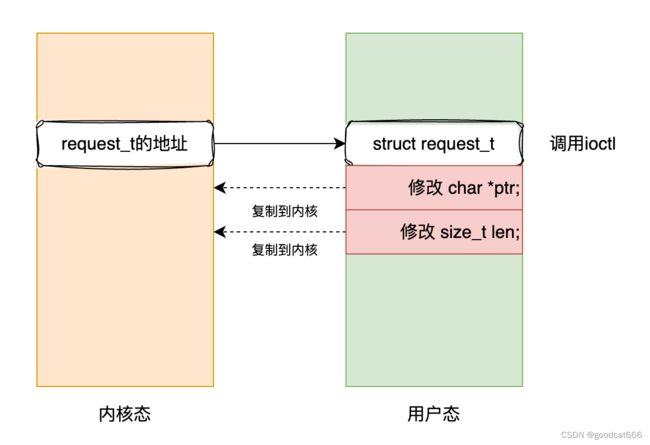
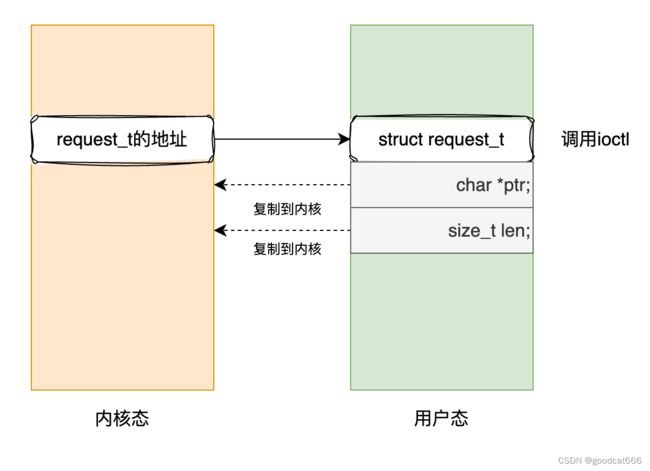
strcut request_t *是一个指针 - 执行
verify_request,会将strcut request_t *指针的内容,从用户态拷贝到内核态进行检查,这个没有问题
- 但是在
verify_request验证成功之后,在执行copy_data_to_user和copy_data_from_user时,还是通过strcut request_t *从用户态复制数据,这就导致在verify_request函数中copy_from_user执行之后,在copy_data_from_user函数copy_from_user执行之前可以修改用户态中struct reuqest的值,从而是verify_request检测无效
poc如下
#define _GNU_SOURCE
#include 漏洞利用
seq_operatioins && kmalloc-32
由于本题中,可通过Double-Fetch利用的堆对象在 kmalloc-32中
#define BUFFER_SIZE 0x20
filp->private_data = kzalloc(BUFFER_SIZE, GFP_KERNEL);
可通过open("/proc/self/stat", O_RDONLY)堆喷struct seq_operations结构体,填充到kmalloc-32 slab中
int fd_staa = open("/proc/self/stat", O_RDONLY);
struct seq_operations {
void * (*start) (struct seq_file *m, loff_t *pos);
void (*stop) (struct seq_file *m, void *v);
void * (*next) (struct seq_file *m, void *v, loff_t *pos);
int (*show) (struct seq_file *m, void *v);
};
通过read系统调用会触发 seq_operations->start,但是read系统调用传递的参数无法传递给 seq_operations->start
漏洞利用 pt_regs
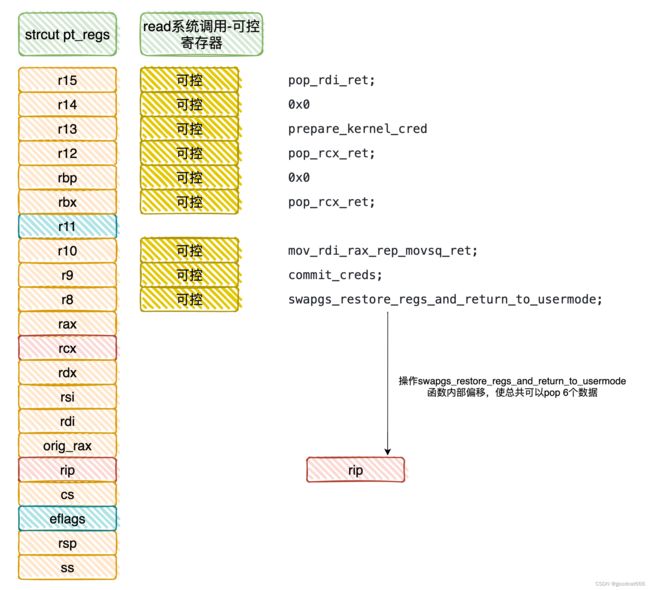
在系统调用进入内核态时,会将用户态的寄存器,保存在内核态的struct pt_regs结构体中,该结构体位于内核栈的栈底
可通过在用户态的寄存器中布局rop,再通过seq_operations->start实现栈迁移到pt_regs处,实现提权
关于怎么从seq_operations->start栈迁移到pt_regs处,对于本题,可以通过调试,在seq_operations->start触发前,观察当前rsp到栈底部pt_regs首部的偏移,再通过类似add rsp number; xxx; xxx; ret;跳转到pt_regs首部
#define _GNU_SOURCE
#include 新版本内核对抗利用 pt_regs 进行攻击的办法
来源自这里
正所谓魔高一尺道高一丈,内核主线在 这个 commit 中为系统调用栈添加了一个偏移值,这意味着 pt_regs 与我们触发劫持内核执行流时的栈间偏移值不再是固定值,这个保护的开启需要 CONFIG_RANDOMIZE_KSTACK_OFFSET=y (默认开启)
diff --git a/arch/x86/entry/common.c b/arch/x86/entry/common.c
index 4efd39aacb9f2..7b2542b13ebd9 100644
--- a/arch/x86/entry/common.c
+++ b/arch/x86/entry/common.c
@@ -38,6 +38,7 @@
#ifdef CONFIG_X86_64
__visible noinstr void do_syscall_64(unsigned long nr, struct pt_regs *regs)
{
+ add_random_kstack_offset();
nr = syscall_enter_from_user_mode(regs, nr);
instrumentation_begin();
当然,若是在这个随机偏移值较小且我们仍有足够多的寄存器可用的情况下,仍然可以通过布置一些 slide gadget 来继续完成利用,不过稳定性也大幅下降了, 可以说这种利用方式基本上是废了