0015-TIPS-pawnyable : userfaultfd
原文
Linux Kernel PWN | 040303 Pawnyable之userfaultfd
userfaultfdの利用
题目下载
代码分析
#include 打开驱动
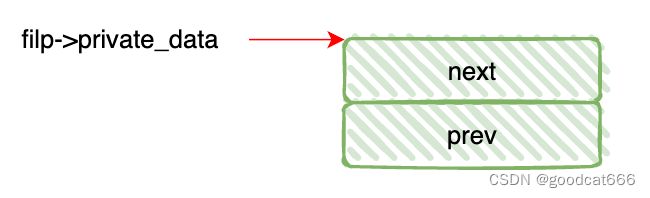
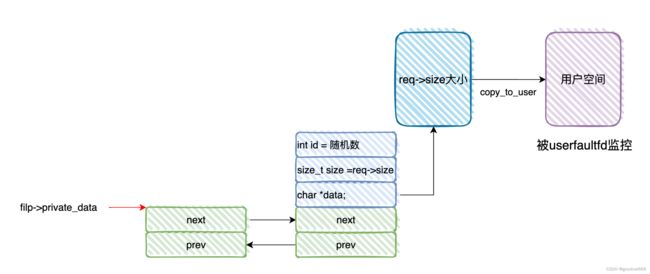
会创建一个双向链表,并将filp->private_data指向这个双向链表
blob_add
- 创建一个
struct blob_list节点, - 并根据参数
req-size传递的长度,创建一个堆空间,blob_list->data指向这个堆空间, - 再通过
copy_from_user,将参数req->data指向的用户空间的内容复制到blob_list->data中, - 之后将
req->size也就是req->data的长度值赋值给blob_list->size - 接着初始化
blob_list->list双向链表,并链入到filp->private_data - 最后生成一个随机数,赋值到
blob_list->id中,并返回给调用者,用来索引该节点

blob_del
- 通过参数
req->id索引到blob_list节点 - 将该节点从
filp->private_data双向链表中断开 - 删除
blob_list->data指向的堆空间 - 删除
struct blob_list节点占据的空间
blob_get
- 通过参数
req->id索引到blob_list节点 - 通过
copy_to_user将blob_list->data中的内容复制到参数req->data指向的用户空间
blob_set
- 通过参数
req->id索引到blob_list节点 - 通过
copy_from_user将参数req->data指向用户空间的内容复制到blob_list->data指向的内核空间
漏洞分析
代码存在条件竞争,并可转换为UAF漏洞
条件竞争->UAF:实现内核地址泄露
- 线程1新增一个链表节点A(blob_add)

- 线程1对链表节点A执行查询操作(blob_get);在copy_to_user执行前,线程2对链表节点A执行删除操作(blob_del),并喷射tty_struct占位(依赖于blob_add是传递参数req->size的值)

- 线程1执行copy_to_user,实际上将某个tty_struct的内容复制到了用户空间
条件竞争->UAF:实现控制流劫持
转化为UAF漏洞并实现控制流劫持所需的竞态状态:
1.线程1新增一个链表节点B(blob_add)

2.线程1对链表节点B执行查询操作(blob_set);在copy_from_user执行前,线程2对链表节点B执行删除操作(blob_del),并喷射tty_struct占位

3.线程1执行copy_from_user,实际上将占位的tty_struct内容替换成了攻击者的伪造tty_struct
条件竞争点在于,在执行copy_to_user和copy_from_user前,需要完成blob_list节点的删除,和堆喷的重新占位,这个难度较大,但是userfaultfd可以解决当前题目环境的问题。
userfaultfd解析
参考
man ioctl_userfaultfd
man userfaultfd
userfaultfd的功能
userfaultfd用于处理用户态缺页异常。比如mmap分配一段内存空间,此刻这段这段内存空间没有与物理页挂钩,只有实际对该空间进行读/写时,才通过缺页异常进入内核态挂载物理页。
现在可以通过userfaultfd机制,在用户态处理这个缺页异常。
比方,mmap 4页大小的虚拟空间,现在还没有挂上物理页

现在要往这段空间写入大量的数据,4 * 0x1000字节的数据。由于4 * 0x1000是4个page页的大小,每个页都会触发一次缺页异常,因此每个页都会触发一次userfaultfd
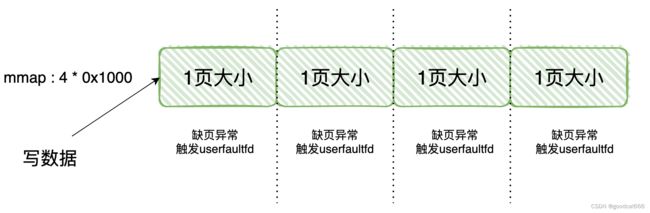
在经过userfaultfd处理后,这段4 * 0x1000虚拟空间都挂上了物理页,以后对这些虚拟空间的读写就不会发生缺页异常,因此对于每一个page大小的虚拟空间,userfaultfd只触发一次。
现在看看userfaultfd是怎么进行处理的
(步骤5大概就是这意思,我不知道是挂载的原始页,还是再生成新页,再把新页挂载到虚拟空间上?)
对于写
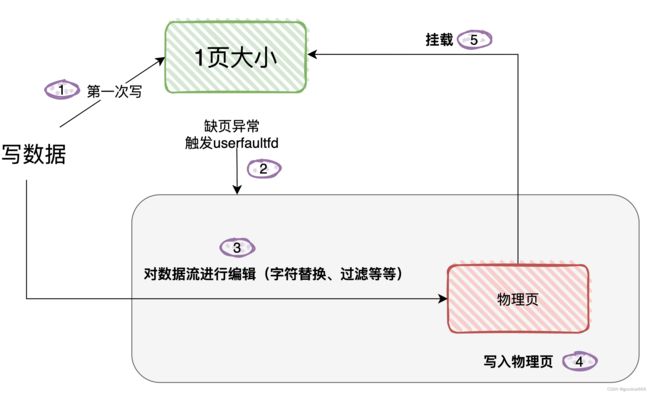
对于读

userfaultfd 操作逻辑
- 1、要使用userfaultfd功能,需要通过系统调用获取操作
userfaultfd的文件句柄,假设获取到的句柄是uffdint uffd = syscall(__NR_userfaultfd, O_CLOEXEC | O_NONBLOCK);
- 2、通过
uffd配置userfaultfd功能版本,缺页类型ioctl(uffd, UFFDIO_API, &uffdio_api)
- 3、通过
uffd配置注册缺页监控范围ioctl(uffd, UFFDIO_REGISTER, &uffdio_register)
- 4、通过
uffd文件描述符轮询缺页事件(由于从轮询事件会发生阻塞,所以从这一步往下需要放到一个新线程中)pthread_create(&th, NULL, fault_handler_thread, (void *)uffd)
- 5、通过
uffd配置处理缺页事件ioctl(uffd, UFFDIO_COPY, ©)
推荐看这三个文档
man ioctl_userfaultfd
man userfaultfd
https://www.kernel.org/doc/html/next/admin-guide/mm/userfaultfd.html
https://xz.aliyun.com/t/6653
再结合如下demo进行理解
/*
serfaultfd机制允许多线程程序中的某个线程为其他线程提供用户空间页面——如果该线程将这些页面注册到了userfaultfd对象上,
那么当针对这些页面的缺页异常发生时,触发缺页异常的线程将暂停运行,内核将生成一个缺页异常事件并通过userfaultfd文件描述符传递给异常处理线程。
异常处理线程可以做一些处理,然后唤醒之前暂停的线程
该程序首先使用mmap在用户空间分配两个匿名页,接着创建userfaultfd,并启动一个线程来处理缺页异常。
然后,主线程尝试向先前申请的两个匿名页依次写入数据。
针对这两个页的第一次读操作将触发两次缺页异常,子线程将从阻塞态恢复并执行处理逻辑。
针对同一页面的第二次及之后的读写操作将不再触发缺页异常
*/
#define _GNU_SOURCE
#include 漏洞利用
对于本体,只要用户空间被userfaultfd监控,条件竞争就能稳定触发成功
poc
#define _GNU_SOURCE
#include exp
#define _GNU_SOURCE
#include