安全漏洞之host头攻击漏洞
安全漏洞之host头攻击漏洞
漏洞描述
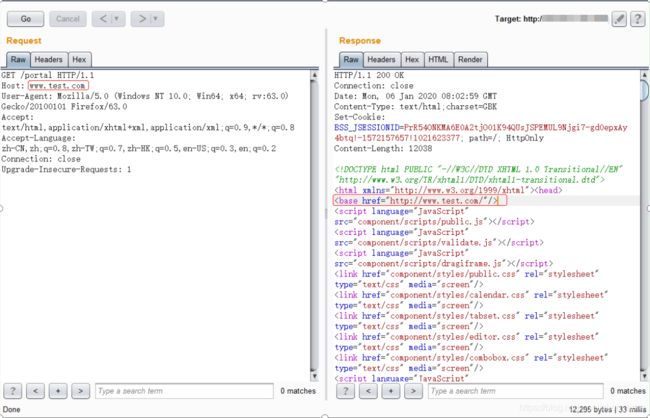
渗透测试人员发现,抓包修改host头,在返回包中的base标签中的值会随host值改变,说明存在host头攻击漏洞。
漏洞建议
建议使用SERVER_NAME而不是host header。
脆弱性评价:
| 严重程度 |
高 |
|
中 |
■ |
低 |
|
修复过程:
web.xml:
image
com.linkage.component.util.file.ImageServlet
bssframe
/portal
attach
/attach
image
/image
480
ImageServlet.java:
//
// Source code recreated from a .class file by IntelliJ IDEA
// (powered by Fernflower decompiler)
//
package com.linkage.component.util.file;
import com.linkage.appframework.common.Common;
import com.linkage.appframework.data.IData;
import com.linkage.component.AppServlet;
import com.linkage.component.PageData;
import com.linkage.component.bean.adm.UtilBean;
import com.linkage.webframework.util.file.FileMan;
import com.linkage.webframework.util.file.ImageMan;
import java.io.IOException;
import java.io.PrintWriter;
import javax.servlet.ServletException;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import org.apache.commons.fileupload.FileItem;
public class ImageServlet extends AppServlet {
public static final String IMAGE_ACTION_UPLOAD = "upload";
public static final String IMAGE_ACTION_VIEW = "view";
public static final String IMAGE_VIEW_VALIDATE = "validate";
public static final String IMAGE_VIEW_FILE = "file";
protected Common common = Common.getInstance();
public ImageServlet() {
}
public void service(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
try {
this.servletInit(request, response);
PageData pd = this.getPageData();
UtilBean bean = new UtilBean();
String action = pd.getParameter("action", "view");
String mode;
String width;
if ("upload".equals(action)) {
mode = pd.getParameter("IMAGE_WIDTH");
width = pd.getParameter("IMAGE_HEIGHT");
FileItem item = pd.getFileItem("IMAGE_PATH");
IData data = bean.createFile(pd, item, "2", "1");
StringBuffer src = new StringBuffer();
src.append("image?file_id=" + data.get("FILE_ID"));
if (!"".equals(mode)) {
src.append("&width=" + mode);
}
if (!"".equals(width)) {
src.append("&height=" + width);
}
StringBuffer image = new StringBuffer();
image.append(" ");
PrintWriter out = response.getWriter();
out.println("");
}
if ("view".equals(action)) {
mode = pd.getParameter("mode", "file");
width = pd.getParameter("width");
String height = pd.getParameter("height");
String file_id;
if ("validate".equals(mode)) {
String query = request.getQueryString();
String[] arrs = new String[]{"|", "$", "'", "'", "(", "CR", "(HOST)", "", "--", "%", "LF", "(host)", "<", "script", "@", "+", "<>"};
int num = 0;
for(int i = 0; i < arrs.length; i++) {
if (arrs[i].length() > 0 && query.indexOf(arrs[i]) > 0) {
log.debug("HOST WARNING !!!--->( " + arrs[i] + " ) ");
num++;
}
}
if (num > 0) {
this.common.error("您采取非法登陆方式,参数含有特殊字符,拒绝访问");
}
file_id = ImageMan.showValidateImage(response, Integer.parseInt(width), Integer.parseInt(height));
request.getSession().setAttribute("VERIFY_CODE", file_id);
String verify_code = ImageMan.showValidateImage(response, Integer.parseInt(width), Integer.parseInt(height));
request.getSession().setAttribute("VERIFY_CODE", verify_code);
}
if ("file".equals(mode)) {
file_id = pd.getParameter("file_id");
String file_path = pd.getParameter("file_path");
if (file_id == null) {
ImageMan.showImage(response, file_path, FileMan.getFileType(file_path), width, height);
} else {
IData data = bean.queryFile(pd, file_id);
if (data == null) {
this.common.error("文件记录 " + file_id + " 不存在!");
}
String full_name = (String)data.get("FILE_PATH") + "/" + data.get("FILE_ID");
String file_name = (String)data.get("FILE_NAME");
ImageMan.showImage(response, full_name, FileMan.getFileType(file_name), width, height);
}
}
}
} catch (Exception var17) {
this.servletReseted();
this.setErrorInfo(var17);
} finally {
this.servletDetached();
}
}
}
");
PrintWriter out = response.getWriter();
out.println("");
}
if ("view".equals(action)) {
mode = pd.getParameter("mode", "file");
width = pd.getParameter("width");
String height = pd.getParameter("height");
String file_id;
if ("validate".equals(mode)) {
String query = request.getQueryString();
String[] arrs = new String[]{"|", "$", "'", "'", "(", "CR", "(HOST)", "", "--", "%", "LF", "(host)", "<", "script", "@", "+", "<>"};
int num = 0;
for(int i = 0; i < arrs.length; i++) {
if (arrs[i].length() > 0 && query.indexOf(arrs[i]) > 0) {
log.debug("HOST WARNING !!!--->( " + arrs[i] + " ) ");
num++;
}
}
if (num > 0) {
this.common.error("您采取非法登陆方式,参数含有特殊字符,拒绝访问");
}
file_id = ImageMan.showValidateImage(response, Integer.parseInt(width), Integer.parseInt(height));
request.getSession().setAttribute("VERIFY_CODE", file_id);
String verify_code = ImageMan.showValidateImage(response, Integer.parseInt(width), Integer.parseInt(height));
request.getSession().setAttribute("VERIFY_CODE", verify_code);
}
if ("file".equals(mode)) {
file_id = pd.getParameter("file_id");
String file_path = pd.getParameter("file_path");
if (file_id == null) {
ImageMan.showImage(response, file_path, FileMan.getFileType(file_path), width, height);
} else {
IData data = bean.queryFile(pd, file_id);
if (data == null) {
this.common.error("文件记录 " + file_id + " 不存在!");
}
String full_name = (String)data.get("FILE_PATH") + "/" + data.get("FILE_ID");
String file_name = (String)data.get("FILE_NAME");
ImageMan.showImage(response, full_name, FileMan.getFileType(file_name), width, height);
}
}
}
} catch (Exception var17) {
this.servletReseted();
this.setErrorInfo(var17);
} finally {
this.servletDetached();
}
}
}
home.java:
//防止host头攻击漏洞
String host =pd.getRequest().getHeader("referer");
log.debug("host--------->"+host);
String[] arrs ={"|","$","'","\'","(","CR","(HOST)","","--","%","LF","(host)","<","script","@","+","<>"};
int num=0;
for(int i=0;i0 && host.indexOf(arrs[i])>0 ){
log.debug("HOST WARNING !!!--->( " + arrs[i] + " ) ");
num++;
}
}
if(num>0){
common.error("您采取非法登陆方式,参数含有特殊字符,拒绝访问");
}