企业入门实战--k8s之vxlan 、calico、 ingress实现七层负载均衡
企业入门实战--k8s之vxlan 、calico、 ingress实现七层负载均衡
- Flannel vxlan
-
- DR模式实现
- calico网络插件替换flannel
- calico支持的网络策略-访问控制
- Ingress-nginx七层负载均衡实现
-
- 安装Ingress
Flannel vxlan
DR模式实现
flannel支持多种后端,包括
vxlan默认报文封装模式,适用于跨网段通信
Directrouting直连路由模式,适用于同网段通信。表现为host-gw,主机网关,性能好,但只能在二层网络中,不支持跨网。
flannel 会缓存所有节点的mac地址
两个eth0 如何知道对方的ip:桥接数据库
kubectl -n kube-system get cm
kubectl -n kube-system get pod
kubectl -n kube-system edit cm kube-flannel-cfg ## 编辑文件
calico网络插件替换flannel
server1
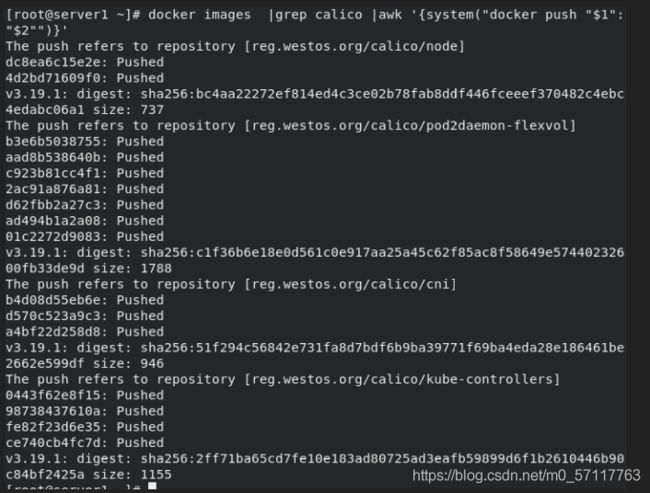
打标签 上传至harbor仓库
docker load -i calico-v3.19.1.tar
docker images |grep calico |awk '{system("docker push "$1":"$2"")
修改yaml资源清单,使得镜像拉取本地harbor仓库。(需要修改全部的image路径)

删除之前的网络插件flannel
kubectl delete -f kube-flannel.yml
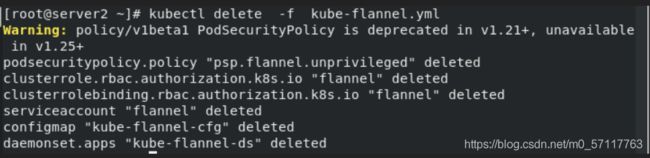
必要步骤:删除所有k8s节点的插件配置缓存文件
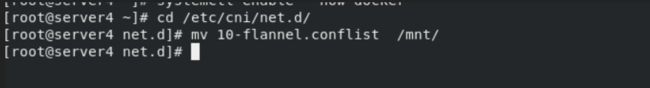
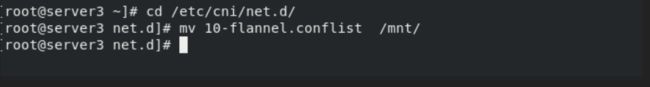

拉起插件,等待初始化
kubectl apply -f calico.yaml
kubectl get pod -n kube-system
calico支持的网络策略-访问控制
限制访问指定服务:
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-nginx
spec:
podSelector:
matchLabels:
app: nginx
允许指定pod访问服务:
kind: NetworkPolicy
apiVersion: networking.k8s.io/v1
metadata:
name: access-nginx
spec:
podSelector:
matchLabels:
app: nginx
ingress:
- from:
- podSelector:
matchLabels:
app: demo
禁止 namespace 中所有 Pod 之间的相互访问:
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: default-deny
namespace: default
spec:
podSelector: {}
禁止其他 namespace 访问服务:
kind: NetworkPolicy
apiVersion: networking.k8s.io/v1
metadata:
name: deny-namespace
spec:
podSelector:
matchLabels:
ingress:
- from:
- podSelector: {}
只允许指定namespace访问服务:
kind: NetworkPolicy
apiVersion: networking.k8s.io/v1
metadata:
name: access-namespace
spec:
podSelector:
matchLabels:
app: myapp
ingress:
- from:
- namespaceSelector:
matchLabels:
role: prod
允许外网访问:
kind: NetworkPolicy
apiVersion: networking.k8s.io/v1
metadata:
name: web-allow-external
spec:
podSelector:
matchLabels:
app: web
ingress:
- ports:
- port: 80
from: []
Ingress-nginx七层负载均衡实现
安装Ingress
,harbor仓库中新建项目ingress-nginx,压入镜像到harbor仓库

docker tag reg.westos.org/ingress-nginx/controller:v0.48.1 hyl.westos.org/ingress-nginx/controller:v0.48.1
docker tag reg.westos.org/ingress-nginx/kube-webhook-certgen:v1.5.1 hyl.westos.org/ingress-nginx/kube-webhook-certgen:v1.5.1
docker push hyl.westos.org/ingress-nginx/controller:v0.48.1
docker push hyl.westos.org/ingress-nginx/kube-webhook-certgen:v1.5.1



官网下载ingress-nginx部署所需资源清单,修改镜像get地址为本地harbor仓库

拉起pod节点,kubectl apply -f deploy.yaml

查看生成的namespace状态
kubectl get ns

查看ingress-nginx的所有信息,可以看到ingress-nginx-controller已经running
kubectl -n ingress-nginx get all
kubectl -n ingress-nginx get svc

访问测试:

配置ingress-nginx七层均衡
添加svc服务
vim svc.yaml
apiVersion: v1
kind: Service
metadata:
name: mysvc
spec:
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: myapp
拉起服务并查看endpoint
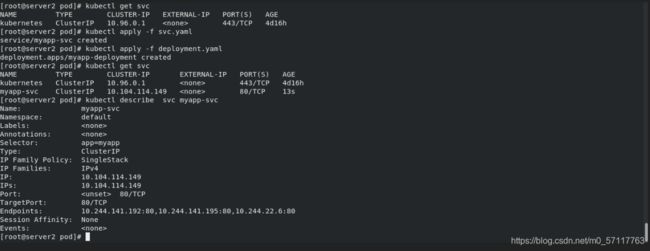
修改svc配置文件为负载均衡
kubectl -n ingress-nginx edit svc ingress-nginx-controller
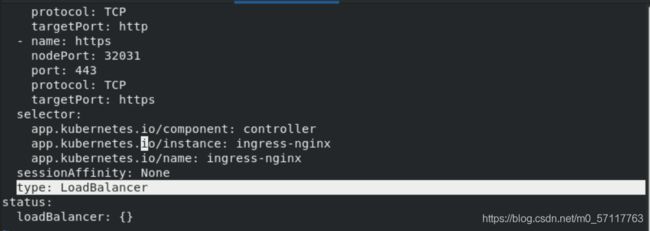
kubectl -n ingress-nginx get svc
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 3
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: myapp:v2
拉起deployment,通过标签来锁定域名
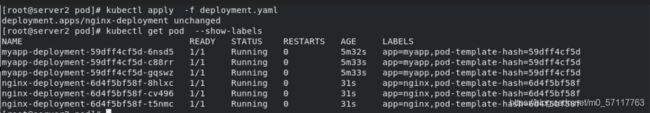
为标签为nginx的deployment添加服务
vim svc.yaml
apiVersion: v1
kind: Service
metadata:
name: myapp-svc
spec:
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: myapp
---
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
ports:
kubectl apply -f deployment.yaml
kubectl apply -f svc.yaml
kubectl -n ingress-nginx get all
kubectl get ns
测试:
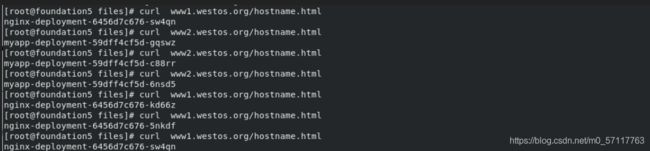
curl www1.westos.org/hostname.html
curl www2.westos.org/hostname.html
- protocol: TCP
port: 80
targetPort: 80
selector:
app: nginx
kubectl describe svc myapp-svc
kubectl describe svc nginx-svc

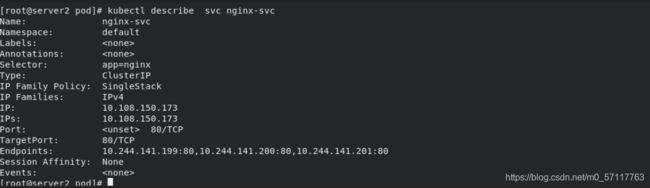
配置服务与ingress连接,并给定域名
vim ingress.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-nginx
spec:
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-myapp
spec:
rules:
- host: www2.westos.org
http:
paths:
- path: /
backend:
serviceName: myapp-svc
servicePort: 80
拉起资源清单
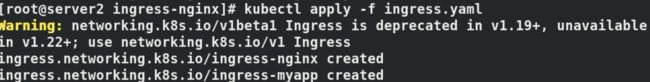
kubectl apply -f ingress.yaml
kubectl get ingress
172.25.5.10 www1.westos.org www2.westos.org
访问测试
curl www1.westos.org
curl www2.westos.org