基于Window 2003环境下搭建Snort混合入侵检测系统
搭建Snort+BASE入侵检测系统
基于Window 2003环境下搭建的Snort混合环境入侵检测系统,本文参考至:https://www.jianshu.com/p/d8ca2e8c0858,作者afternone
目录
- 搭建Snort+BASE入侵检测系统
- 部署过程
- 一、安装并配置Snort
-
- 1.安装Snort
- 2.替换Snort规则
- 3.打开配置文件
- 4.修改配置文件
- 二、安装并配置AppServ
-
- 1.安装AppServ
- 2.查看Apache是否已安装好
- 3.创建mysql数据库和表
- 三、配置BASE
-
- 1.拷贝base、adodb文件夹至AppServ\www目录下
- 2.进行可视化窗口操作
- 四、启动Snort
-
- 1.进入 snort\bin目录下
- 2.使snort工作在网络监测系统模式
- 3.观察统计信息
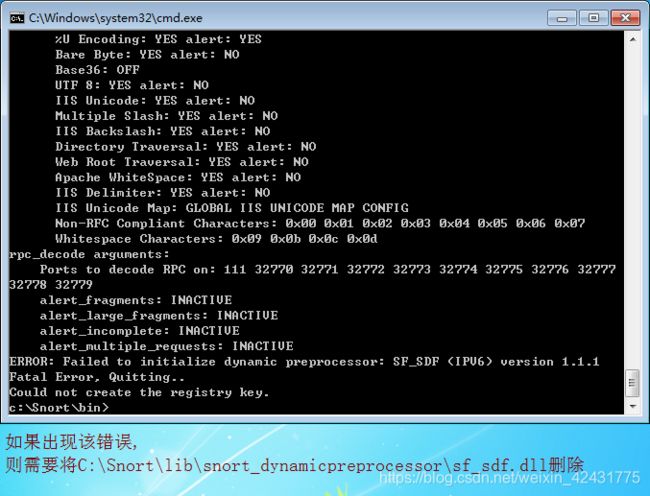
- 4.如果启动snort失败(设置snort工作在网络监测系统模式失败)运行失败并显示错误,如下图
部署过程
下载好各种环境包即可开始搭建
环境包下载地址:https://download.csdn.net/download/weixin_42431775/19826391?spm=1001.2014.3001.5503
一、安装并配置Snort
1.安装Snort
此处采用Snort_2_8_6版本,安装过程一路默认点击下一步即可,并没有特殊操作
2.替换Snort规则
将对应Snort版本的规则包的doc、rules、so_rules文件夹拷贝至Snort安装目录下,并全部选择覆盖文件

3.打开配置文件
打开Snort安装目录中的etc文件夹,用编辑器打开snort.conf(推荐用notepad++,或编辑器,直接用文本打开的话里面的代码简直不能看)
4.修改配置文件
1、根据关键字var RULE_PATH,检索到其所在位置并进行修改

//可直接拷贝进行覆盖
var RULE_PATH c:\snort\rules
var SO_RULE_PATH c:\snort\so_rules
var PREPROC_RULE_PATH c:\snort\preproc_rules
2、根据# path to dynamic preprocessor关键字,检索其所在位置并修改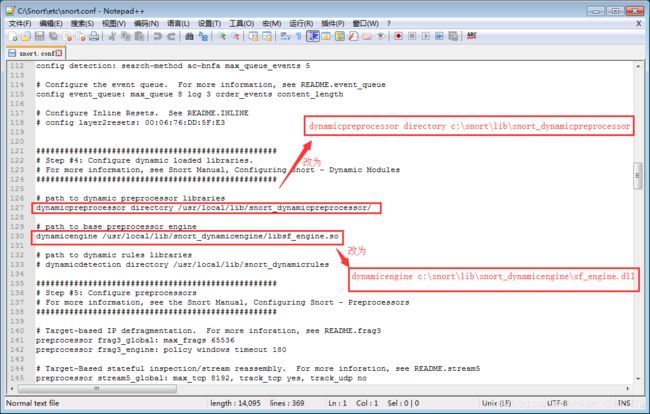
//可直接拷贝覆盖
# path to dynamic preprocessor libraries
dynamicpreprocessor directory c:\snort\lib\snort_dynamicpreprocessor
# path to base preprocessor engine
dynamicengine c:\snort\lib\snort_dynamicengine\sf_engine.dll
3、根据关键字preprocessor http_inspect,检索所在位置并修改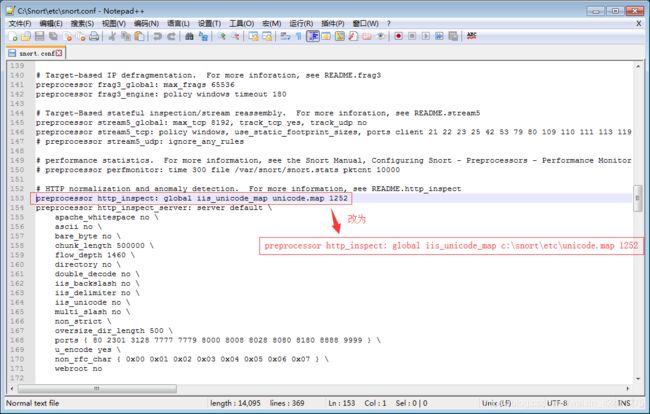
//可直接拷贝复制
preprocessor http_inspect: global iis_unicode_map c:\snort\etc\unicode.map 1252
4、根据关键字output database,检索所在位置并修改
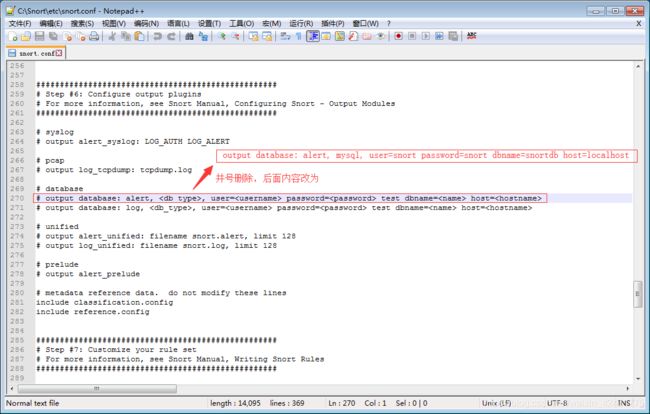
//可直接拷贝覆盖
output database: alert, mysql, user=snort password=snort dbname=snortdb host=localhost
5、根据关键字# decoder and preprocessor event rules,检索所在位置,修改所在行及其上下大行
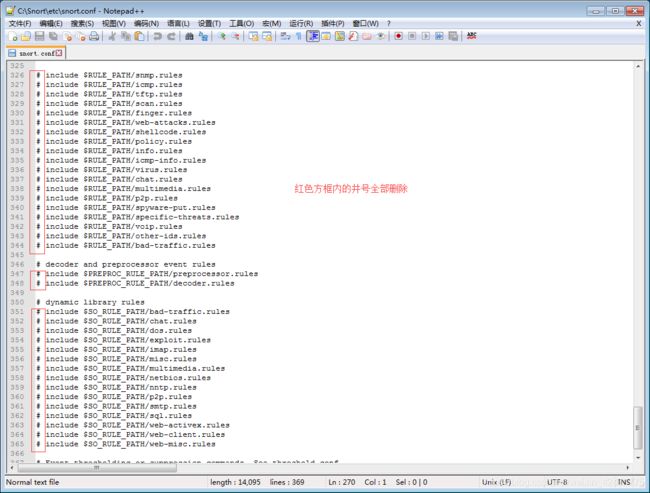
//可直接拷贝覆盖,注意覆盖范围!注意覆盖范围!注意覆盖范围!
include $RULE_PATH/snmp.rules
include $RULE_PATH/icmp.rules
include $RULE_PATH/tftp.rules
include $RULE_PATH/scan.rules
include $RULE_PATH/finger.rules
include $RULE_PATH/web-attacks.rules
include $RULE_PATH/shellcode.rules
include $RULE_PATH/policy.rules
include $RULE_PATH/info.rules
include $RULE_PATH/icmp-info.rules
include $RULE_PATH/virus.rules
include $RULE_PATH/chat.rules
include $RULE_PATH/multimedia.rules
include $RULE_PATH/p2p.rules
include $RULE_PATH/spyware-put.rules
include $RULE_PATH/specific-threats.rules
include $RULE_PATH/voip.rules
include $RULE_PATH/other-ids.rules
include $RULE_PATH/bad-traffic.rules
# decoder and preprocessor event rules
include $PREPROC_RULE_PATH/preprocessor.rules
include $PREPROC_RULE_PATH/decoder.rules
# dynamic library rules
include $SO_RULE_PATH/bad-traffic.rules
include $SO_RULE_PATH/chat.rules
include $SO_RULE_PATH/dos.rules
include $SO_RULE_PATH/exploit.rules
include $SO_RULE_PATH/imap.rules
include $SO_RULE_PATH/misc.rules
include $SO_RULE_PATH/multimedia.rules
include $SO_RULE_PATH/netbios.rules
include $SO_RULE_PATH/nntp.rules
include $SO_RULE_PATH/p2p.rules
include $SO_RULE_PATH/smtp.rules
include $SO_RULE_PATH/sql.rules
include $SO_RULE_PATH/web-activex.rules
include $SO_RULE_PATH/web-client.rules
include $SO_RULE_PATH/web-misc.rules
二、安装并配置AppServ
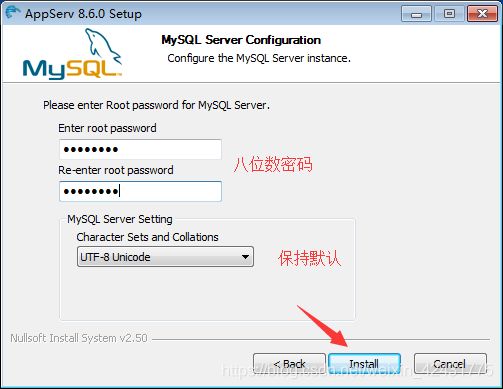
1.安装AppServ
AppServ是一个集成软件(集成了Apache和Mysql)一路选择默认点击下一步,直到
2.查看Apache是否已安装好
打开浏览器,输入localhost或127.0.0.1查看是否安装好Apache,若打开失败,则查看是否80端口被IIS占用、apache服务是否已启动

3.创建mysql数据库和表
//可直接复制粘贴,注意,有的末尾要带分号有的不用!!!
mysql> create database snortdb;
mysql> create database snortarc;
mysql> use snortdb;
mysql> source c:\snort\schemas\create_mysql
mysql> use snortarc;
mysql> source c:\snort\schemas\create_mysql
mysql> grant usage on *.* to "snort"@"localhost" identified by "snort";
mysql> grant select,insert,update,delete,create,alter on snortdb .* to "snort"@"localhost";
mysql> grant select,insert,update,delete,create,alter on snortarc .* to "snort"@"localhost";
mysql> set password for "snort"@"localhost"=password('snort');
三、配置BASE
可用命令行也可用可视化窗口,建议用可视化窗口
1.拷贝base、adodb文件夹至AppServ\www目录下
2.进行可视化窗口操作
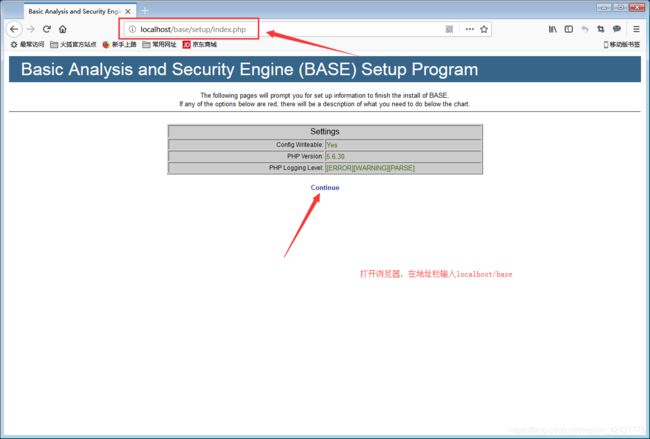
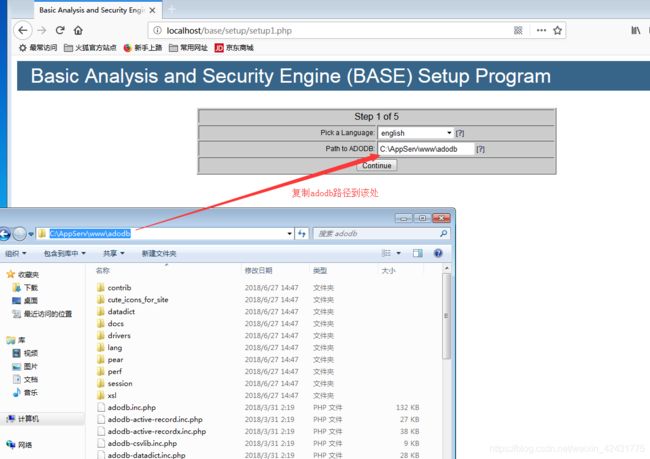
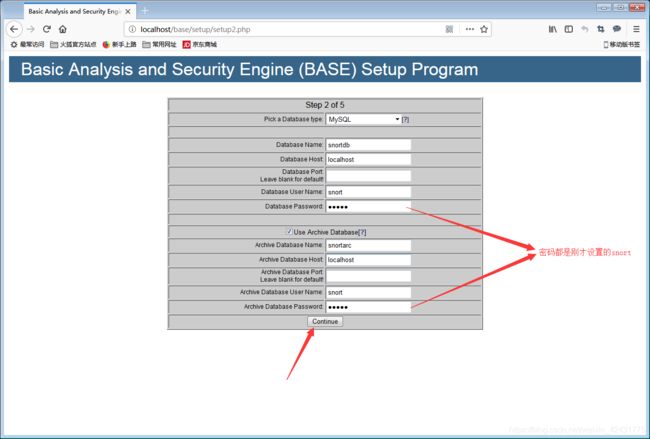
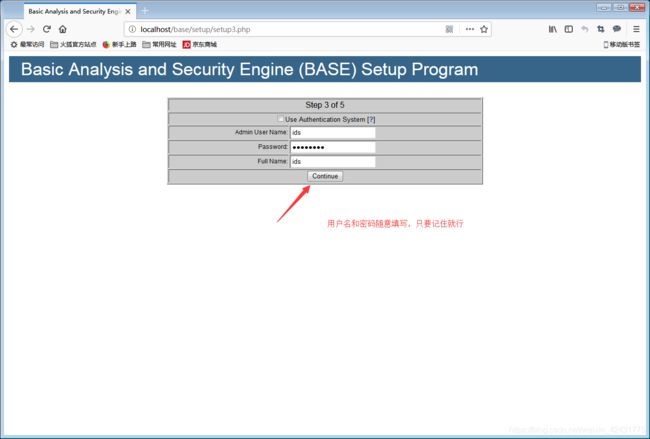
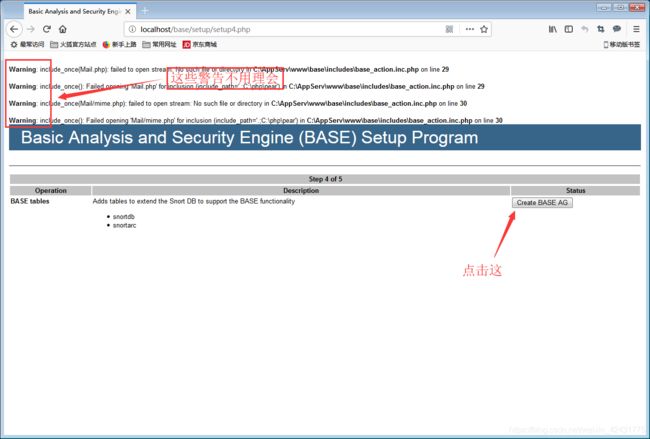
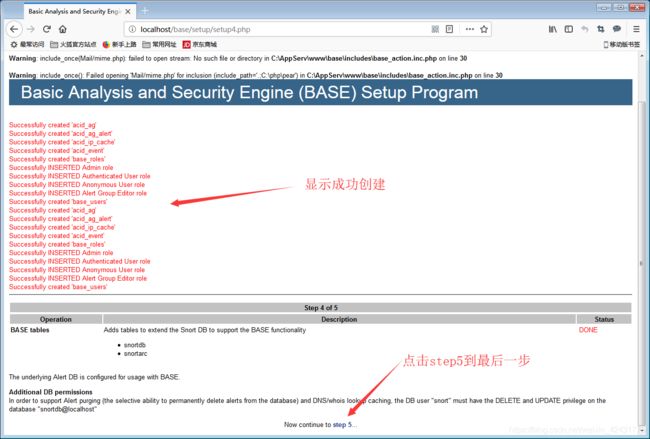
在浏览器中输入:localhost\base\base_main.php或127.0.0.1\base\base_main.php进入BASE可视化界面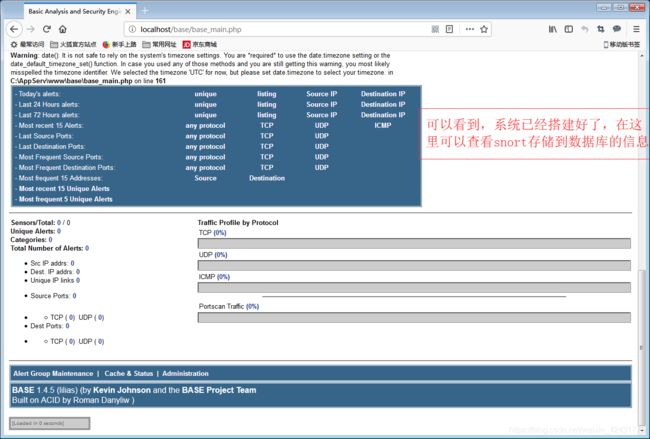
四、启动Snort
1.进入 snort\bin目录下
cd /Snort/bin
2.使snort工作在网络监测系统模式
snort -c c:\snort\etc\snort.conf -l c:\snort\logs -d -e -v
3.观察统计信息
另一台主机用nmap扫描该主机,则可以在base界面看到统计信息(需要手动刷新才能看到新的统计信息)
c:\snort\bin\snort -i1 -dev -c c:\snort\etc\snort.conf -l c:\snort\log