2022宁波市第五届网络安全大赛(初赛Misc部分)
听说线下决赛有菠萝包吃?
解题情况:5题解4,一个三血,哆哆嗦嗦进决赛
BlackAndWhite
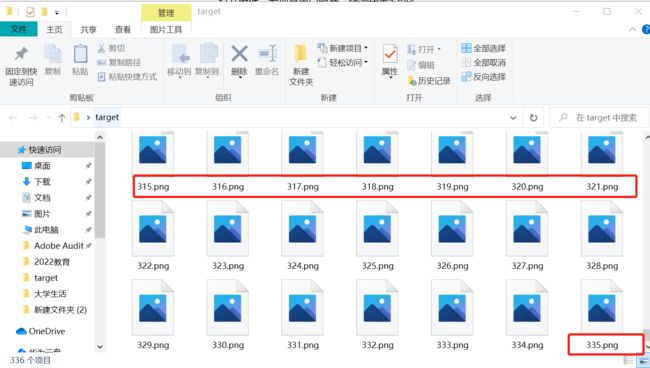
打开附件,发现是黑色和白色照片,猜测代表2进制,一共336张
脚本如下
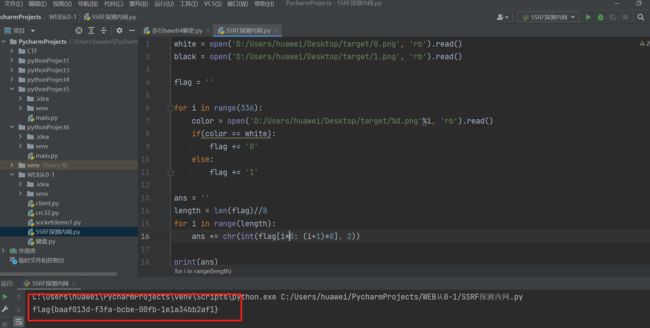
white = open('D:/Users/huawei/Desktop/target/0.png', 'rb').read()
black = open('D:/Users/huawei/Desktop/target/1.png', 'rb').read()
flag = ''
for i in range(336):
color = open('D:/Users/huawei/Desktop/target/%d.png'%i, 'rb').read()
if(color == white):
flag += '0'
else:
flag += '1'
ans = ''
length = len(flag)//8
for i in range(length):
ans += chr(int(flag[i*8: (i+1)*8], 2))
print(ans)
flag{baaf013d-f3fa-bcbe-00fb-1e1a34bb2af1}
Analyze
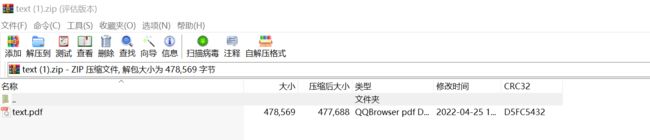
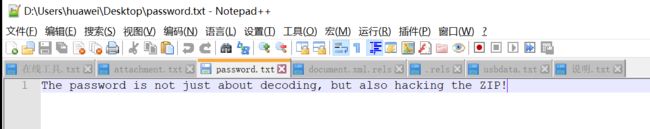
PDF文件
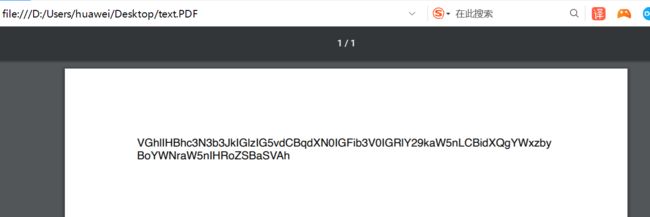
base64编码过
VGhlIHBhc3N3b3JkIGlzIG5vdCBqdXN0IGFib3V0IGRlY29kaW5nLCBidXQgYWxzbyBoYWNraW5nIHRoZSBaSVAh 解码之后 The password is not just about decoding, but also hacking the ZIP!
提示爆破,爆破出密码为cr4ck!*
成功解压
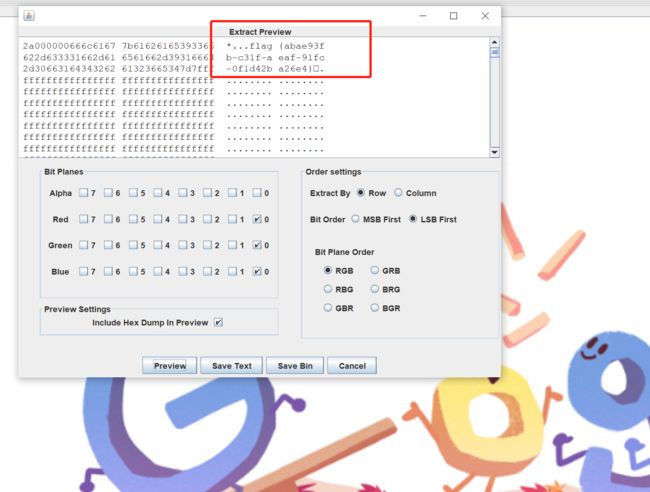
使用stegsolve打开图片
拿到flag
flag{abae93fb-c31f-aeaf-91fc-0f1d42ba26e4}
DocDocDoc
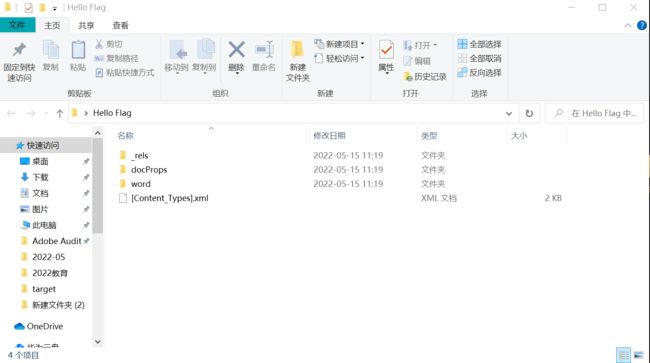
打开附件
D:\Users\huawei\Desktop\Hello Flag\word\media
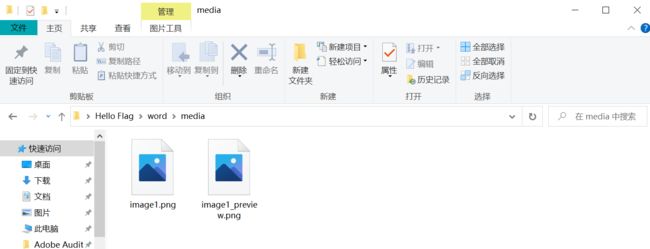
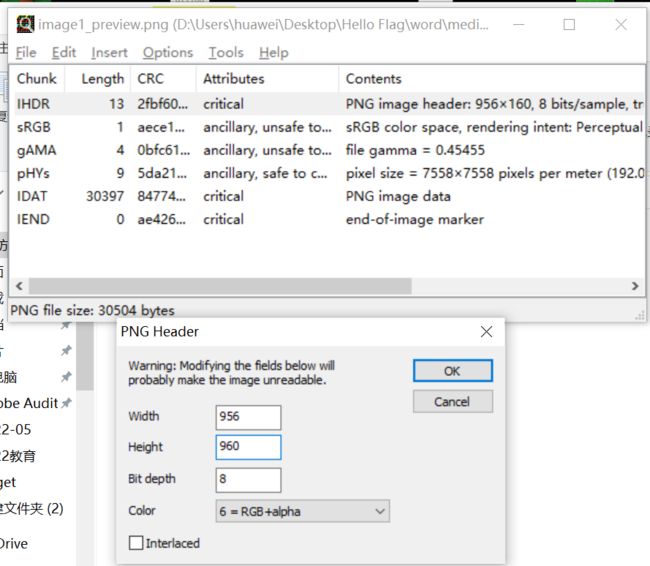
这个路径下有两张图片
第二张图片,使用tweakpng修改高度为960
打开图片
pvkq{olp281m-m2pk-kmlo-81pl-2o2m08m0pmk1}
位移密码,key=10
flag{ebf281c-c2fa-acbe-81fb-2e2c08c0fca1}
Digtal_plate
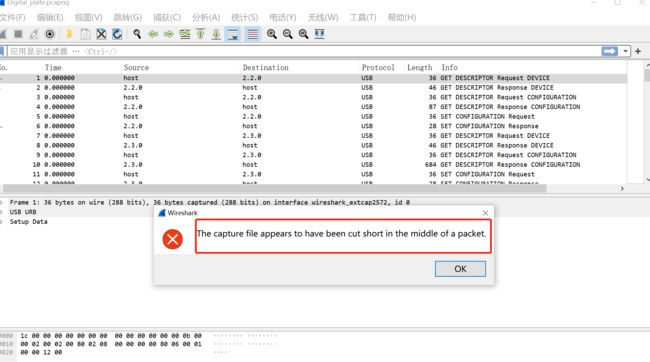
流量包报错
提取usbdata脚本
#!/usr/bin/env python
# coding:utf-8
import sys
import os
import numpy as np
import matplotlib.pyplot as plt
mousePositionX = 0
mousePositionY = 0
X = []
Y = []
DataFileName = "usb.dat"
data = []
def main():
global mousePositionX
global mousePositionY
# check argv
if len(sys.argv) != 3:
print ("Usage : ")
print (" python UsbMiceHacker.py data.pcap [LEFT|RIGHT|MOVE|ALL]")
print ("Tips : ")
print (" To use this python script , you must install the numpy,matplotlib first.")
print (" You can use `sudo pip install matplotlib numpy` to install it")
print ("Author : ")
print (" WangYihang ")
print (" If you have any questions , please contact me by email.")
print (" Thank you for using.")
exit(1)
# get argv
pcapFilePath = sys.argv[1]
action = sys.argv[2]
if action != "LEFT" and action != "ALL" and action != "RIGHT" and action != "MOVE":
action = "LEFT"
# get data of pcap
command = "tshark -r '%s' -T fields -e usbhid.data > %s" % (
pcapFilePath, DataFileName)
print (command)
os.system(command)
# read data
with open(DataFileName, "r") as f:
for line in f:
data.append(line[0:-1])
# handle move
for i in data:
Bytes = i.split(":")
if len(Bytes) == 8:
horizontal = 2 # -
vertical = 4 # |
elif len(Bytes) == 4:
horizontal = 1 # -
vertical = 2 # |
else:
continue
offsetX = int(Bytes[horizontal], 16)
offsetY = int(Bytes[vertical], 16)
if offsetX > 127:
offsetX -= 256
if offsetY > 127:
offsetY -= 256
mousePositionX += offsetX
mousePositionY += offsetY
if Bytes[0] == "01":
# print "[+] Left butten."
if action == "LEFT":
# draw point to the image panel
X.append(mousePositionX)
Y.append(-mousePositionY)
elif Bytes[0] == "02":
# print "[+] Right Butten."
if action == "RIGHT":
# draw point to the image panel
X.append(mousePositionX)
Y.append(-mousePositionY)
elif Bytes[0] == "00":
# print "[+] Move."
if action == "MOVE":
# draw point to the image panel
X.append(mousePositionX)
Y.append(-mousePositionY)
else:
# print "[-] Known operate."
pass
if action == "ALL":
# draw point to the image panel
X.append(mousePositionX)
Y.append(-mousePositionY)
fig = plt.figure()
ax1 = fig.add_subplot(111)
ax1.set_title('[%s]-[%s] Author : WangYihang' % (pcapFilePath, action))
ax1.scatter(X, Y, c='r', marker='o')
plt.show()
# clean temp data
os.system("rm ./%s" % (DataFileName))
if __name__ == "__main__":
main()
发现是 数位板流量(前三位是088,后8位是八个0)
判断是数位板上画图
画图脚本
#!/usr/bin/env python
# coding:utf-8
import sys
import os
import numpy as np
import matplotlib.pyplot as plt
data=[]
with open("usbdata.txt","r") as f:
for line in f.readlines():
data.append(line)
X = []
Y = []
for line in data:
x0=int(line[4:6],16)
x1=int(line[6:8],16)
x=x0+x1*256
y0=int(line[8:10],16)
y1=int(line[10:12],16)
y=y0+y1*256
X.append(x)
Y.append(-y)
fig = plt.figure()
ax1 = fig.add_subplot(111)
ax1.set_title("key")
ax1.scatter(X, Y, c='r', marker='o')
plt.show()
画图结果如下
拿到一个key
kaseyd4wi2v3sc518dc84bsa4a96
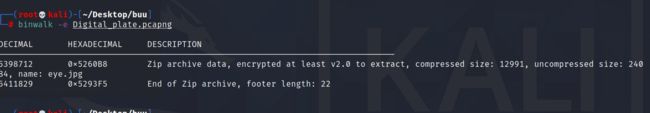
binwalk -e 出来一个zip文件
解压密码就是上面那个
解压出一个图片
猜测是silenteye解密,解密失败
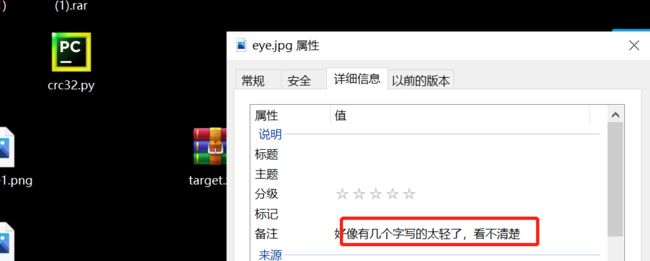
备注发现异常
写的太轻,提示到数位板画画的时候,会有压力感觉
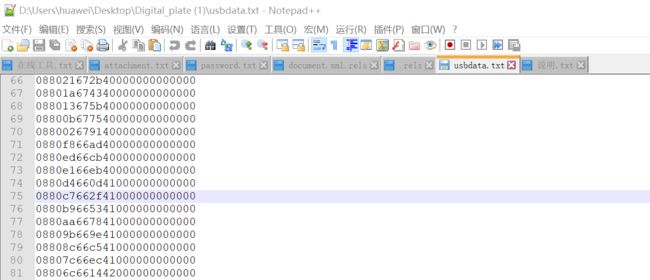
看一下前面都有
0880应该是标识所以画点的数据应该在后面
有数值的是八位
所以x四位y四位
然后发现后面有0880,0881
两个都导出一下,0880是没按压,0881是按压,把0881为前缀的数据提取出来然后描点就行了
#!/usr/bin/env python
# coding:utf-8
# beizi
import matplotlib.pyplot as plt
import sys
import numpy as np
import os
data=[]
with open("usbhiddata.txt","r") as f:
for line in f.readlines():
data.append(line)
X = []
Y = []
for line in data:
x0=int(line[4:6],16)
x1=int(line[6:8],16)
x=x0+x1*256
y0=int(line[8:10],16)
y1=int(line[10:12],16)
y=y0+y1*256
X.append(x)
Y.append(-y)
fig = plt.figure()
ax1 = fig.add_subplot(111)
ax1.set_title("key")
ax1.scatter(X, Y, c='r', marker='o')
plt.show()
提取带有压感的流量数据,画图得到
18cba496
作为key,使用slienceeye解密
flag{42a12187c01a4a4f2b3f5ccd0a019656}